Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,322
- Points
- 113
Android users voluntarily give their data to the new Trojan.
Intel 471 specialists have identified a new banking Trojan called BlankBot, targeting Android users in Turkey. The program is designed to steal financial information and has a wide range of malicious features.
BlankBot is capable of performing a number of dangerous actions: recording keystrokes, recording the screen, and communicating with the management server via WebSocket. The Trojan is under active development and uses Android Accessibility Services permissions to gain full control over the infected device.
Similar to the recently revived Mandrake trojan, BlankBot uses a session-based package installer to circumvent an Android 13 limitation that blocks apps that request dangerous permissions when installed from third-party sources.
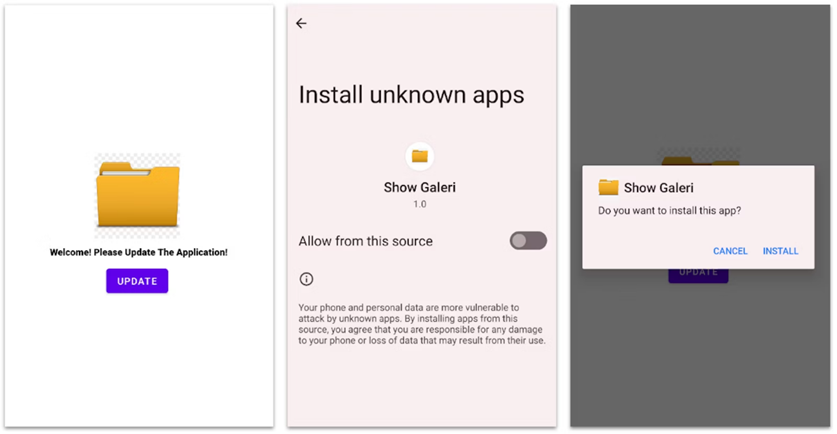
Installing the BlankBot payload in Android 13
BlankBot requires the victim's permission to install apps from third-party sources, then extracts the APK from the app's resource directory and starts installing. The malware has screen recording, keylogging, and overlay functions for collecting bank data, payment information, and even a device unlock template.
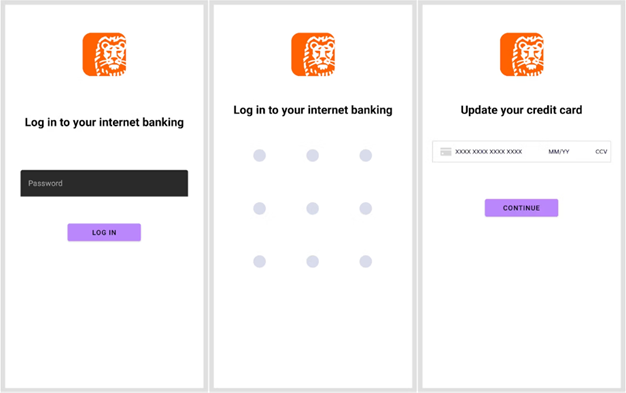
Overlay for stealing payment data
In addition, BlankBot is able to intercept SMS messages, delete apps, and collect data such as contact lists and installed apps. The Trojan also uses the Accessibility Service API to block users from accessing device settings or running antivirus applications.
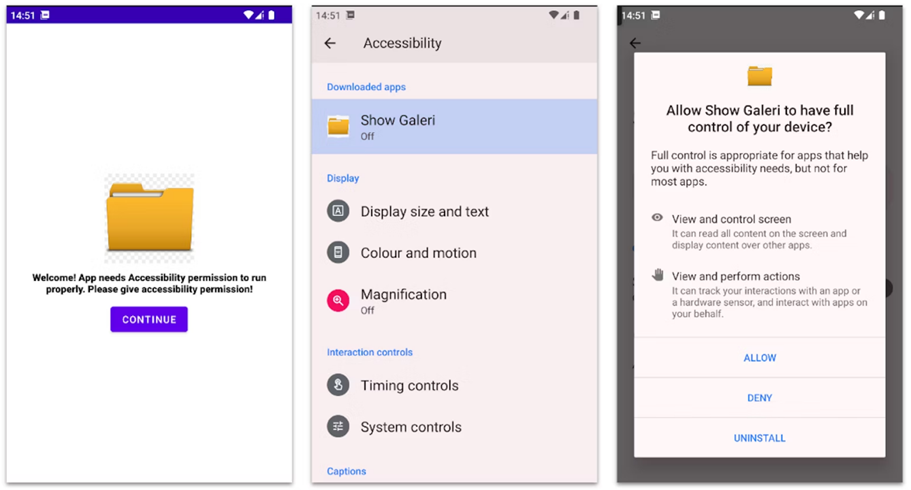
BlankBot Installation Process
The BlankBot Trojan is under active development, which is confirmed by the presence of many code variants in various applications. However, malware can perform dangerous actions immediately after infecting the device.
A Google spokesperson said that the company did not find any infected apps in the Google Play Store. The employee mentioned that the Google Play Protect feature, activated by default on devices with Google Play Services, automatically protects users from known versions of BlankBot by alerting the user and blocking infected apps, even if they come from external sources.
Source
Intel 471 specialists have identified a new banking Trojan called BlankBot, targeting Android users in Turkey. The program is designed to steal financial information and has a wide range of malicious features.
BlankBot is capable of performing a number of dangerous actions: recording keystrokes, recording the screen, and communicating with the management server via WebSocket. The Trojan is under active development and uses Android Accessibility Services permissions to gain full control over the infected device.
Similar to the recently revived Mandrake trojan, BlankBot uses a session-based package installer to circumvent an Android 13 limitation that blocks apps that request dangerous permissions when installed from third-party sources.

Installing the BlankBot payload in Android 13
BlankBot requires the victim's permission to install apps from third-party sources, then extracts the APK from the app's resource directory and starts installing. The malware has screen recording, keylogging, and overlay functions for collecting bank data, payment information, and even a device unlock template.

Overlay for stealing payment data
In addition, BlankBot is able to intercept SMS messages, delete apps, and collect data such as contact lists and installed apps. The Trojan also uses the Accessibility Service API to block users from accessing device settings or running antivirus applications.

BlankBot Installation Process
The BlankBot Trojan is under active development, which is confirmed by the presence of many code variants in various applications. However, malware can perform dangerous actions immediately after infecting the device.
A Google spokesperson said that the company did not find any infected apps in the Google Play Store. The employee mentioned that the Google Play Protect feature, activated by default on devices with Google Play Services, automatically protects users from known versions of BlankBot by alerting the user and blocking infected apps, even if they come from external sources.
Source

