Father
Professional
- Messages
- 2,602
- Reaction score
- 838
- Points
- 113
Experts from Palo Alto are doing everything possible to protect users, but even this may not be enough.
An exploit was recently discovered on the Internet for a critical vulnerability in the PAN-OS software used in Palo Alto Networks firewalls. Vulnerability CVE-2024-3400, which we wrote about earlier, allows attackers to execute arbitrary code with superuser rights on network screens with GlobalProtect or telemetry collection enabled.
If earlier the company actively offered users to simply disable the above functions in order to avoid an attack, now experts were surprised to find that these measures were ineffective. Now the main recommended action is to install the latest PAN-OS software updates.
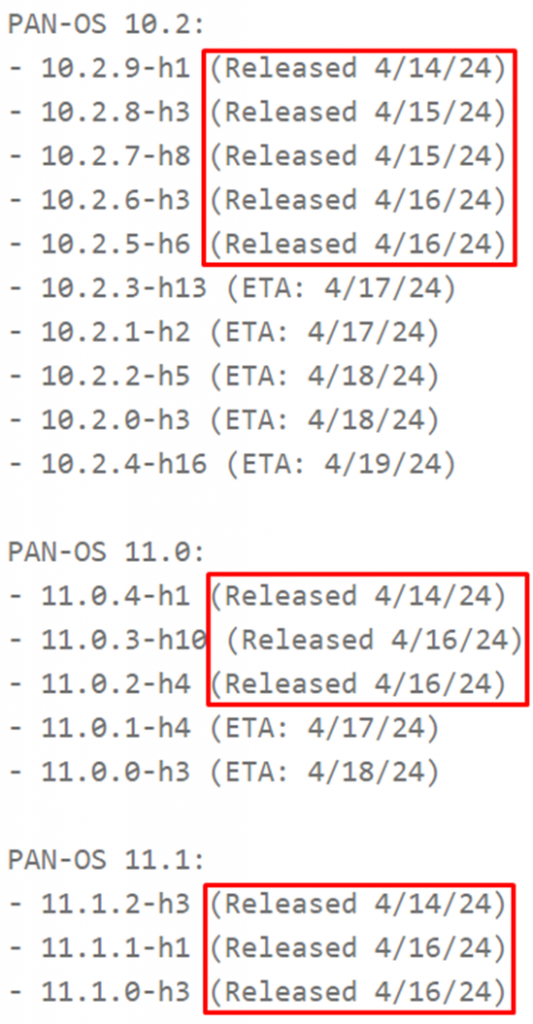
The security flaw itself was discovered in PAN-OS versions 10.2, 11.0 and 11.1. According to information from Palo Alto Networks, the release of fixes is in full swing, and at the time of publication of this news, fixes have already been released for most vulnerable software builds.
However, according to researcher Yutaka Sejiyama, currently more than 82,000 Palo Alto Networks devices are still at risk due to this vulnerability, most of them located in the United States.
Experts from the watchTowr Labs analyzed the vulnerability and presented a proof-of-concept demonstrating how command injection can manipulate devices that are not protected by the latest updates.
In addition, it became known that the vulnerability was already actively used in March of this year to install bookmarks in firewalls using Upstyle malware, which allowed attackers to gain access to internal networks and steal data. It is assumed that the state-sponsored UTA0218 group is behind the attacks, but experts have not yet linked it to any particular country.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) recently added CVE-2024-3400 to its catalog of known exploited vulnerabilities and required federal agencies to secure their devices by April 19.
For Palo Alto Networks users with a subscription to "Threat Prevention", activation of a special protection tool" Threat ID 95187 " is available, which helps block attacks using the ill-fated vulnerability CVE-2024-3400.
An exploit was recently discovered on the Internet for a critical vulnerability in the PAN-OS software used in Palo Alto Networks firewalls. Vulnerability CVE-2024-3400, which we wrote about earlier, allows attackers to execute arbitrary code with superuser rights on network screens with GlobalProtect or telemetry collection enabled.
If earlier the company actively offered users to simply disable the above functions in order to avoid an attack, now experts were surprised to find that these measures were ineffective. Now the main recommended action is to install the latest PAN-OS software updates.
The security flaw itself was discovered in PAN-OS versions 10.2, 11.0 and 11.1. According to information from Palo Alto Networks, the release of fixes is in full swing, and at the time of publication of this news, fixes have already been released for most vulnerable software builds.

However, according to researcher Yutaka Sejiyama, currently more than 82,000 Palo Alto Networks devices are still at risk due to this vulnerability, most of them located in the United States.
Experts from the watchTowr Labs analyzed the vulnerability and presented a proof-of-concept demonstrating how command injection can manipulate devices that are not protected by the latest updates.
In addition, it became known that the vulnerability was already actively used in March of this year to install bookmarks in firewalls using Upstyle malware, which allowed attackers to gain access to internal networks and steal data. It is assumed that the state-sponsored UTA0218 group is behind the attacks, but experts have not yet linked it to any particular country.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) recently added CVE-2024-3400 to its catalog of known exploited vulnerabilities and required federal agencies to secure their devices by April 19.
For Palo Alto Networks users with a subscription to "Threat Prevention", activation of a special protection tool" Threat ID 95187 " is available, which helps block attacks using the ill-fated vulnerability CVE-2024-3400.

