Man
Professional
- Messages
- 3,222
- Reaction score
- 1,201
- Points
- 113
We store a lot of personal information on our mobile phones and obviously do not want our correspondence, cryptocurrency wallets or contact list to become public knowledge. However, in some cases, law enforcement officials may require us to provide full access to our device.
To what extent such a requirement complies with the law, is it possible to prevent a search and how to hide confidential information - we will tell you in a special ForkLog article.
Who and why can search me?
Any state considers the border as a source of increased danger. Therefore, services that deal with visa, passport and customs control, as a rule, have more opportunities to violate your personal space and conduct searches more often than any other organizations.
The right to check the contents of digital devices is granted to border officials in the United States, China and Canada. In case of refusal to provide a device for inspection, a decision may be made to deny entry. Customs officers analyze social media posts, call and browser history, look at correspondence, photos, videos and documents of those entering the country to determine the purpose of their visit. Border control officers can inspect devices and check the data stored on them, but they do not have the right to check data stored in the cloud and on third-party web services.
According to available data, in 2017 alone, customs services in the United States conducted 30,000 device searches, which is 58% more than the year before. Considering that travelers cross the US border about 400 million times each year, the number of searches is on average 1 in 13,000.

In Russia, the powers of border control officers to check digital devices are prescribed in paragraph 2 of Article 20 of the Law of the Russian Federation of April 1, 1993 No. 4730-I “On the State Border of the Russian Federation”.
Police officers may also search citizens and items , in accordance with Article 13 of the Law "On Police" and Article 27.7 of the Code of Administrative Offenses of the Russian Federation on personal searches. It sets out clear rules: officers are required to draw up a report, involve two witnesses, state their positions, full name and date, and also indicate the number of items inspected and information about the citizen. Failure to comply with a lawful demand of a police officer is punishable by a fine or administrative arrest for up to 15 days.
As part of the search, the police officer may only look at the phone from the outside, but may not disassemble or break it.
If you are required to provide your PIN code, you can refer to Article 51 of the Constitution of the Russian Federation , which allows you not to give any evidence against yourself. The law also does not provide for the obligation to independently unlock the device at the request of a border service, customs or police officer.
You may not store personal information on your mobile phone or sign out of all accounts. However, it is unlikely that background checks will be conducted in a way that respects privacy—even in places where electronic device searches are not officially permitted, law enforcement is likely to turn a blind eye to restrictions that are inconvenient for them.
What information can law enforcement officers access?
Since the path of resistance and providing false information will not be interpreted in your favor, let's talk about the situation when your device has fallen into the hands of inspectors.
If your phone has not been encrypted, then data can be extracted from it in almost one hundred percent of cases.
Many Android and Windows Phone devices have a service mode that allows you to drain all data from the device's memory via a regular USB cable. This applies to most devices on the Qualcomm platform (HS-USB mode, which works even with a locked bootloader), on Chinese smartphones with MediaTek (MTK), Spreadtrum and Allwinner processors (if the bootloader is unlocked), as well as all smartphones manufactured by LG (their service mode allows you to drain data even from a "bricked" device).
But even if the phone does not have a service "back door", data from the device can still be obtained by disassembling the device and connecting to the JTAG test port. In the most advanced cases, the eMMC chip is removed from the device, inserted into a simple and very cheap adapter and works on the same protocol as the most common SD card. If the data was not encrypted, everything can be easily extracted from the phone, including authentication markers that provide access to cloud storage.
Representatives of the human rights organization Electronic Frontier Foundation Kurt Opsahl and William Budington remind that border guards may have special equipment in stock for quickly and effectively extracting data from mobile gadgets. Most often, Cellebrite devices are used, which are capable of copying even deleted information. In some cases, these devices are capable of extracting data even from locked smartphones.
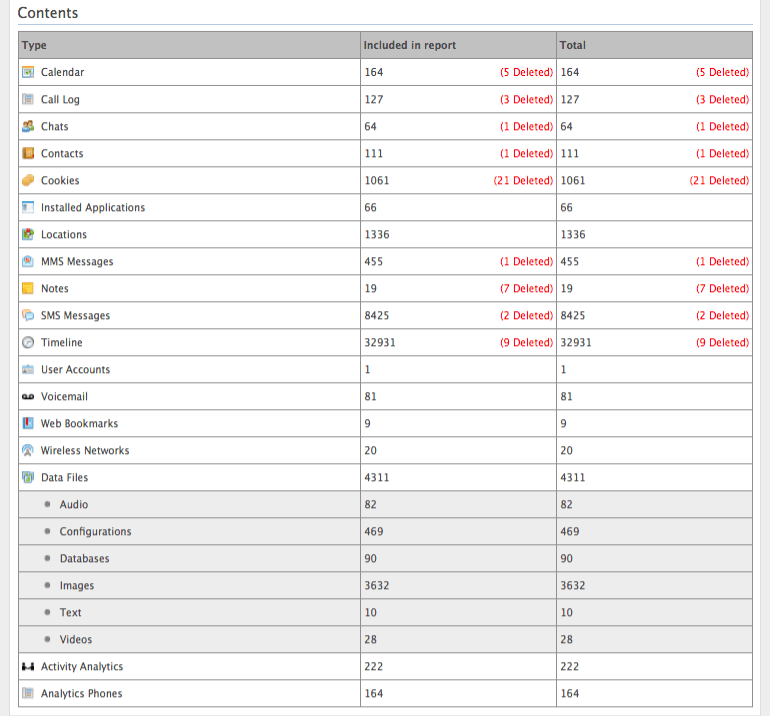
If your phone is backed up via ADB (Android Debug Bridge), it may contain:
Another vulnerability of Android devices is the numerous insecure unlocking methods under the common name Smart Lock. Nothing can prevent a border guard from taking a photo of your face or pressing your finger to the sensor (sometimes the gadget can be unlocked even with a copy of your fingerprint, if it is in the database). Therefore, make sure that the phone can only be unlocked with a PIN code or password, preferably a complex one.
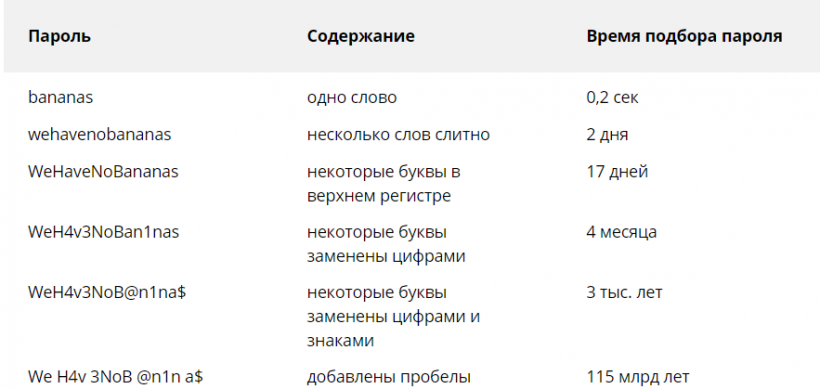
It is recommended to use a combination of letters in different cases, special characters and numbers in the password. It is even better if the password is longer than 16 characters. For example, it will take more than 200 years to pick a password P#$$M>Rd_wR1443N_c0Wpl1c4^3D.
To avoid inventing passwords yourself, use services like GenPas - they generate strong passwords from a random set of characters.
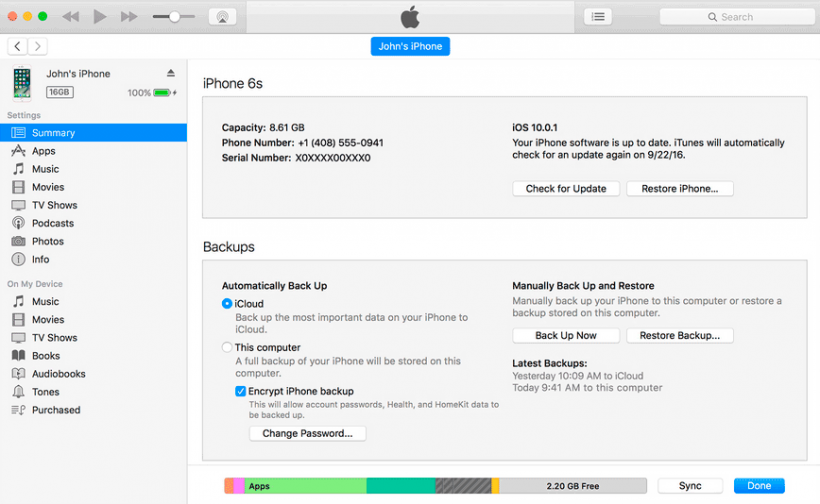
If you have an iPhone with the latest version of iOS and you have not jailbroken it, it is impossible to take a physical image of the device. The only analysis method available to border guards, other than manually launching applications on the phone, is to take a backup copy via iTunes or a specialized application, such as Elcomsoft iOS Forensic Toolkit. To counteract this, you just need to take care of setting a password for the backup copies in advance. To do this, launch iTunes and activate the Encrypt iPhone backup option, then specify the password.
To protect your passwords, turn off keychain and iCloud Keychain on your phone. Passwords will be deleted from your device and will not be pulled from the cloud until you activate iCloud Keychain. Browser history and search queries are deleted in the same way.
However, browser history will still be stored in iCloud for at least two weeks after deletion. To finally “nail the ends”, you will need to disable data synchronization with the cloud.
Finally, you can completely disable iCloud. However, this is not recommended, as this will disable iCloud Lock and Find My Phone theft protection.
How can I protect information on an unencrypted Android device?
With encryption disabled and the ability to make a backup of the device, you can use the following method. Install custom TWRP recovery on your smartphone, reboot into it, make a Nandroid backup of the system and data partitions (they contain the OS itself and your data / applications, respectively), extract the backup from the smartphone (it is stored in the TWRP directory on the memory card) and save it, for example, in Dropbox.
Then reset the smartphone to factory settings, link it to a fake account, install several applications, enter several unimportant passwords in the browser - thus creating the appearance of an actively used device. And then reboot into TWRP again, make a backup and save it to the cloud again.
As a result, you will get two backups: one will contain your main system, the second - the Potemkin one. All that remains for you to do is restore the second, fake backup before the trip, cross the border, and then restore the main one. In this case, all your settings, software and everything else, right down to the location of the icons on the desktop, will be preserved in their original form.
How can I encrypt my device?
If you still prefer not to take risks, activate Full Disk Encryption (FDE) in your Android smartphone and turn off the device. After turning on, the device will ask you to enter a password, even if it is usually unlocked with a fingerprint.
iOS device owners can also enable full disk encryption and then erase the encryption keys. This operation is built into the factory reset.
Once the inspection is complete, you just need to connect to Wi-Fi, reset the phone again and restore from the cloud backup.
Important: to log in to your Apple ID, you will need to have a second authentication factor (for example, a SIM card with a trusted phone number to which you can receive an SMS with a one-time code). Otherwise, you may be cut off from your own account and data in iCloud.
Remember that it will take several hours to encrypt the device, during which you will not be able to use it.
Encrypting laptops
On Apple computers with OS X, use the FileVault program, which has a full-disk encryption function. You can find instructions on how to use it on the company's official website.
Professional versions of the Windows operating system (Enterprise, Pro, Ultimate Edition) from Microsoft have a built-in BitLocker program. For other cases, there is the VeraCrypt program. With today's technology, it will take the special services at least 40 years to decrypt the data protected by it.
Two types of two-factor authentication
Two-factor authentication provides additional protection for accounts in social networks, instant messengers, email, Google, Apple, iCloud.
In most communication services, two-factor authentication is only possible via SMS. However, in some email services, you can install an application that automatically generates temporary codes. This is a safer method than SMS confirmation, which can be intercepted directly from the telecom operator.
In Gmail, you can set up login via a code generator on the Security page of your account.
Use secure messengers
Among the popular messengers, Telegram and Signal are among the most secure.
Telegram has a secret chat feature, the content of which is not stored on the company's servers and can self-destruct. To use a secret chat, you need to select a user in the list, click on their avatar and select the "Start Secret Chat" option.
Secret Telegram chats cannot be created for groups and you cannot make voice calls through them. If you need both, you can use Signal. It completely encrypts any information all the way from one subscriber to another.
Both messengers have versions for Android, iOS, and personal computers, while the Telegram PC version does not have secret chats. Both programs are free. But before using them, you should additionally configure them.
Email encryption
To encrypt emails, you can use PGP technology, which encrypts messages before sending and allows them to be read only by the owner of a special password. Even if your letter is intercepted, it will be impossible for outsiders to read its contents. Neither the FBI nor the CIA have yet been able to decode data from PGP correspondence.
As an alternative to email, you can use the Peerio service. It is easier to use than setting up PGP services and provides full encryption of data from one user to another. Peerio has versions for iOS, Android, Windows, and an extension for the Google Chrome browser.
Using cryptocontainers
One way to protect data is to create a cryptocontainer. It is a logical disk, the file structure of which in most cases coincides with the structure of the operating system. In open form, you can write files of any format and size to it. To hide files, you need to unmount the cryptocontainer. To see the files again, you need to enter a previously created key or password.
If the cryptocontainer is unmounted, an outsider will not even know about its existence. Data - the data encrypted in it will thus be reliably protected from prying eyes.
In addition, decryption of information bypassing the key is impossible. Creating special utilities that could crack an encrypted disk is an expensive undertaking. Moreover, their effectiveness is highly questionable.
The main advantage of this encryption is the ability to create a cryptocontainer with a "double bottom". The first key can be safely provided to the person conducting the inspection, and the really important data will remain untouched until another password is entered. Neither software nor hardware methods can detect the presence of a hidden part.
However, this method has a number of problems: if you forget the access key, you will not have alternative ways to reopen access to the data. It will also not be possible to restore a faulty encrypted file. The only thing you can do in this case is to create a backup copy of this information elsewhere.
In addition, the speed of writing files to a crypto container is significantly lower than to a regular hard drive.
The following encryption programs are currently available on Google Play:
LUKS Manager is the oldest file encryption program for Android. The program uses the AES encryption algorithm, while supporting the EXT2/4 and FAT32 file systems. The size of the encrypted container is limited only by the size of the phone's memory.
The advantages of the program include on-the-fly encryption and ease of use - encrypted containers are processed like regular folders.
Disadvantages: the program requires root rights to operate and does not support TrueCrypt containers, which are the de facto standard for major desktop platforms.
EDS Lite does not require root rights to operate and supports TrueCrypt containers. It uses two encryption algorithms - AES 256 and SHA-512.
Disadvantages: encryption is not on-the-fly and you cannot work with an encrypted container like a regular folder. However, there is a built-in file manager that supports all file operations. For example, you can create an encrypted container in EDS Lite or TrueCrypt, open it in the program's built-in file manager and copy all the files you want to encrypt to it.
The Cryptonite program is still in the testing stage. Its advantages include support for cloud drives. Disadvantage: it requires the Android kernel to support Kernel FUSE, and not every phone has this support.
The strong point of the CyberSafe Mobile application is the ability to synchronize crypto containers with Google Drive, which allows you to work with the same set of data on different devices. The application itself does not require root rights to work, but only until you decide to mount the container to a folder.
In addition, the application allows you to share encrypted files with other users and allows you to encrypt arbitrary folders on Google Drive. The application is paid. The free version limits the maximum password length to only two characters.
Methods for hacking crypto containers
One of the ways to hack a crypto container is a BruteForce attack, that is, a simple enumeration of various password options. With a strong password and encryption algorithm, a regular computer will take hundreds of years to crack it.
However, if this work is entrusted to a quantum computer, the cracking will take only a few days. The positive aspect is that this type of attack costs a lot of money and is unlikely to be used against an ordinary person, unless he is a particularly dangerous criminal. The
most effective protection against a BruteForce attack is onion encryption, when information is encrypted several times with different passwords, for example, first TrueCrypt encrypts files with one algorithm, and then AES Crypt with another algorithm.
For ordinary users, a much more real threat is a dictionary attack, which takes a database of passwords and checks each one. This attack is simple and relatively low-resource compared to a brute-force attack, which tries all existing options until the right one is found.
Success largely depends on the quality of the database and the complexity of the user's password. According to available data, one of the structures in Russia contains such a database of 250 million options.
The protection in this case is extremely simple: your password should not be in the database that will be used for hacking. If you use random generation of a password of 50 characters and a key, the hackers will not have a chance.
Thermorectal cryptanalysis
This general term refers to pressure to obtain passwords to access encrypted data. Pressure can range from a finger caught in a door to imprisonment for refusing to give up data.
In this way, any algorithms and passwords of any complexity are broken, but even in this case, you have several ways to protect yourself. The first of them assumes that access to the cryptocontainer will be physically destroyed.
To implement such a system, when creating a cryptocontainer, you need to add a key and place it on a microSD card. A microSD card is destroyed very easily, you can just break it with your hands and throw it out the window. After that, the information will no longer be recoverable, and, accordingly, there will be no way to access the encrypted data.
The second method of protection, already described above, is cryptocontainers with a double bottom.
The third method is to use professional software for emergency data destruction. Panic Button will not only instantly destroy cryptocontainers or key files without the possibility of recovery, but also clear passwords, browser history, history of viewing documents, pictures and running programs.
Forensic analysis of RAM
Removing and forensic analysis of a memory dump is a standard practice in forensics. Law enforcement agencies use special software to dump the RAM of digital devices. This dump is then studied, and valuable artifacts are found in it, such as encryption keys.
To protect against forensic analysis, it is enough to set the option to automatically dismantle the cryptocontainer and delete the key from the computer's RAM if there is no activity for a certain period of time.
In addition, you can use Panic Button - the program can delete valuable data from RAM if there is no activity.
Hacking a cryptocontainer using a spare key
This method is not dangerous for users of TrueCrypt, AES Crypt, VeraCrypt, LUKS, it refers to encrypted systems, but also deserves mentioning.
With complex encryption of the system, the keys for Microsoft encryption are saved by default in the Microsoft Account, the key for macOS encryption is saved by default in iCloud. Having gained access to the account, you can decrypt all the data on the hard drive, and therefore, when encrypting the system, disable saving the key in the cloud.
Conclusions
It is necessary to understand that on the side of border guards and police - if not the law, then the ability to interpret the law in their favor and the methods of coercion, which they do not hesitate to use.
From the point of view of your own safety, you should not object and lie to the border guards: all this will lead to additional complications in an already acute situation. It will be much more effective to use the complex of technical protection methods described in this material.
Remember: you can’t extract from your smartphone what is not physically on it, but any password from you can be obtained, if there is a desire.
Source
To what extent such a requirement complies with the law, is it possible to prevent a search and how to hide confidential information - we will tell you in a special ForkLog article.
Who and why can search me?
Any state considers the border as a source of increased danger. Therefore, services that deal with visa, passport and customs control, as a rule, have more opportunities to violate your personal space and conduct searches more often than any other organizations.
The right to check the contents of digital devices is granted to border officials in the United States, China and Canada. In case of refusal to provide a device for inspection, a decision may be made to deny entry. Customs officers analyze social media posts, call and browser history, look at correspondence, photos, videos and documents of those entering the country to determine the purpose of their visit. Border control officers can inspect devices and check the data stored on them, but they do not have the right to check data stored in the cloud and on third-party web services.
According to available data, in 2017 alone, customs services in the United States conducted 30,000 device searches, which is 58% more than the year before. Considering that travelers cross the US border about 400 million times each year, the number of searches is on average 1 in 13,000.

In Russia, the powers of border control officers to check digital devices are prescribed in paragraph 2 of Article 20 of the Law of the Russian Federation of April 1, 1993 No. 4730-I “On the State Border of the Russian Federation”.
"A search may be conducted if there is a suspicion of transporting prohibited substances, weapons, or illegally transporting people," says lawyer and partner at the Digital Rights Center Sarkis Darbinyan. "Border guards may ask to show a phone, citing that this is necessary to make sure that it is not a bomb and that the phone is not being used to conceal contraband. However, Russian law does not grant border guards any right to demand that the device be unlocked or a PIN code be provided, or to search applications on a mobile device."
Police officers may also search citizens and items , in accordance with Article 13 of the Law "On Police" and Article 27.7 of the Code of Administrative Offenses of the Russian Federation on personal searches. It sets out clear rules: officers are required to draw up a report, involve two witnesses, state their positions, full name and date, and also indicate the number of items inspected and information about the citizen. Failure to comply with a lawful demand of a police officer is punishable by a fine or administrative arrest for up to 15 days.
As part of the search, the police officer may only look at the phone from the outside, but may not disassemble or break it.
If you are required to provide your PIN code, you can refer to Article 51 of the Constitution of the Russian Federation , which allows you not to give any evidence against yourself. The law also does not provide for the obligation to independently unlock the device at the request of a border service, customs or police officer.
"In accordance with Article 23 of the Constitution, you have the right to privacy, personal and family secrets, protection of your honor and good name. In addition, you have the right to privacy of correspondence, telephone conversations, and electronic messages. Restriction of this right is allowed only on the basis of a court decision. The decision of a border guard or customs officer is not enough for this. They can only ask to voluntarily show the contents of the phone. The citizen has every right to refuse them this," explains Sarkis Darbinyan.
You may not store personal information on your mobile phone or sign out of all accounts. However, it is unlikely that background checks will be conducted in a way that respects privacy—even in places where electronic device searches are not officially permitted, law enforcement is likely to turn a blind eye to restrictions that are inconvenient for them.
"If an employee gains access to a phone and finds Telegram, LinkedIn or Zello there, he cannot do anything to you for it. The law does not provide for liability for end users for using services and applications prohibited in Russia, as well as for visiting sites blocked by Roskomnadzor. The use of any cryptocurrency wallets by users is also not prohibited by current legislation," the expert reminds.
What information can law enforcement officers access?
Since the path of resistance and providing false information will not be interpreted in your favor, let's talk about the situation when your device has fallen into the hands of inspectors.
If your phone has not been encrypted, then data can be extracted from it in almost one hundred percent of cases.
Many Android and Windows Phone devices have a service mode that allows you to drain all data from the device's memory via a regular USB cable. This applies to most devices on the Qualcomm platform (HS-USB mode, which works even with a locked bootloader), on Chinese smartphones with MediaTek (MTK), Spreadtrum and Allwinner processors (if the bootloader is unlocked), as well as all smartphones manufactured by LG (their service mode allows you to drain data even from a "bricked" device).
But even if the phone does not have a service "back door", data from the device can still be obtained by disassembling the device and connecting to the JTAG test port. In the most advanced cases, the eMMC chip is removed from the device, inserted into a simple and very cheap adapter and works on the same protocol as the most common SD card. If the data was not encrypted, everything can be easily extracted from the phone, including authentication markers that provide access to cloud storage.
Representatives of the human rights organization Electronic Frontier Foundation Kurt Opsahl and William Budington remind that border guards may have special equipment in stock for quickly and effectively extracting data from mobile gadgets. Most often, Cellebrite devices are used, which are capable of copying even deleted information. In some cases, these devices are capable of extracting data even from locked smartphones.

If your phone is backed up via ADB (Android Debug Bridge), it may contain:
- Wi-Fi network passwords, system settings;
- photos, videos and contents of internal memory;
- installed applications (APK files);
- data from applications that support backup (including authentication tokens).
Another vulnerability of Android devices is the numerous insecure unlocking methods under the common name Smart Lock. Nothing can prevent a border guard from taking a photo of your face or pressing your finger to the sensor (sometimes the gadget can be unlocked even with a copy of your fingerprint, if it is in the database). Therefore, make sure that the phone can only be unlocked with a PIN code or password, preferably a complex one.
It is recommended to use a combination of letters in different cases, special characters and numbers in the password. It is even better if the password is longer than 16 characters. For example, it will take more than 200 years to pick a password P#$$M>Rd_wR1443N_c0Wpl1c4^3D.
To avoid inventing passwords yourself, use services like GenPas - they generate strong passwords from a random set of characters.

If you have an iPhone with the latest version of iOS and you have not jailbroken it, it is impossible to take a physical image of the device. The only analysis method available to border guards, other than manually launching applications on the phone, is to take a backup copy via iTunes or a specialized application, such as Elcomsoft iOS Forensic Toolkit. To counteract this, you just need to take care of setting a password for the backup copies in advance. To do this, launch iTunes and activate the Encrypt iPhone backup option, then specify the password.

To protect your passwords, turn off keychain and iCloud Keychain on your phone. Passwords will be deleted from your device and will not be pulled from the cloud until you activate iCloud Keychain. Browser history and search queries are deleted in the same way.
However, browser history will still be stored in iCloud for at least two weeks after deletion. To finally “nail the ends”, you will need to disable data synchronization with the cloud.
Finally, you can completely disable iCloud. However, this is not recommended, as this will disable iCloud Lock and Find My Phone theft protection.
How can I protect information on an unencrypted Android device?
With encryption disabled and the ability to make a backup of the device, you can use the following method. Install custom TWRP recovery on your smartphone, reboot into it, make a Nandroid backup of the system and data partitions (they contain the OS itself and your data / applications, respectively), extract the backup from the smartphone (it is stored in the TWRP directory on the memory card) and save it, for example, in Dropbox.
Then reset the smartphone to factory settings, link it to a fake account, install several applications, enter several unimportant passwords in the browser - thus creating the appearance of an actively used device. And then reboot into TWRP again, make a backup and save it to the cloud again.
As a result, you will get two backups: one will contain your main system, the second - the Potemkin one. All that remains for you to do is restore the second, fake backup before the trip, cross the border, and then restore the main one. In this case, all your settings, software and everything else, right down to the location of the icons on the desktop, will be preserved in their original form.
How can I encrypt my device?
If you still prefer not to take risks, activate Full Disk Encryption (FDE) in your Android smartphone and turn off the device. After turning on, the device will ask you to enter a password, even if it is usually unlocked with a fingerprint.
iOS device owners can also enable full disk encryption and then erase the encryption keys. This operation is built into the factory reset.
Once the inspection is complete, you just need to connect to Wi-Fi, reset the phone again and restore from the cloud backup.
Important: to log in to your Apple ID, you will need to have a second authentication factor (for example, a SIM card with a trusted phone number to which you can receive an SMS with a one-time code). Otherwise, you may be cut off from your own account and data in iCloud.
Remember that it will take several hours to encrypt the device, during which you will not be able to use it.
Encrypting laptops
On Apple computers with OS X, use the FileVault program, which has a full-disk encryption function. You can find instructions on how to use it on the company's official website.
Professional versions of the Windows operating system (Enterprise, Pro, Ultimate Edition) from Microsoft have a built-in BitLocker program. For other cases, there is the VeraCrypt program. With today's technology, it will take the special services at least 40 years to decrypt the data protected by it.
Two types of two-factor authentication
Two-factor authentication provides additional protection for accounts in social networks, instant messengers, email, Google, Apple, iCloud.
In most communication services, two-factor authentication is only possible via SMS. However, in some email services, you can install an application that automatically generates temporary codes. This is a safer method than SMS confirmation, which can be intercepted directly from the telecom operator.
In Gmail, you can set up login via a code generator on the Security page of your account.
Use secure messengers
Among the popular messengers, Telegram and Signal are among the most secure.
Telegram has a secret chat feature, the content of which is not stored on the company's servers and can self-destruct. To use a secret chat, you need to select a user in the list, click on their avatar and select the "Start Secret Chat" option.
Secret Telegram chats cannot be created for groups and you cannot make voice calls through them. If you need both, you can use Signal. It completely encrypts any information all the way from one subscriber to another.
Both messengers have versions for Android, iOS, and personal computers, while the Telegram PC version does not have secret chats. Both programs are free. But before using them, you should additionally configure them.
Email encryption
To encrypt emails, you can use PGP technology, which encrypts messages before sending and allows them to be read only by the owner of a special password. Even if your letter is intercepted, it will be impossible for outsiders to read its contents. Neither the FBI nor the CIA have yet been able to decode data from PGP correspondence.
As an alternative to email, you can use the Peerio service. It is easier to use than setting up PGP services and provides full encryption of data from one user to another. Peerio has versions for iOS, Android, Windows, and an extension for the Google Chrome browser.
Using cryptocontainers
One way to protect data is to create a cryptocontainer. It is a logical disk, the file structure of which in most cases coincides with the structure of the operating system. In open form, you can write files of any format and size to it. To hide files, you need to unmount the cryptocontainer. To see the files again, you need to enter a previously created key or password.
If the cryptocontainer is unmounted, an outsider will not even know about its existence. Data - the data encrypted in it will thus be reliably protected from prying eyes.
In addition, decryption of information bypassing the key is impossible. Creating special utilities that could crack an encrypted disk is an expensive undertaking. Moreover, their effectiveness is highly questionable.
The main advantage of this encryption is the ability to create a cryptocontainer with a "double bottom". The first key can be safely provided to the person conducting the inspection, and the really important data will remain untouched until another password is entered. Neither software nor hardware methods can detect the presence of a hidden part.
However, this method has a number of problems: if you forget the access key, you will not have alternative ways to reopen access to the data. It will also not be possible to restore a faulty encrypted file. The only thing you can do in this case is to create a backup copy of this information elsewhere.
In addition, the speed of writing files to a crypto container is significantly lower than to a regular hard drive.
The following encryption programs are currently available on Google Play:
- LUKS Manager;
- EDS Lite;
- Cryptonite;
- CyberSafe Mobile.
LUKS Manager is the oldest file encryption program for Android. The program uses the AES encryption algorithm, while supporting the EXT2/4 and FAT32 file systems. The size of the encrypted container is limited only by the size of the phone's memory.
The advantages of the program include on-the-fly encryption and ease of use - encrypted containers are processed like regular folders.
Disadvantages: the program requires root rights to operate and does not support TrueCrypt containers, which are the de facto standard for major desktop platforms.
EDS Lite does not require root rights to operate and supports TrueCrypt containers. It uses two encryption algorithms - AES 256 and SHA-512.
Disadvantages: encryption is not on-the-fly and you cannot work with an encrypted container like a regular folder. However, there is a built-in file manager that supports all file operations. For example, you can create an encrypted container in EDS Lite or TrueCrypt, open it in the program's built-in file manager and copy all the files you want to encrypt to it.
The Cryptonite program is still in the testing stage. Its advantages include support for cloud drives. Disadvantage: it requires the Android kernel to support Kernel FUSE, and not every phone has this support.
The strong point of the CyberSafe Mobile application is the ability to synchronize crypto containers with Google Drive, which allows you to work with the same set of data on different devices. The application itself does not require root rights to work, but only until you decide to mount the container to a folder.
In addition, the application allows you to share encrypted files with other users and allows you to encrypt arbitrary folders on Google Drive. The application is paid. The free version limits the maximum password length to only two characters.
Methods for hacking crypto containers
One of the ways to hack a crypto container is a BruteForce attack, that is, a simple enumeration of various password options. With a strong password and encryption algorithm, a regular computer will take hundreds of years to crack it.
However, if this work is entrusted to a quantum computer, the cracking will take only a few days. The positive aspect is that this type of attack costs a lot of money and is unlikely to be used against an ordinary person, unless he is a particularly dangerous criminal. The
most effective protection against a BruteForce attack is onion encryption, when information is encrypted several times with different passwords, for example, first TrueCrypt encrypts files with one algorithm, and then AES Crypt with another algorithm.
For ordinary users, a much more real threat is a dictionary attack, which takes a database of passwords and checks each one. This attack is simple and relatively low-resource compared to a brute-force attack, which tries all existing options until the right one is found.
Success largely depends on the quality of the database and the complexity of the user's password. According to available data, one of the structures in Russia contains such a database of 250 million options.
The protection in this case is extremely simple: your password should not be in the database that will be used for hacking. If you use random generation of a password of 50 characters and a key, the hackers will not have a chance.
Thermorectal cryptanalysis
This general term refers to pressure to obtain passwords to access encrypted data. Pressure can range from a finger caught in a door to imprisonment for refusing to give up data.
In this way, any algorithms and passwords of any complexity are broken, but even in this case, you have several ways to protect yourself. The first of them assumes that access to the cryptocontainer will be physically destroyed.
To implement such a system, when creating a cryptocontainer, you need to add a key and place it on a microSD card. A microSD card is destroyed very easily, you can just break it with your hands and throw it out the window. After that, the information will no longer be recoverable, and, accordingly, there will be no way to access the encrypted data.
The second method of protection, already described above, is cryptocontainers with a double bottom.
The third method is to use professional software for emergency data destruction. Panic Button will not only instantly destroy cryptocontainers or key files without the possibility of recovery, but also clear passwords, browser history, history of viewing documents, pictures and running programs.
Forensic analysis of RAM
Removing and forensic analysis of a memory dump is a standard practice in forensics. Law enforcement agencies use special software to dump the RAM of digital devices. This dump is then studied, and valuable artifacts are found in it, such as encryption keys.
To protect against forensic analysis, it is enough to set the option to automatically dismantle the cryptocontainer and delete the key from the computer's RAM if there is no activity for a certain period of time.
In addition, you can use Panic Button - the program can delete valuable data from RAM if there is no activity.
Hacking a cryptocontainer using a spare key
This method is not dangerous for users of TrueCrypt, AES Crypt, VeraCrypt, LUKS, it refers to encrypted systems, but also deserves mentioning.
With complex encryption of the system, the keys for Microsoft encryption are saved by default in the Microsoft Account, the key for macOS encryption is saved by default in iCloud. Having gained access to the account, you can decrypt all the data on the hard drive, and therefore, when encrypting the system, disable saving the key in the cloud.
Conclusions
It is necessary to understand that on the side of border guards and police - if not the law, then the ability to interpret the law in their favor and the methods of coercion, which they do not hesitate to use.
From the point of view of your own safety, you should not object and lie to the border guards: all this will lead to additional complications in an already acute situation. It will be much more effective to use the complex of technical protection methods described in this material.
Remember: you can’t extract from your smartphone what is not physically on it, but any password from you can be obtained, if there is a desire.
Source

