Tinder is a dating app with extremely high popularity worldwide. It helps people build romantic emotional bonds with advanced technology. It was born in 2012 and attracts attention with its simple style and innovative design. Sean Rad, Jonathan Badeen and Justin Mateen are the founders of Tinder.
Why has Tinder achieved such remarkable success?
This is mainly due to its excellent strategic marketing, localization strategy and continuous improvement. In the dating app market, various niches are emerging one after another, and Tinder is able to stand out as a versatile platform. It provides users with a rich variety of dating options and experiences while keeping the process simple and pleasant. For many independent website owners and cross-border marketers, Tinder has become an indispensable and important tool in promotion work. However, novices who are new to the world of Tinder often fall into the trouble of "instant ban", which makes people feel lost. To help you get out of this dilemma, here is a detailed Tinder anti-association guide to help you get started smoothly!
What caused your Tinder account to be blocked?
Like other social giants, Tinder strictly controls the ecological environment of the community, and any violations will be severely punished. Coupled with the particularity of the mainland network environment, Tinder's association detection mechanism is extremely strict, and its degree is no less than Tinder. Common account minefields mainly cover:
Violation of terms and agreements or community guidelines: If a user violates the terms and agreements or community guidelines, his account will be automatically blocked by the server. Sometimes, blocked users cannot restore their accounts because they have been permanently banned from using the application. In order to avoid trouble during use, you'd better read the relevant guidelines of the application carefully.
Similar registration information: If personal information is repeated or shared with others, the system will identify it as impersonation and ban it mercilessly.
Improper use of chat language: During the chat process, if a user uses inappropriate language, such as swear words, racist comments, and homophobic remarks, other end users can report it. Tinder is committed to creating a safe and healthy environment for everyone looking for a match.
Device fingerprint overlap: Tinder strictly investigates the situation of multiple accounts on one device, and its device identification technology is designed to ensure the independence of each account. If your device has logged into other accounts before, it is very likely to trigger an association warning, resulting in the account being blocked.
IP address abnormality: It is absolutely not allowed to have one IP corresponding to multiple accounts, and frequent changes or sharing of IPs are also very dangerous. The platform will regard such behavior as an abuse of resources and impose penalties.
How to unblock a blocked Tinder account? The latest solution.
Tinder's official policy clearly states that blocking an account is usually the final decision, but this is not without room for maneuver. It has to be said that Tinder is quite firm in its attitude towards blocking accounts. The official statement of their blocking decision is irrevocable, but as long as you file an appeal, there is still a slight possibility of unblocking. If you get a message saying you've violated the Terms of Use when you're logging into the app or website, that means your account has been blocked.
If you subscribed to Tinder Gold or Tinder Plus and subscribed through your Apple ID or Google Play Store account, cancel your subscription here to prevent further charges.
If you signed up for Tinder Gold or Tinder Plus using the credit card option or on the Tinder website, your subscription will be automatically canceled.
Can I appeal a ban on Tinder?
Yes, it's the only official way to get unblocked.
Yes, it's the only official way to get unblocked. Although Tinder claims that they don't offer appeals for bans, you can actually submit a request here. Select "Account login issues," then "Can't log in, my account is blocked." Enter your information and explain why you think you should not have been blocked. After that, they may be able to unblock your account.
For example, if it's because of a misunderstanding by other users, you can try to explain: "I know that a matched user is unhappy with me, but I think it's a misunderstanding. Can you check and help me get my account unblocked?"
If you don't know why you were blocked, ask the other party to review your account. You can say: "I don't think I violated any rules. This must be a mistake. Can you check my activities and find out what the problem is?"
Finally, end your description with honest and concise words, don't do it too much. If you are lucky enough and meet a kind reviewer, they may help you get your account unblocked.
How to prevent Tinder account blocking? 2024 version
Personalize registration information: Make sure each account has a unique name (use English name), age, location and photo. When registering a new account, never use old photos or similar information, and once the registration is completed, never change it easily.
Optimize the network environment: In order to prevent the association between accounts, you need to carefully plan the network environment. Use BitBrowser and proxy IP to create an independent virtual environment for each account, effectively avoiding the risk of device blocking. At the same time, remember to clean the browser cache regularly to keep the network environment pure.
Smart matching strategy: When a new account logs in for the first time, you should wait for half an hour to stabilize the system. When matching, do not be too eager, control the rhythm, and avoid frequent operations to attract attention. In addition, follow the habits of real users and add friends and groups moderately.
Content security specifications: Strictly abide by the rules of the platform and stay away from sensitive words and topics. When communicating with customers, guide the other party to provide contact information to reduce your own exposure risk.
Reasons for the ban of Tinder social platform, and how to prevent bans and unbans
BitBrowser Your Protection of Multiple Tinder Accounts
In daily social and professional activities, managing multiple Tinder accounts has become a necessary task for many people, but this work is often accompanied by considerable challenges, especially how to ensure the independence of accounts, prevent mutual associations, and avoid the risk of account bans.
Given the complexity and potential risks of multi-account management, it is particularly important to seek a management strategy that is both efficient and secure. At this time, fingerprint browsers become an ideal solution. Such tools use advanced technology to simulate different browser environments and device features, and tailor independent browser profiles for each account, so that the login activities of each account seem to occur in completely independent physical devices and network environments.
BitBrowser optimizes multi-account management
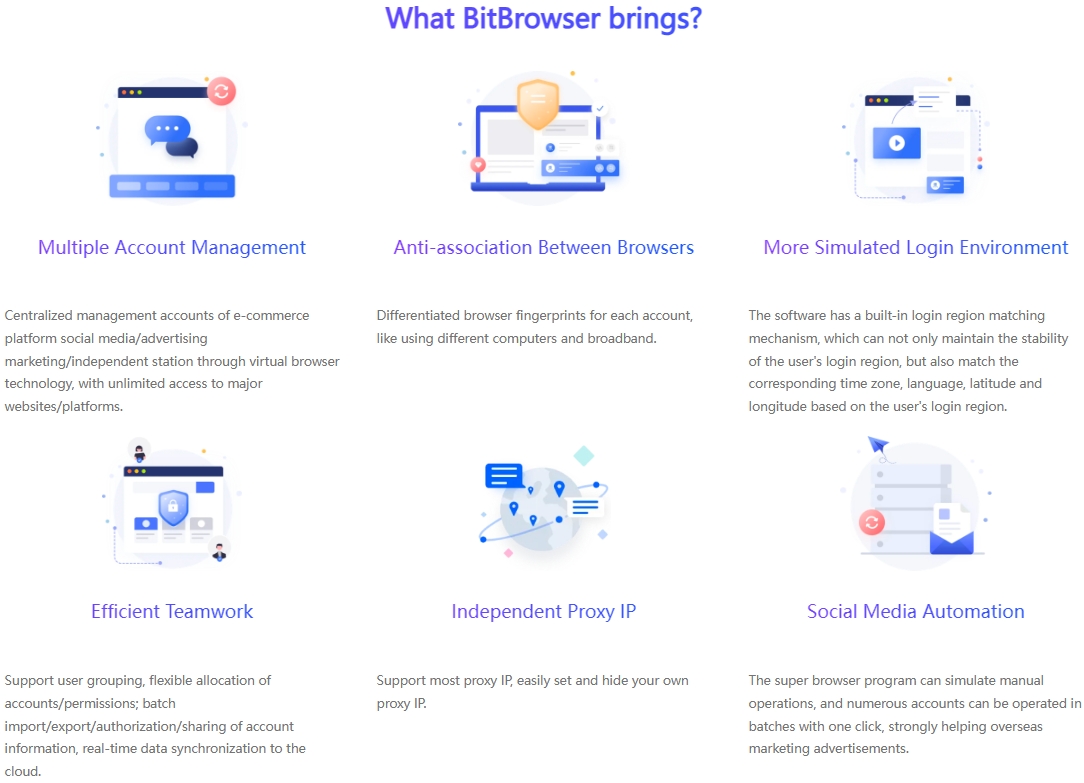
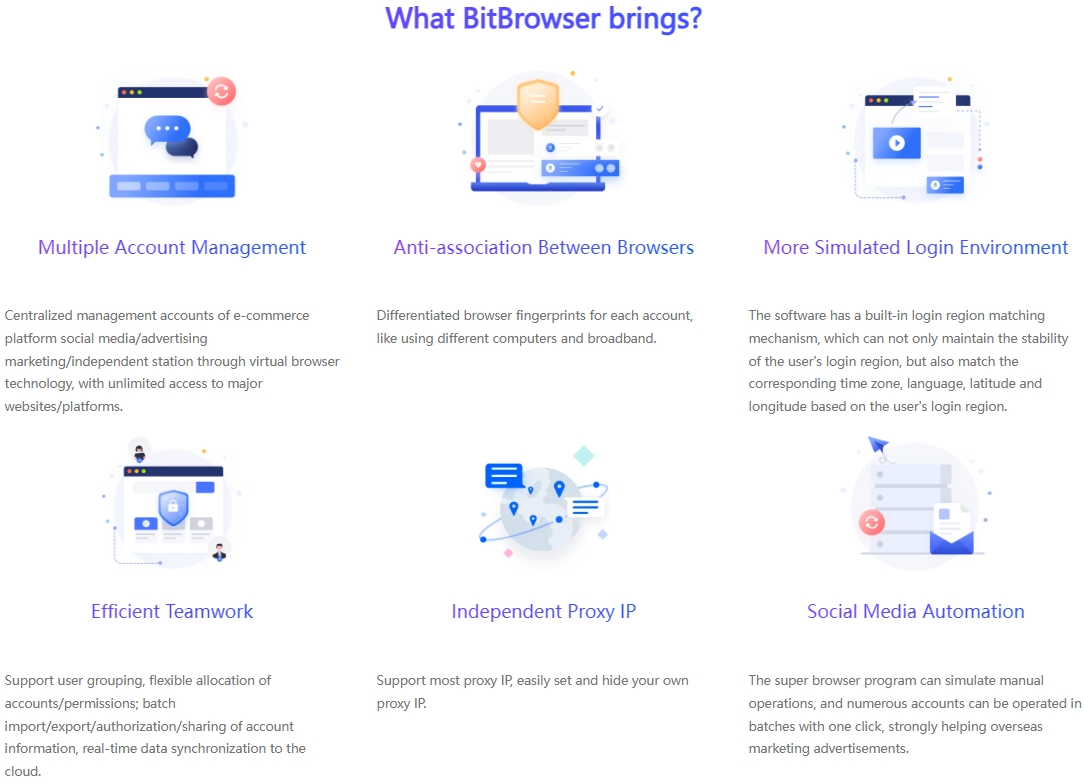
As an advanced fingerprint browser designed for multi-account management, BitBrowser greatly simplifies the anti-association management process of Tinder accounts, allowing users to easily manage multiple accounts without worrying about risks.
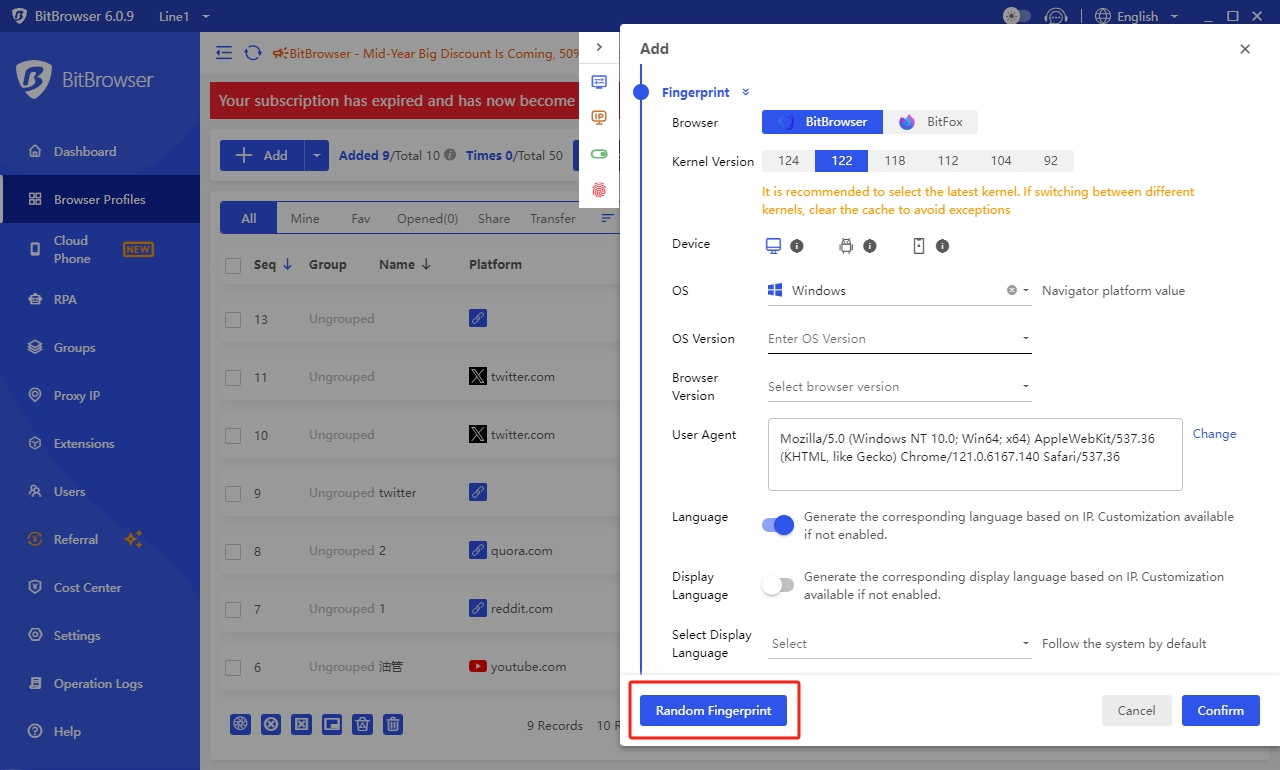
Account isolation technology: BitBrowser generates unique browser profiles, simulates different operating systems, browser versions and cookie records, etc., to create a completely isolated login environment for each Tinder account, effectively preventing mutual interference and association between accounts.
Window synchronization function: In order to improve operational efficiency, BitBrowser also provides a window synchronization feature, allowing users to synchronize operations between different browser windows, such as batch editing content or executing unified instructions, which greatly saves time and energy.
Automated workflow: With the help of RPA (Robotic Process Automation) technology, BitBrowser can automatically perform a series of tedious account management tasks, including but not limited to automatic login, content publishing, interaction (likes, comments), etc., greatly reducing the user's workload.
By adopting BitBrowser, users can not only achieve efficient and secure management of Tinder multiple accounts, but also significantly improve work efficiency while protecting account security. Both individual and corporate users can benefit greatly from it and enjoy a smoother and worry-free social media management experience.
Summary:
Mastering the above anti-blocking and unblocking tips, you have taken the first step towards success. But please remember that the security journey begins with registration and continues in daily use. Always maintain a high degree of vigilance and carefully maintain the security of your account, so that you can bravely move forward in this vast blue ocean of social networking and reap a lot of rewards. Once an account encounters an accident, it will not only lose customer resources, but it is also likely to have an adverse impact on your brand image and long-term development. By adopting
BitBrowser, users can not only achieve efficient and secure management of Tinder multiple accounts, but also significantly improve work efficiency while protecting account security. Both individual and corporate users can benefit greatly from it and enjoy a smoother and worry-free social media management experience.