In 2024, Facebook's ban has not been lifted, and in some areas it has even become more serious. Of course, there are some countermeasures to resolve this, thereby reducing the risk of permanent account loss. Here, we have carefully prepared a guide for you, which will explain in detail the reasons for the ban and the key and effective methods to restore your account to normal operation.
What caused the problem with your Facebook advertising account?
1) Non-fixed IP access:
The IP address of each login is changing, which may trigger Facebook's security alarm and misjudge it as abnormal activity, and then impose security restrictions or bans on the account. Therefore, it is recommended to adopt a stable and reliable access strategy to reduce unnecessary IP changes.
2) Improper cross-device login operation:
In the absence of appropriate account isolation measures, frequently changing computers or using the same device to log in to multiple Facebook accounts may violate its single user principle and trigger system monitoring and account blocking risks. To ensure account security, you should carefully manage cross-device logins and use professional tools such as BitBrowser to maintain the independence of fingerprint information such as cookies to avoid account association risks.
3) Violation of platform policy red line:
Facebook is extremely strict about content management. Any advertisement that touches on prohibited content will immediately face severe penalties such as account restrictions or closure. This type of blocking only affects advertisements, and the account itself will not be blocked. This is usually caused by what Facebook considers to be suspicious behavior. You can familiarize yourself with the restrictions in Facebook's official policies to avoid restrictions.
4) Illegal commercial marketing content:
Facebook strictly prohibits the use of images of celebrities and public figures in creativity, and does not allow misleading information (such as claiming that the offer can cure diseases 100%). As in the case of rule violations, the ban may target the advertising content of this account rather than the entire account. To unlock and restart the account, the illegal advertising content must be resolved and deleted.
This type of blocking occurs when Facebook detects errors and suspicious activities related to bank cards or payment data. To solve this problem, you need to ensure that the GEO of the campaign matches the location of the card and verify that the balance is positive. Of course, you can also try to link other bank cards.
To prevent account abuse, Facebook requires users to bind their mobile phone numbers to verify their identities. Accounts that are not bound to mobile phone numbers may increase the risk of being restricted due to unknown identities. Timely completion of mobile phone number binding will help improve account security.
Adding a large number of friends in a short period of time may be regarded as abnormal behavior, resulting in the account being temporarily locked by the system. It is recommended that users reasonably control the speed of adding friends according to natural social habits to maintain a healthy balance of social interaction.
If a new account is eager to post a large number of pictures and videos in the early stage, it may trigger the system review mechanism and be regarded as abnormally active. It is recommended that new accounts gradually increase the amount of content released to maintain a natural growth trend and avoid risks caused by excessive promotion.
Facebook is highly vigilant against counterfeit brands and materials with high content similarity. Its advanced detection mechanism can quickly identify potential risks. At the same time, if a newly established independent station lacks good user experience and reputation accumulation, it may also affect Facebook's trust assessment. Therefore, ensuring product originality and independent station quality is the key to improving account trust.
How to unblock a blocked Facebook account?
Method 1.
If some functions of your account are temporarily unavailable, you don't need to appeal, just wait. If it is not restored after about a week, try to unblock it again.
Method 2.
If your phone is already linked to your Facebook account, you only need to unblock it through the phone verification code (provided that you really have no serious violations)
Method 3.
Remove or change any elements that violate the rules in the campaign, delete all illegal content in the ad account you use, and there is a chance to restore the account.
Method 4.
Check your payment method and bank card, verify the accuracy of the data, correct any errors, and verify your account again. There is also a possibility of restoring the ad account.
Method 5.
You select several well-known and closely connected friends from your friends, and then send them a security code. Then, contact them to get the verification code they received from Facebook, use this verification code to unlock your account, and follow the prompts given by the system to achieve unblocking. For individual users, if you can submit relevant information seriously, the probability of successful unblocking is more than 90%.
Method 6.
Restart the campaign and wait 2-3 days, which will help if your ad account is frozen.
Method 7.
If none of the above methods can help you, and your account has no other violations, you can contact Facebook support. Sometimes, Facebook accounts may not have such a button, or the account has been completely blocked. In this case, you can write to support from another account and attach a link to the blocked profile, and upload the ID card photo of the account application in the attachment to clearly indicate that the account is indeed operated by yourself. The next step is to wait patiently for the administrator to reply and clearly explain the reason for your appeal. Once it is confirmed that the violation is locked, your account will be unblocked soon. If you don’t know how to explain to the administrator, don’t worry. There is a detailed email content writing tutorial at the end of the article to help you explain that this is a wrong ban.
In the process of using Facebook advertising accounts, it is very important to understand how to unblock the blocked accounts, but it is also essential to learn how to protect the accounts that are still in operation. It is the best solution to plan ahead and avoid problems before the accounts have problems. Follow the editor to see how to safely operate multiple Facebook accounts.
Prevent Facebook Advertising Account Blocking through
In the process of
multi-account marketing on social media, everyone must pay great attention to account security issues, especially to prevent Facebook accounts from being blocked. Especially for social media practitioners, they often operate multiple Faceboo accounts. However, this multi-account operation model hides huge risks and is extremely easy to trigger Facebook account blocking strategies.
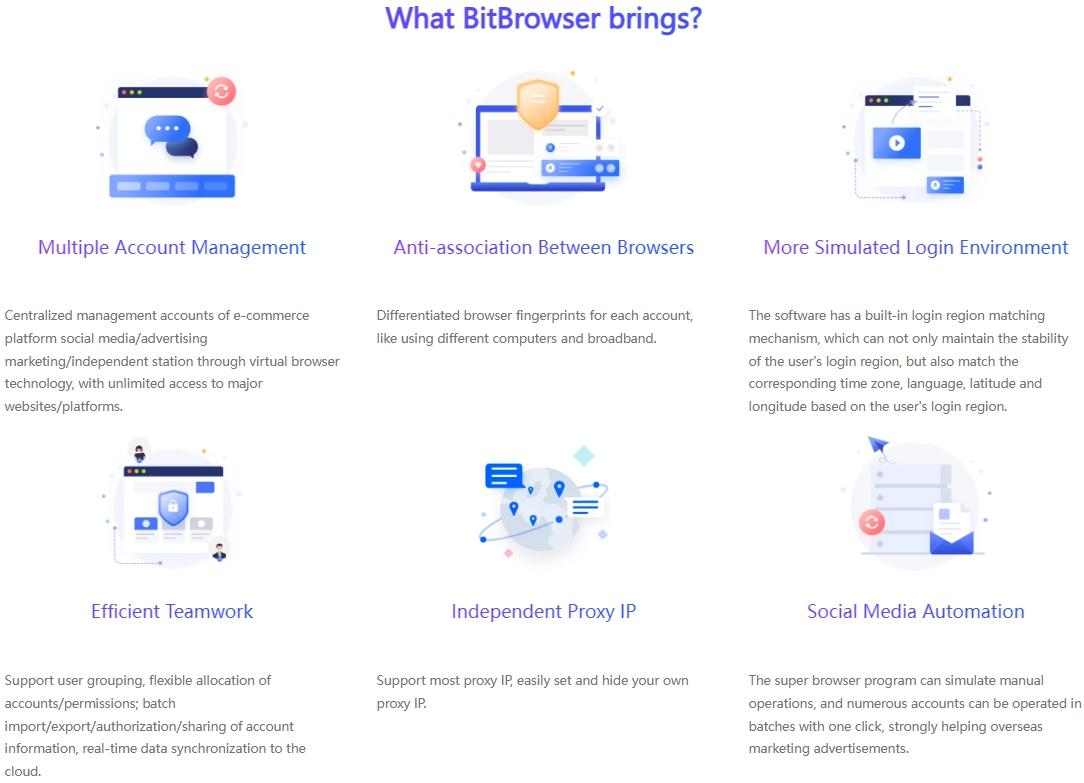
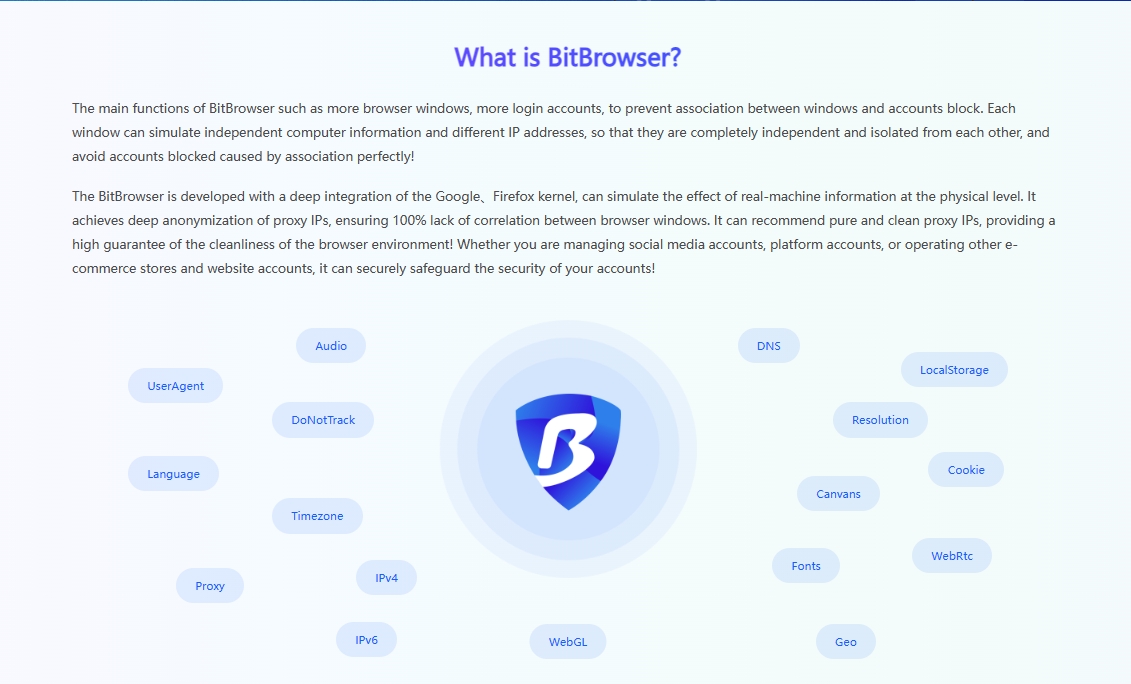
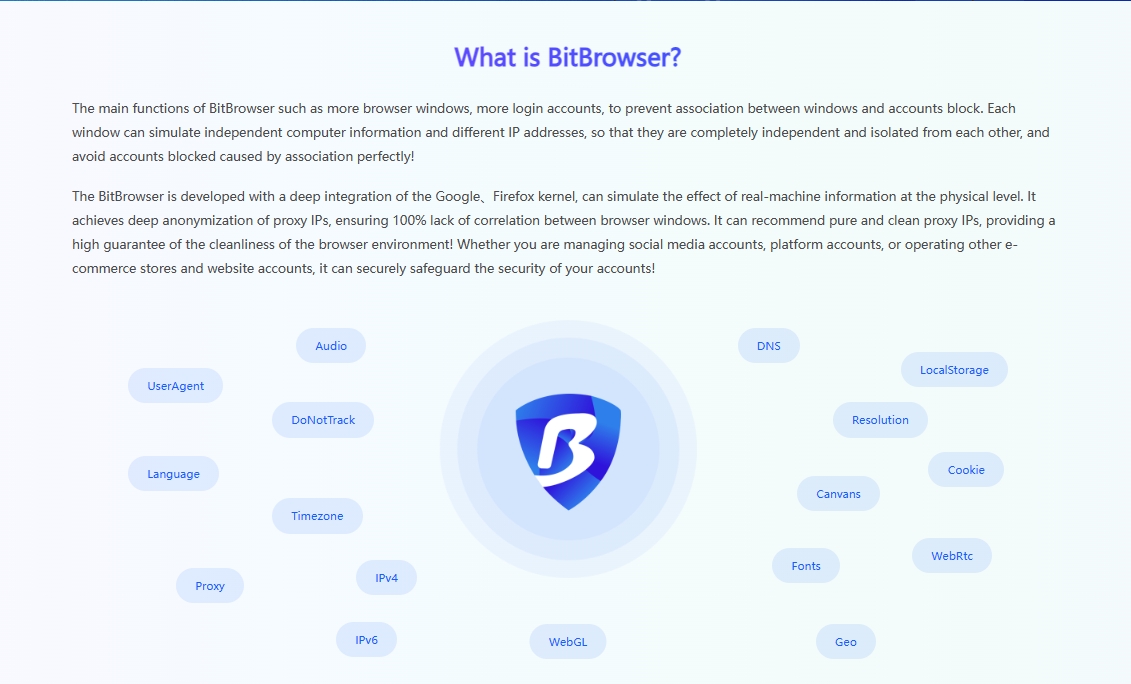
In order to minimize the possibility of Facebook being blocked, BitBrowser is undoubtedly your best choice for multi-account management. Traditional browsers have obvious shortcomings when dealing with multi-account management. Because they are easy to leave browser fingerprint information, once Facebook finds that multiple accounts are logged in from the same device, it may be identified as a violation, and then restrict or even block the account.
BitBrowser Fingerprint Browser is unique. It can create a unique browsing environment for each social media account. With the help of advanced browser fingerprint technology, it can cleverly simulate different devices and network scenarios. Even if you log in to multiple accounts such as Instagram, Facebook, Amazon, etc. on the same device, the operation of each account seems to be performed on completely different computers and locations.
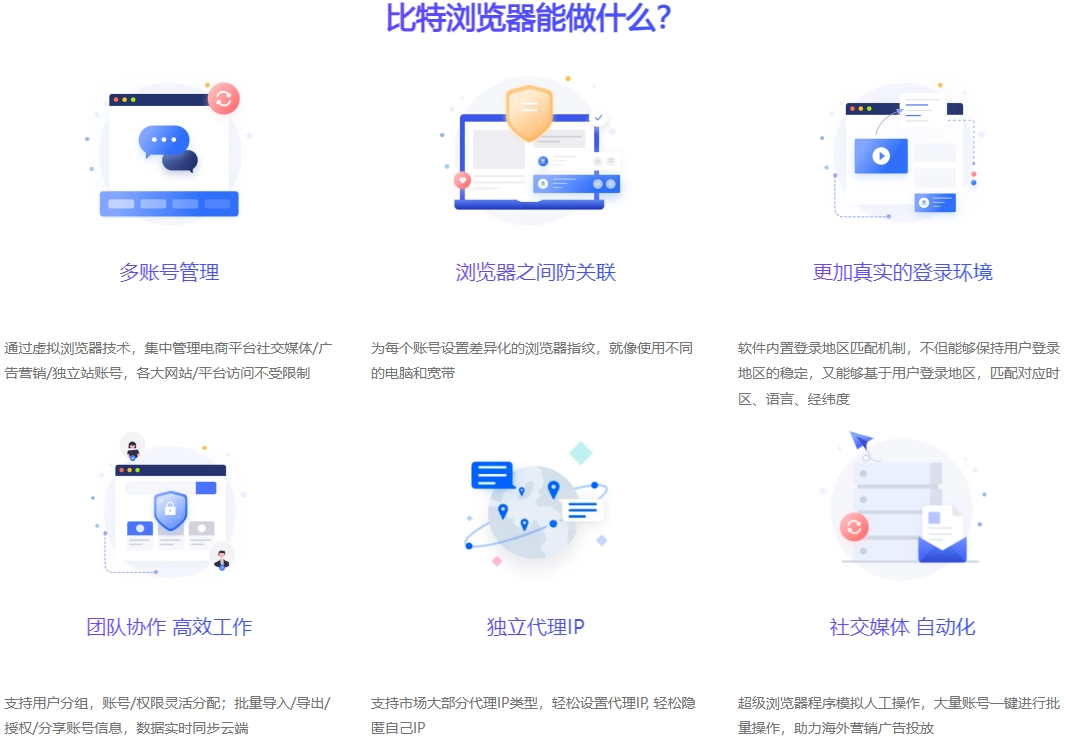
In addition to effectively avoiding account association, BitBrowser also has the following outstanding functions and significant advantages:
RPA Automation: This free and practical function can automatically complete repetitive operations such as following, liking and commenting, which can significantly increase the speed of Facebook's fan growth. At the same time, it can also maintain the randomness of human behavior and cleverly circumvent Facebook's automated detection mechanism.
Window Group Control: When you need to post the same content on multiple accounts or perform unified operations, the window group control function can greatly improve your work efficiency.
Guarantee account security: The global setting function of BitBrowser can be described as a "solid fortress" of multi-layer security protection, such as providing email remote login reminders, and being able to fill in the account's 2FA key when creating an environment, providing strong protection for account security.
How to explain to Facebook administrators that this was a wrongful ban?
1. Greet Facebook employees.
A polite opening statement shows that you are committed to a constructive attitude to solve the problem.
2. Describe the situation.
Next, inform the other party that your account has been blocked, clearly indicate the name or ID of the account, and express your view that the ban is unfair.
3. Provide useful information about yourself.
You can show that you are an entrepreneur or a representative of a small business that only promotes legal goods and services.
4. Prove the wrong nature of the ban.
Emphasis that you did not break any rules.
5. Provide alternatives.
Depending on the type of ban, you can point out that the mistake has been discovered and corrected. Or, you can request a review of your profile and ask why the ban was caused.
6. Don't forget to add a call to action.
At the end of the message, you should ask support to help unlock the account. You can also add that you will be extra careful in the future to avoid similar problems.
7. Express gratitude.
The letter ends on a positive note and shows a willingness to engage in constructive dialogue. You can also express your hope for a prompt response.
Some suggestions on the content of the email:
① The letter should be concise and clear.
Ideally, keep it to two or three paragraphs.
② Be polite.
Aggression, profanity, and insults are absolutely unacceptable, otherwise you may not be able to wait for the unlock.
③ Provide proof.
As evidence of the problem or that the violation has been corrected, relevant screenshots should be attached. For example, you have removed the banned elements from the creative.
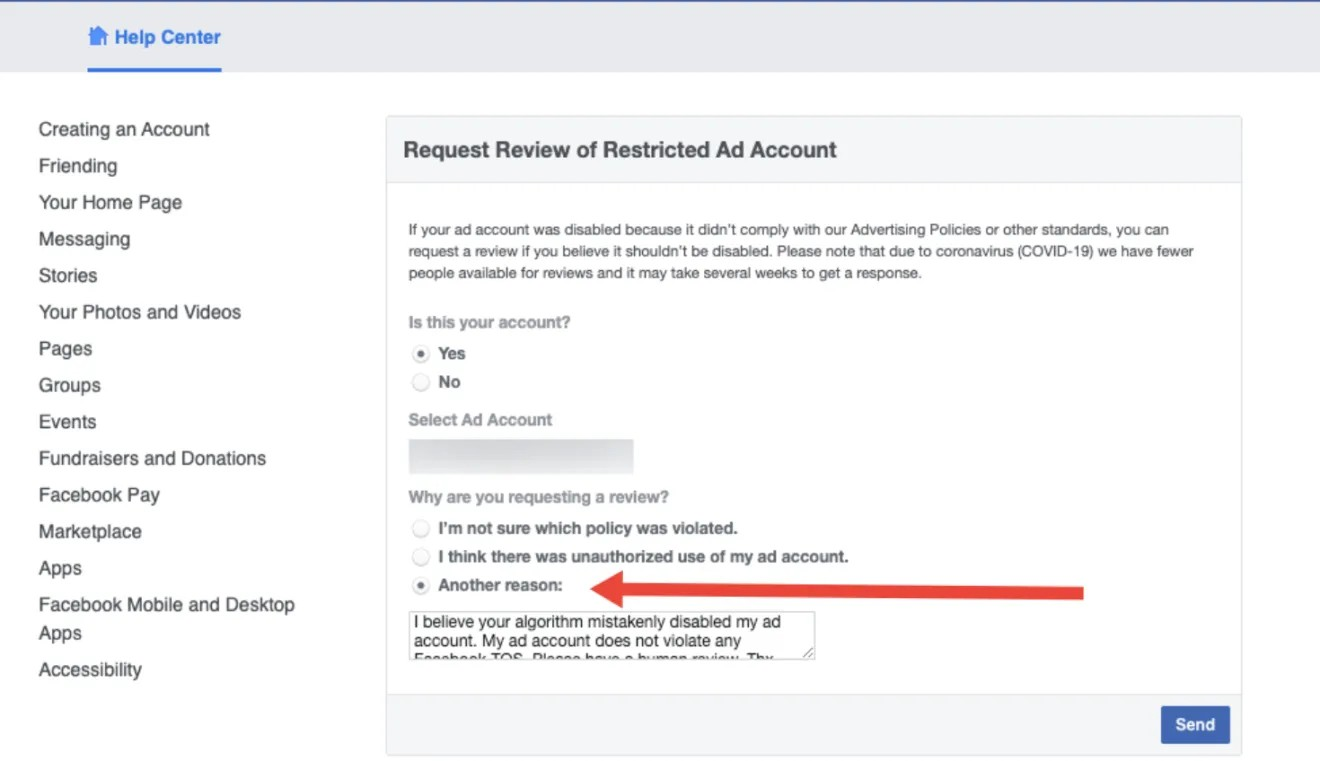
④ Write a personalized message yourself instead of using a template. .
The other options in the ticket are templates, in which you need to fill in the information. However, the support team is not very enthusiastic about reviewing such templates. The "another" option allows you to write a unique letter.
⑤ Business style.
It is important to maintain a formal business communication style and abandon all emotions.
⑥ Express genuine surprise and confusion.
You can create a situation, for example, you are an honest marketer who has been promoting legitimate goods or services, but was suddenly blocked for no reason.
⑦ Communicate in English.
English-speaking support staff usually respond faster.
When sending emails to Facebook management, an important principle is to make them believe that you are a potential customer who is ready to invest a lot of money in advertising on Facebook, and Facebook has no benefit in losing you.
Summary:
I believe everyone has already understood how to unblock a blocked Facebook account. By correcting the illegal content of the blocked account and sending email feedback to Facebook management, I believe everyone's account problems can be solved. At the same time, it is also essential to avoid the blocking of Facebook accounts in advance.
BitBrowser is a tool specially designed for Facebook marketers. It can not only protect the security of marketers' social media accounts, but also increase sales. Download BitBrowser now and get 10 permanent free windows immediately. Click to download BitBrowser to get a more convenient solution.