BitBrowser Anti - Detect
Professional
- Messages
- 381
- Reaction score
- 4
- Points
- 18

Proxy IP has become an important tool for multi-account operation. However, e-commerce people know that if you manage many stores through the same IP address, it is like directly telling Amazon and other platforms that your stores are related, which may cause the stores to be related or even banned. Therefore, it is particularly important to use a proxy IP unlimited browser.
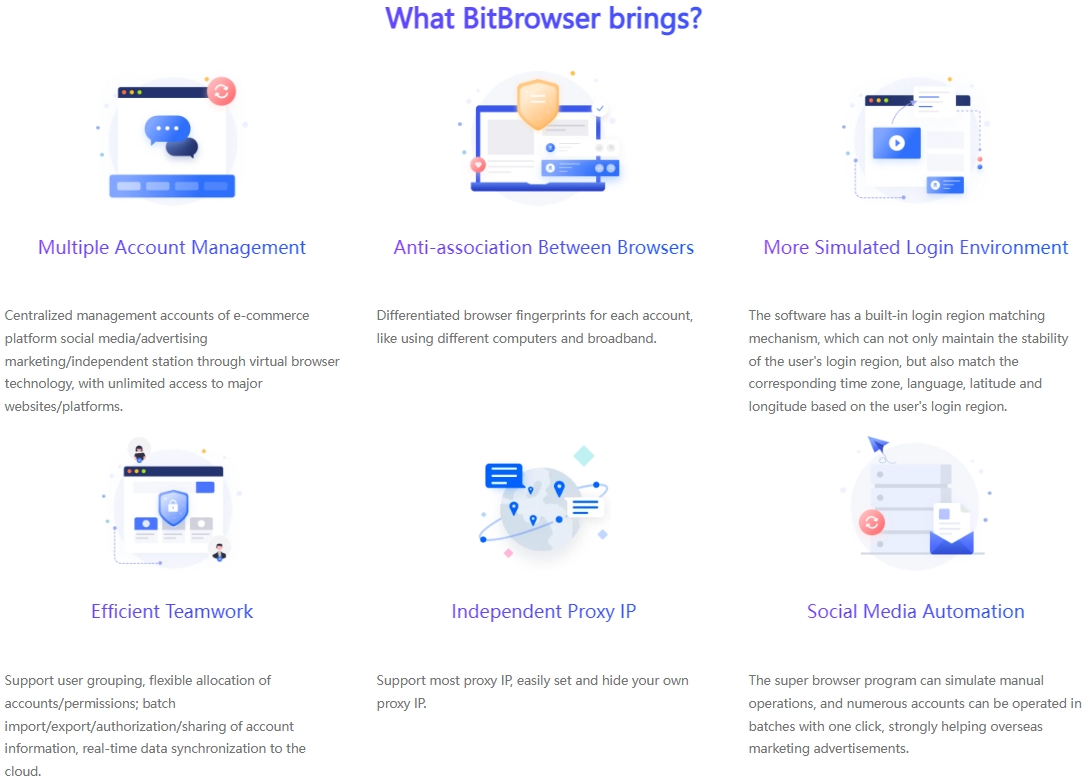
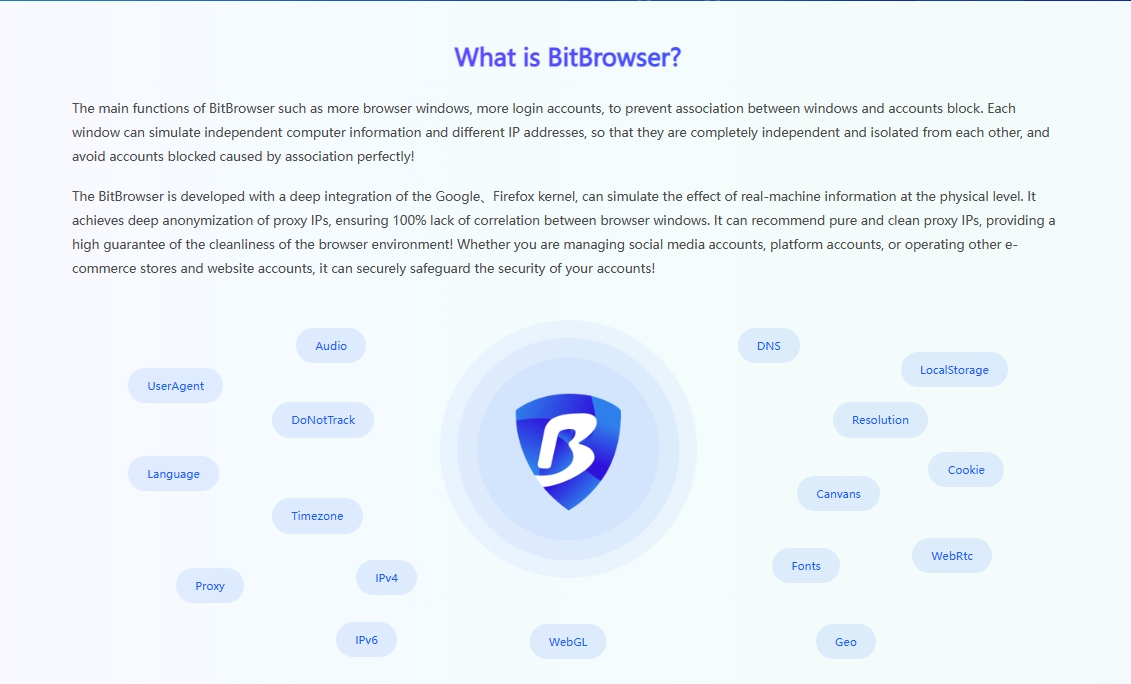
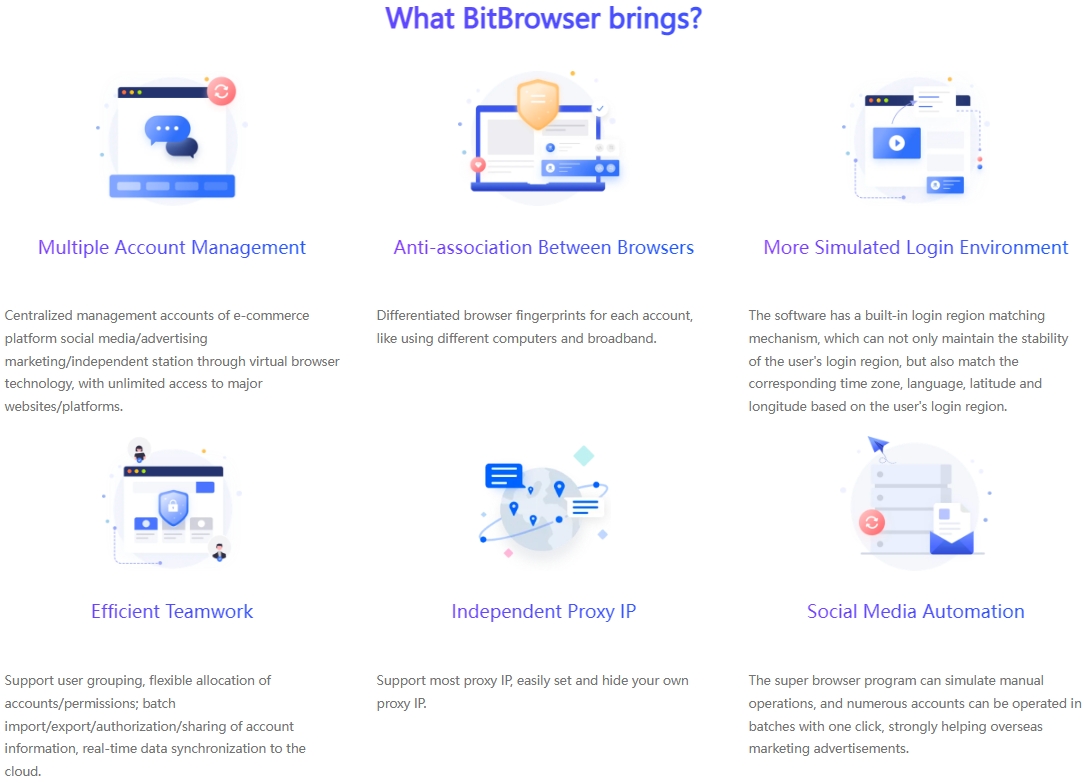
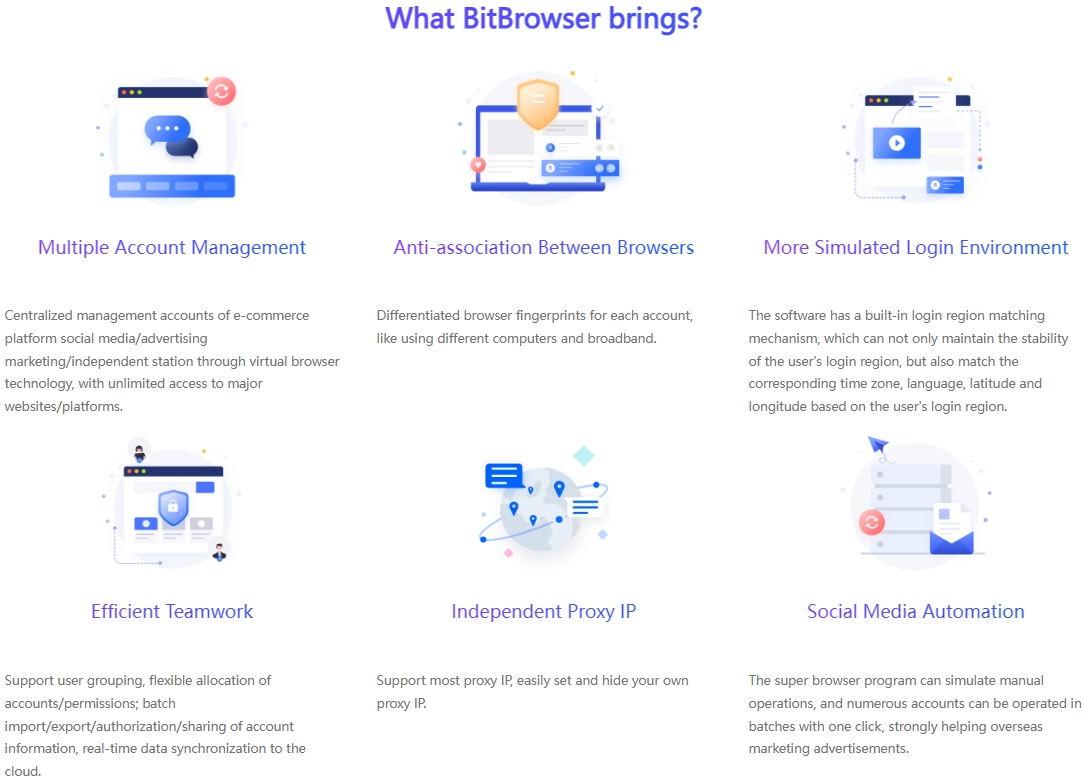
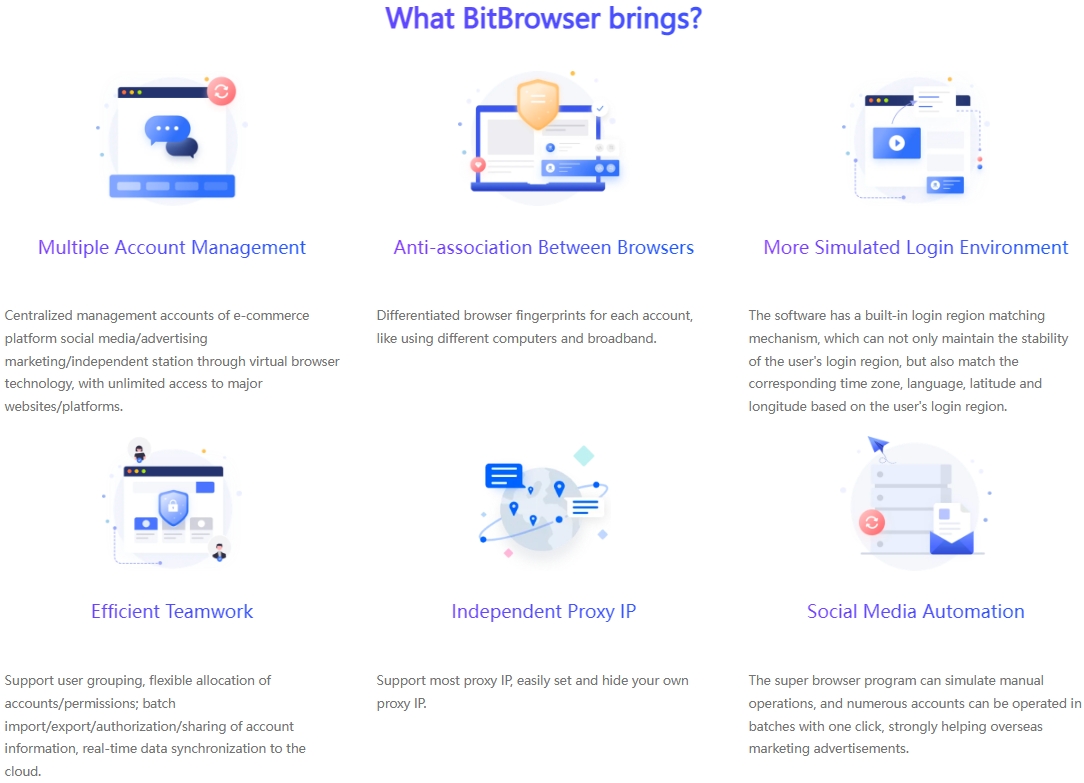
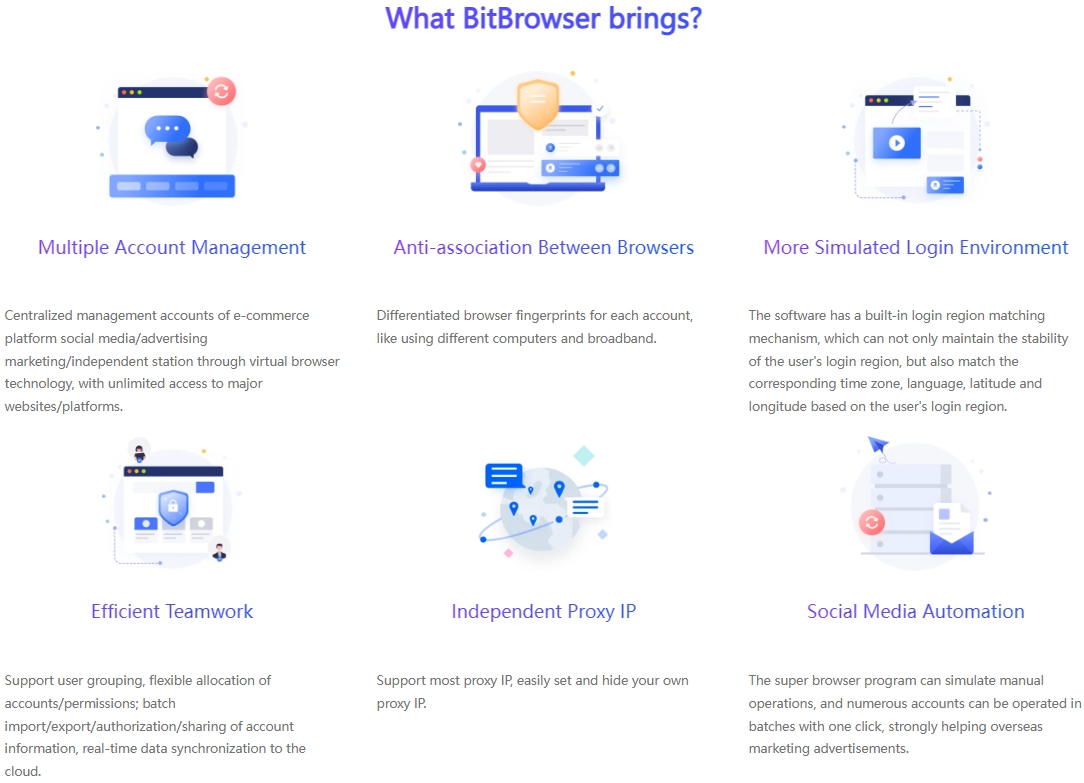
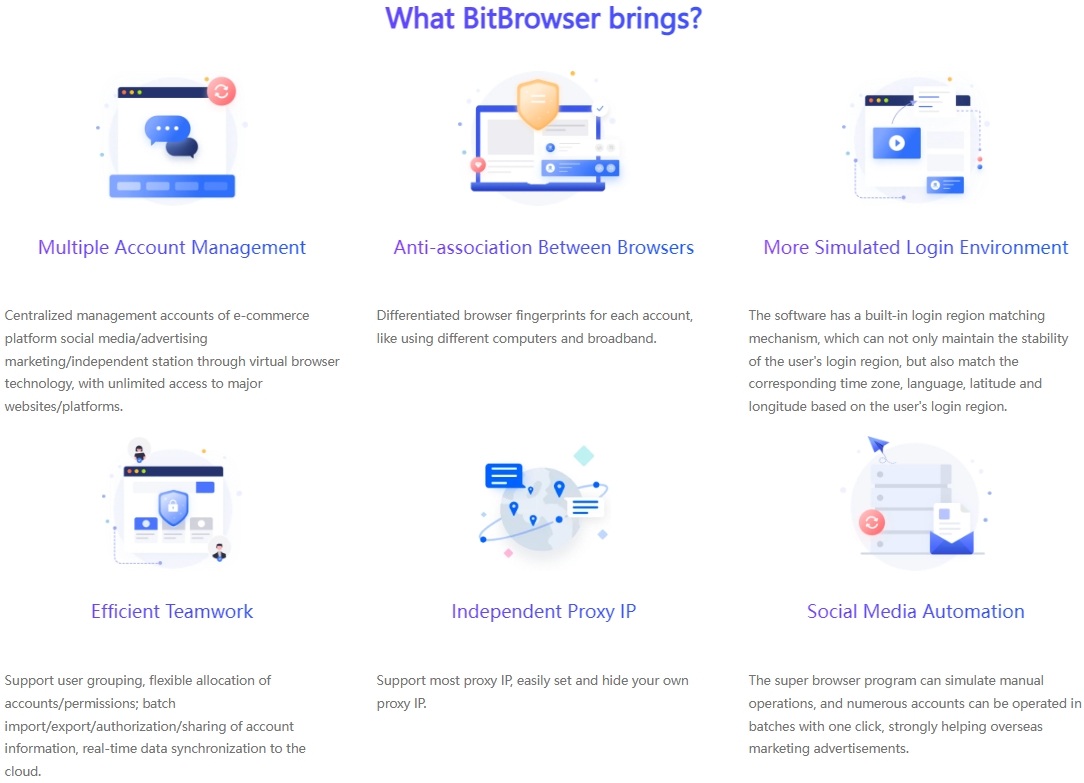
The main functions of the proxy IP unlimited browsers in the current market are gradually showing similar trends. They basically include conventional features such as simulation construction of fingerprint environment, replacement and adjustment of dynamic IP, synchronous operation of multiple windows, setting of RPA automation process, adaptation of a large number of e-commerce plug-ins, collaboration modules between teams, and login control of multiple accounts.
In such a situation, when you choose a suitable proxy IP unlimited browser, the following key points are particularly important:
Security performance evaluation:
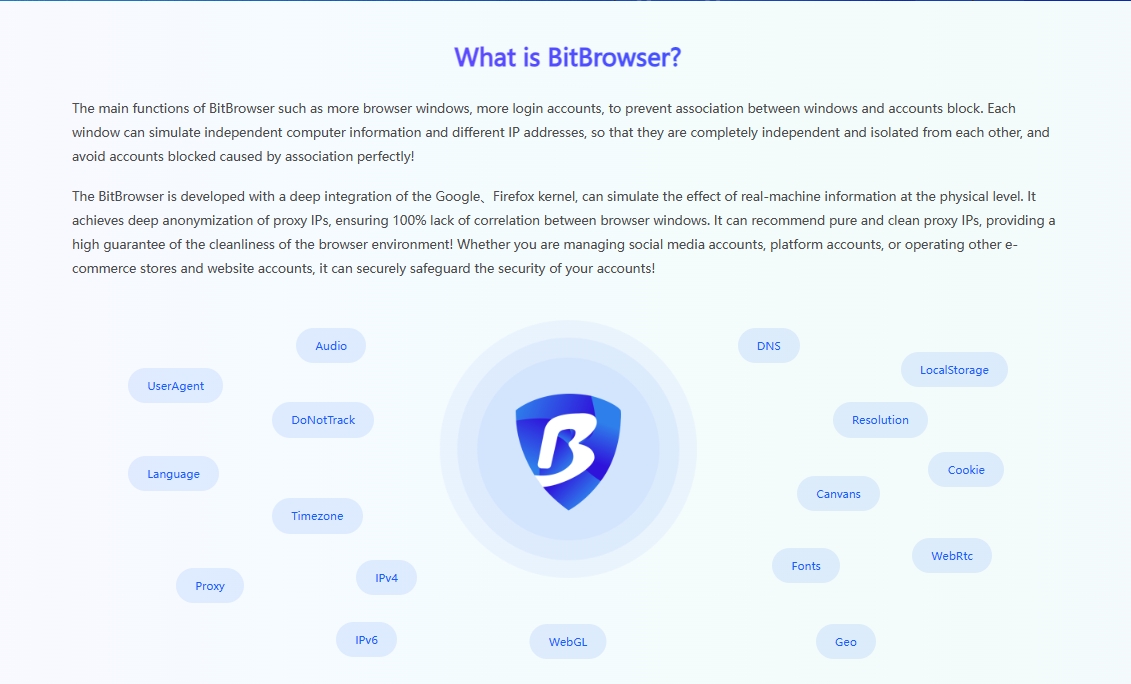
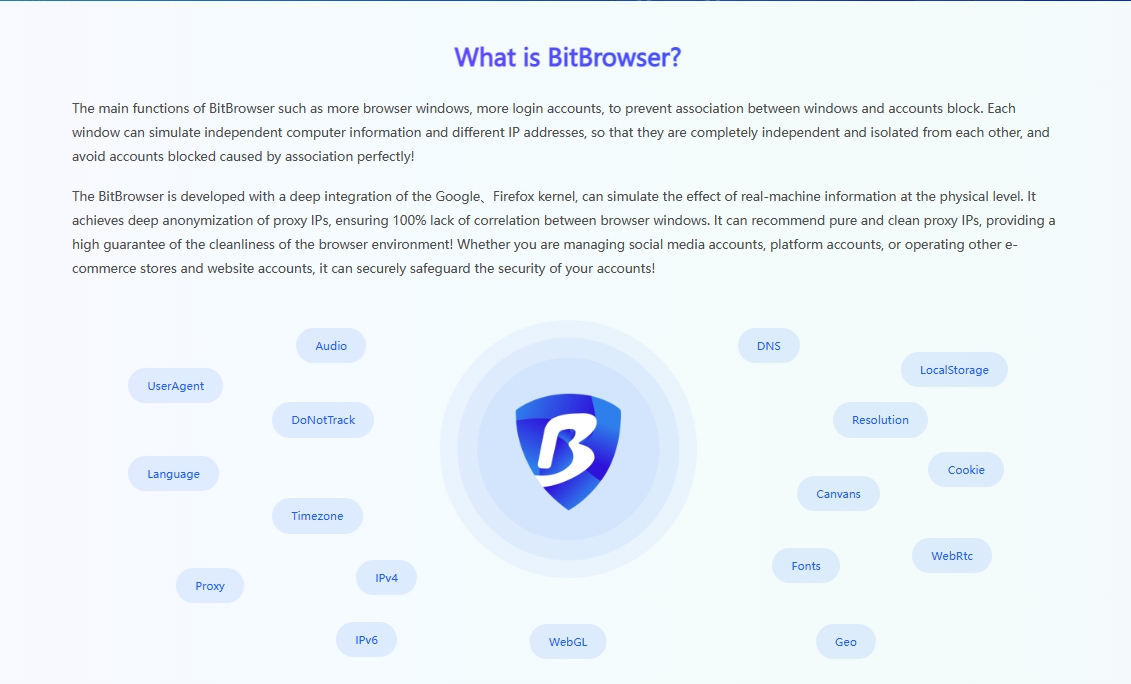
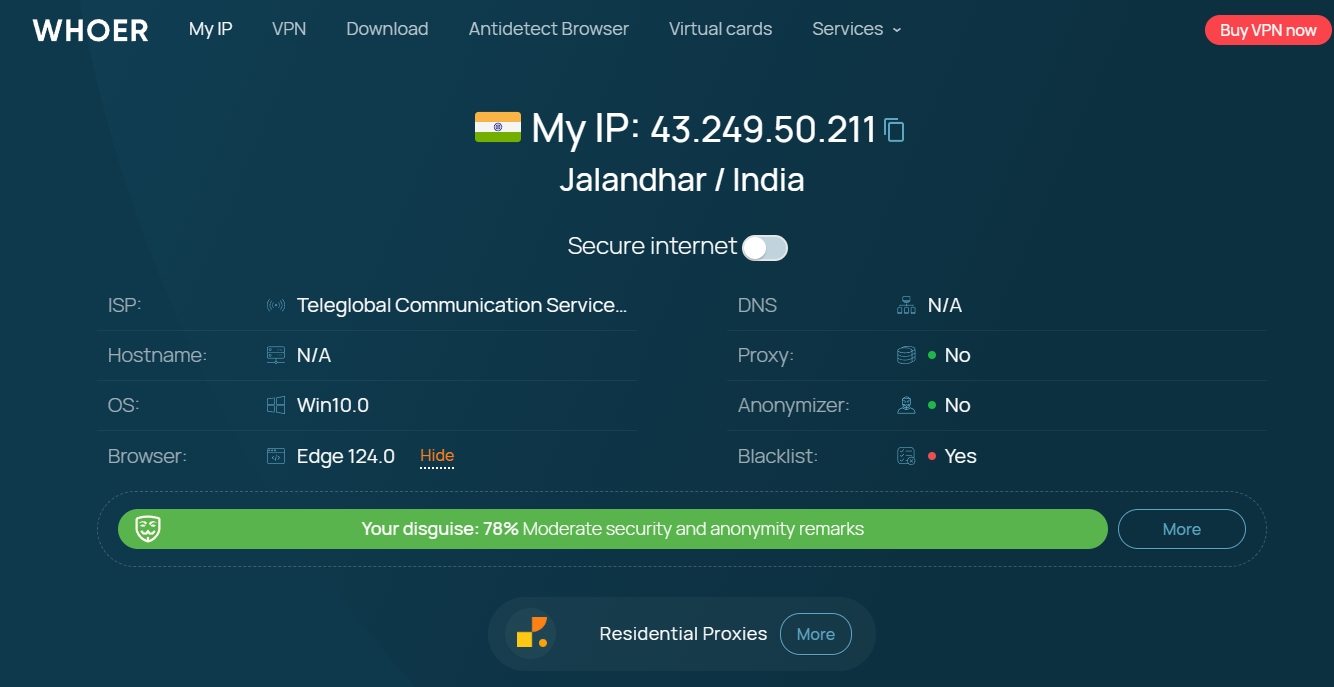
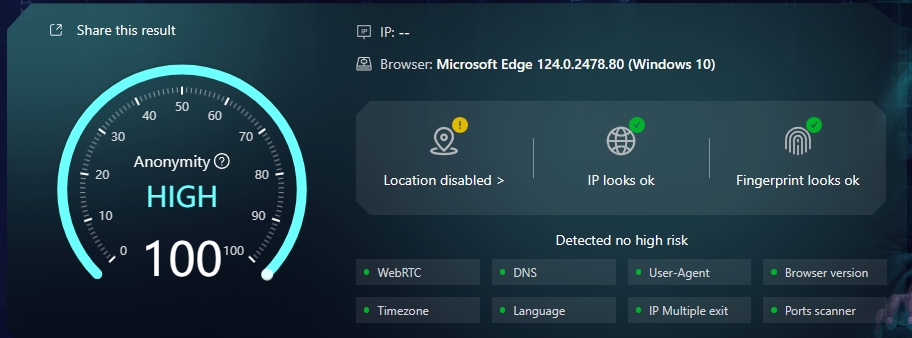
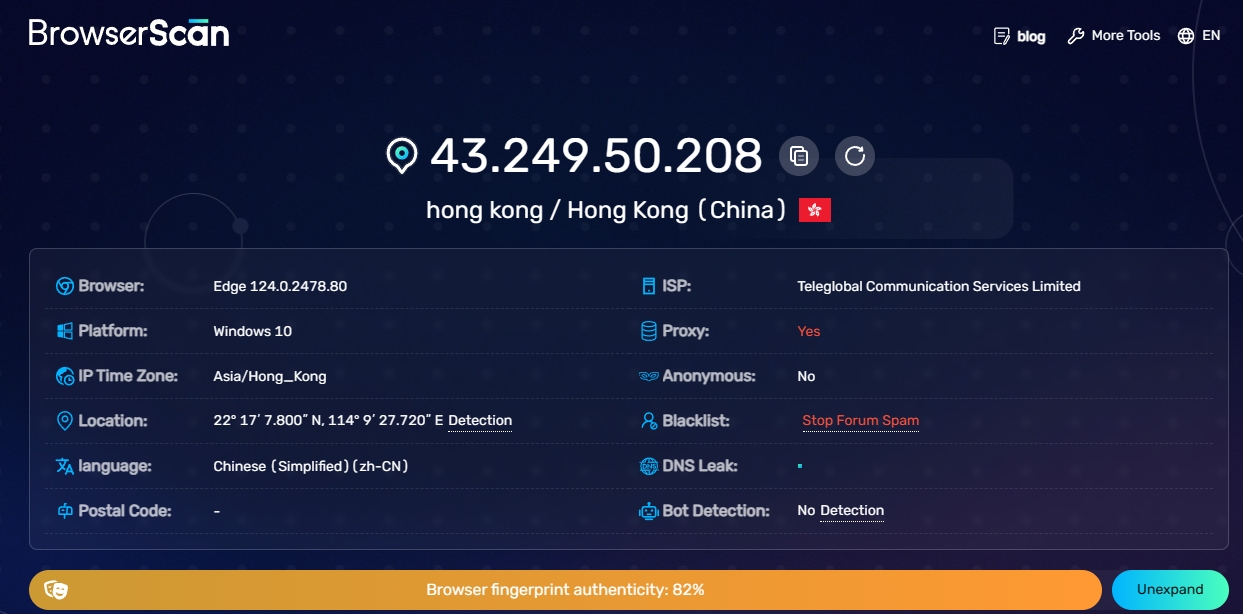
The first thing to consider is the security of the browser environment. An excellent proxy IP unlimited browser should be equipped with a strong security protection mechanism to ensure that there is no risk of association between your various accounts. For example, BitBrowser provides up to 50 personalized fingerprint parameter settings, which can create unique browser fingerprint data for different categories of accounts and build multiple protection barriers for your account security. At the same time, BitBrowser ensures that all data generated by the browser is stored only on your device to prevent the outflow of sensitive information, and uses unique encryption methods to ensure the security of data transmission and storage.
Multi-account management efficiency:
If you need to manage multiple accounts, it is extremely important to choose a proxy IP unlimited browser that can easily operate multi-account management. The RPA automation function of the proxy IP unlimited browser can support cross-platform business operations, simulate manual operation processes, easily achieve batch management of multiple accounts, and significantly improve work efficiency.
Stability and running speed:
The stability and running speed of the browser have a direct impact on work efficiency. With its top technical R&D team, the proxy IP unlimited browser has effectively guaranteed the stable operation and rapid response of the browser, avoided frequent crashes and freezes, and improved overall work efficiency.

After-sales support service quality:
High-quality after-sales support service is an aspect that cannot be ignored when choosing a proxy IP unlimited browser. The proxy IP unlimited browser is equipped with a professional after-sales support team to ensure that users can get timely and effective help during use.IP dynamic switching ability:
For overseas e-commerce, the function of dynamic IP switching is extremely critical. The proxy IP unlimited browser provides a global IP proxy service, allowing users to easily switch IP addresses in different regions, effectively avoiding account bans or restrictions.Automation tool integration effect:
Automation tools play an important role in overseas e-commerce. The automatic script function of the proxy IP unlimited browser can perform a variety of tasks according to user needs, such as automatic registration, login, order placement, etc., which greatly improves work efficiency and reduces error rates.Rich extension plug-in configuration:
Excellent proxy IP unlimited browser should provide diversified extension plug-ins to meet the needs of different users. BitBrowser has set up a variety of e-commerce related plug-ins, such as automatic form filling, order-brushing auxiliary tools, proxy switching, etc., which can be customized according to the specific needs of users to improve work efficiency.Cost-effectiveness trade-off:
Finally, cost-effectiveness is also an important factor to consider when choosing a fingerprint browser. BitBrowser in the Proxy IP Unlimited Browser provides a variety of package options to meet the budgets and needs of different users and achieve effective cost control. The free package provides 10 permanent free windows, and the paid version provides different price plans according to the number of windows and provides different numbers of sub-accounts.
Summary:
It is very important to choose a fingerprint browser that meets the needs of overseas e-commerce. The Proxy IP Unlimited Browser has become an ideal choice in the overseas e-commerce field with its outstanding security, rich functions, convenient operability, stable performance, high-quality after-sales support and good cost-effectiveness. Whether you are a novice who has just started or an experienced seller, the Proxy IP Unlimited Browser can meet your needs and help you to smoothly carry out your e-commerce business. If you are a novice who has just used the Proxy IP Unlimited Browser, it is recommended to use BitBrowser. BitBrowser provides you with 10 permanent free windows for free, making your overseas e-commerce journey more convenient.