Man
Professional
- Messages
- 3,222
- Reaction score
- 1,199
- Points
- 113
AMOS and Lumma Stealer are after user data.
Cybersecurity experts have discovered a new fraud scheme in which attackers distribute malware under the guise of AI-enabled photo and video editors.
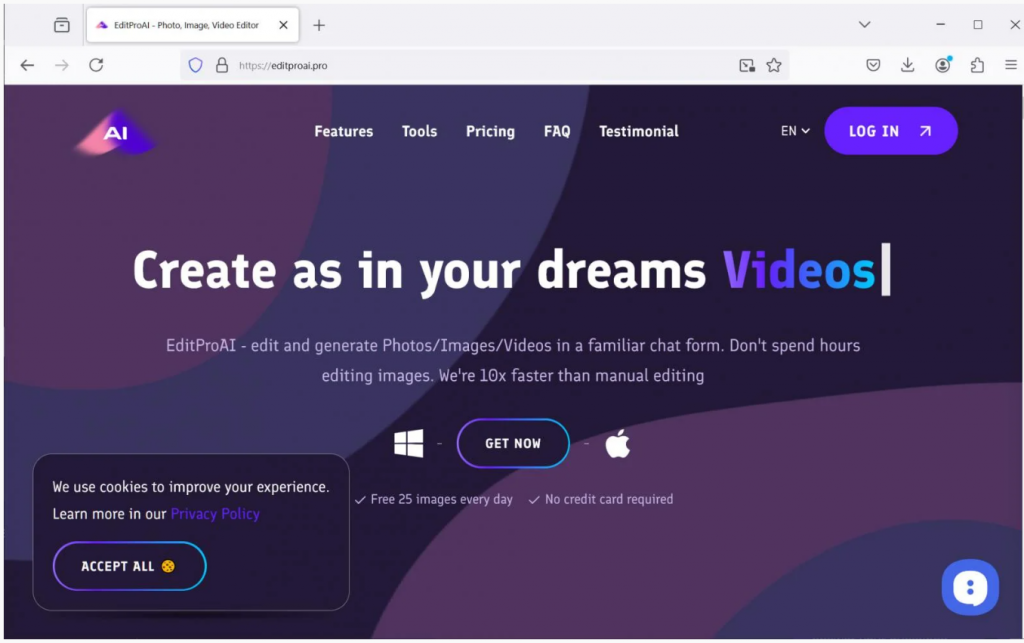
EditProAI website
A cybersecurity researcher under the pseudonym g0njxa has identified a social media advertising campaign promoting the fake EditPro editor. To add credibility, the scammers created the website editproai[dot]pro and posted ads on social media, including X*, with deepfake videos of Presidents Trump and Biden eating ice cream together.
The attackers have developed versions of the fake editor for both Windows and macOS. When you download the program, one of the malware is installed on the user's device - Lumma Stealer or AMOS.
Lumma Stealer: Features and Risks
The Lumma Stealer is a malware-as-a-service (MaaS) malware. The main goal of the program is to steal sensitive data, including accounts, cookies, browsing history, credit card data, and cryptocurrency wallets. To achieve its goals, the program uses sophisticated techniques such as process injection and encrypted communication channels with command and control servers, which makes it much more difficult to detect and eliminate. The Lumma Stealer has been in operation since 2022, and regular updates make it increasingly effective at bypassing defense mechanisms.
AMOS: An Attack Management Tool
AMOS (Attack Management and Operations System) is a comprehensive platform for managing malicious campaigns. It allows cybercriminals with minimal technical skills to deploy attacks, manage infected devices, and exfiltrate data. AMOS acts as a command-and-control (C2) center, automating many steps of attackers' work. Its capabilities are especially in demand when conducting large-scale attacks.
Experts warn that the installation of the EditPro fake software can lead to the compromise of all passwords and confidential data stored on the device. For protection, it is recommended:
Source
Cybersecurity experts have discovered a new fraud scheme in which attackers distribute malware under the guise of AI-enabled photo and video editors.

EditProAI website
A cybersecurity researcher under the pseudonym g0njxa has identified a social media advertising campaign promoting the fake EditPro editor. To add credibility, the scammers created the website editproai[dot]pro and posted ads on social media, including X*, with deepfake videos of Presidents Trump and Biden eating ice cream together.
The attackers have developed versions of the fake editor for both Windows and macOS. When you download the program, one of the malware is installed on the user's device - Lumma Stealer or AMOS.
Lumma Stealer: Features and Risks
The Lumma Stealer is a malware-as-a-service (MaaS) malware. The main goal of the program is to steal sensitive data, including accounts, cookies, browsing history, credit card data, and cryptocurrency wallets. To achieve its goals, the program uses sophisticated techniques such as process injection and encrypted communication channels with command and control servers, which makes it much more difficult to detect and eliminate. The Lumma Stealer has been in operation since 2022, and regular updates make it increasingly effective at bypassing defense mechanisms.
AMOS: An Attack Management Tool
AMOS (Attack Management and Operations System) is a comprehensive platform for managing malicious campaigns. It allows cybercriminals with minimal technical skills to deploy attacks, manage infected devices, and exfiltrate data. AMOS acts as a command-and-control (C2) center, automating many steps of attackers' work. Its capabilities are especially in demand when conducting large-scale attacks.
Experts warn that the installation of the EditPro fake software can lead to the compromise of all passwords and confidential data stored on the device. For protection, it is recommended:
- remove all traces of malware from your computer using specialized antivirus tools
- update all passwords and other sensitive data
- enable two-factor authentication wherever possible
- transfer cryptocurrencies and NFTs to a new wallet with a new seed phrase.
Source

