Tomcat
Professional
- Messages
- 2,689
- Reaction score
- 951
- Points
- 113
How an AI ransomware can become a weapon of cybercriminals.
A group of scientists from the United States and Africa has developed an advanced method for creating a ransomware program that can bypass modern AI-based antivirus systems.
Ransomware poses a serious threat by blocking access to the victim's accounts, websites, or computer systems until a ransom is paid. Some types of ransomware attacks use Generative Adversarial Networks( GANS), deep learning architectures that improve their capabilities through trial and error.
GAN architectures consist of two artificial neural networks that compete with each other to create more and more advanced results in a particular task. In this case, this may mean analyzing the characteristics of malware that was able to circumvent security measures, and further improving software development.
The method created by scientists is called EGAN (Evolution Generative Adversarial Network). EGAN combines the Evolution Strategy (ES) and generative adversarial networks (GANS) to select actions that can change the ransomware file while maintaining its functionality. The ES agent in EGAN competes with an algorithm trained to recognize malware, testing various ways to modify ransomware files.
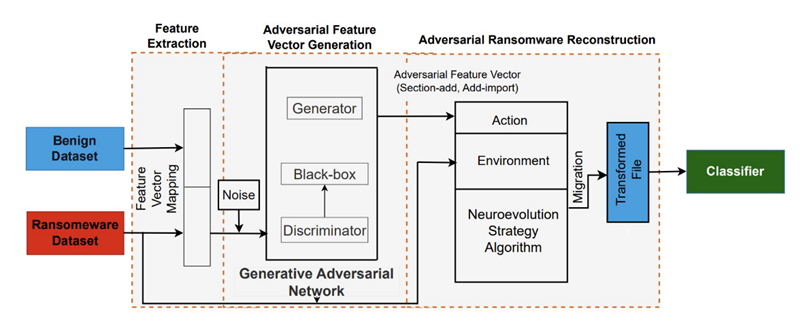
Diagram of EGAN, a ransomware sample generator
The approach determines the most optimal sequence of actions that leads to incorrect classification of ransomware. If the ES agent's manipulations are effective, the GAN generates signs that change the ransomware file so that it looks harmless.
The researchers tested their approach in a series of experiments and found that it allows you to create ransomware that successfully bypasses many commercial antivirus programs (including those based on AI). The results show the serious threat that such software poses, highlighting the need for more robust security measures.
In the future, the study may inspire the development of new cybersecurity techniques to protect computer systems from ransomware. In the meantime, the researchers plan to continue exploring other actions and additional PE (Portable Executable) file structures that can bypass dynamic analysis. Experiments show that the actions currently used lack the reliability necessary to avoid dynamic analysis.
A group of scientists from the United States and Africa has developed an advanced method for creating a ransomware program that can bypass modern AI-based antivirus systems.
Ransomware poses a serious threat by blocking access to the victim's accounts, websites, or computer systems until a ransom is paid. Some types of ransomware attacks use Generative Adversarial Networks( GANS), deep learning architectures that improve their capabilities through trial and error.
GAN architectures consist of two artificial neural networks that compete with each other to create more and more advanced results in a particular task. In this case, this may mean analyzing the characteristics of malware that was able to circumvent security measures, and further improving software development.
The method created by scientists is called EGAN (Evolution Generative Adversarial Network). EGAN combines the Evolution Strategy (ES) and generative adversarial networks (GANS) to select actions that can change the ransomware file while maintaining its functionality. The ES agent in EGAN competes with an algorithm trained to recognize malware, testing various ways to modify ransomware files.

Diagram of EGAN, a ransomware sample generator
The approach determines the most optimal sequence of actions that leads to incorrect classification of ransomware. If the ES agent's manipulations are effective, the GAN generates signs that change the ransomware file so that it looks harmless.
The researchers tested their approach in a series of experiments and found that it allows you to create ransomware that successfully bypasses many commercial antivirus programs (including those based on AI). The results show the serious threat that such software poses, highlighting the need for more robust security measures.
In the future, the study may inspire the development of new cybersecurity techniques to protect computer systems from ransomware. In the meantime, the researchers plan to continue exploring other actions and additional PE (Portable Executable) file structures that can bypass dynamic analysis. Experiments show that the actions currently used lack the reliability necessary to avoid dynamic analysis.
