CarderPlanet
Professional
Key features of the new malware that is already being sold on the darknet.
Cybersecurity researchers at Zscaler ThreatLabZ have discovered a new malware called BunnyLoader, which is distributed on a Malware-as-a-Service (MaaS) model and sold on underground cybercrime forums.
The researchers noted that BunnyLoader has various functions:
BunnyLoader, written in C / C++, is offered for $250 for a lifetime license. Since its debut on September 4, 2023, the malware has been continuously evolving, including new features and improvements that enable evasion from antivirus and sandbox attacks.
The C2 Server Control Panel (Command and Control Server) offers customers the ability to monitor active tasks, infection statistics, the total number of connected and inactive hosts, and logs of the data theft utility. It also provides remote monitoring of compromised machines.
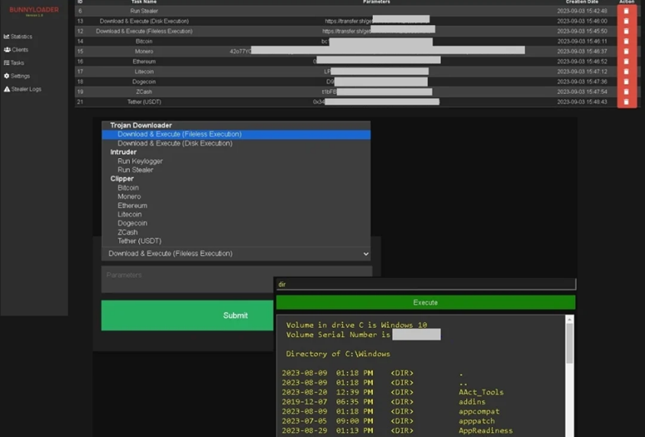
Screenshot of the BunnyLoader control panel
The exact initial access mechanism used to distribute BunnyLoader is currently unclear. Once installed, the malware configures its permanent presence by modifying the Windows registry and performs a series of checks for sandboxes and virtual machines before activating its malicious actions, sending task requests to the remote server and receiving the desired responses.
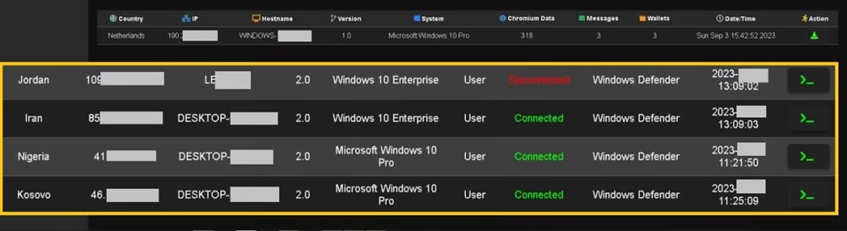
The Control Panel displays a list of infected computers
The tasks sent include downloading and executing next-stage malware, running a keylogger and utilities to steal data from instant messengers, VPN clients, and web browsers, as well as redirecting payments in cryptocurrencies and profiting from illegal transactions. The last step involves encapsulating all the collected data in a ZIP archive and transferring it to the server.
The researchers emphasize that BunnyLoader is a new MaaS service that constantly develops its tactics and adds new features to successfully conduct campaigns against its goals.
Cybersecurity researchers at Zscaler ThreatLabZ have discovered a new malware called BunnyLoader, which is distributed on a Malware-as-a-Service (MaaS) model and sold on underground cybercrime forums.
The researchers noted that BunnyLoader has various functions:
- Loading and executing malicious code at the second stage.
- Theft of browser credentials and system information.
- Executing remote commands on an infected machine.
- Registering keystrokes (keylogging).
- Clipper function for tracking the victim's clipboard and replacing the contents corresponding to the addresses of cryptocurrency wallets with the addresses of the attackers ' wallets.
- Fileless download to make it harder for antivirus software to remove malware ( Fileless malware).
- Configure permanent presence by changing the Windows registry.
BunnyLoader, written in C / C++, is offered for $250 for a lifetime license. Since its debut on September 4, 2023, the malware has been continuously evolving, including new features and improvements that enable evasion from antivirus and sandbox attacks.
The C2 Server Control Panel (Command and Control Server) offers customers the ability to monitor active tasks, infection statistics, the total number of connected and inactive hosts, and logs of the data theft utility. It also provides remote monitoring of compromised machines.

Screenshot of the BunnyLoader control panel
The exact initial access mechanism used to distribute BunnyLoader is currently unclear. Once installed, the malware configures its permanent presence by modifying the Windows registry and performs a series of checks for sandboxes and virtual machines before activating its malicious actions, sending task requests to the remote server and receiving the desired responses.

The Control Panel displays a list of infected computers
The tasks sent include downloading and executing next-stage malware, running a keylogger and utilities to steal data from instant messengers, VPN clients, and web browsers, as well as redirecting payments in cryptocurrencies and profiting from illegal transactions. The last step involves encapsulating all the collected data in a ZIP archive and transferring it to the server.
The researchers emphasize that BunnyLoader is a new MaaS service that constantly develops its tactics and adds new features to successfully conduct campaigns against its goals.
