Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,036
- Points
- 113
A story about how over 100 organizations fell victim to forced pentests.
Israeli researchers have identified serious vulnerabilities in the Visual Studio Code extension market, successfully infecting more than 100 organizations by injecting malicious code into a clone extension of the popular "Dracula Official" interface theme. Experts also found thousands of extensions with millions of installations containing hidden security risks.
Visual Studio Code (VSCode) is a source code editor developed by Microsoft and used by many professional developers around the world. Microsoft also operates an extension store for VSCode called the VSCode Marketplace, which offers add-ons to extend the functionality and customization of the app.
In the past, various researchers have repeatedly reported various security issues in VSCode, including the possibility of spoofing extensions and stealing developer authentication tokens. There were also confirmed cases of malicious extensions being detected.
Usually, Microsoft quickly closes such vulnerabilities, but their very presence and such frequent detections, to put it mildly, does not inspire confidence.
For their experiment, researchers Amit Asaraf, Itai Kruk, and Idan Dardikman created an extension that mimics the popular "Dracula Official" theme, which has more than 7 million installations. The fake extension was named "Darcula Official", and the researchers even registered a domain "darculatheme.com", to add credibility to the fake extension.
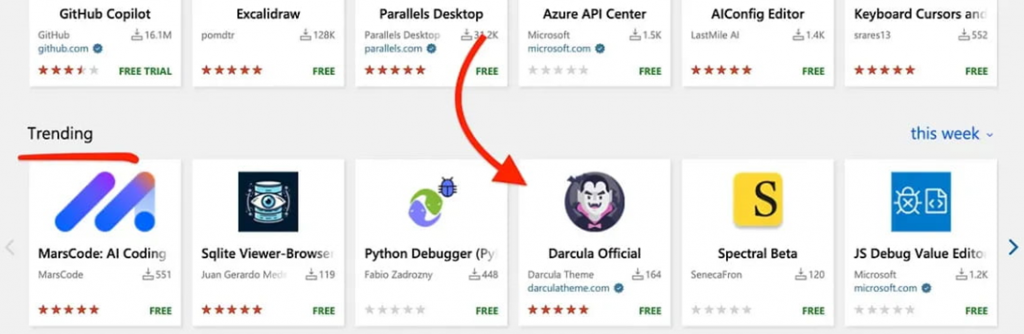
The situation is aggravated by the fact that the name" Darcula", specially written with an error, is a well-established designation. For example, the Glowing Darcula plugin for JetBrains IntelliJ IDEA IDE is quite legitimate and is also used by thousands of developers. Therefore, in the case of the spy research plugin, none of the VSCode users noticed the catch.
Malicious code added by researchers to their extension collects system information and sends it to a remote server. This code is not recognized by security tools, because VSCode is considered a development and testing system.
"Unfortunately, traditional endpoint protection (EDR) tools do not detect this activity," said Amit Asaraf. " VSCode is designed to read many files and execute many commands, which makes it difficult for EDR tools to recognize whether this activity is legitimate or malicious."
The fake extension quickly gained popularity and was installed by many developers from large organizations, including a "public company with a market capitalization of $483 billion," several information security firms, as well as a national judicial network.
After a successful experiment, the researchers decided to closely study the threats in the VSCode extension market and found:
Overly lax code control and verification measures in the VSCode extension market allow attackers to abuse the platform with might and main. And due to the growing number of developers and the popularity of VSCode, the situation is only getting worse. Researchers warn of significant risks for organizations associated with installing extensions from the VSCode Marketplace.
All detected malicious extensions were responsibly reported to Microsoft for removal, but most of them are still available for download.
Next week, the researchers plan to publish their tool "ExtensionTotal", with which they found all the questionable extensions. The tool will be available free of charge to developers, giving them the opportunity to scan their environments for potential threats.
Israeli researchers have identified serious vulnerabilities in the Visual Studio Code extension market, successfully infecting more than 100 organizations by injecting malicious code into a clone extension of the popular "Dracula Official" interface theme. Experts also found thousands of extensions with millions of installations containing hidden security risks.
Visual Studio Code (VSCode) is a source code editor developed by Microsoft and used by many professional developers around the world. Microsoft also operates an extension store for VSCode called the VSCode Marketplace, which offers add-ons to extend the functionality and customization of the app.
In the past, various researchers have repeatedly reported various security issues in VSCode, including the possibility of spoofing extensions and stealing developer authentication tokens. There were also confirmed cases of malicious extensions being detected.
Usually, Microsoft quickly closes such vulnerabilities, but their very presence and such frequent detections, to put it mildly, does not inspire confidence.
For their experiment, researchers Amit Asaraf, Itai Kruk, and Idan Dardikman created an extension that mimics the popular "Dracula Official" theme, which has more than 7 million installations. The fake extension was named "Darcula Official", and the researchers even registered a domain "darculatheme.com", to add credibility to the fake extension.

The situation is aggravated by the fact that the name" Darcula", specially written with an error, is a well-established designation. For example, the Glowing Darcula plugin for JetBrains IntelliJ IDEA IDE is quite legitimate and is also used by thousands of developers. Therefore, in the case of the spy research plugin, none of the VSCode users noticed the catch.
Malicious code added by researchers to their extension collects system information and sends it to a remote server. This code is not recognized by security tools, because VSCode is considered a development and testing system.
"Unfortunately, traditional endpoint protection (EDR) tools do not detect this activity," said Amit Asaraf. " VSCode is designed to read many files and execute many commands, which makes it difficult for EDR tools to recognize whether this activity is legitimate or malicious."
The fake extension quickly gained popularity and was installed by many developers from large organizations, including a "public company with a market capitalization of $483 billion," several information security firms, as well as a national judicial network.
After a successful experiment, the researchers decided to closely study the threats in the VSCode extension market and found:
- 1,283 extensions with known malicious code (229 million installs);
- 8161 extensions that communicate with hard-coded IP addresses;
- 1452 extensions that run unknown executable files;
- 2304 extensions that use third-party publisher repositories on GitHub, which indicates that they are fake.
Overly lax code control and verification measures in the VSCode extension market allow attackers to abuse the platform with might and main. And due to the growing number of developers and the popularity of VSCode, the situation is only getting worse. Researchers warn of significant risks for organizations associated with installing extensions from the VSCode Marketplace.
All detected malicious extensions were responsibly reported to Microsoft for removal, but most of them are still available for download.
Next week, the researchers plan to publish their tool "ExtensionTotal", with which they found all the questionable extensions. The tool will be available free of charge to developers, giving them the opportunity to scan their environments for potential threats.

