Palo Alto has revealed more details about a critical vulnerability in PAN-OS.
Palo Alto Networks has revealed details of a critical vulnerability in the PAN-OS operating system, which has become the object of active exploitation.
Vulnerability CVE-2024-3400 (CVSS score: 10.0) is a combination of two bugs in PAN-OS versions 10.2, 11.0, and 11.1. The first bug is related to insufficient verification of the session ID format by GlobalProtect before saving them, which allows an attacker to save files with arbitrary names. The second problem is that the system mistakenly trusts these files by using their names as part of system commands. Together, two vulnerabilities allow you to execute commands on behalf of the system without authentication.
Palo Alto experts track attacks using this vulnerability under the code name "MidnightEclipse", noting that they are backed by a threat entity codenamed UTA0218, whose origin has not yet been determined.
The attack consists of two stages: at the first stage, the hacker sends specially formed requests containing the command, and at the second stage, the system task that runs on a schedule uses this file name to execute the command.
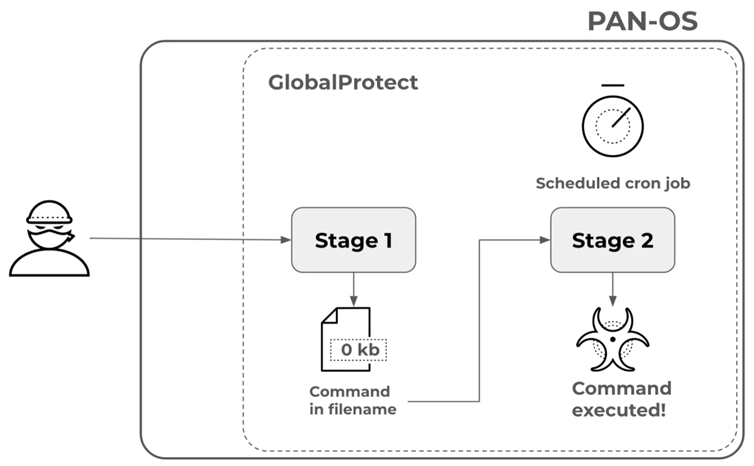
Attack stages
Experts from Unit 42 and Volexity emphasized that the initial mechanism for preserving the vulnerability included installing a cron task for downloading and executing malicious code using the GOST tool.
Volexity experts noted that the attackers used Palo Alto firewalls to create a reverse connection( Reverse Shell), download additional tools, penetrate internal networks and steal data.
After identifying the vulnerability, Palo Alto Networks released updates for all affected versions of the operating system to prevent further attacks. It was also confirmed that the presence of telemetry on the device does not affect the exploitation of the vulnerability.
The CISA agency added the vulnerability to its catalog of known exploited vulnerabilities (KEV) and called on federal agencies to ensure the security of their devices by April 19, 2024.
Also, experts from the watchTowr Labs laboratory analyzed the vulnerability and presented a proof of concept that demonstrates how you can use command injection to manipulate devices that are not protected by the latest updates. In addition, it became known that the vulnerability was already actively used in March to install bookmarks in firewalls using Upstyle malware, which allowed attackers to gain access to internal networks and steal data.
According to the Shadowserver Foundation, approximately 22,542 Internet-accessible security devices may be vulnerable to attacks, mainly in the United States, Japan, India, Germany, the United Kingdom, Canada, Australia, France and China.
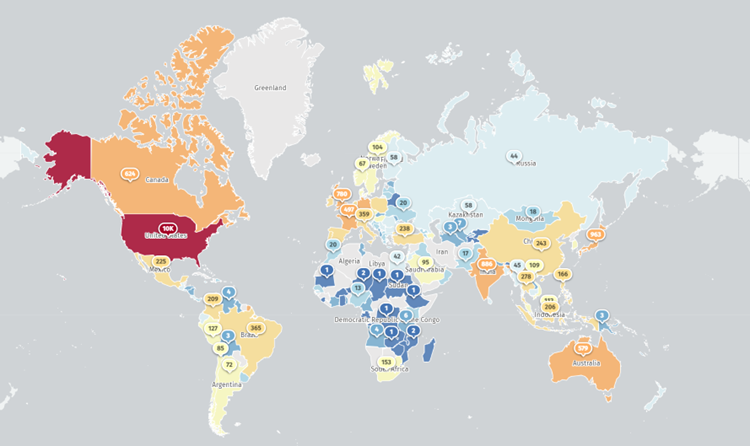
Geography of vulnerable Pan-OS devices
Experts strongly recommend that users immediately apply the released patches to protect against potential threats.
Palo Alto Networks has revealed details of a critical vulnerability in the PAN-OS operating system, which has become the object of active exploitation.
Vulnerability CVE-2024-3400 (CVSS score: 10.0) is a combination of two bugs in PAN-OS versions 10.2, 11.0, and 11.1. The first bug is related to insufficient verification of the session ID format by GlobalProtect before saving them, which allows an attacker to save files with arbitrary names. The second problem is that the system mistakenly trusts these files by using their names as part of system commands. Together, two vulnerabilities allow you to execute commands on behalf of the system without authentication.
Palo Alto experts track attacks using this vulnerability under the code name "MidnightEclipse", noting that they are backed by a threat entity codenamed UTA0218, whose origin has not yet been determined.
The attack consists of two stages: at the first stage, the hacker sends specially formed requests containing the command, and at the second stage, the system task that runs on a schedule uses this file name to execute the command.

Attack stages
Experts from Unit 42 and Volexity emphasized that the initial mechanism for preserving the vulnerability included installing a cron task for downloading and executing malicious code using the GOST tool.
Volexity experts noted that the attackers used Palo Alto firewalls to create a reverse connection( Reverse Shell), download additional tools, penetrate internal networks and steal data.
After identifying the vulnerability, Palo Alto Networks released updates for all affected versions of the operating system to prevent further attacks. It was also confirmed that the presence of telemetry on the device does not affect the exploitation of the vulnerability.
The CISA agency added the vulnerability to its catalog of known exploited vulnerabilities (KEV) and called on federal agencies to ensure the security of their devices by April 19, 2024.
Also, experts from the watchTowr Labs laboratory analyzed the vulnerability and presented a proof of concept that demonstrates how you can use command injection to manipulate devices that are not protected by the latest updates. In addition, it became known that the vulnerability was already actively used in March to install bookmarks in firewalls using Upstyle malware, which allowed attackers to gain access to internal networks and steal data.
According to the Shadowserver Foundation, approximately 22,542 Internet-accessible security devices may be vulnerable to attacks, mainly in the United States, Japan, India, Germany, the United Kingdom, Canada, Australia, France and China.

Geography of vulnerable Pan-OS devices
Experts strongly recommend that users immediately apply the released patches to protect against potential threats.
