Tomcat
Professional
- Messages
- 2,695
- Reaction score
- 1,055
- Points
- 113
It's been 10 years since Skimer, the first malware designed specifically to attack automated teller machines (ATMs), was discovered. During this time, entire families of such malicious programs appeared. In this article, we will look at the most significant of them and talk about the best practices for detecting and countering such programs.
10 years ago, understanding a previously unprecedented threat was extremely difficult, because the analysis required understanding the functions and parameters of the application program interface (API) of ATMs from various manufacturers, which were never published in publicly available sources.
Prior to Skimer's discovery, ATMs were often viewed as proprietary hardware devices running custom versions of the operating system and equipped with specialized protection against specific types of money-theft attacks. But, as often happens, chance put everything in its place. During Skimer's research, experts found that ATMs from all the most common manufacturers run a standard version of Windows OS and, from a technical point of view, are the most ordinary computers with special equipment connected to them, such as, for example, a banknote dispenser and a card reader. This means that a potential vulnerability to malicious code can be used for unauthorized cash withdrawals.
The advent of dedicated ATM malware has provided criminals with a more subtle and stealthy alternative to physical hacking. Previously, their methods were limited to either the traditional breaking of a safe lock using a crowbar or grinder, or the spectacular detonation of an ATM using a flammable gas mixture. Of course, none of these methods can be called quiet and unnoticeable.
Over the past 10 years, there has been a steady increase in the number of detected samples of malicious software (malware) for ATM. Since the very first versions of Skimer, this type of malware has developed rapidly and has gone from single copies available only to their creators to “package” solutions on the black market and complex tools used by professional hacker groups. Today, there are entire families of programs created for unauthorized withdrawal of money from ATMs. Despite this, the total number of such programs, due to their extreme specificity, is significantly inferior to almost any other category of malware
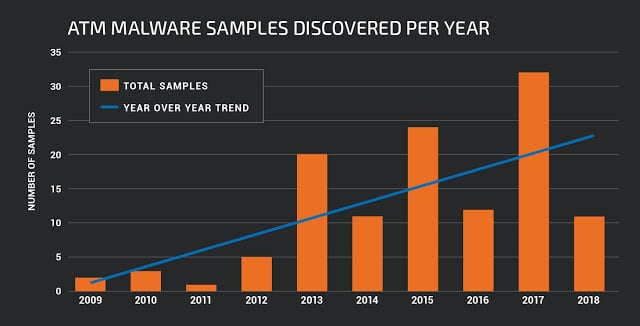
Number of detected malware samples according to VirusTotal
For any attack on an ATM, you must be close to it, because you need to take the money. To directly “collect” cash from an infected ATM, criminals usually involve so-called mules—accomplices who, on command, enter a unique session key or use a special card to authorize an unauthorized transaction, after which they take the money dispensed by the ATM. Thus, the attacker himself (this could be the author and/or seller of the malware) controls the entire operation remotely and does not risk being caught in the act. But before it comes to the work of the “mules,” criminals need to introduce malware into the ATM computer, which most often means gaining physical access to the USB ports or optical drive.
If you look at the information available in open sources, you will notice that reports of attacks on banking organizations around the world appear quite regularly. Countries in Latin America and Eastern Europe are “leading” in such attacks, where outdated infrastructure is often used and insufficient attention is paid to ensuring the security of the ATM network. Thus, according to EAST (European Association for Secure Transactions), the total damage from logical attacks on ATMs in recent years has exceeded $4 million. However, you need to understand that these are only confirmed attacks. The damage to banks is rarely disclosed; the actual figures are much higher, possibly reaching tens of millions of dollars.
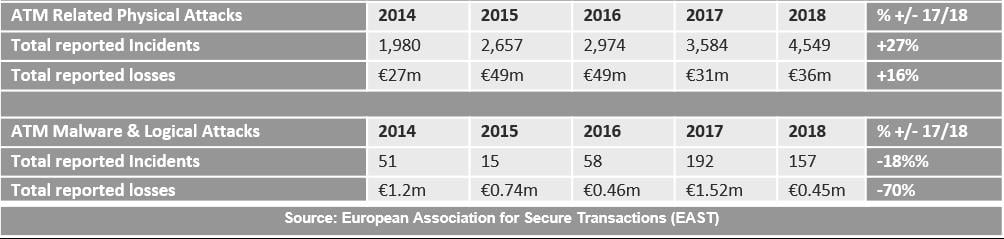
Comparative statistics on physical and logical attacks on ATM for 2014–2018.
It should be emphasized that such software harms not only the banks themselves, but also the reputation of ATM manufacturers, as well as individuals and companies whose credentials can be compromised as a result of successful cyber attacks.
The purpose of skimmers is to steal bank card and transaction data, and, if possible, even a PIN code if the PIN keyboard encryption keys have previously been compromised.
Direct cash withdrawal utilities have a functionality called jackpotting (from the English jackpot - a large win in a lottery, jackpot), which allows attackers to carry out unauthorized withdrawal of money from an ATM without the need to authorize the transaction on the bank's side. At the same time, there is malware that combines the functionality of a skimmer and jackpotting.
In classifying the method of “delivery” of ATM Malware to the end device, two approaches can also be distinguished. The first involves an attacker gaining physical access to the ATM’s USB interfaces and directly copying or launching the malware from a flash drive. The second is remote implementation of malware, which involves preliminary compromise of the bank’s internal corporate network, obtaining administrative privileges (for example, in a software replication system) and further distribution of malicious code to the ATM network from a source that is legitimate from the point of view of the end devices themselves.
The second approach requires serious preparation and is implemented, as a rule, by organized criminal groups. Here we should mention such “professionals” in the field of targeted attacks on financial organizations as the hacker groups Anunak, Corkow, Buhtrap, Lurk, Lazarus, Metel, Cobalt. The latter made itself known loudly in July 2016, when the Taiwanese First Bank was attacked. The attackers simultaneously cleared dozens of ATMs throughout Taipei. This was an example of a well-planned, targeted logical attack on a financial institution. Hackers penetrated the bank's internal network through phishing emails and, using infrastructure vulnerabilities, gained access to the ATM management system. Then the “mules” acted.
In addition, ATM malware can be classified according to its applicability to the target of the attack. There are Malware aimed at specific models of ATMs from a specific manufacturer, and universal malware that works on all ATMs, regardless of the manufacturer.
The presence of universal Malware is due to the fact that all major ATM manufacturers support the CEN/XFS standard (from the English eXtensions for Financial Services), which provides a common API for managing various ATM modules. Thus, CEN/XFS can also be used to create malware so that it can “communicate” with the ATM in its native language.
The XFS API contains high-level functions for communicating with various ATM modules such as the banknote dispenser, PIN keypad, cash acceptance module, etc. High-level functions are provided through a common SDK, while low-level functions are provided through service providers, which are different for each ATM manufacturer. This architecture is very similar to the Win32 architecture, where developers use a high-level API to communicate with the OS kernel and various device drivers provided by individual hardware component manufacturers.
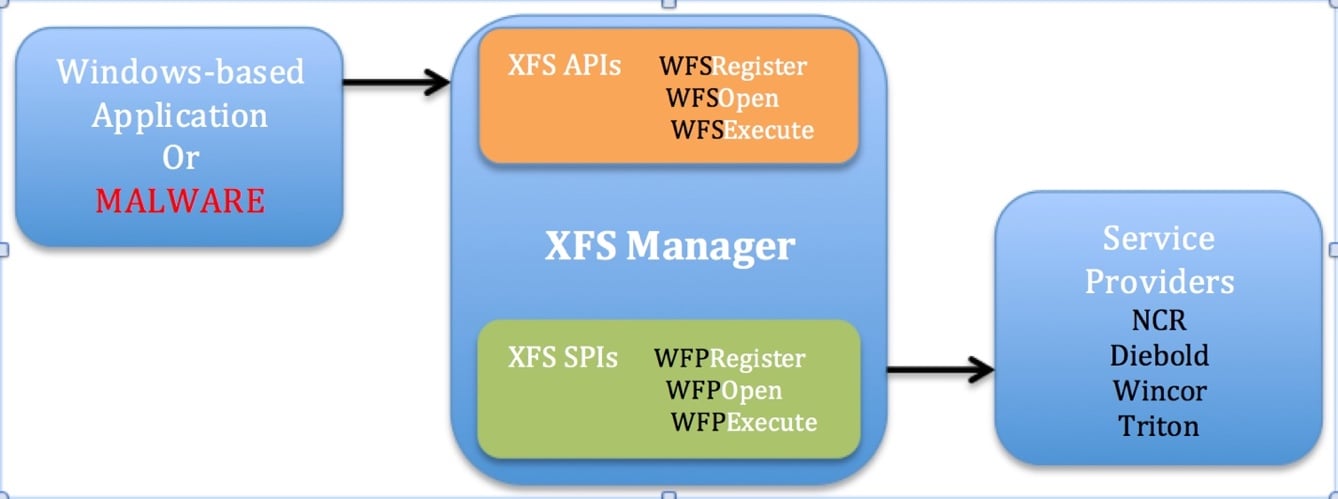
High-level architecture CEN/XFS
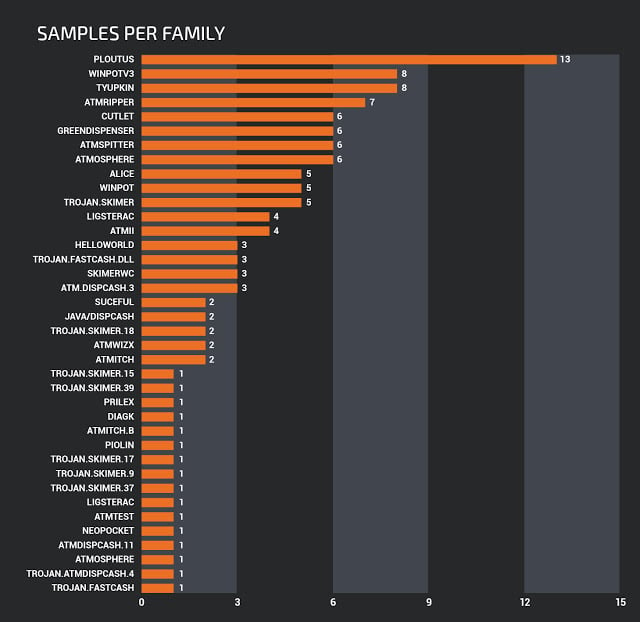
Number of malware samples by family
Ploutus
Ploutus is the malware family with the largest number of detected samples. Most of them were registered in Mexico. Ploutus is a typical example of a direct output utility. To download malware, attackers must have access to USB ports or a CD-ROM drive.
An example is one of the recent modifications - Ploutus-D, which was initially aimed at Diebold ATMs, widely used in the United States. However, the malware interacts with the ATM through the multi-vendor KAL Kalignite platform, and after a simple modification of the Ploutus-D code can be used to attack ATMs from other manufacturers.
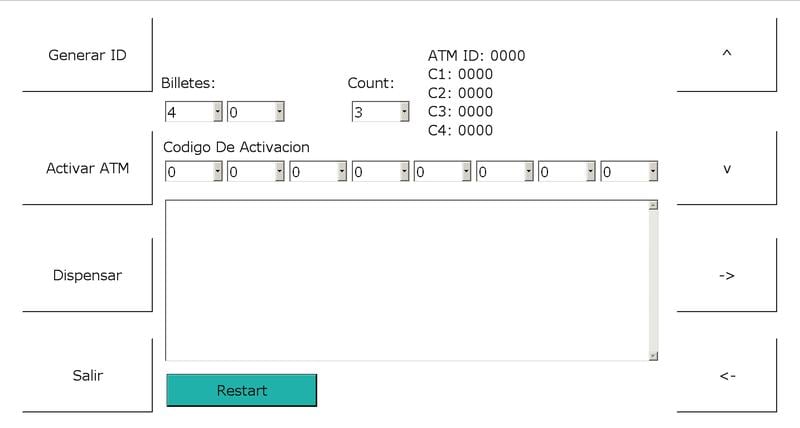
One of the Ploutus interface options
Skimer
Skimer is one of the first logical attacks on ATMs. Functionally, this malware fully lives up to its name and is essentially a virtual skimming device that copies data from the magnetic stripe of a bank card.
In addition, Skimer is a backdoor and can be used for unauthorized withdrawal of money from an ATM. If the attacker knows the key to activate the program, the malware displays a menu from which you can dispense money from each of the four dispenser cassettes.
Most other families of ATM malware work on a similar principle. Attackers must provide themselves with physical access to the service area of the ATM in order to connect an external drive with malware. After introducing malware into the system, the attacker needs to enter a unique code to activate the cash withdrawal process.
Tyupkin (PadPin)
Real fame came to ATM malware with the emergence of the infamous Tyupkin Trojan, whose activity was first recorded in 2014. Since then, many ATMs around the world have been attacked.
A distinctive feature of Tyupkin is its ability to limit the time of its activity to specified hours and days of the week. Some of the first varieties of Tyupkin were initially only able to run on Sunday and Monday nights.
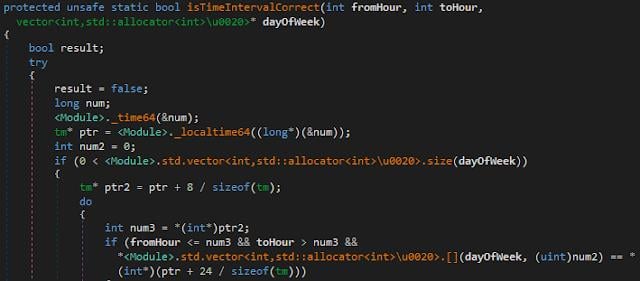
Tyupkin function for checking startup time
In addition, the Trojan has a self-defense function. Immediately before dispensing cash, Tyupkin disconnects all network connections so that if suspicious activity is detected on the bank’s side, the monitoring service will not be able to turn off the ATM, thereby interrupting the fraudulent operation.
Alice
The operating principle of Alice is the same as that of many other ATM malware. Installation requires physical access to the ATM system. Once launched, Alice asks for an access code to continue working. If the correct activation code is entered, the malware gains access to the banknote dispenser and allows cash to be dispensed.
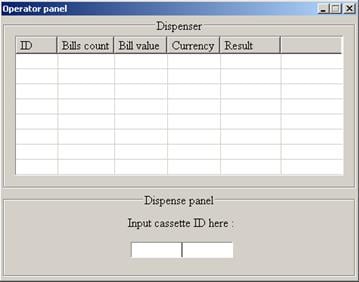
Alice main interface
Cutlet Maker
In 2017, cybercriminals began selling “ATM Malware-as-a-Service” on the darknet. For $5,000, anyone can purchase a package of ready-to-use Cutlet Maker malware and video instructions on how to open an ATM. Those who purchase the service need to select a suitable ATM (the authors of the malware recommend Wincor Nixdorf), use the instructions for hacking its service part, download the malicious program and pay the service organizers for its activation (obtaining a unique session key) in order to start the process of issuing money.
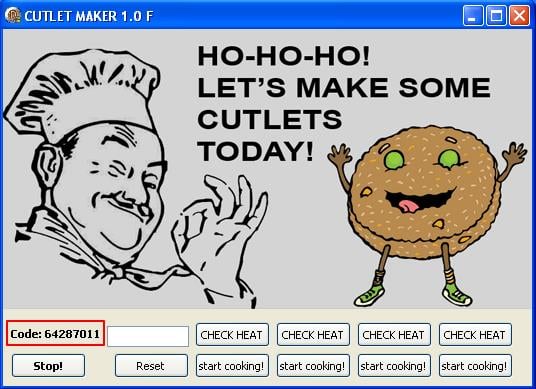
Cutlet Maker main interface
In the case of Cutlet Maker, the potential consumer of the service may have minimal knowledge about the target of the attack. This example shows how such schemes reduce the entry threshold into this type of crime and lead to a significant increase in the number of cybercriminals.
FASTCash
FASTCash is a unique tool that the Lazarus hacker group used to attack financial organizations in more than 20 countries. Total for 2016-2018 Several tens of millions of dollars were stolen.
The peculiarity of FASTCash lies in the mechanism of its operation and its orientation to the IBM AIX OS. The hackers introduced a Trojan into a legitimate process on the application server of processing systems that control transactions in the ATM network and run AIX.
After compromising the server, the Trojan was able to create fake ISO 8583 messages (a standard that describes the transmission process and format of financial messages of systems that process bank card data), generating a response confirming a fraudulent cash withdrawal operation from ATMs. It should be noted that in all cases, successful attacks were made possible because financial institutions were using outdated versions of AIX - without the necessary security updates.

FASTCash operation diagram from Symantec report
This is another example of a targeted attack on financial organizations, in this case through processing systems. At the same time, the level of complexity and sophistication of FASTCash is very high and cannot be compared with any other “standard” ATM Malware.
We list the main measures that each bank must take into account when organizing the protection of its own ATM network and successfully countering relevant threats:
While the vast majority of attacks on ATMs using malware are targeted and carried out by individual attackers or small groups, the potential ability to unload large amounts of cash simultaneously from several dozen ATMs is increasingly attracting professional hacker groups to this area, which use much more sophisticated and complex tools for targeted attacks on financial organizations.
However, despite the growing popularity of logical attacks, physical attacks still make up the vast majority of the total number of attacks on ATMs. To effectively counteract it, you need to take an integrated approach to ensuring the security of your network. Video monitoring of ATM installation areas, security alarms with a quick response team connected to the remote control, strengthening of ATM cases and safes, equipping with special sensors - these physical protection measures in combination with cyber defense means greatly enhance the overall level of security and reduce the desire of an attacker to attack you.
Organizing monitoring of cyber threats and prompt response is also an important step in ensuring comprehensive protection of the organization’s infrastructure. To solve this problem, Sberbank operates its own Security Operations Center (SOC), which provides continuous online monitoring and response to cyber threats. The combination of modern methods used to counter cyber threats allows us to successfully identify and repel attacks at the initial stages of their occurrence.
Active development of software for ATMs is a trend of today and the near future. Cybercriminals are not standing still, and their methods are becoming more sophisticated. Accordingly, investments by organizations in cybersecurity should not be a forced measure, but a conscious step by management (primarily business) - not only to protect their own infrastructure and data, but also to provide customers with a reliable and secure service.
(c) Valery Torchikov

 www.secuteck.ru
www.secuteck.ru
10 years ago, understanding a previously unprecedented threat was extremely difficult, because the analysis required understanding the functions and parameters of the application program interface (API) of ATMs from various manufacturers, which were never published in publicly available sources.
Prior to Skimer's discovery, ATMs were often viewed as proprietary hardware devices running custom versions of the operating system and equipped with specialized protection against specific types of money-theft attacks. But, as often happens, chance put everything in its place. During Skimer's research, experts found that ATMs from all the most common manufacturers run a standard version of Windows OS and, from a technical point of view, are the most ordinary computers with special equipment connected to them, such as, for example, a banknote dispenser and a card reader. This means that a potential vulnerability to malicious code can be used for unauthorized cash withdrawals.
The evolution of attacks on ATMs
Criminals have always viewed ATMs as a potential source of profit: a safe with money, standing practically on the street, could not but be ignored. However, while initially there were no alternatives to physical attacks, technology has evolved greatly over the past few years.The advent of dedicated ATM malware has provided criminals with a more subtle and stealthy alternative to physical hacking. Previously, their methods were limited to either the traditional breaking of a safe lock using a crowbar or grinder, or the spectacular detonation of an ATM using a flammable gas mixture. Of course, none of these methods can be called quiet and unnoticeable.
Over the past 10 years, there has been a steady increase in the number of detected samples of malicious software (malware) for ATM. Since the very first versions of Skimer, this type of malware has developed rapidly and has gone from single copies available only to their creators to “package” solutions on the black market and complex tools used by professional hacker groups. Today, there are entire families of programs created for unauthorized withdrawal of money from ATMs. Despite this, the total number of such programs, due to their extreme specificity, is significantly inferior to almost any other category of malware

Number of detected malware samples according to VirusTotal
For any attack on an ATM, you must be close to it, because you need to take the money. To directly “collect” cash from an infected ATM, criminals usually involve so-called mules—accomplices who, on command, enter a unique session key or use a special card to authorize an unauthorized transaction, after which they take the money dispensed by the ATM. Thus, the attacker himself (this could be the author and/or seller of the malware) controls the entire operation remotely and does not risk being caught in the act. But before it comes to the work of the “mules,” criminals need to introduce malware into the ATM computer, which most often means gaining physical access to the USB ports or optical drive.
If you look at the information available in open sources, you will notice that reports of attacks on banking organizations around the world appear quite regularly. Countries in Latin America and Eastern Europe are “leading” in such attacks, where outdated infrastructure is often used and insufficient attention is paid to ensuring the security of the ATM network. Thus, according to EAST (European Association for Secure Transactions), the total damage from logical attacks on ATMs in recent years has exceeded $4 million. However, you need to understand that these are only confirmed attacks. The damage to banks is rarely disclosed; the actual figures are much higher, possibly reaching tens of millions of dollars.

Comparative statistics on physical and logical attacks on ATM for 2014–2018.
It should be emphasized that such software harms not only the banks themselves, but also the reputation of ATM manufacturers, as well as individuals and companies whose credentials can be compromised as a result of successful cyber attacks.
ATM Malware Classification
There are several different classifications of ATM Malware (ATM malware). Based on functionality, all such programs can be divided into two types: virtual skimmers and Direct Dispense utilities.The purpose of skimmers is to steal bank card and transaction data, and, if possible, even a PIN code if the PIN keyboard encryption keys have previously been compromised.
Direct cash withdrawal utilities have a functionality called jackpotting (from the English jackpot - a large win in a lottery, jackpot), which allows attackers to carry out unauthorized withdrawal of money from an ATM without the need to authorize the transaction on the bank's side. At the same time, there is malware that combines the functionality of a skimmer and jackpotting.
In classifying the method of “delivery” of ATM Malware to the end device, two approaches can also be distinguished. The first involves an attacker gaining physical access to the ATM’s USB interfaces and directly copying or launching the malware from a flash drive. The second is remote implementation of malware, which involves preliminary compromise of the bank’s internal corporate network, obtaining administrative privileges (for example, in a software replication system) and further distribution of malicious code to the ATM network from a source that is legitimate from the point of view of the end devices themselves.
The second approach requires serious preparation and is implemented, as a rule, by organized criminal groups. Here we should mention such “professionals” in the field of targeted attacks on financial organizations as the hacker groups Anunak, Corkow, Buhtrap, Lurk, Lazarus, Metel, Cobalt. The latter made itself known loudly in July 2016, when the Taiwanese First Bank was attacked. The attackers simultaneously cleared dozens of ATMs throughout Taipei. This was an example of a well-planned, targeted logical attack on a financial institution. Hackers penetrated the bank's internal network through phishing emails and, using infrastructure vulnerabilities, gained access to the ATM management system. Then the “mules” acted.
In addition, ATM malware can be classified according to its applicability to the target of the attack. There are Malware aimed at specific models of ATMs from a specific manufacturer, and universal malware that works on all ATMs, regardless of the manufacturer.
The presence of universal Malware is due to the fact that all major ATM manufacturers support the CEN/XFS standard (from the English eXtensions for Financial Services), which provides a common API for managing various ATM modules. Thus, CEN/XFS can also be used to create malware so that it can “communicate” with the ATM in its native language.
The XFS API contains high-level functions for communicating with various ATM modules such as the banknote dispenser, PIN keypad, cash acceptance module, etc. High-level functions are provided through a common SDK, while low-level functions are provided through service providers, which are different for each ATM manufacturer. This architecture is very similar to the Win32 architecture, where developers use a high-level API to communicate with the OS kernel and various device drivers provided by individual hardware component manufacturers.

High-level architecture CEN/XFS
Known ATM Malware Families
Over the past 10 years, over 30 different families of ATM malware have been discovered. Let's look at some of the most popular and significant ones and try to highlight the common features and unique differences of each malware.
Number of malware samples by family
Ploutus
Ploutus is the malware family with the largest number of detected samples. Most of them were registered in Mexico. Ploutus is a typical example of a direct output utility. To download malware, attackers must have access to USB ports or a CD-ROM drive.
An example is one of the recent modifications - Ploutus-D, which was initially aimed at Diebold ATMs, widely used in the United States. However, the malware interacts with the ATM through the multi-vendor KAL Kalignite platform, and after a simple modification of the Ploutus-D code can be used to attack ATMs from other manufacturers.

One of the Ploutus interface options
Skimer
Skimer is one of the first logical attacks on ATMs. Functionally, this malware fully lives up to its name and is essentially a virtual skimming device that copies data from the magnetic stripe of a bank card.
In addition, Skimer is a backdoor and can be used for unauthorized withdrawal of money from an ATM. If the attacker knows the key to activate the program, the malware displays a menu from which you can dispense money from each of the four dispenser cassettes.
Most other families of ATM malware work on a similar principle. Attackers must provide themselves with physical access to the service area of the ATM in order to connect an external drive with malware. After introducing malware into the system, the attacker needs to enter a unique code to activate the cash withdrawal process.
Tyupkin (PadPin)
Real fame came to ATM malware with the emergence of the infamous Tyupkin Trojan, whose activity was first recorded in 2014. Since then, many ATMs around the world have been attacked.
A distinctive feature of Tyupkin is its ability to limit the time of its activity to specified hours and days of the week. Some of the first varieties of Tyupkin were initially only able to run on Sunday and Monday nights.

Tyupkin function for checking startup time
In addition, the Trojan has a self-defense function. Immediately before dispensing cash, Tyupkin disconnects all network connections so that if suspicious activity is detected on the bank’s side, the monitoring service will not be able to turn off the ATM, thereby interrupting the fraudulent operation.
Alice
The operating principle of Alice is the same as that of many other ATM malware. Installation requires physical access to the ATM system. Once launched, Alice asks for an access code to continue working. If the correct activation code is entered, the malware gains access to the banknote dispenser and allows cash to be dispensed.

Alice main interface
Cutlet Maker
In 2017, cybercriminals began selling “ATM Malware-as-a-Service” on the darknet. For $5,000, anyone can purchase a package of ready-to-use Cutlet Maker malware and video instructions on how to open an ATM. Those who purchase the service need to select a suitable ATM (the authors of the malware recommend Wincor Nixdorf), use the instructions for hacking its service part, download the malicious program and pay the service organizers for its activation (obtaining a unique session key) in order to start the process of issuing money.

Cutlet Maker main interface
In the case of Cutlet Maker, the potential consumer of the service may have minimal knowledge about the target of the attack. This example shows how such schemes reduce the entry threshold into this type of crime and lead to a significant increase in the number of cybercriminals.
FASTCash
FASTCash is a unique tool that the Lazarus hacker group used to attack financial organizations in more than 20 countries. Total for 2016-2018 Several tens of millions of dollars were stolen.
The peculiarity of FASTCash lies in the mechanism of its operation and its orientation to the IBM AIX OS. The hackers introduced a Trojan into a legitimate process on the application server of processing systems that control transactions in the ATM network and run AIX.
After compromising the server, the Trojan was able to create fake ISO 8583 messages (a standard that describes the transmission process and format of financial messages of systems that process bank card data), generating a response confirming a fraudulent cash withdrawal operation from ATMs. It should be noted that in all cases, successful attacks were made possible because financial institutions were using outdated versions of AIX - without the necessary security updates.

FASTCash operation diagram from Symantec report
This is another example of a targeted attack on financial organizations, in this case through processing systems. At the same time, the level of complexity and sophistication of FASTCash is very high and cannot be compared with any other “standard” ATM Malware.
Detection and counteraction. Best practice
To effectively counter attacks using ATM Malware, it is necessary to ensure comprehensive protection of the infrastructure, including the physical security of the ATMs themselves, the security of the software used in the system and all network segments interacting with ATMs.We list the main measures that each bank must take into account when organizing the protection of its own ATM network and successfully countering relevant threats:
- ATMs and all associated systems must be running the latest versions of the OS with the latest security updates installed.
- Disable autorun in Windows and the ability to boot from external media in the BIOS, set a strong password to protect BIOS settings.
- Create a functionally closed environment at ATMs, eliminating access to the desktop. RDP sessions must be protected by multiple authentication factors. Consider using a Privileged Access Management (PAM) system.
- Disable all unused system services and applications to eliminate additional attack vectors.
- Implement strong encryption of the connection between ATMs and the host.
- Apply integrity control mechanisms and software whitelisting (Whitelisting) to allow only trusted code to run. Follow the Default Deny principle: everything that is not clearly permitted is prohibited. Traditional signature-based AVPO is powerless against 0-day vulnerabilities and APT attacks used by hacker groups.
- Prohibit the ability to connect unauthorized external USB drives.
- Maintain a physically and logically segmented network environment within the organization. ATMs should not be located on the same network as employee workstations.
- Ensure reliable physical protection of ATMs and areas where they are located. The defense must be layered: ideally, the criminal’s intentions should be stopped even before he directly penetrates the “insides” of the ATM.
- Control and limit access of employees of service organizations servicing the ATM network.
- Conduct regular training on countering current threats for employees involved in the processes of servicing and monitoring the operation of ATMs.
- Organize online monitoring of the ATM network both in terms of ATM performance and continuity of operations, as well as the state of cybersecurity.
- Subscribe to receive threat intelligence feeds to quickly learn about all new threats against ATMs and related systems.
- Organize online monitoring of cybersecurity events based on aggregation of events in the SIEM system and generation of the necessary alerts for the purpose of prompt response.
Conclusions
ATM Malware can potentially bring significant benefits to attackers. In the 10 years since the appearance of the first malware created specifically to attack ATMs, more than 30 families of malware in this category, of varying degrees of complexity and with different functionality, have been discovered.While the vast majority of attacks on ATMs using malware are targeted and carried out by individual attackers or small groups, the potential ability to unload large amounts of cash simultaneously from several dozen ATMs is increasingly attracting professional hacker groups to this area, which use much more sophisticated and complex tools for targeted attacks on financial organizations.
However, despite the growing popularity of logical attacks, physical attacks still make up the vast majority of the total number of attacks on ATMs. To effectively counteract it, you need to take an integrated approach to ensuring the security of your network. Video monitoring of ATM installation areas, security alarms with a quick response team connected to the remote control, strengthening of ATM cases and safes, equipping with special sensors - these physical protection measures in combination with cyber defense means greatly enhance the overall level of security and reduce the desire of an attacker to attack you.
Organizing monitoring of cyber threats and prompt response is also an important step in ensuring comprehensive protection of the organization’s infrastructure. To solve this problem, Sberbank operates its own Security Operations Center (SOC), which provides continuous online monitoring and response to cyber threats. The combination of modern methods used to counter cyber threats allows us to successfully identify and repel attacks at the initial stages of their occurrence.
Active development of software for ATMs is a trend of today and the near future. Cybercriminals are not standing still, and their methods are becoming more sophisticated. Accordingly, investments by organizations in cybersecurity should not be a forced measure, but a conscious step by management (primarily business) - not only to protect their own infrastructure and data, but also to provide customers with a reliable and secure service.
(c) Valery Torchikov

10 лет изящного взлома. Как развивалось вредоносное ПО для банкоматов
В этой статье мы рассмотрим самые значимые из вредоносных программ и расскажем о лучших практиках обнаружения и противодействия таким программам.
 www.secuteck.ru
www.secuteck.ru
