Professor
Professional
- Messages
- 1,393
- Reaction score
- 1,399
- Points
- 113
NordVPN analysts estimate that billions of stolen cookies are being sold on the dark web and Telegram. Around 7-9% of these cookies are still active and can be used by attackers.
According to researchers, criminals can currently purchase more than 93.7 billion cookies online.
NordVPN warns that the vast majority of stolen cookies (90.25%) contain identification data that is intended to identify users and deliver targeted advertising. Cookies may also contain data such as names, home addresses and email addresses, location data, passwords, phone numbers. However, it is noted that such information is present in only 0.5% of all stolen cookies.
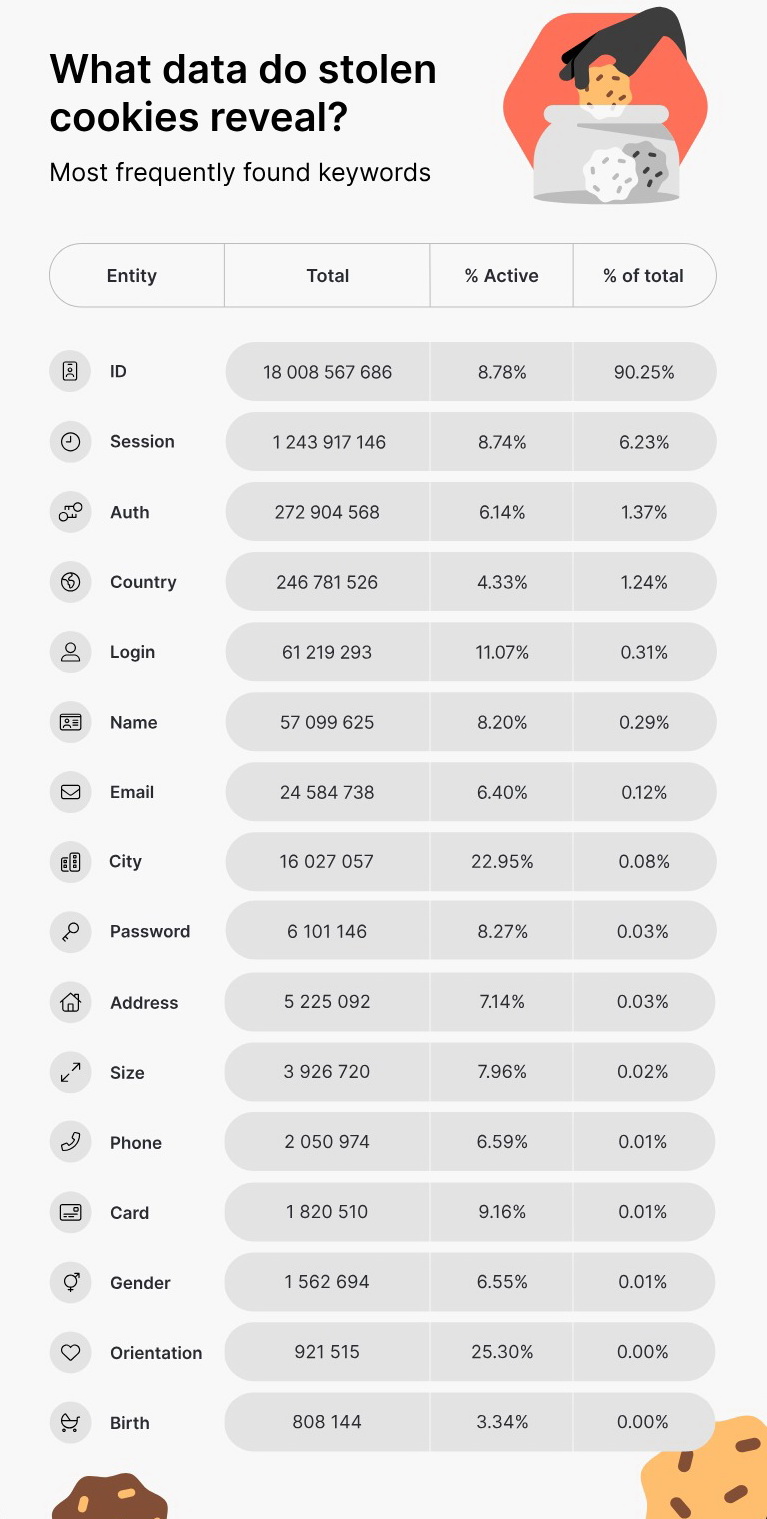
Cookies can also contain information about user sessions. According to experts, more than 1.2 billion such files are still active (about 6% of the total), and they are generally considered the most serious problem.
Cybercriminals can use session cookies to impersonate other people on websites, authenticate to various services without using credentials, and in many cases bypass multi-factor authentication. Therefore, session cookies are very attractive to cybercriminals, who can use them to collect information from mailboxes, banking applications, corporate systems, and so on.
Cookies most often fall into the hands of criminals thanks to infostealers. The leader in this area, according to researchers, is the Redline stealer (44% of all detected cookies were associated with it). The second, third and fourth places on the list are occupied by Vidar, LummaC2 and Meta, although law enforcement agencies have taken action against the last two (as well as against Redline).
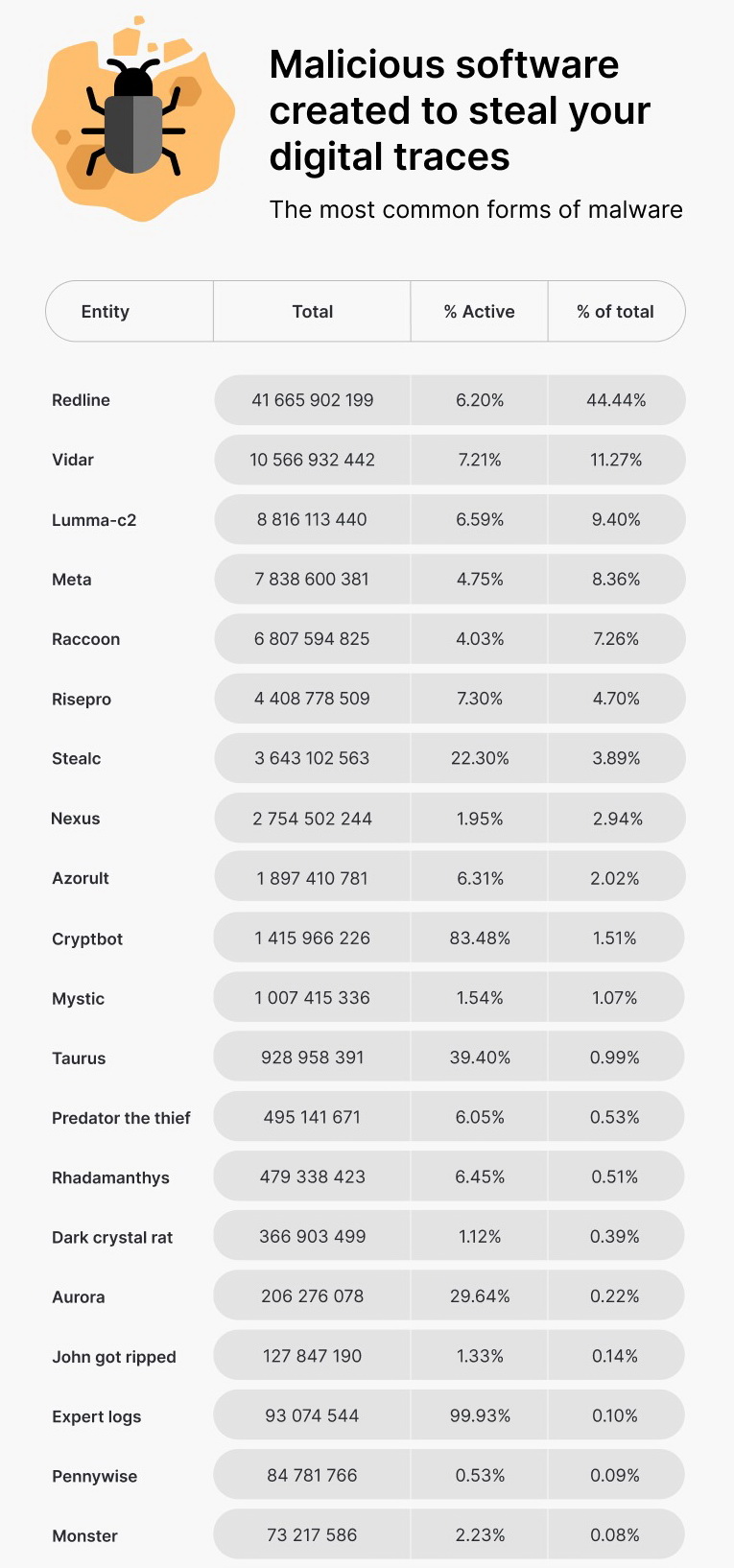
The cost of accessing these malicious tools is relatively low considering how much profit can be made from stealing users' digital assets. Lumma, for example, can be purchased for as little as $250, while Redline and Meta cost only $150 for the basic set of features.
Experts also recommend regularly updating devices and installing the latest patches on them if the priority is to prevent infection with stealers and other malware. It would also be a good idea to regularly clear your browser history and delete unnecessary cookies.
(c) Source
According to researchers, criminals can currently purchase more than 93.7 billion cookies online.
“Cookies may seem harmless, but in the wrong hands they are digital keys to your most personal information. What was designed for convenience is now a growing vulnerability that is being exploited by cybercriminals around the world,” says Adrianus Warmenhoven. “Most people don’t realize that a stolen cookie can be as dangerous as a stolen password, and they unthinkingly accept cookies when visiting websites just to get rid of the pop-up at the bottom of the screen. However, hijacking a cookie can give hackers direct access to all sorts of accounts containing sensitive data, without the need to enter a username and password.”
NordVPN warns that the vast majority of stolen cookies (90.25%) contain identification data that is intended to identify users and deliver targeted advertising. Cookies may also contain data such as names, home addresses and email addresses, location data, passwords, phone numbers. However, it is noted that such information is present in only 0.5% of all stolen cookies.

Cookies can also contain information about user sessions. According to experts, more than 1.2 billion such files are still active (about 6% of the total), and they are generally considered the most serious problem.
Cybercriminals can use session cookies to impersonate other people on websites, authenticate to various services without using credentials, and in many cases bypass multi-factor authentication. Therefore, session cookies are very attractive to cybercriminals, who can use them to collect information from mailboxes, banking applications, corporate systems, and so on.
Cookies most often fall into the hands of criminals thanks to infostealers. The leader in this area, according to researchers, is the Redline stealer (44% of all detected cookies were associated with it). The second, third and fourth places on the list are occupied by Vidar, LummaC2 and Meta, although law enforcement agencies have taken action against the last two (as well as against Redline).

The cost of accessing these malicious tools is relatively low considering how much profit can be made from stealing users' digital assets. Lumma, for example, can be purchased for as little as $250, while Redline and Meta cost only $150 for the basic set of features.
“Think twice before accepting any cookies,” the researchers advise. “The first step to improving security is understanding that not all cookies are necessary, and while you can agree to all cookies, that doesn’t mean you should. Opt out of unnecessary cookies whenever possible, especially third-party cookies or those that track your behavior. Most sites work just fine without them.”
Experts also recommend regularly updating devices and installing the latest patches on them if the priority is to prevent infection with stealers and other malware. It would also be a good idea to regularly clear your browser history and delete unnecessary cookies.
“Many users don’t realize that active sessions can persist even after the browser is closed,” Warmenhoven says. “Clearing this data helps reduce the opportunities for unauthorized access.”
(c) Source
