Reddit, like a vast starry sky across the digital sky, is not just a gathering place for information, but a wonderful field where passion and creativity blend and coexist. Here, users are not only content creators, but also a powerful driving force to lead cultural trends. With their unique vision and infinite creativity, they write legendary chapters about interests, knowledge and spiritual resonance.
Origin and Evolution of Reddit
Back in 2005, two outstanding alumni of the University of Virginia, Alexis Ohanian and Steve Hoffman, worked together to outline a magnificent dream: to build a bridge connecting wisdom and joy. At first, it was just a warm harbor for sharing anecdotes and stimulating heated discussions, but as time went by, Reddit quietly transformed and was incorporated into Advance Publications in 2011, like a dazzling new star, thus gaining unprecedented broad development space.
The Bloom of Digital Miracles
Today, Reddit attracts more than 50 million active explorers every day, who travel between hundreds of thousands of active "galaxies" (i.e., Subreddits). Each "galaxy" revolves around a specific theme or interest, covering everything from the deep mysteries of the universe to the trivial details of daily life. In the past three months, this digital starry sky has received nearly 7 billion visits, with an average of 2.3 billion visits per month. Its influence ranks 16th in the world, and in the United States, it has successfully jumped to 8th, becoming a shining pearl that cannot be ignored in the Internet landscape.
User portrait
In this vast digital world, the portrait of the user group presents a colorful picture. Young adults aged 18 to 34 have become the backbone, and male users, with nearly twice the number of female users, show their unique vitality and charm on this platform. This is not a simple listing of numbers, but a vivid portrayal of the young generation's pursuit of new knowledge and courageous self-expression.
Subreddit: Interest as a carrier
Subreddit, as a unique cultural carrier of Reddit, is full of enthusiasm and persistence for specific topics. Here, users are not only passengers, but also captains who control the direction. They work together to formulate the rules of navigation and protect the purity and vitality of the community. From in-depth professional discussions to relaxing and pleasant entertainment, from rigorous professional exchanges to warm emotional resonance, Subreddit attracts like-minded partners with its unique charm to sail to the unknown vast interstellar together.
From Reddit to infinite possibilities
Like social platforms such as Twitter, Reddit accepts diverse expressions including 18+ content with its open and inclusive mind. However, it cleverly grasps the balance between freedom and responsibility, and ensures that every explorer can fly freely in a safe and worry-free environment through fuzzy processing and warning labels. At the same time, Reddit has also become a fertile soil for traffic monetization. Users use clever strategies to divert traffic on the platform to other platforms such as Telegram and OnlyFans, realizing the maximum expansion of value.
Navigating Reddit
For new explorers, the vast world of Reddit may seem a bit complicated. But don't worry, the platform provides a variety of navigation methods to help you easily find the precious treasures in your heart. The popular feed brings together the latest hot topics, and the new feature displays posts in chronological order so that you will not miss any fresh information. For registered users, the best feed is a personalized and exclusive universe carefully crafted for you based on your interests and personal preferences.
Account wisdom: building a strong fortress of trust
In the vast universe of Reddit, an account with rich karma and active history is like a well-equipped exploration ship, which can make you more confident and calm in your journey of exploration. Therefore, when choosing or creating an account, be sure to carefully consider its accumulation of karma and activity to ensure your smooth journey.
When discussing Reddit account optimization, we must first realize that each account is like a ship sailing in the digital ocean. Its value lies not only in its own construction, but also in how to skillfully control it to attract and retain the audience's attention.
In-depth analysis of excellent account cases
Let's focus on a model account and carefully observe its top posts and profile descriptions. Close interaction with the audience is the key to increasing the attractiveness of an account. Therefore, it is necessary to fully shape your account image and elaborate on your content features, OnlyFans links and any details that highlight your unique charm in the "About" section. Remember, every description is an opportunity to show yourself and make readers feel your professionalism and enthusiasm.
Daily updates
For Reddit, the freshness of content is crucial. Make sure to post content at least once a day and incorporate new elements in each post to keep the audience interested. In the field of adult content, it is your first priority to cleverly set suspense and guidance to turn the audience's attention into action.
Avoid the trap of low-quality accounts
Although buying accounts can save time, the risks should not be ignored. Before buying, be sure to search for usernames on Reddit and avoid any accounts marked as "BotDefense". At the same time, be wary of newly created accounts, especially those in the "banned" or "pending" status, which may hide irreversible risks.
Start from scratch and move forward steadily
If your budget is limited, it is also a good idea to choose to build an account from scratch. Although you may face insufficient traffic and posting restrictions in the early stage, this is also a good opportunity to exercise patience and familiarize yourself with the platform rules. By manually accumulating comment karma and actively participating in community discussions, you will gradually build a solid account foundation.
The unique charm of personal branding
Compared with purchasing an account, building your own account gives you more autonomy. You can freely choose your username and avatar to shape a unique personal brand image. Over time, users will gradually realize that this is your personal space, thus building deep trust and dependence.
Strategies to improve purchased accounts
For purchased accounts, moderately increasing the number of likes can be a short-term improvement strategy. But please remember that excessive operations may bring high costs or even account bans. Therefore, be sure to act with caution and ensure that every operation is within a reasonable range.
Dealing with Reddit account bans
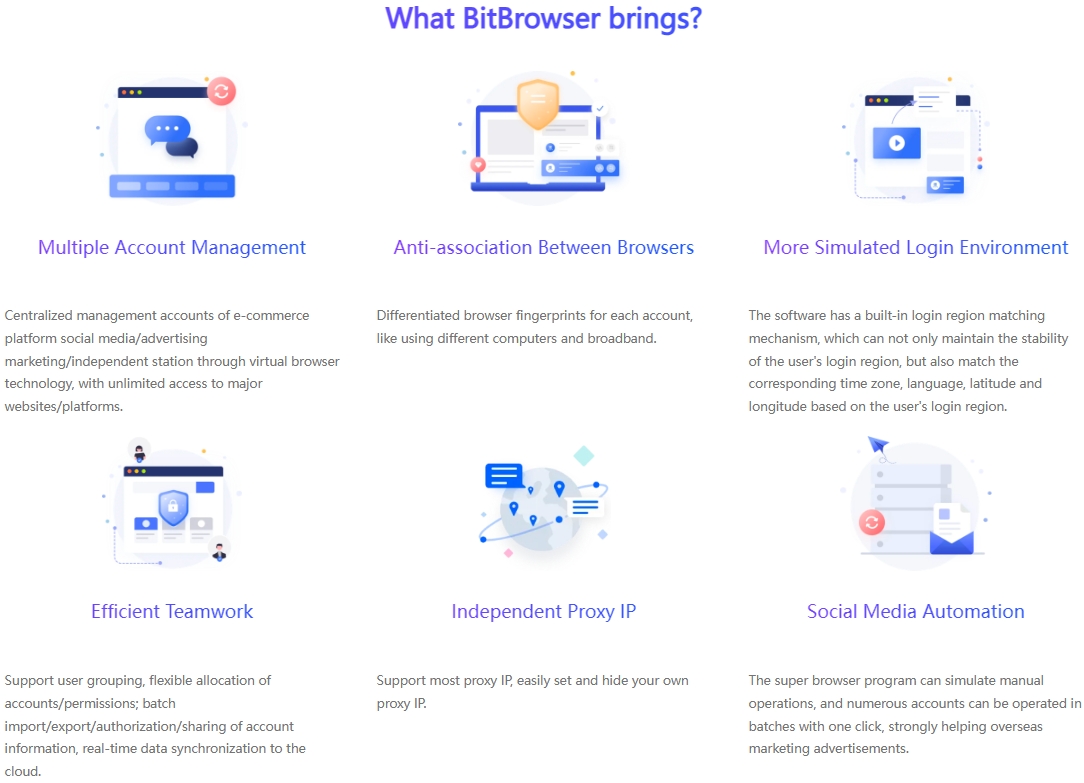
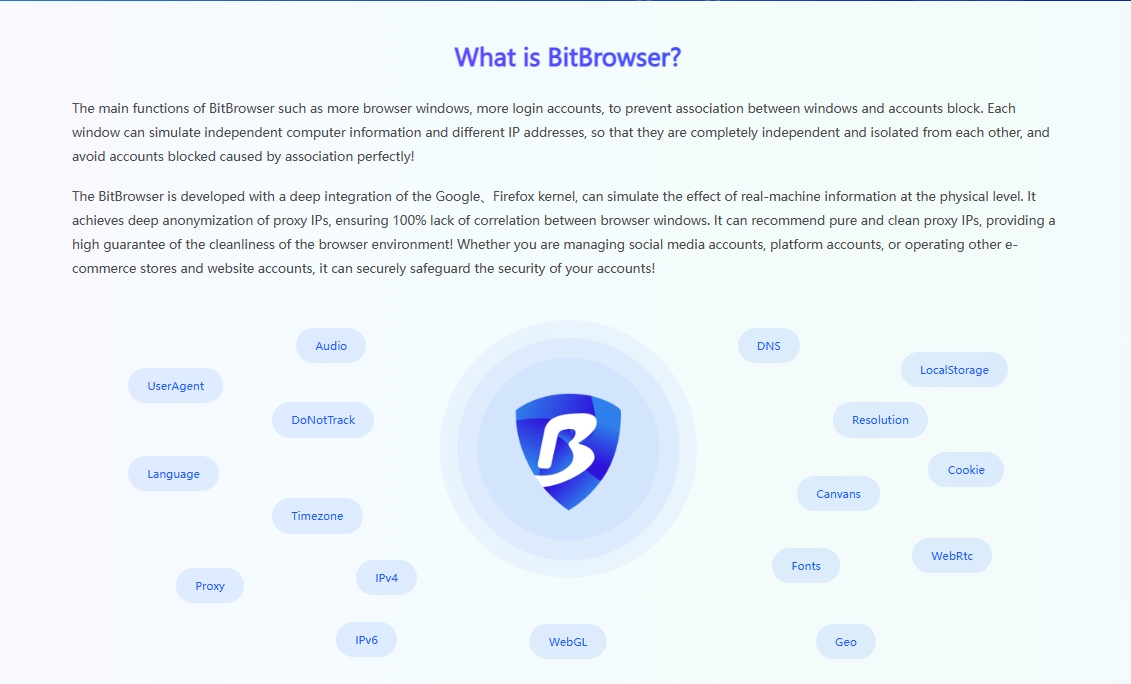
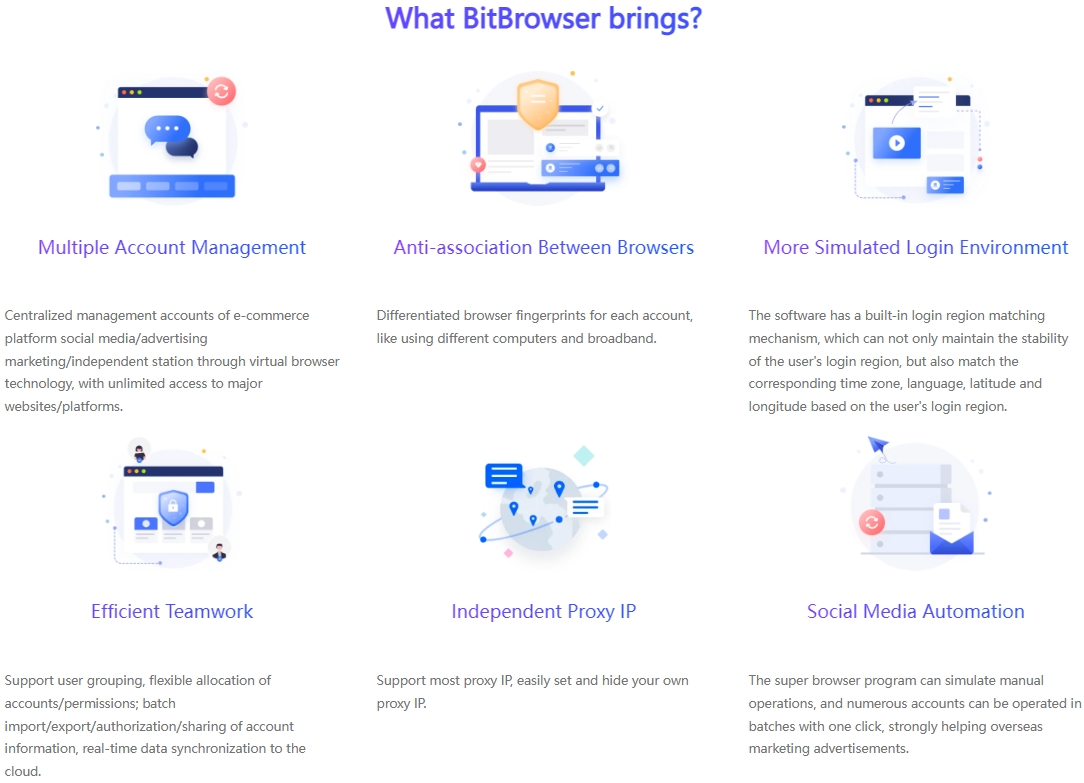
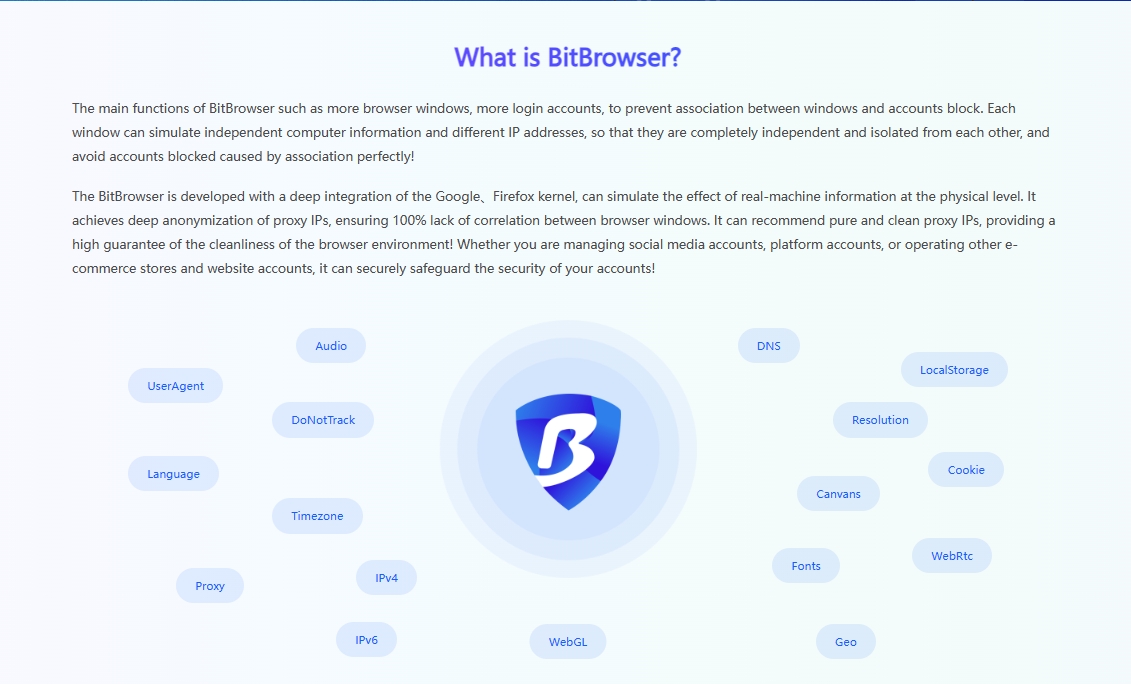
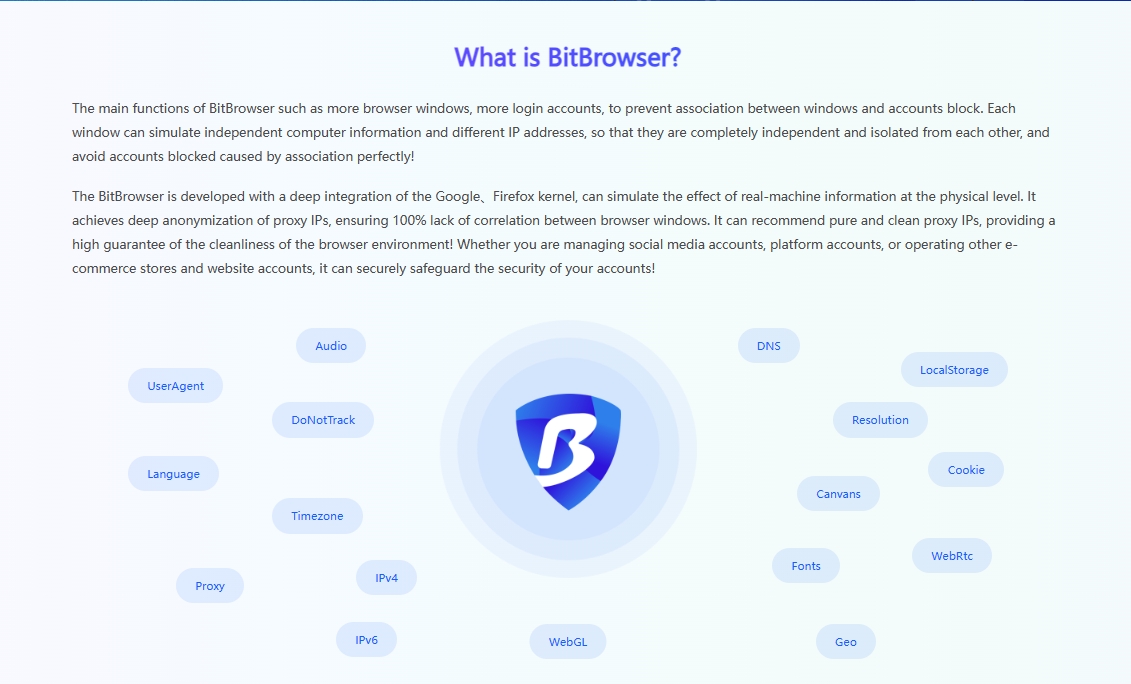
Dealing with Reddit account bans, don't panic too much. By visiting reddit.com/appeals and submitting an appeal, you have the opportunity to let the moderator review your account. Honestly explaining the situation and promising to abide by the platform rules can often win the understanding and support of the moderator. Of course, taking precautions before problems occur in Reddit accounts can better protect account behavior. Marketing on Reddit, a vibrant social platform, especially in situations where multiple accounts need to be operated simultaneously to expand influence, ensuring the independence and security of each account has become a crucial consideration. To this end, the introduction of professional tools such as BitFinger Browser has become a wise choice for cross-border independent station sellers.
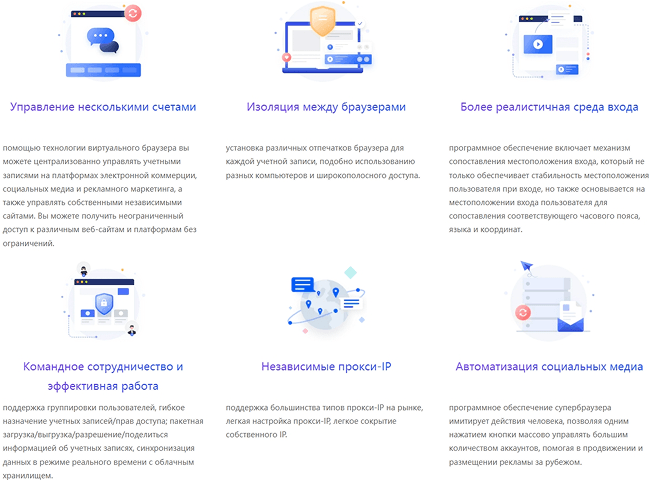
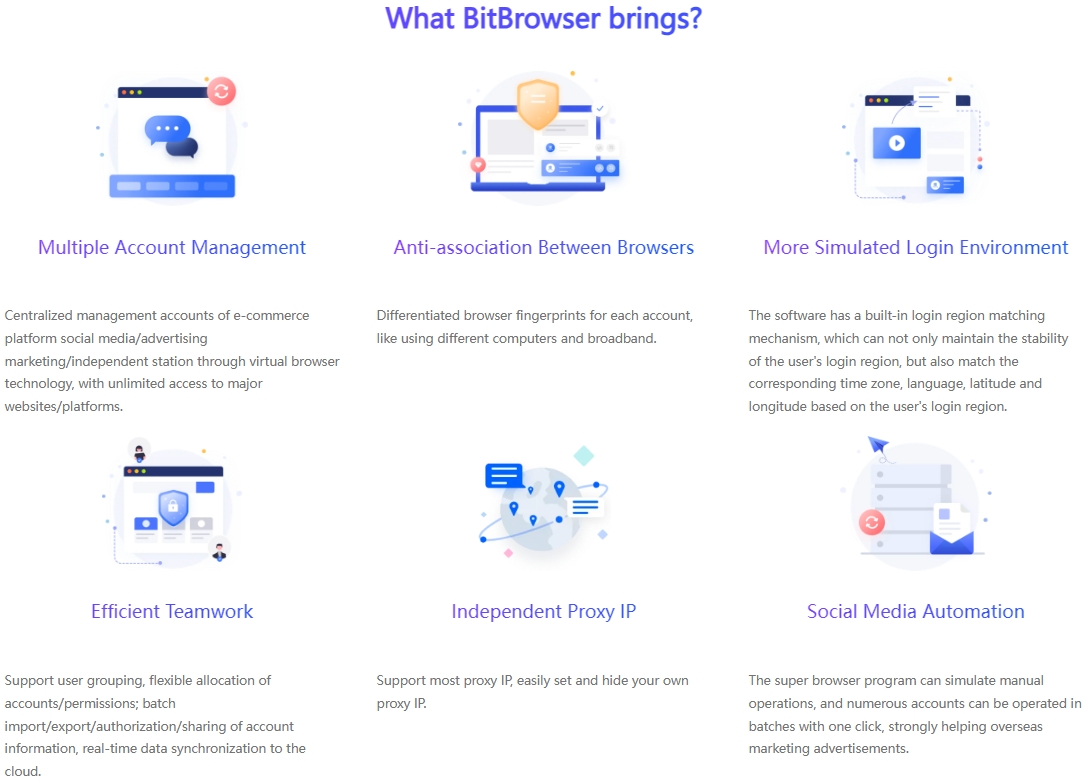
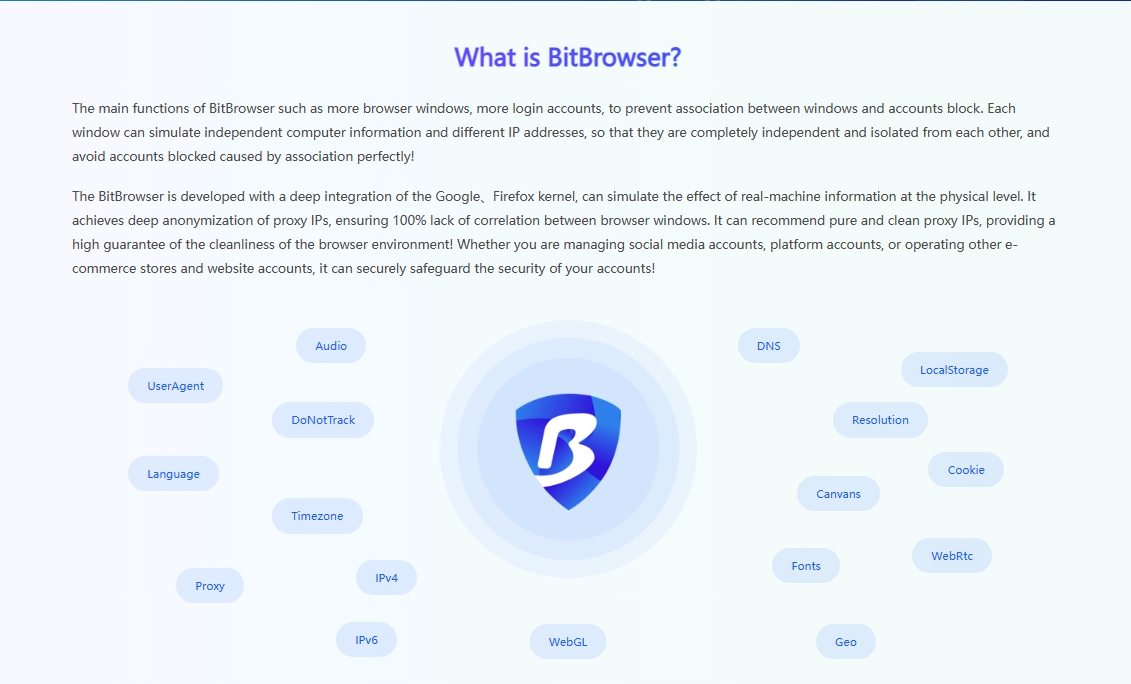
Environmental Isolation: Building a Secure Account Ecosystem
BitFinger Browser Fingerprint Browser creates an independent virtual environment for each Reddit account to ensure that they do not interfere with each other. Each account has its own cookies, cache, and browsing history, just like operating on an independent physical device. This high degree of environmental isolation not only improves the security of the account, but also effectively reduces the risk caused by information leakage or association between accounts.
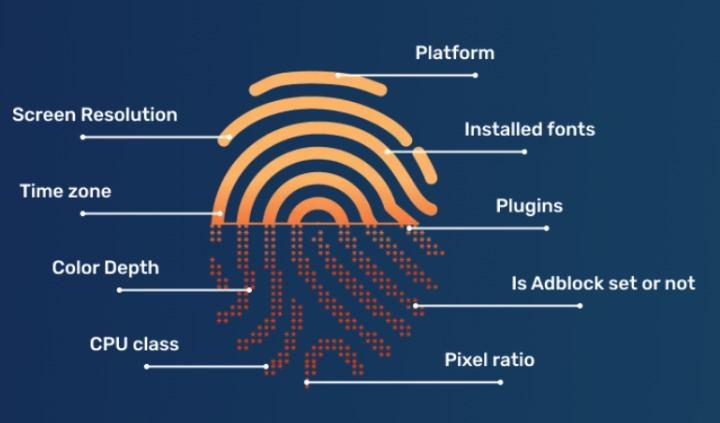
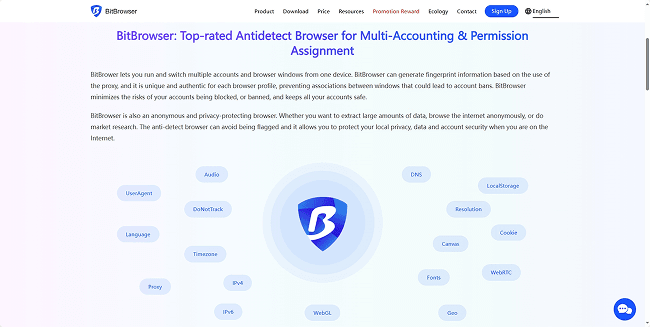
Browser fingerprint disguise: invisible protection, avoid ban
When the device is online, it will leave unique "fingerprint" information, such as operating system, browser version, etc., which is often used by the platform to track and identify users. BitFingerprint Browser provides a powerful browser fingerprint modification function, allowing users to customize these parameters to hide the real device information. In this way, each Reddit account looks like it is accessed from a brand new, independent device in the eyes of the platform, greatly reducing the risk of being identified and banned due to similar fingerprints.
RPA Automation: Double Improvement of Efficiency and Authenticity
For sellers who need to maintain a large number of accounts, BitFingerprint Browser also integrates RPA (Robotic Process Automation) function. This function can automatically handle daily operations such as logging in, posting, browsing, etc., greatly improving work efficiency. At the same time, the RPA automation process simulates the behavior patterns of real users, making account activities more natural, helping to enhance the credibility of the account and further improve marketing effectiveness.
The use of verification and hosting services
In some subreddits, verification is a necessary step before publishing content. Enhancing your account's credibility by uploading verification files will bring you more traffic and trust. At the same time, using hosting services such as Imgur to upload images and platforms such as RedGIF to share videos is also an effective way to improve content quality. Please pay attention to the restrictions on video content in different subreddits.
Summary:
As a vibrant and diverse social platform, Reddit provides users with a broad communication space and rich thematic communities. Since its birth in 2005, it has continued to evolve and become a bridge connecting millions of users around the world. By using the
BitBrowser Fingerprint Browser, cross-border independent station sellers can achieve safer, more efficient and authentic marketing activities on Reddit. Features such as environmental isolation, browser fingerprint camouflage and RPA automation have jointly created an ideal account management platform for sellers, helping them to accurately guide traffic, expand brand influence and maximize business goals on the vast social stage of Reddit.