Man
Professional
- Messages
- 3,222
- Reaction score
- 1,199
- Points
- 113
0Day unlocks Palo Alto firewalls worldwide.
On November 8, Palo Alto Networks called on its customers to urgently strengthen the protection of firewall management interfaces due to rumors of a new vulnerability. Experts from Rapid7 also tracked information about a possible zero-day vulnerability, but until recently, the reports were not confirmed.
On November 14, the company updated its warning, reporting the documented exploitation of a vulnerability in remote command execution without authentication. Malicious activity affected a limited number of firewall management interfaces open on the Internet.
The company is currently actively investigating the incident, but at the moment there is no information about the CVE or fix for the identified vulnerability.
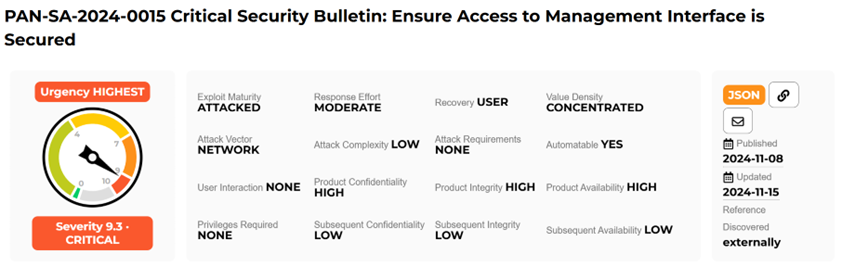
Summary of the vulnerability in the bulletin (PAN-SA-2024-0015)
According to the information from the bulletin:
At the same time, it is noted that Prisma Access and cloud NGFWs are not affected at the moment. If the situation changes, the company will update its data.
Until a patch is released, users of Palo Alto Networks products are encouraged to ensure that access to the management interface is limited to trusted internal IP addresses and that the interface is not accessible from the Internet. For additional instructions, please refer to the Palo Alto Networks bulletin.
Also, users are advised to check what devices can be opened on the Internet and take action if necessary. Experts strongly recommend that you read the instructions and follow all the security settings specified in the notification.
Source
On November 8, Palo Alto Networks called on its customers to urgently strengthen the protection of firewall management interfaces due to rumors of a new vulnerability. Experts from Rapid7 also tracked information about a possible zero-day vulnerability, but until recently, the reports were not confirmed.
On November 14, the company updated its warning, reporting the documented exploitation of a vulnerability in remote command execution without authentication. Malicious activity affected a limited number of firewall management interfaces open on the Internet.
The company is currently actively investigating the incident, but at the moment there is no information about the CVE or fix for the identified vulnerability.

Summary of the vulnerability in the bulletin (PAN-SA-2024-0015)
According to the information from the bulletin:
- The risk of hacking is minimal if access to the management interface is restricted;
- At the moment, there are no specific indicators of compromise (IoC));
- If the interface has access to the Internet, it is recommended to monitor for suspicious activity, such as unknown configuration changes or the appearance of new users.
At the same time, it is noted that Prisma Access and cloud NGFWs are not affected at the moment. If the situation changes, the company will update its data.
Until a patch is released, users of Palo Alto Networks products are encouraged to ensure that access to the management interface is limited to trusted internal IP addresses and that the interface is not accessible from the Internet. For additional instructions, please refer to the Palo Alto Networks bulletin.
Also, users are advised to check what devices can be opened on the Internet and take action if necessary. Experts strongly recommend that you read the instructions and follow all the security settings specified in the notification.
Source

