How Operation MidnightEclipse has become a headache for security teams around the world.
Last Friday, April 12, we told you about a new vulnerability in the PAN-OS operating system used in Palo Alto Networks network gateways. Then the company said that it was aware of cases of real exploitation of the CVE-2024-3400 vulnerability, but experts did not disclose detailed technical details.
Now, Volexity experts responsible for detecting the error, as well as Unit 42 specialists from Palo Alto Networks itself, have joined the information, describing in as much detail as possible both the vulnerability itself and the attacks using it.
It is reported that the first cases of exploitation of CVE-2024-3400 were recorded on March 26, a few weeks before the actual detection, and therefore the vulnerability receives zero-day status.
Palo Alto experts track attacks using this breach under the code name "MidnightEclipse", noting that a lone hacker is behind them, whose origin has not yet been determined.
The vulnerability, which received the highest CVSS criticality rating (10 points), allows unauthorized attackers to execute arbitrary code with administrator rights on Palo Alto Networks network firewall devices. The issue affects firewall configurations on PAN-OS 10.2, 11.0, and 11.1 with GlobalProtect gateway options enabled and telemetry collection enabled.
Attackers use the identified vulnerability to create a cron job that requests commands from an external server every minute and executes them. These commands may include Python scripts that install additional malicious modules.
The most interesting aspect of the attack is that both files used to extract commands and write results are legitimate firewall-related files:
It is reported that the attacker specifically creates network requests to non-existent web pages in order to inject code into the error log of the web server, which is then used for further malicious actions.
Cyber experts from the company Volexity noted that the attackers used Palo Alto firewalls to create a reverse connection, download additional tools, penetrate internal networks and steal data. It is not yet possible to estimate the full scale of the campaign.
The US cybersecurity agency CISA has already added the breach to its catalog of known exploited vulnerabilities, requiring federal agencies to apply the necessary patches by April 19.
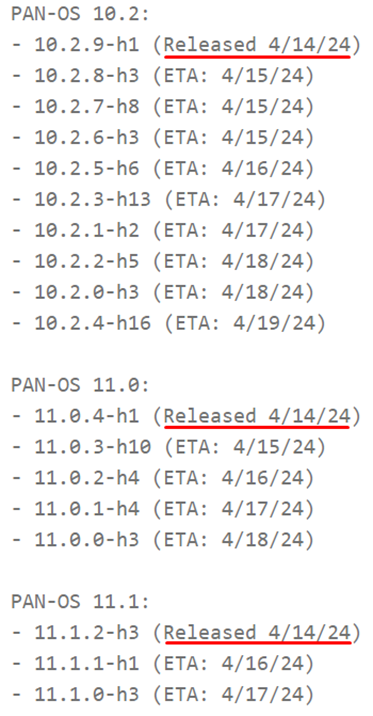
Previously, Palo Alto Networks planned to release fixes no later than April 14, but at the time of publication of the news, the vulnerability page indicates that only some vulnerable PAN-OS releases have been fixed, in particular, 10.2.9-h1, 11.0.4-h1 and 11.1.2-h3. It is quite possible that they were the most common ones, so the company started with them. For another 15 PAN-OS releases, approximate patch release dates vary from April 15 to April 19.
In the context of these developments, experts recommend that organizations actively monitor for signs of lateral movements in their networks, as well as monitor the release of fixes for the used PAN-OS releases and update them as soon as possible.
Last Friday, April 12, we told you about a new vulnerability in the PAN-OS operating system used in Palo Alto Networks network gateways. Then the company said that it was aware of cases of real exploitation of the CVE-2024-3400 vulnerability, but experts did not disclose detailed technical details.
Now, Volexity experts responsible for detecting the error, as well as Unit 42 specialists from Palo Alto Networks itself, have joined the information, describing in as much detail as possible both the vulnerability itself and the attacks using it.
It is reported that the first cases of exploitation of CVE-2024-3400 were recorded on March 26, a few weeks before the actual detection, and therefore the vulnerability receives zero-day status.
Palo Alto experts track attacks using this breach under the code name "MidnightEclipse", noting that a lone hacker is behind them, whose origin has not yet been determined.
The vulnerability, which received the highest CVSS criticality rating (10 points), allows unauthorized attackers to execute arbitrary code with administrator rights on Palo Alto Networks network firewall devices. The issue affects firewall configurations on PAN-OS 10.2, 11.0, and 11.1 with GlobalProtect gateway options enabled and telemetry collection enabled.
Attackers use the identified vulnerability to create a cron job that requests commands from an external server every minute and executes them. These commands may include Python scripts that install additional malicious modules.
The most interesting aspect of the attack is that both files used to extract commands and write results are legitimate firewall-related files:
- /var/log/pan/sslvpn_ngx_error.log
- /var/appweb/sslvpndocs/global-protect/портал/css/bootstrap.min.css
It is reported that the attacker specifically creates network requests to non-existent web pages in order to inject code into the error log of the web server, which is then used for further malicious actions.
Cyber experts from the company Volexity noted that the attackers used Palo Alto firewalls to create a reverse connection, download additional tools, penetrate internal networks and steal data. It is not yet possible to estimate the full scale of the campaign.
The US cybersecurity agency CISA has already added the breach to its catalog of known exploited vulnerabilities, requiring federal agencies to apply the necessary patches by April 19.
Previously, Palo Alto Networks planned to release fixes no later than April 14, but at the time of publication of the news, the vulnerability page indicates that only some vulnerable PAN-OS releases have been fixed, in particular, 10.2.9-h1, 11.0.4-h1 and 11.1.2-h3. It is quite possible that they were the most common ones, so the company started with them. For another 15 PAN-OS releases, approximate patch release dates vary from April 15 to April 19.

In the context of these developments, experts recommend that organizations actively monitor for signs of lateral movements in their networks, as well as monitor the release of fixes for the used PAN-OS releases and update them as soon as possible.
