Man
Professional
- Messages
- 3,222
- Reaction score
- 1,199
- Points
- 113
The updated SpyNote uses the trust of users for selfish purposes.
Researchers from Cyfirma have identified a new cyber threat — an updated Android Trojan called SpyNote, which actively attacks users under the guise of Avast antivirus. The malware masquerades as a well-known application and uses sophisticated techniques to take control of the device.
SpyNote is distributed through fake sites that mimic the official Avast portal and, once installed, gains access to the device's system functions. The application asks for permissions to control the screen and notifications, which allows it to gain privileges to perform actions without the user's knowledge. Once installed, it uses accessibility services to automatically approve all necessary permissions, hiding from antiviruses.
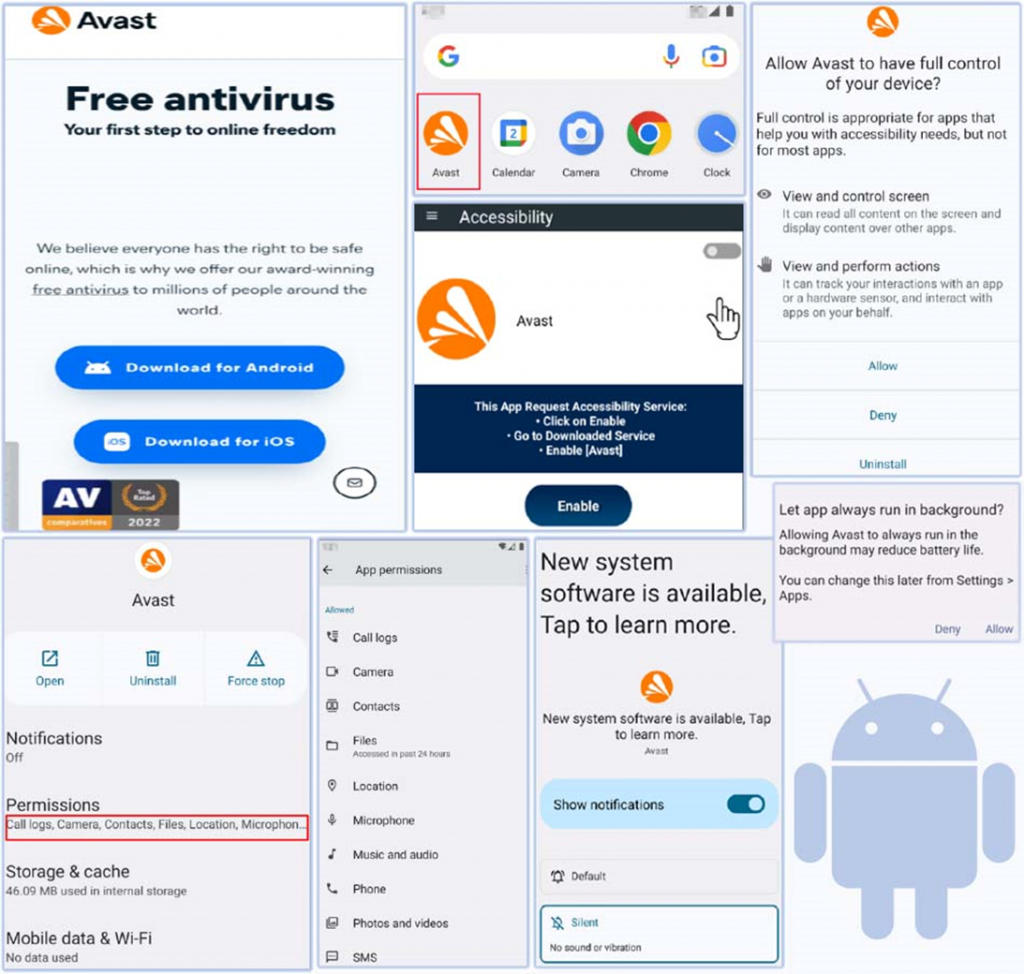
Analysis has shown that the Trojan has a wide range of capabilities. It monitors calls and messages, gets access to the camera and microphone, and steals data from other applications, including instant messengers and payment services. It is noteworthy that the malware is able to prevent its uninstallation by automatically blocking attempts to remove it through the settings.
SpyNote actively searches for crypto wallets and steals data about the cryptocurrency you have, such as passwords and transactions. The Trojan also collects personal information about the victim by exploiting vulnerabilities in popular apps and social networks, including Instagram and WhatsApp.
To disguise its actions, the Trojan uses code obfuscation, which makes it difficult to analyze and detect. The program hides its icon on the device and sends commands to the attackers' servers to download additional components. This allows it to be constantly updated and expand its functionality even months after installation on the device.
SpyNote's malicious activity doesn't just extend to mobile devices. Cybercriminals also use fake sites to download remote access programs to computers running Windows and macOS. Cyfirma researchers have identified 14 domains used to propagate this threat.
Experts warn about the need to be vigilant and not to download applications from dubious sources. Installing reliable antivirus solutions and practicing good digital hygiene will help prevent devices from getting infected.
Source
Researchers from Cyfirma have identified a new cyber threat — an updated Android Trojan called SpyNote, which actively attacks users under the guise of Avast antivirus. The malware masquerades as a well-known application and uses sophisticated techniques to take control of the device.
SpyNote is distributed through fake sites that mimic the official Avast portal and, once installed, gains access to the device's system functions. The application asks for permissions to control the screen and notifications, which allows it to gain privileges to perform actions without the user's knowledge. Once installed, it uses accessibility services to automatically approve all necessary permissions, hiding from antiviruses.

Analysis has shown that the Trojan has a wide range of capabilities. It monitors calls and messages, gets access to the camera and microphone, and steals data from other applications, including instant messengers and payment services. It is noteworthy that the malware is able to prevent its uninstallation by automatically blocking attempts to remove it through the settings.
SpyNote actively searches for crypto wallets and steals data about the cryptocurrency you have, such as passwords and transactions. The Trojan also collects personal information about the victim by exploiting vulnerabilities in popular apps and social networks, including Instagram and WhatsApp.
To disguise its actions, the Trojan uses code obfuscation, which makes it difficult to analyze and detect. The program hides its icon on the device and sends commands to the attackers' servers to download additional components. This allows it to be constantly updated and expand its functionality even months after installation on the device.
SpyNote's malicious activity doesn't just extend to mobile devices. Cybercriminals also use fake sites to download remote access programs to computers running Windows and macOS. Cyfirma researchers have identified 14 domains used to propagate this threat.
Experts warn about the need to be vigilant and not to download applications from dubious sources. Installing reliable antivirus solutions and practicing good digital hygiene will help prevent devices from getting infected.
Source

