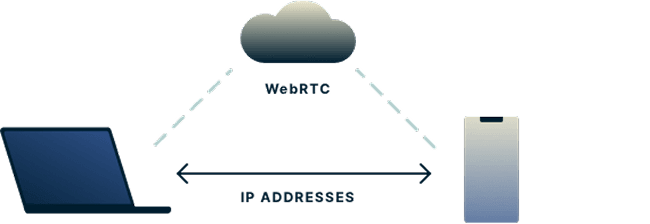
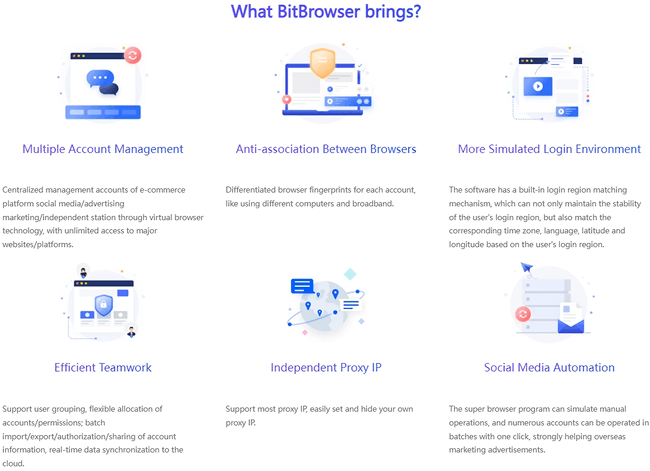
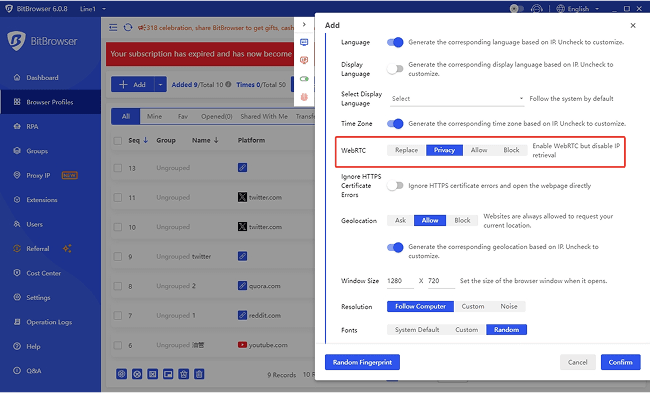
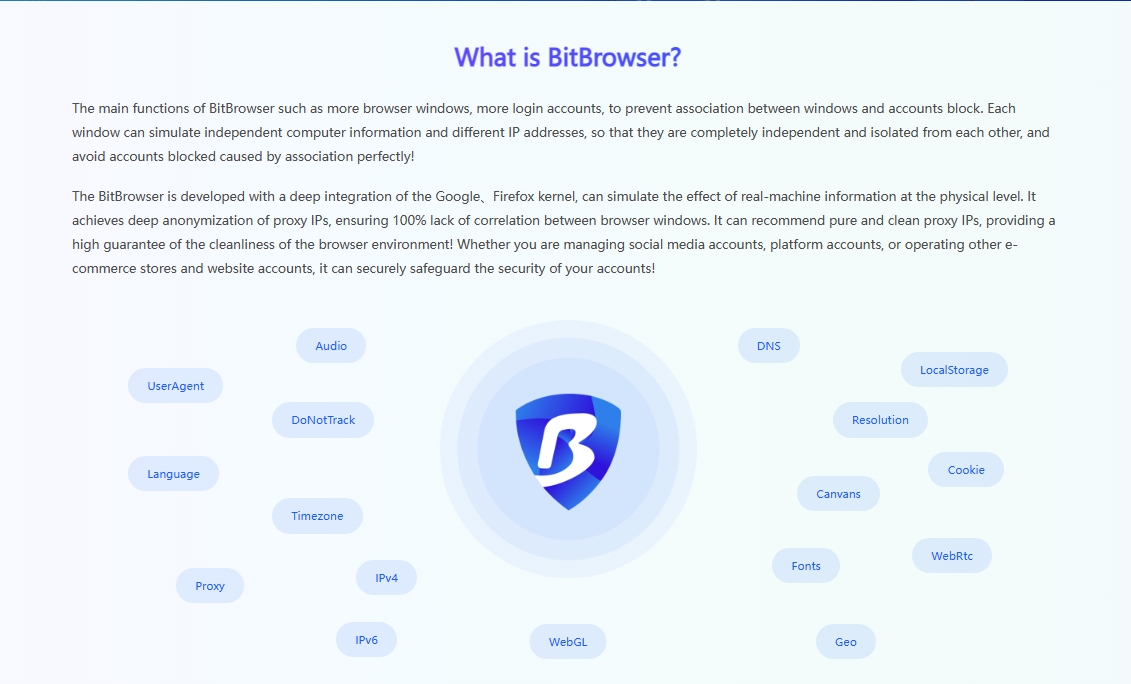
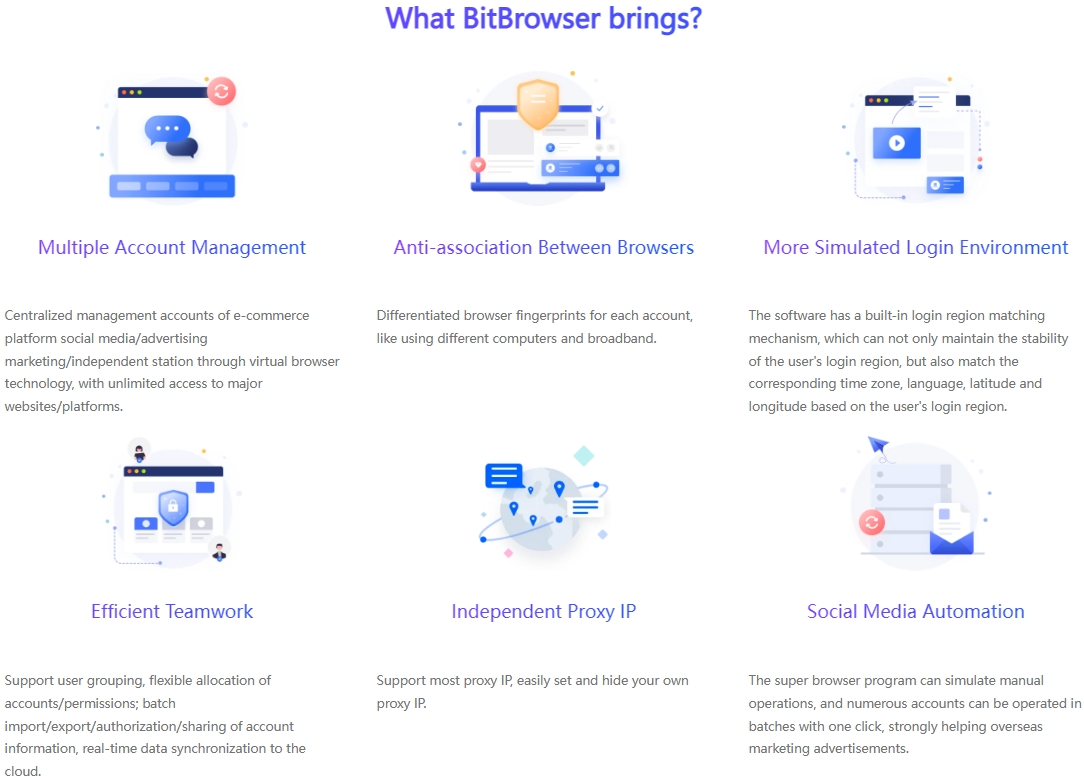
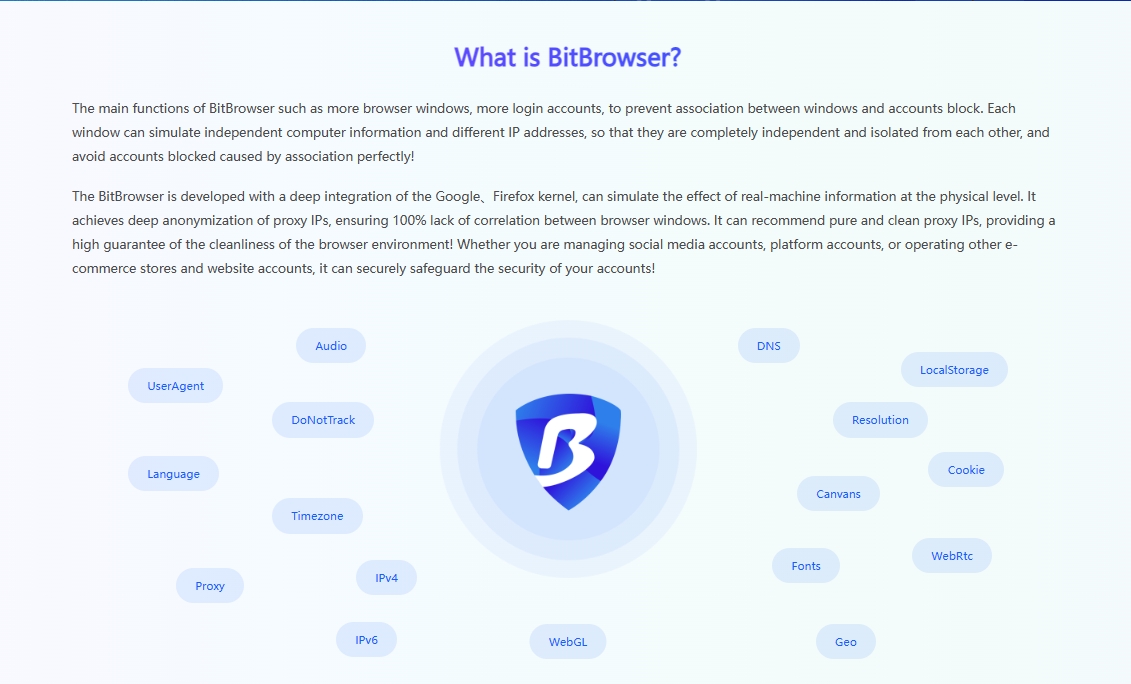
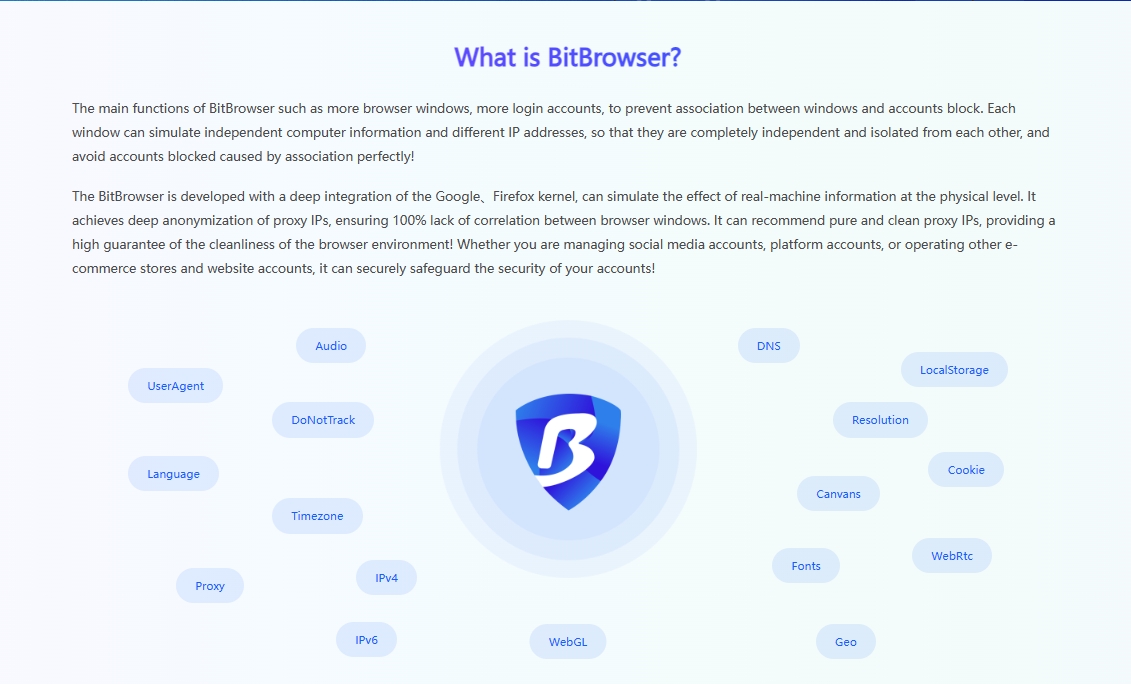
BitBrowser Anti - Detect
Professional
- Messages
- 377
- Reaction score
- 4
- Points
- 18
Getting the ideal results on Facebook is usually the product of the interaction of multiple factors, not a single element. To break through the current dilemma, we must start from the essence and reconsider and improve the advertising strategy in an all-round way. The following is an in-depth exploration of the poor results of Facebook advertising and a novel solution:

Problem analysis: For a long time, the narrow audience group setting will directly restrict the display scope of the advertisement. Behind this, there may be a superficial understanding of the target market or too limited positioning strategy.
Introducing intelligent screening technology: With the help of Facebook's advanced intelligent screening system, such as "Similar Audiences", more potential users with similar interests and behavioral habits are mined based on existing customer data.
Multi-level integrated positioning: Not only relying on basic attributes such as age and gender, but also integrating multiple information such as interests, behavioral patterns, and geographic locations to create a more three-dimensional and rich audience image.
Continuously optimize and test: Regularly evaluate the effectiveness of audience positioning, and use A/B testing to continuously adjust and improve positioning strategies.

Problem analysis: Advertising content that violates regulations or lacks appeal is another important factor that leads to unsatisfactory advertising results. Facebook's strict review standards and high standards for creativity make many advertisers feel timid.
In-depth grasp of platform rules: Frequently study Facebook's advertising policies and best practices to ensure that advertising content is both compliant with regulations and creative.
Visual and emotional integration: Carefully design high-quality, eye-catching visual materials, while incorporating emotional elements to arouse users' resonance and enthusiasm for participation.
Storytelling: Use storytelling marketing methods to tell brand stories or product advantages in the form of videos or graphics to strengthen the memory points and communication capabilities of advertisements.
Problem analysis: Low interactivity and participation often indicate that the advertisement fails to effectively attract the attention of the target audience.
Innovative interactive advertising: Use innovative interactive forms such as carousels and sliding videos to increase opportunities for users to interact with advertisements.
Launch social media challenges: Launch social media challenges related to advertising content to encourage users to participate and share, creating a viral effect.
Establish a reward mechanism: Set participation rewards, such as coupons, lucky draws, etc., to encourage users to interact with ads.
Problem analysis: Improper or too low budget allocation will limit the optimization space and display frequency of ads.
Use smart budget allocation mode: Use Facebook's automatic bidding function to dynamically adjust budget allocation based on advertising performance to ensure efficient use of funds.
Phase-based delivery: According to the product life cycle and marketing goals, formulate a phased delivery strategy, such as increasing investment in the new product launch stage, and focusing on maintaining brand image in the stable period.
Continuous monitoring and adjustment: Regularly monitor advertising performance data, such as click-through rate, conversion rate, etc., and adjust budgets and delivery strategies in a timely manner based on data feedback.
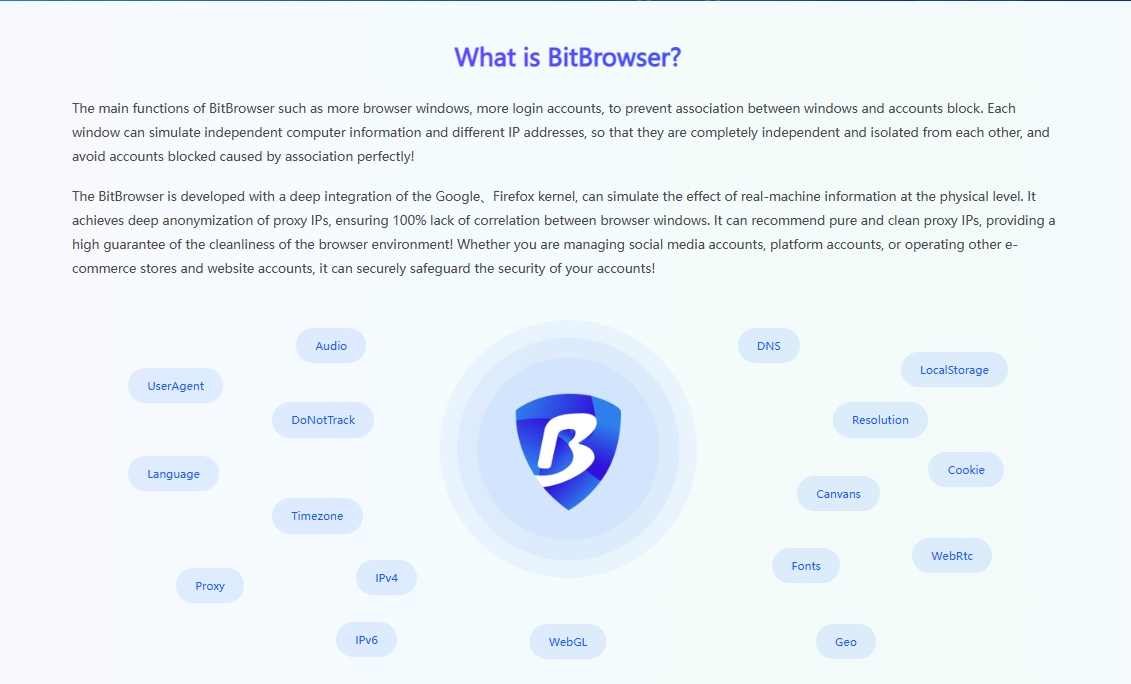
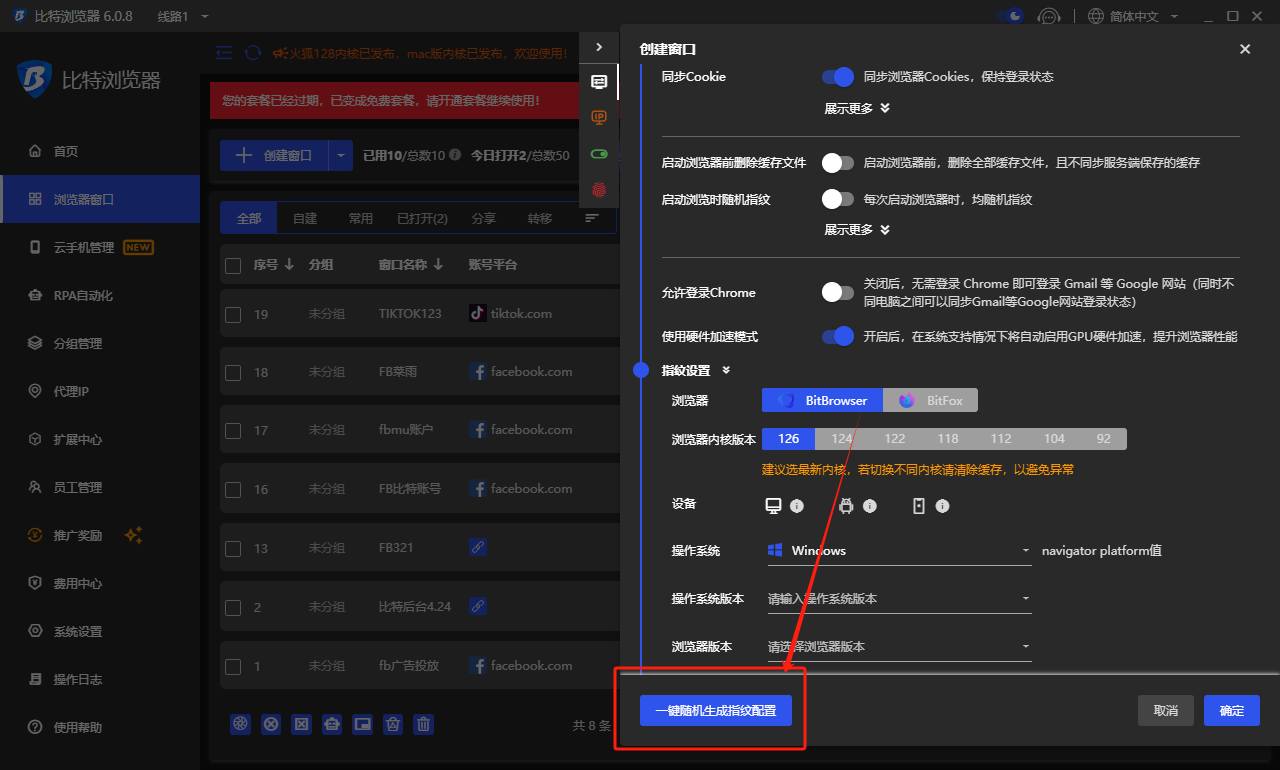
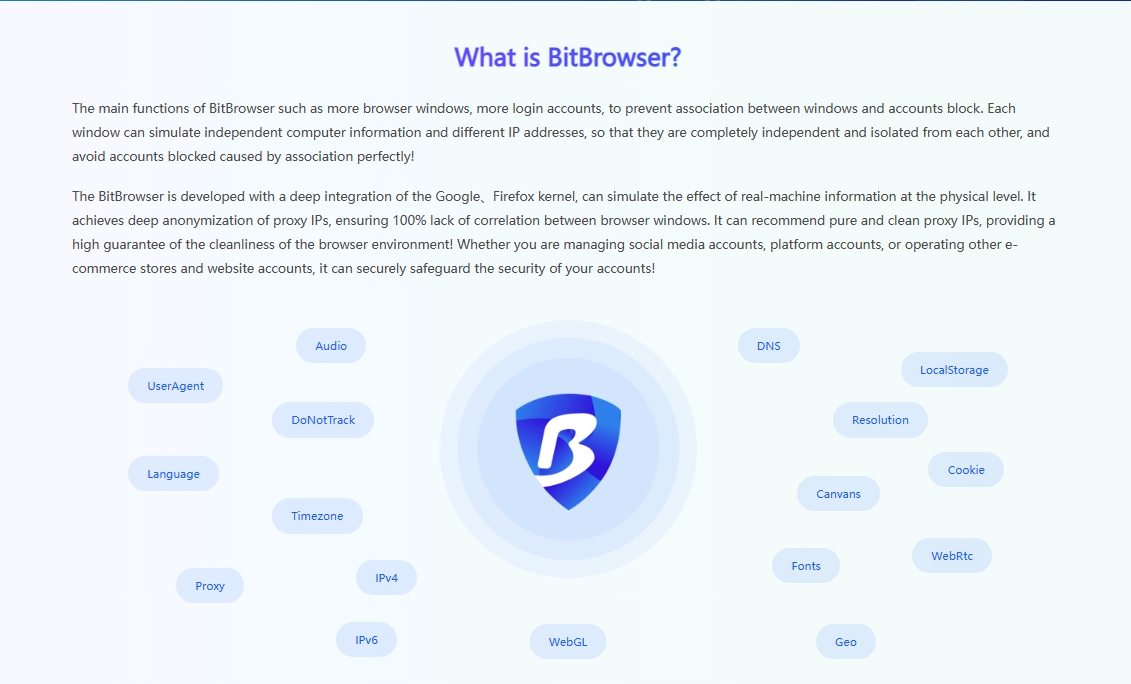
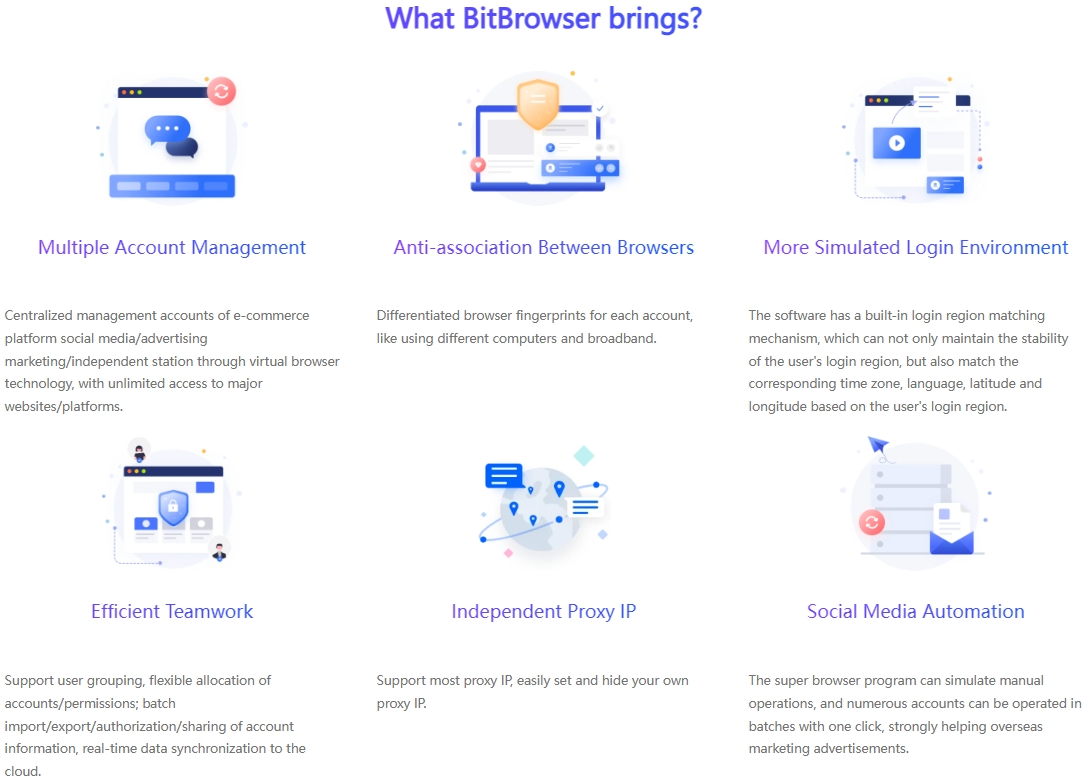
In this era of digital marketing, for many advertisers, how to properly manage and ensure the security and efficient operation of multiple advertising accounts is a difficult task, especially on social platforms like Facebook that have attracted global attention. The introduction of top browser fingerprint camouflage technology solutions such as BitBrowser has undoubtedly brought subversive changes to advertising operation strategies.
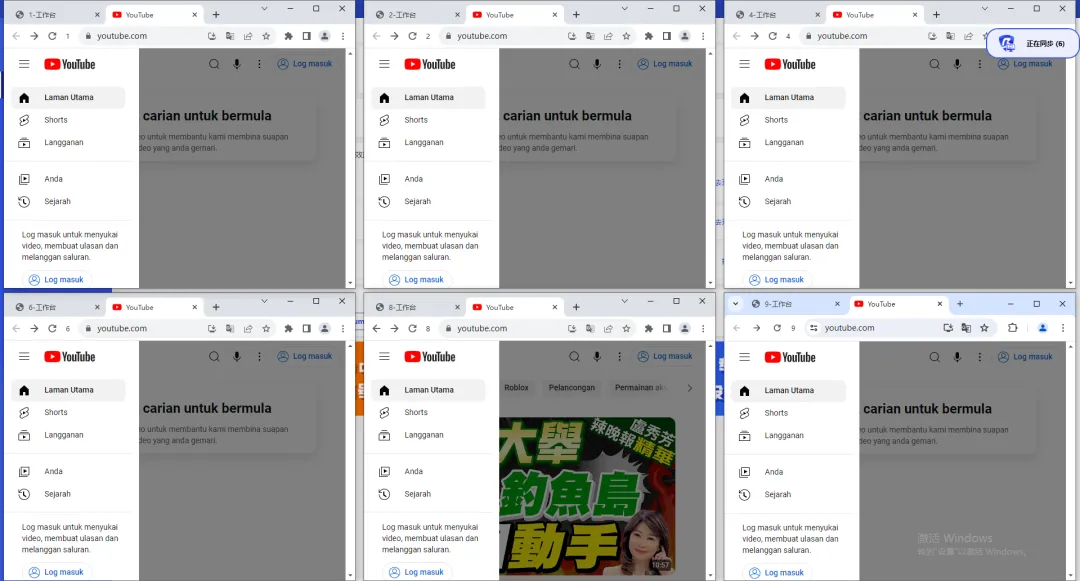
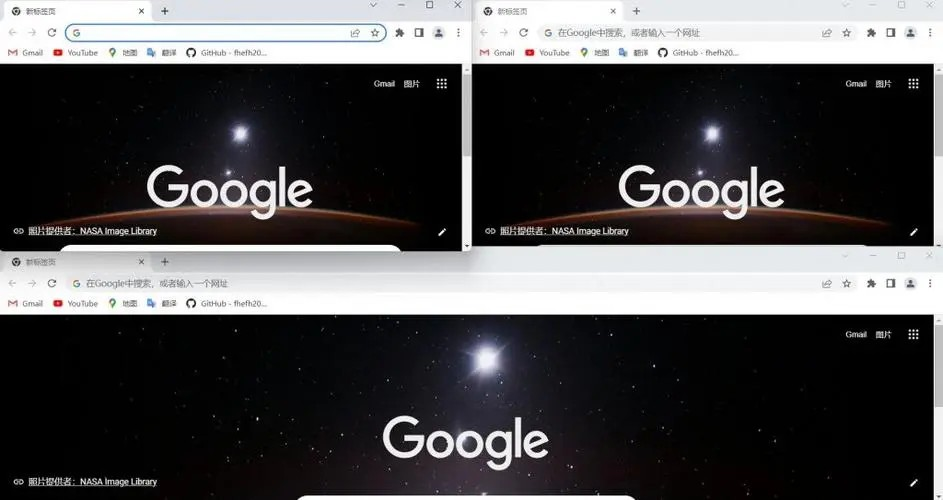
BitBrowser is not an ordinary tool, but a solid shield for advertising accounts. With its unique browser fingerprint isolation method, it creates a unique and distinctive digital identity for each advertising account. Even if it is operated on the same physical device, it can successfully confuse platforms such as Facebook, making them mistakenly believe that each account is accessed by different users through different devices, thereby successfully avoiding the risks brought by account association, allowing advertisers' many accounts to run unimpeded in a stable and secure environment.
In addition to its powerful account isolation features, BitBrowser also integrates cutting-edge automated RPA technology, bringing advertisers an unimaginable automated operation experience. Whether it is automatically pushing high-quality content, or performing precise interactive operations (such as likes and comments), or even daily maintenance of the account, it can be easily controlled. This not only significantly improves work efficiency, but also enhances the credibility and activity of the account on platforms such as Facebook through a series of continuous and natural user behaviors, greatly reducing the possibility of the account being banned.
In 2024, as the competition in the field of digital marketing becomes increasingly fierce, how to achieve accurate and efficient advertising on Facebook has become a key issue that advertisers need to solve urgently. With the help of BitBrowser, advertisers can successfully achieve cross-platform advertising management and optimization goals. Whether it is creative advertising aimed at increasing brand awareness or promotional activities aimed at promoting product sales, BitBrowser can help advertisers maintain a unified brand image and marketing strategy on the Facebook platform, while ensuring that each advertising account can operate in a safe and efficient state, completely eliminating the potential risk of account blocking.
To improve the effectiveness of Facebook advertising, advertisers need to go all out in terms of precise positioning, creative content, interactive strategies, and budget optimization. Only by continuous learning, testing and adjustment, and continuous optimization of advertising strategies, can we stand out in the fiercely competitive market and maximize the value of advertising. At the same time, maintaining a keen sense of the market and users and flexibly responding to various changes and challenges are also the core elements for advertisers to succeed on the Facebook platform. BitBrowser provides users with the possibility of using multiple accounts for Facebook marketing. Download BitBrowser now and get 10 permanent free windows immediately.

1. Accurate positioning, expand the scope of the audience
Problem analysis: For a long time, the narrow audience group setting will directly restrict the display scope of the advertisement. Behind this, there may be a superficial understanding of the target market or too limited positioning strategy.
Innovative solution:
Introducing intelligent screening technology: With the help of Facebook's advanced intelligent screening system, such as "Similar Audiences", more potential users with similar interests and behavioral habits are mined based on existing customer data.
Multi-level integrated positioning: Not only relying on basic attributes such as age and gender, but also integrating multiple information such as interests, behavioral patterns, and geographic locations to create a more three-dimensional and rich audience image.
Continuously optimize and test: Regularly evaluate the effectiveness of audience positioning, and use A/B testing to continuously adjust and improve positioning strategies.
2. Content first, follow the rules and innovate

Problem analysis: Advertising content that violates regulations or lacks appeal is another important factor that leads to unsatisfactory advertising results. Facebook's strict review standards and high standards for creativity make many advertisers feel timid.
Innovative solutions:
In-depth grasp of platform rules: Frequently study Facebook's advertising policies and best practices to ensure that advertising content is both compliant with regulations and creative.
Visual and emotional integration: Carefully design high-quality, eye-catching visual materials, while incorporating emotional elements to arouse users' resonance and enthusiasm for participation.
Storytelling: Use storytelling marketing methods to tell brand stories or product advantages in the form of videos or graphics to strengthen the memory points and communication capabilities of advertisements.
3. Enhance interaction and stimulate user participation
Problem analysis: Low interactivity and participation often indicate that the advertisement fails to effectively attract the attention of the target audience.
Innovative solutions:
Innovative interactive advertising: Use innovative interactive forms such as carousels and sliding videos to increase opportunities for users to interact with advertisements.
Launch social media challenges: Launch social media challenges related to advertising content to encourage users to participate and share, creating a viral effect.
Establish a reward mechanism: Set participation rewards, such as coupons, lucky draws, etc., to encourage users to interact with ads.
4, flexible budget, optimized delivery strategy
Problem analysis: Improper or too low budget allocation will limit the optimization space and display frequency of ads.
Innovative solutions:
Use smart budget allocation mode: Use Facebook's automatic bidding function to dynamically adjust budget allocation based on advertising performance to ensure efficient use of funds.
Phase-based delivery: According to the product life cycle and marketing goals, formulate a phased delivery strategy, such as increasing investment in the new product launch stage, and focusing on maintaining brand image in the stable period.
Continuous monitoring and adjustment: Regularly monitor advertising performance data, such as click-through rate, conversion rate, etc., and adjust budgets and delivery strategies in a timely manner based on data feedback.
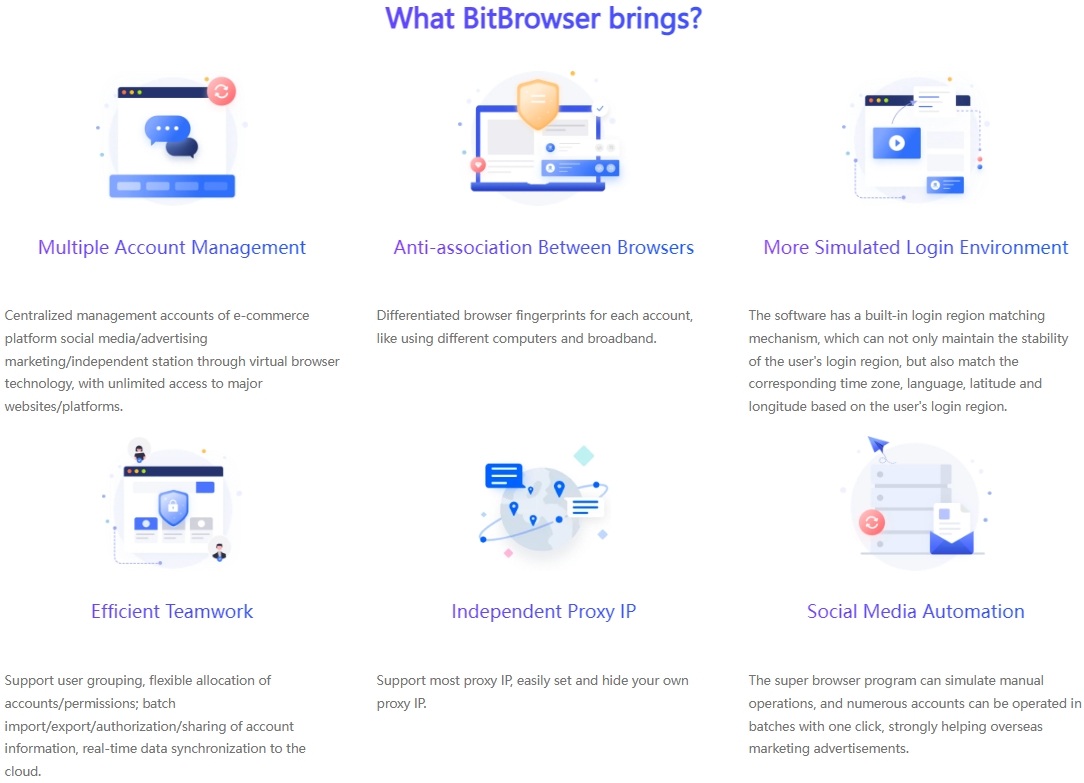
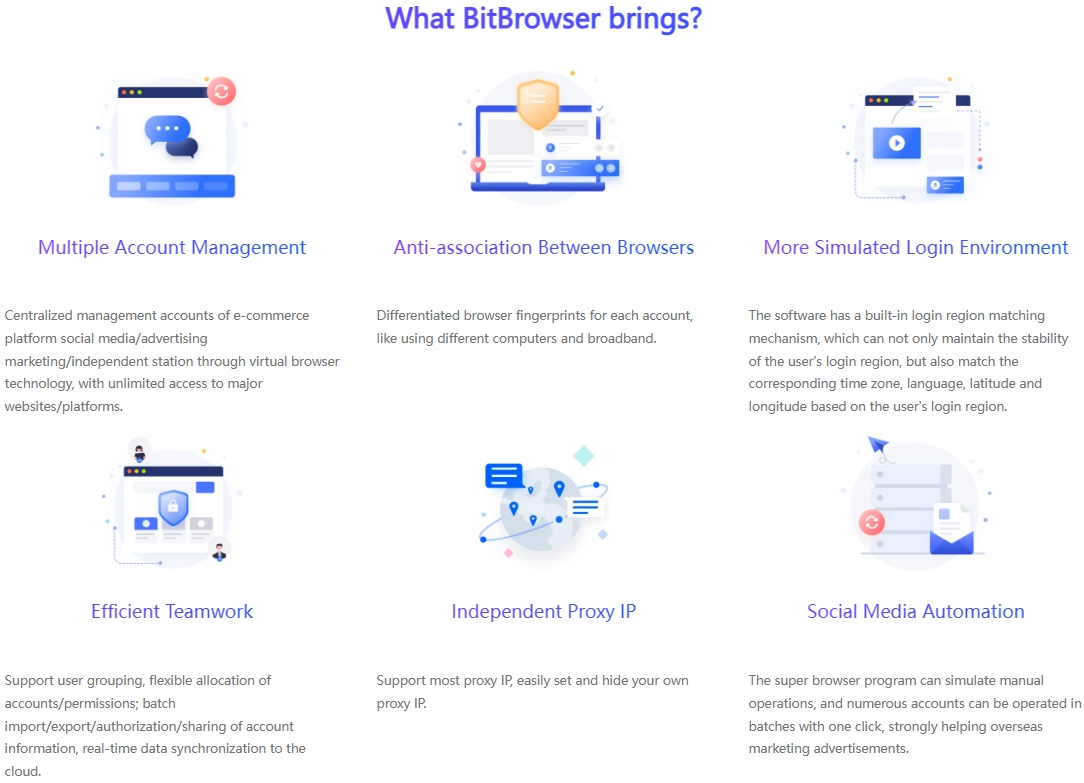
5. BitBrowser Multi-Account Solution
In this era of digital marketing, for many advertisers, how to properly manage and ensure the security and efficient operation of multiple advertising accounts is a difficult task, especially on social platforms like Facebook that have attracted global attention. The introduction of top browser fingerprint camouflage technology solutions such as BitBrowser has undoubtedly brought subversive changes to advertising operation strategies.
BitBrowser that breaks through the limitations of account management
BitBrowser is not an ordinary tool, but a solid shield for advertising accounts. With its unique browser fingerprint isolation method, it creates a unique and distinctive digital identity for each advertising account. Even if it is operated on the same physical device, it can successfully confuse platforms such as Facebook, making them mistakenly believe that each account is accessed by different users through different devices, thereby successfully avoiding the risks brought by account association, allowing advertisers' many accounts to run unimpeded in a stable and secure environment.
BitBrowser's all-round services

In addition to its powerful account isolation features, BitBrowser also integrates cutting-edge automated RPA technology, bringing advertisers an unimaginable automated operation experience. Whether it is automatically pushing high-quality content, or performing precise interactive operations (such as likes and comments), or even daily maintenance of the account, it can be easily controlled. This not only significantly improves work efficiency, but also enhances the credibility and activity of the account on platforms such as Facebook through a series of continuous and natural user behaviors, greatly reducing the possibility of the account being banned.
Multi-platform collaborative development promoted by BitBrowser
In 2024, as the competition in the field of digital marketing becomes increasingly fierce, how to achieve accurate and efficient advertising on Facebook has become a key issue that advertisers need to solve urgently. With the help of BitBrowser, advertisers can successfully achieve cross-platform advertising management and optimization goals. Whether it is creative advertising aimed at increasing brand awareness or promotional activities aimed at promoting product sales, BitBrowser can help advertisers maintain a unified brand image and marketing strategy on the Facebook platform, while ensuring that each advertising account can operate in a safe and efficient state, completely eliminating the potential risk of account blocking.
Summary:
To improve the effectiveness of Facebook advertising, advertisers need to go all out in terms of precise positioning, creative content, interactive strategies, and budget optimization. Only by continuous learning, testing and adjustment, and continuous optimization of advertising strategies, can we stand out in the fiercely competitive market and maximize the value of advertising. At the same time, maintaining a keen sense of the market and users and flexibly responding to various changes and challenges are also the core elements for advertisers to succeed on the Facebook platform. BitBrowser provides users with the possibility of using multiple accounts for Facebook marketing. Download BitBrowser now and get 10 permanent free windows immediately.