CarderPlanet
Professional
- Messages
- 2,552
- Reaction score
- 724
- Points
- 113
A log is data from the owner's computer, which contains cookies, passes, information about the hardware, iP, as well as files from the desktop.
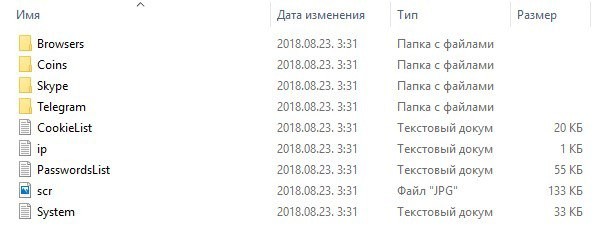
I will give an example of a log from the AzorUlt styler.
This is what the log looks like. The meaning is about the same, from different stealers the logs can look differently. The date indicated on the log is the date when the upload to your panel occurred. Thus, when buying logs, by opening this file at the initial stage, you can understand how its limitation period. Usually, bona fide sellers sell logs that are 3 weeks old or a month old.
If the date is quite old, then the log is considered to be of poor quality.
The main task in working with the log is picking it. In general, the logs contain enough information that is suitable for various purposes. This is a personal matter for everyone who likes to work and how. You can take it by blackmail, drive in, you can steal someone else's accounts and then ask for a ransom for them, you can work with a crypt, with exchanges, with cold wallets, with ebey accounts, amazon, etc. Who has enough imagination for what)
In general, the most important thing in working with logs is for the system to perceive us as its own person. I use a simple available bundle when working, namely
Chrome + editthiscoockie + webrtc + vpn + user agent. Currently I use Windscribe and Ip Vanish. Often, the ip does not mean much to us, you can use any, the main thing is that it does not have blackouts. For individual countries, for example, when working with a stick, it is advisable to adjust to the zip, or take a clean socks5)
The main requirement in working with logs is not passwords, as many people think, but the
presence of cookies. With cookies, you can get the most out of it.
PART 1. Where can I get the logs?
There are several options for obtaining logs. The easiest one is to buy them. On the forums there are a sufficient number of sellers who sell logs, and different prices.
You can buy here http://buylogs.info
There are logs for 20 rubles apiece, there are also for $ 20. The price of a log depends on its quality, country, as well as the services that are inside. Most expensive in the sale of US logs. Due to the fact that there are a huge number of banks, as well as paypal accounts. Logs that cost 20p, most often without a sample, and basically there is all sorts of rubbish, like social networks or toys, although it happens that you get lucky and come across worthwhile things
For example, when buying a log with a PayPal account, it is important to check not only the presence of a password for it, but also whether it is in the cookies.
We check it with a regular search in a textbook with cookies, at the request of paypal. If there are lines and more than one, then this log is considered good.
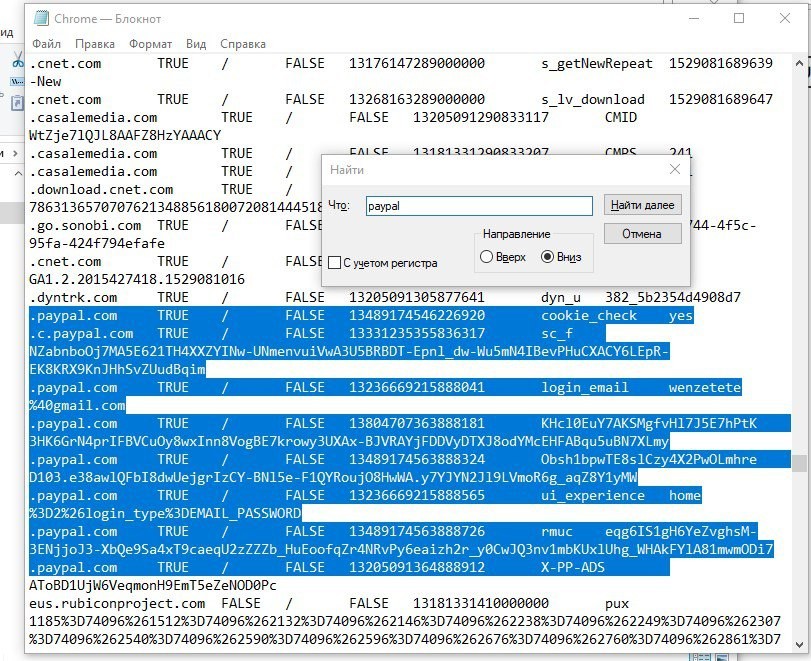
This is what a normal log looks like))
Most often, when embedding cookies from such a log, the same paper automatically issues the mail we need, on which the account is registered. Because it often happens that the owner has a bunch of mails, but we do not have a password or login to paypal. With such a log, having received at least a login, we can try to pick up a password from the account that we have. Also, the plus of such a log is that the Paypal system perceives us as its person, due to the presence of cookies, and can allow us to drive in something without first swinging it.
What else you need to know about the purchased log is whether it sold in 10 hands. The simplest check is mail check. First of all, when checking, we embed cookies into the browser and stamp on the owner's mail.
In the case of gmail mail, you just need to check the logging in it.
Mate mail to the very bottom and press the "Details" button.
A window with the latest activities in the mail will open for us.
Thus, it is possible to understand if there were other extraneous logs besides our
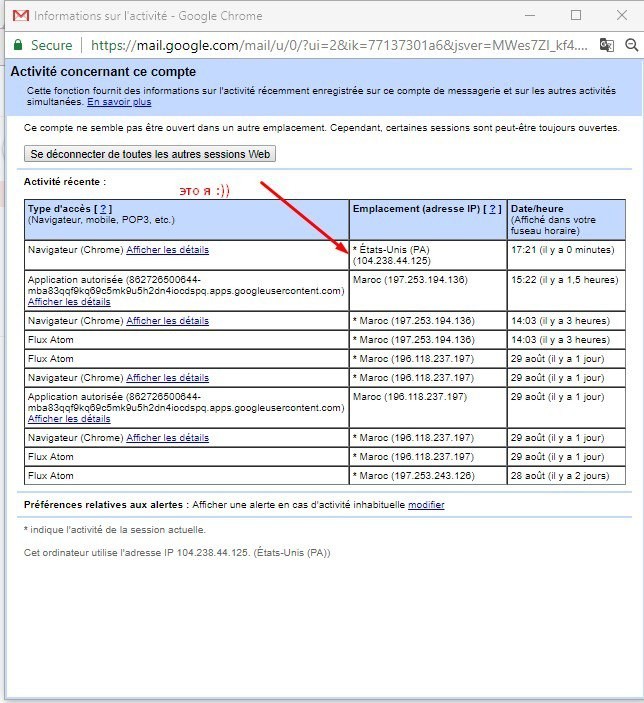
This is a good log)
By IP and country, you can understand that over the past 3 days, except for me and the owner, no one has logged into the account. You can also look at the letters in the basket, otherwise you never know, someone has already tried to "break" it. Running a little ahead, I'll say right away that the owner does not receive any notifications about third-party logging, the whole point is that the system took us for its own person because we had cookies.
Great, now having a whole log with cookies on hand, you can start working with passes )
The second option for obtaining logs is to buy your own stealer / botnet with a loader function.
Having your own stealer, in general, you do not have to worry about the fact that someone has already picked your log before you. What is the difference between stealers? In their functionality. The stealers who pull passes from Firefox and Chrome, as well as the form grabber setting (typing files from the desktop), and wallet.dat are good stealers. Although, there are cheap in sales without faerfoks, but only with Chrome, well, in general, and this too can fuck) Buying your own Stealer, you need to take care of the hosting, free or cheap does not last long and there is a risk after the Straits remain with than, due to the fact that your socket will simply fly off, it will be blocked and you will say goodbye to your logs. Therefore, you can either purchase a stealer already on a ready-made bullet-resistant hosting, such as Nocturnal, or put the panel on a separate bullet-resistant hosting yourself.
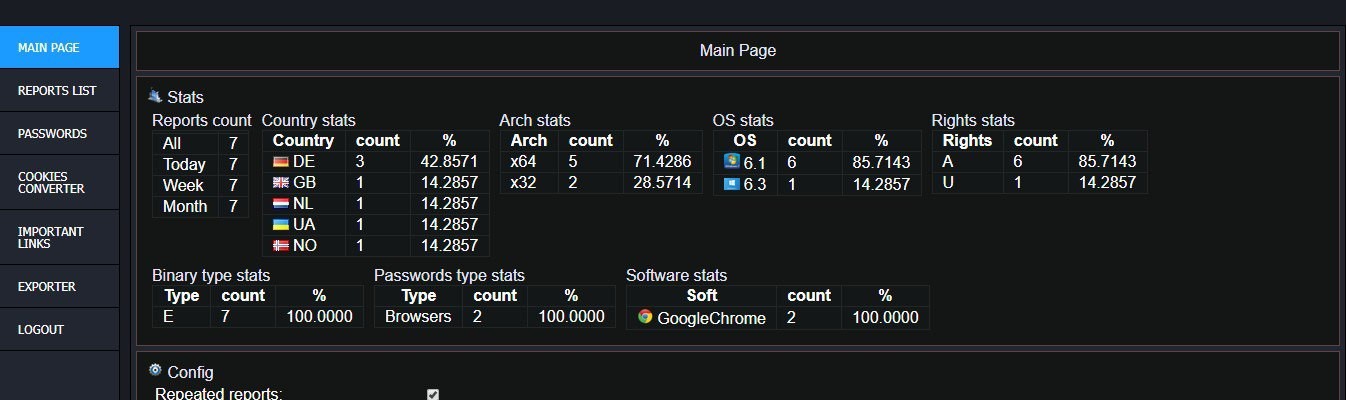
This is how the AzorUlt styler panel looks like
This is what Nocturnal looks like
This is what Arkei looks like
Screens of panels, not mine, but honestly copied.)))
As we can see from the example of 3 styler panels, they look about the same. Content of passes, logsin general, country or ip, jack of date, data from ss and files, etc.
How to get the cherished logs into our panel? There are 2 options. Buy installations, or rather the installation of our virus, or distribute it yourself.
When purchasing installs, we receive logs in a limited and initially specified quantity. The main rule is 1000 intalls - NOT EQUAL 1000 LOGS !!! In general, what kind of
kick is important, and the kick depends on many factors. From, for example, crypt (masking), our file, or from setting up a form grabber. If we want to cover everything in a row that is on the desktop, then the footprint can be 20%, checked on ourselves)))
In general, when buying 1000 installs, the average response is 70-80%, that is, we will have 700-800 logs in the panel. But that's not all! Some of them can be empty, some of them
can only be with cookies, some with 1-2 passwords, and this is absolutely normal. In the end, there can be about 250-300 fatty good logs.
Consider the distribution option yourself. You can just shove our encrypted .exe under the guise of cheats (school scholars)))), or a super-duper of a new program, for something. It so happens that after installing and running the
stealer, it will be displayed in our panel in the form of that very log.) In addition, you can ask a good person to combine your stealer with a real program, then it turns out that our .exe will not cause any suspicion and no one will not run to reinstall Windows)) You can distribute, as it was already clear, in various
forums, on YouTube, on torrents, in forums, in VK, in the end ) Yes, this method is almost free, but time consuming, if you do not want to spend money on installations, or if you simply do not have them, then you can use this option.
That with the first, that with the second option, the result will be the same - getting logs. But here a lot will depend on the quality. It is clear that when distributing in VK, the quality of speech may not go.
PART 2. System configuration.
As I have already written above, I use regular Chrome for work. I do not work with Dedicated computers, I do not work with Virtual Machines, Spheres and other joys. Just Chrome, regular chrome.
On it, we install the Editthiscoockie extensions - this is necessary to embed cookies in the browser.
Also, install WebRTC
And the User-agent, which replaces our browser, under the owner's browser, if necessary!
And of course a VPN. You can buy VPN here - http://ak4you.deer.su/ or http://vpnxxx.ml/
Previously, we only worked with Winscribe, but in the last couple of months, it began to be missed, either there is no country I need, or there is, but the ip is in black metal to the point of impossibility. Therefore, in addition, I can advise you to use the same Ip Vanish.
Ip Vanish is convenient because it has a fairly large number of servers for any country.
After installing all the extensions and connecting to the VPN, we go to check our IP at https://whatleaks.com/
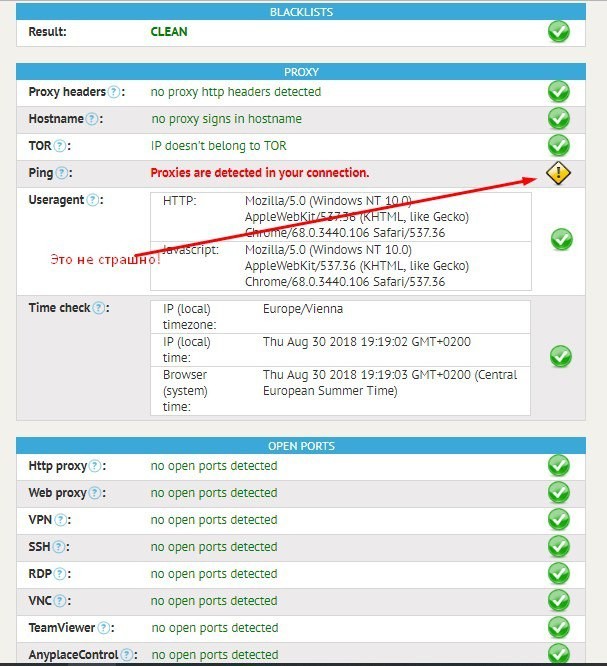
At the exit, you should have something like this.
Next, how do you embed cookies into your browser? We find our cookie file in the log , press CTRL + A CTRL + C and convert the cookies to Json format. AzorUlt stillers have a built-in converter in their panels.
Importing cookies
1) Download the local OpenServer server (Basic),
you can download it from the link https://ospanel.io/download/
2) Download a script with which you can import cookies from .txt format to .json format. Filled this script into the archive, download it from the link https://yadi.sk/d/adIKz-Px3Qk4VY
3) After downloading the script, go to the domains folder (in the OpenServer folder), then create a folder named convert.loc there and upload our script there.
4) Next, launch OpenServer (a green checkbox should appear below ).
5) After starting, open any browser and go to the site: convert.loc, download the cookies we need in txt format and convert to json and copy what was given to you.
6) Next, install the Edit
this Cookies extension in opera or chrome , in the upper right corner you will see an icon in the form of a cookie, click import and insert all the components that were converted through the convert.loc website.
That's all friends, there is nothing complicated about it, if you follow the instructions, then everything will work out! We just take the necessary cookies,
convert them to Json format and import them into the browser through the extension.
And that's it, cookies in the browser, you can start fumbling
First of all, I always check my mail. Because having access to mail, you can pull out a lot of things, even without having passes. In general, you need patience, desire and wide eyes, so as not to inadvertently miss something good.

I will give an example of a log from the AzorUlt styler.
This is what the log looks like. The meaning is about the same, from different stealers the logs can look differently. The date indicated on the log is the date when the upload to your panel occurred. Thus, when buying logs, by opening this file at the initial stage, you can understand how its limitation period. Usually, bona fide sellers sell logs that are 3 weeks old or a month old.
If the date is quite old, then the log is considered to be of poor quality.
The main task in working with the log is picking it. In general, the logs contain enough information that is suitable for various purposes. This is a personal matter for everyone who likes to work and how. You can take it by blackmail, drive in, you can steal someone else's accounts and then ask for a ransom for them, you can work with a crypt, with exchanges, with cold wallets, with ebey accounts, amazon, etc. Who has enough imagination for what)
In general, the most important thing in working with logs is for the system to perceive us as its own person. I use a simple available bundle when working, namely
Chrome + editthiscoockie + webrtc + vpn + user agent. Currently I use Windscribe and Ip Vanish. Often, the ip does not mean much to us, you can use any, the main thing is that it does not have blackouts. For individual countries, for example, when working with a stick, it is advisable to adjust to the zip, or take a clean socks5)
The main requirement in working with logs is not passwords, as many people think, but the
presence of cookies. With cookies, you can get the most out of it.
PART 1. Where can I get the logs?
There are several options for obtaining logs. The easiest one is to buy them. On the forums there are a sufficient number of sellers who sell logs, and different prices.
You can buy here http://buylogs.info
There are logs for 20 rubles apiece, there are also for $ 20. The price of a log depends on its quality, country, as well as the services that are inside. Most expensive in the sale of US logs. Due to the fact that there are a huge number of banks, as well as paypal accounts. Logs that cost 20p, most often without a sample, and basically there is all sorts of rubbish, like social networks or toys, although it happens that you get lucky and come across worthwhile things
For example, when buying a log with a PayPal account, it is important to check not only the presence of a password for it, but also whether it is in the cookies.
We check it with a regular search in a textbook with cookies, at the request of paypal. If there are lines and more than one, then this log is considered good.

This is what a normal log looks like))
Most often, when embedding cookies from such a log, the same paper automatically issues the mail we need, on which the account is registered. Because it often happens that the owner has a bunch of mails, but we do not have a password or login to paypal. With such a log, having received at least a login, we can try to pick up a password from the account that we have. Also, the plus of such a log is that the Paypal system perceives us as its person, due to the presence of cookies, and can allow us to drive in something without first swinging it.
What else you need to know about the purchased log is whether it sold in 10 hands. The simplest check is mail check. First of all, when checking, we embed cookies into the browser and stamp on the owner's mail.
In the case of gmail mail, you just need to check the logging in it.
Mate mail to the very bottom and press the "Details" button.
A window with the latest activities in the mail will open for us.
Thus, it is possible to understand if there were other extraneous logs besides our

This is a good log)
By IP and country, you can understand that over the past 3 days, except for me and the owner, no one has logged into the account. You can also look at the letters in the basket, otherwise you never know, someone has already tried to "break" it. Running a little ahead, I'll say right away that the owner does not receive any notifications about third-party logging, the whole point is that the system took us for its own person because we had cookies.
Great, now having a whole log with cookies on hand, you can start working with passes )
The second option for obtaining logs is to buy your own stealer / botnet with a loader function.
Having your own stealer, in general, you do not have to worry about the fact that someone has already picked your log before you. What is the difference between stealers? In their functionality. The stealers who pull passes from Firefox and Chrome, as well as the form grabber setting (typing files from the desktop), and wallet.dat are good stealers. Although, there are cheap in sales without faerfoks, but only with Chrome, well, in general, and this too can fuck) Buying your own Stealer, you need to take care of the hosting, free or cheap does not last long and there is a risk after the Straits remain with than, due to the fact that your socket will simply fly off, it will be blocked and you will say goodbye to your logs. Therefore, you can either purchase a stealer already on a ready-made bullet-resistant hosting, such as Nocturnal, or put the panel on a separate bullet-resistant hosting yourself.

This is how the AzorUlt styler panel looks like

This is what Nocturnal looks like

This is what Arkei looks like
Screens of panels, not mine, but honestly copied.)))
As we can see from the example of 3 styler panels, they look about the same. Content of passes, logsin general, country or ip, jack of date, data from ss and files, etc.
How to get the cherished logs into our panel? There are 2 options. Buy installations, or rather the installation of our virus, or distribute it yourself.
When purchasing installs, we receive logs in a limited and initially specified quantity. The main rule is 1000 intalls - NOT EQUAL 1000 LOGS !!! In general, what kind of
kick is important, and the kick depends on many factors. From, for example, crypt (masking), our file, or from setting up a form grabber. If we want to cover everything in a row that is on the desktop, then the footprint can be 20%, checked on ourselves)))
In general, when buying 1000 installs, the average response is 70-80%, that is, we will have 700-800 logs in the panel. But that's not all! Some of them can be empty, some of them
can only be with cookies, some with 1-2 passwords, and this is absolutely normal. In the end, there can be about 250-300 fatty good logs.
Consider the distribution option yourself. You can just shove our encrypted .exe under the guise of cheats (school scholars)))), or a super-duper of a new program, for something. It so happens that after installing and running the
stealer, it will be displayed in our panel in the form of that very log.) In addition, you can ask a good person to combine your stealer with a real program, then it turns out that our .exe will not cause any suspicion and no one will not run to reinstall Windows)) You can distribute, as it was already clear, in various
forums, on YouTube, on torrents, in forums, in VK, in the end ) Yes, this method is almost free, but time consuming, if you do not want to spend money on installations, or if you simply do not have them, then you can use this option.
That with the first, that with the second option, the result will be the same - getting logs. But here a lot will depend on the quality. It is clear that when distributing in VK, the quality of speech may not go.
PART 2. System configuration.
As I have already written above, I use regular Chrome for work. I do not work with Dedicated computers, I do not work with Virtual Machines, Spheres and other joys. Just Chrome, regular chrome.
On it, we install the Editthiscoockie extensions - this is necessary to embed cookies in the browser.
Also, install WebRTC
And the User-agent, which replaces our browser, under the owner's browser, if necessary!
And of course a VPN. You can buy VPN here - http://ak4you.deer.su/ or http://vpnxxx.ml/
Previously, we only worked with Winscribe, but in the last couple of months, it began to be missed, either there is no country I need, or there is, but the ip is in black metal to the point of impossibility. Therefore, in addition, I can advise you to use the same Ip Vanish.
Ip Vanish is convenient because it has a fairly large number of servers for any country.
After installing all the extensions and connecting to the VPN, we go to check our IP at https://whatleaks.com/

At the exit, you should have something like this.
Next, how do you embed cookies into your browser? We find our cookie file in the log , press CTRL + A CTRL + C and convert the cookies to Json format. AzorUlt stillers have a built-in converter in their panels.
Importing cookies
1) Download the local OpenServer server (Basic),
you can download it from the link https://ospanel.io/download/
2) Download a script with which you can import cookies from .txt format to .json format. Filled this script into the archive, download it from the link https://yadi.sk/d/adIKz-Px3Qk4VY
3) After downloading the script, go to the domains folder (in the OpenServer folder), then create a folder named convert.loc there and upload our script there.
4) Next, launch OpenServer (a green checkbox should appear below ).
5) After starting, open any browser and go to the site: convert.loc, download the cookies we need in txt format and convert to json and copy what was given to you.
6) Next, install the Edit
this Cookies extension in opera or chrome , in the upper right corner you will see an icon in the form of a cookie, click import and insert all the components that were converted through the convert.loc website.
That's all friends, there is nothing complicated about it, if you follow the instructions, then everything will work out! We just take the necessary cookies,
convert them to Json format and import them into the browser through the extension.


And that's it, cookies in the browser, you can start fumbling
First of all, I always check my mail. Because having access to mail, you can pull out a lot of things, even without having passes. In general, you need patience, desire and wide eyes, so as not to inadvertently miss something good.
