Friend
Professional
- Messages
- 2,675
- Reaction score
- 1,052
- Points
- 113
In the world of cybercrime, predators may face the betrayal of their own colleagues.
Veriti has discovered that cybercriminals have started using a fake OnlyFans account hacking tool that, instead of performing the promised functions, infects the attackers with the Lumma Stealer malware.
OnlyFans is a popular adult content creation and distribution platform where creators can earn from their fans' subscriptions. Due to its high popularity, the platform is the target of attacks by cybercriminals who try to steal accounts in order to extort, receive payments from subscribers, or distribute personal information.
To facilitate the hacking process, attackers use so-called "checkers" that check databases of stolen data for matches with OnlyFans accounts, allowing them to automate the process of guessing passwords and credentials. However, sometimes such tools turn out to be a trap themselves.
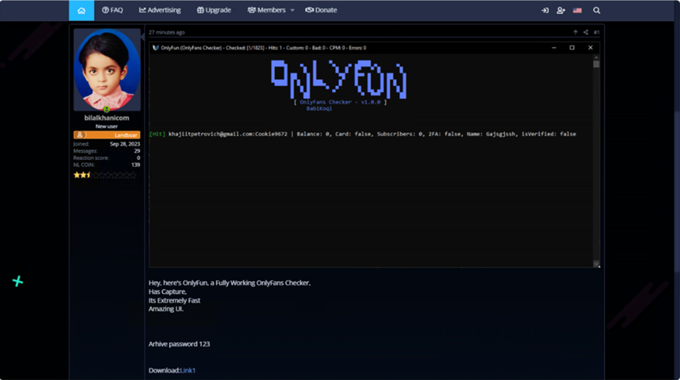
Checker advertising on the darknet forum
Veriti researchers have discovered a case where a fake checker for OnlyFans installed the Lumma Stealer malware on a computer instead of verifying credentials. The malicious file, downloaded from the GitHub repository, was a program "brtjgjsefd.exe" that, once launched, began collecting personal data from the infected device.
The Lumma Stealer specializes in stealing data such as passwords, cookies, two-factor authentication codes, cryptocurrency wallets, and credit card data stored in the victim's browser or file system. Notably, the Lumma Stealer not only steals data, but can also download additional malware to the infected device and execute PowerShell scripts, making the program particularly dangerous.
In addition, cybercriminals used fake checkers for other popular platforms - Disney+ and Instagram. For example, the GitHub repository also contained malicious files named "DisneyChecker.exe", "InstaCheck.exe", and "ccMirai.exe", which were allegedly intended to validate Disney+ and Instagram credentials and create the Mirai botnet, respectively. The files infected the computers of victims, who tried to use them for their own criminal purposes. The researchers also identified C2 servers located on ".shop" domains that controlled infected devices and obtained stolen data.
Source
Veriti has discovered that cybercriminals have started using a fake OnlyFans account hacking tool that, instead of performing the promised functions, infects the attackers with the Lumma Stealer malware.
OnlyFans is a popular adult content creation and distribution platform where creators can earn from their fans' subscriptions. Due to its high popularity, the platform is the target of attacks by cybercriminals who try to steal accounts in order to extort, receive payments from subscribers, or distribute personal information.
To facilitate the hacking process, attackers use so-called "checkers" that check databases of stolen data for matches with OnlyFans accounts, allowing them to automate the process of guessing passwords and credentials. However, sometimes such tools turn out to be a trap themselves.

Checker advertising on the darknet forum
Veriti researchers have discovered a case where a fake checker for OnlyFans installed the Lumma Stealer malware on a computer instead of verifying credentials. The malicious file, downloaded from the GitHub repository, was a program "brtjgjsefd.exe" that, once launched, began collecting personal data from the infected device.
The Lumma Stealer specializes in stealing data such as passwords, cookies, two-factor authentication codes, cryptocurrency wallets, and credit card data stored in the victim's browser or file system. Notably, the Lumma Stealer not only steals data, but can also download additional malware to the infected device and execute PowerShell scripts, making the program particularly dangerous.
In addition, cybercriminals used fake checkers for other popular platforms - Disney+ and Instagram. For example, the GitHub repository also contained malicious files named "DisneyChecker.exe", "InstaCheck.exe", and "ccMirai.exe", which were allegedly intended to validate Disney+ and Instagram credentials and create the Mirai botnet, respectively. The files infected the computers of victims, who tried to use them for their own criminal purposes. The researchers also identified C2 servers located on ".shop" domains that controlled infected devices and obtained stolen data.
Source
