CarderPlanet
Professional
- Messages
- 2,549
- Reaction score
- 723
- Points
- 113
This article is intended for those who either have not heard of Shodan at all, or have heard, but still do not understand how to use it. I did not find similar materials in Russian, I got some of the information here, and added the rest from personal experience. I will give examples of the use of the "scariest internet search engine" named Shodan. The service was developed by web-developer John Matherly and is focused primarily on finding devices connected to the Internet.
Shodan interrogates device ports and, based on the received response banners, draws conclusions about devices and services. The search engine is paid, an annual subscription will cost $ 20, however, you can try it in action for this: after a free registration, 50 search results are available. You will find the history of creation and biography of the author yourself, if it is interesting, but for now let's get down to business:
Filters
Search results can be filtered using the following constructs:
Example 1: Cisco Devices
In order to understand the first example, you need to remember how the main HTTP response codes are:
HTTP status codes:
In this example, we will try to find cisco devices with a web interface to access which does not require authorization.
First, let's see what a typical "401 Unauthorized" banner for a cisco device looks like if we just enter "cisco" in the search bar:
HTTP/1.0 401 Unauthorized
Date: Thu, 20 Oct 1994 05:18:36 GMT
Server: cisco-IOS
Connection: close
Accept-Ranges: none
WWW-Authenticate: Basic realm=«level_15_access»
Please note that the line "WWW-Authenticate: Basic realm ="level_15_access" indicates the need to enter a username and password.
In turn, the device in which authorization is not required will return us a banner with a status of 200 (for this we drive in “200 cisco” in the search bar, and the Last-Modified line is a sure sign that this is “our client”:
HTTP/1.0 200 OK
Date: Mon, 08 Sep 2014 22:28:16 GMT
Server: cisco-IOS
Connection: close
Transfer-Encoding: chunked
Content-Type: text/html
Expires: Mon, 08 Sep 2014 22:28:16 GMT
Last-Modified: Mon, 08 Sep 2014 22:28:16 GMT
Cache-Control: no-store, no-cache, must-revalidate
Accept-Ranges: none
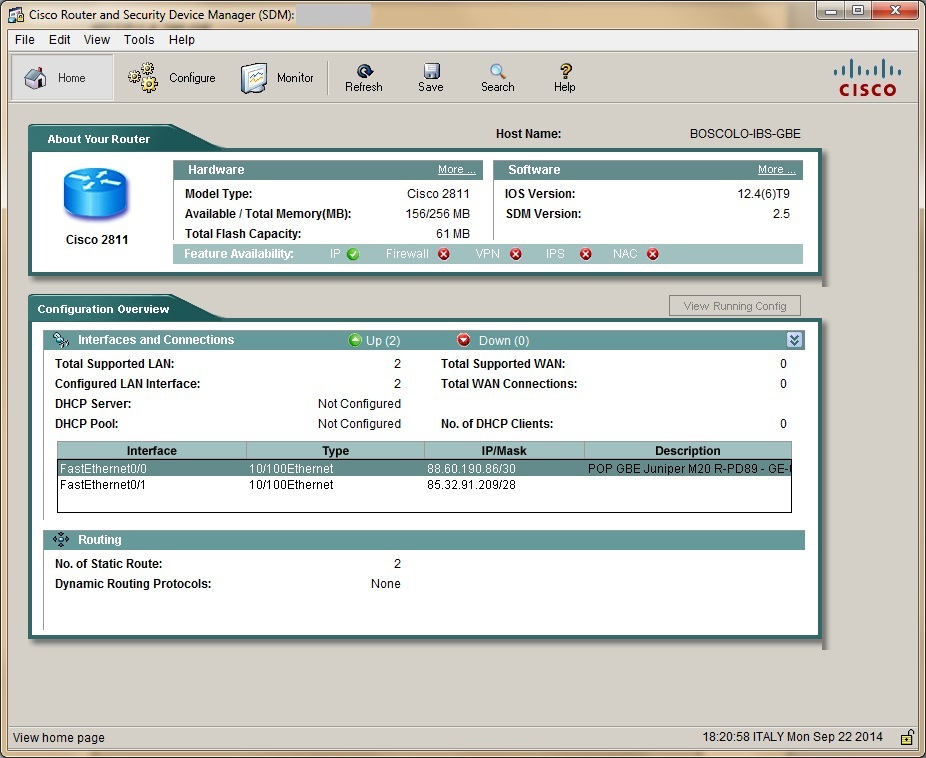
It is enough to follow the link ip-address: 80 and we get to the web-console for device management. I downloaded Cisco SDM for convenience.
Example 2: Default Passwords
Many devices with default logins and passwords are connected to the Internet, let's try to find something. To do this, write "default + password" in the search bar. Let's also add port: 80 to select www-authenticated devices.
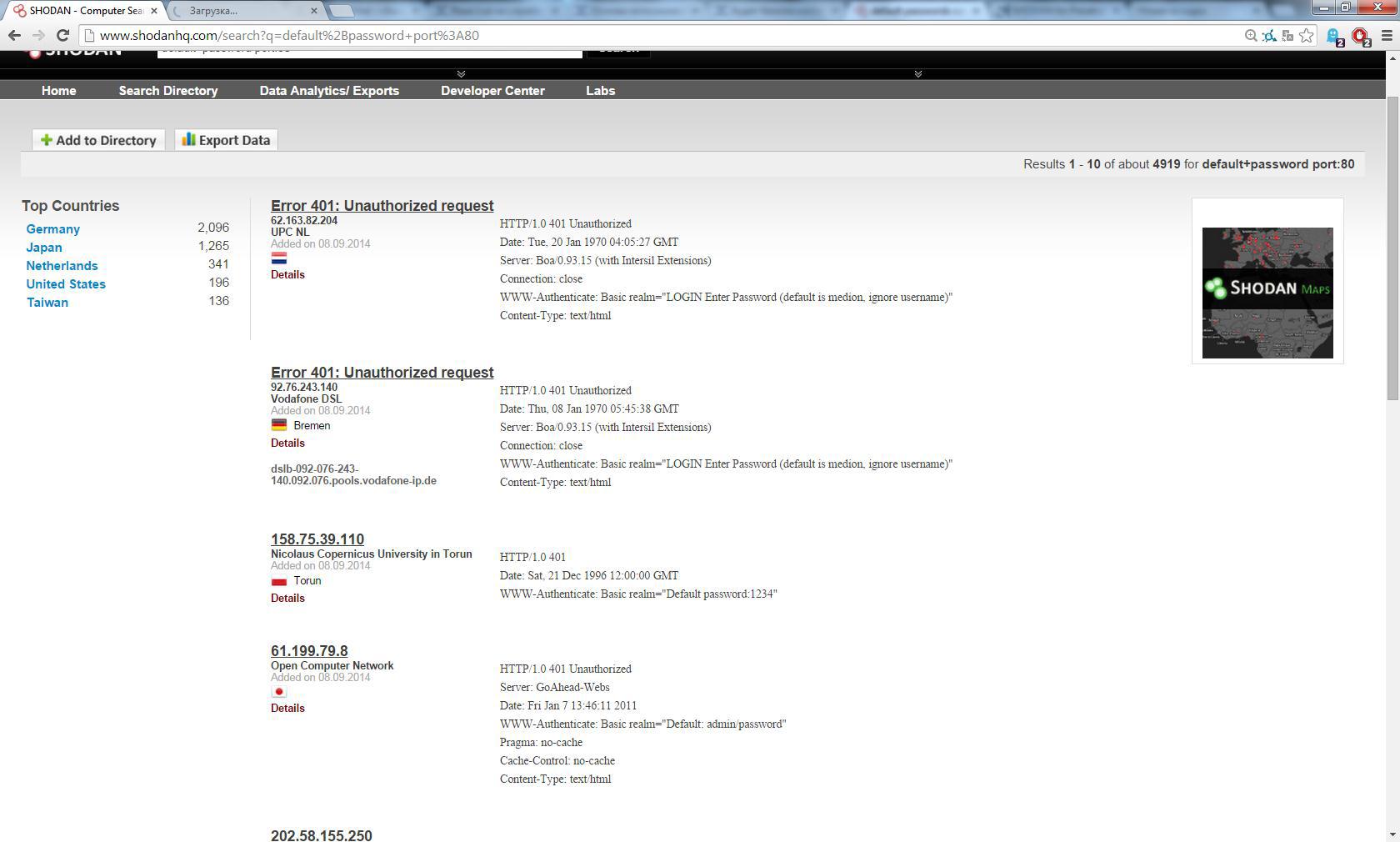
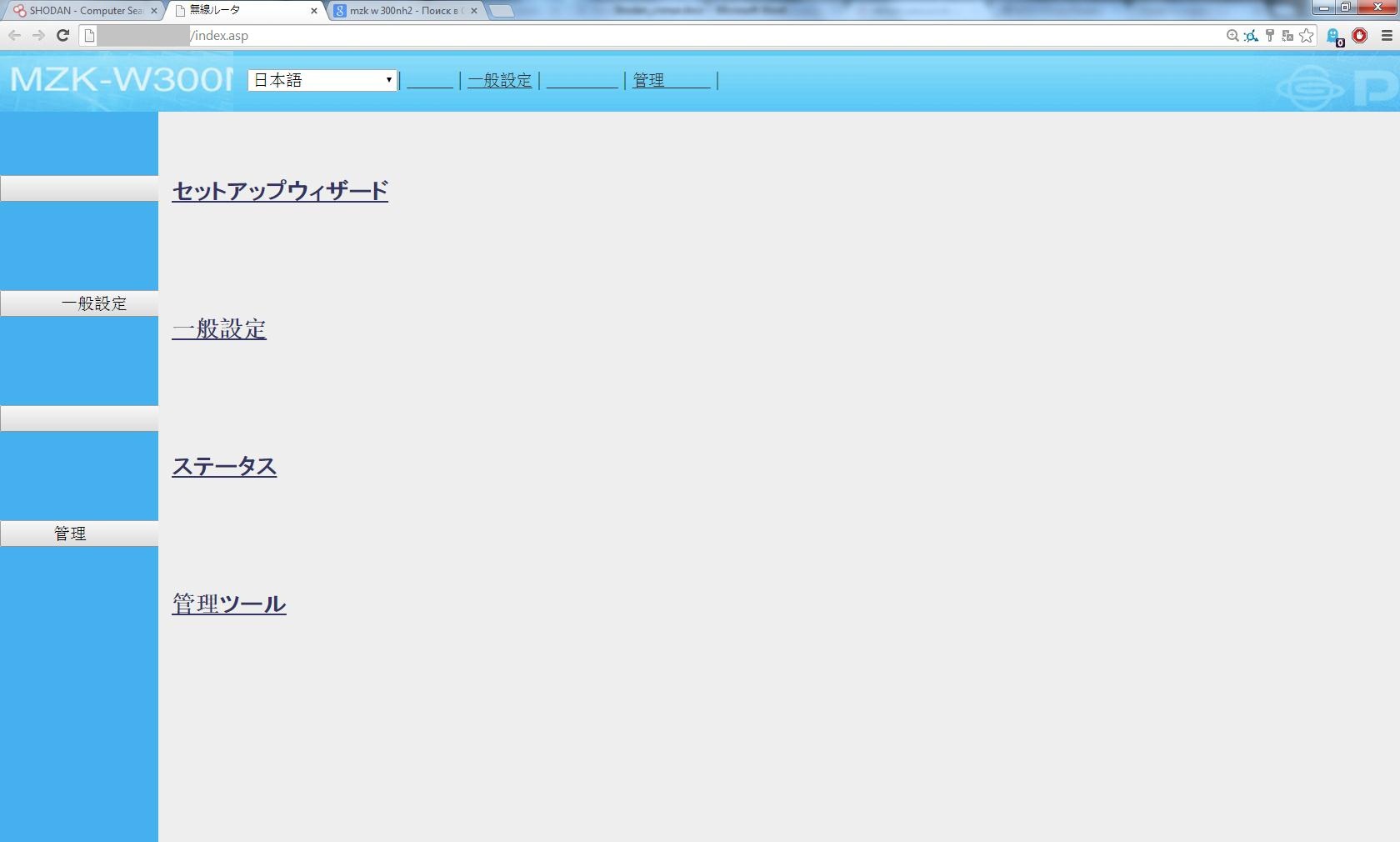
As a result, we will see a lot of banners containing the desired phrase, and, as practice shows, a large percentage of devices will have a login / password of the form admin / password, admin / pass, etc.,
Example 3: CCTV Cameras
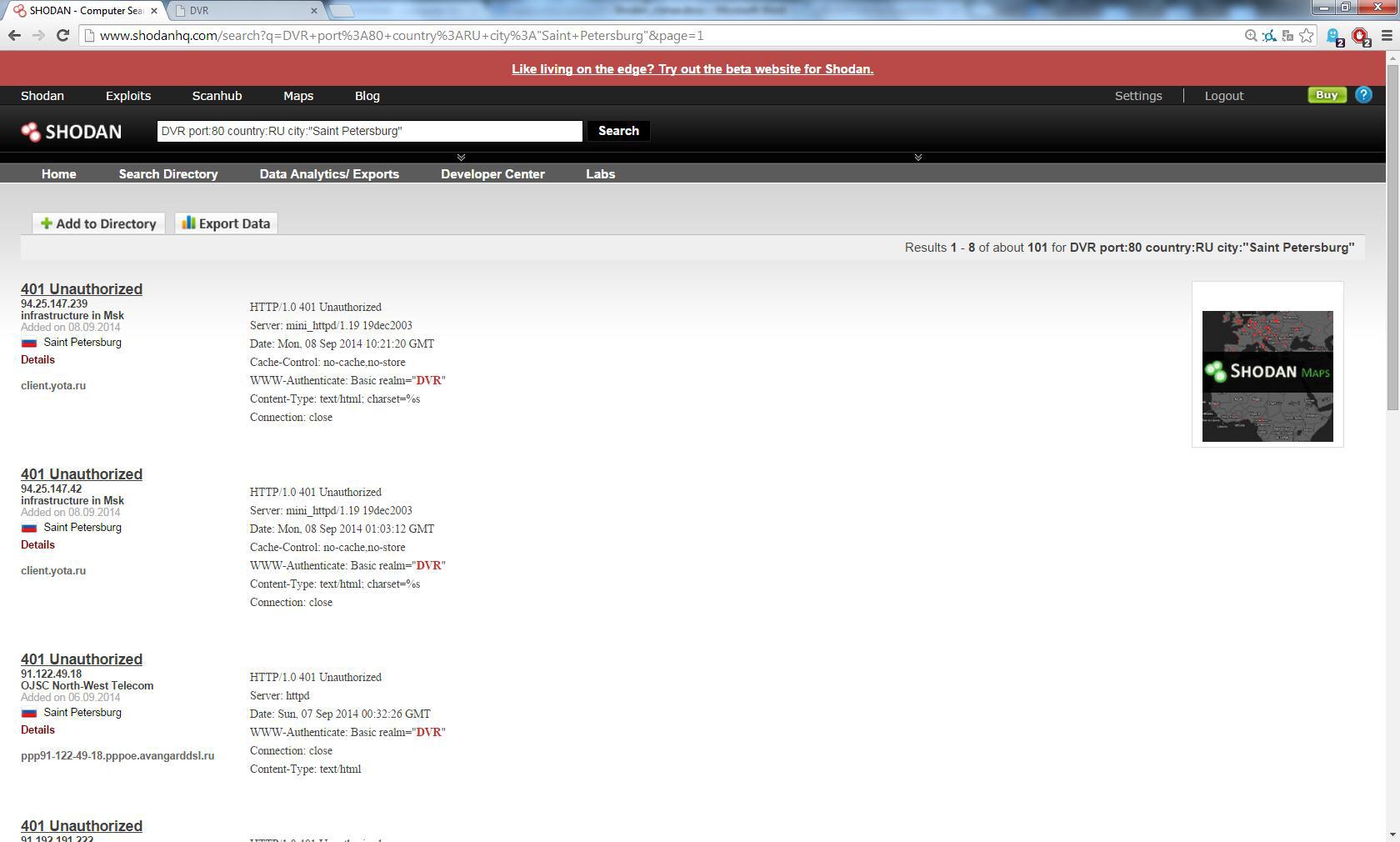
If in the case of network devices, users in most cases set more or less strong passwords, then with the rest of the equipment the situation is much worse. In this example, we will look at CCTV cameras. At work, I often have to deal with DVRs from DVR, some of them have a network connection. We write in the search bar: DVR port: 80 country: RU city: "Saint Petersburg" And we get a list of DVRs in St. Petersburg, about 200 devices were found.
Standard accounts on such devices are admin and user, passwords: admin, user, 1111, 1234, 123456, 8888 (can be found in the instructions). Already on the first page a device with a standard account:
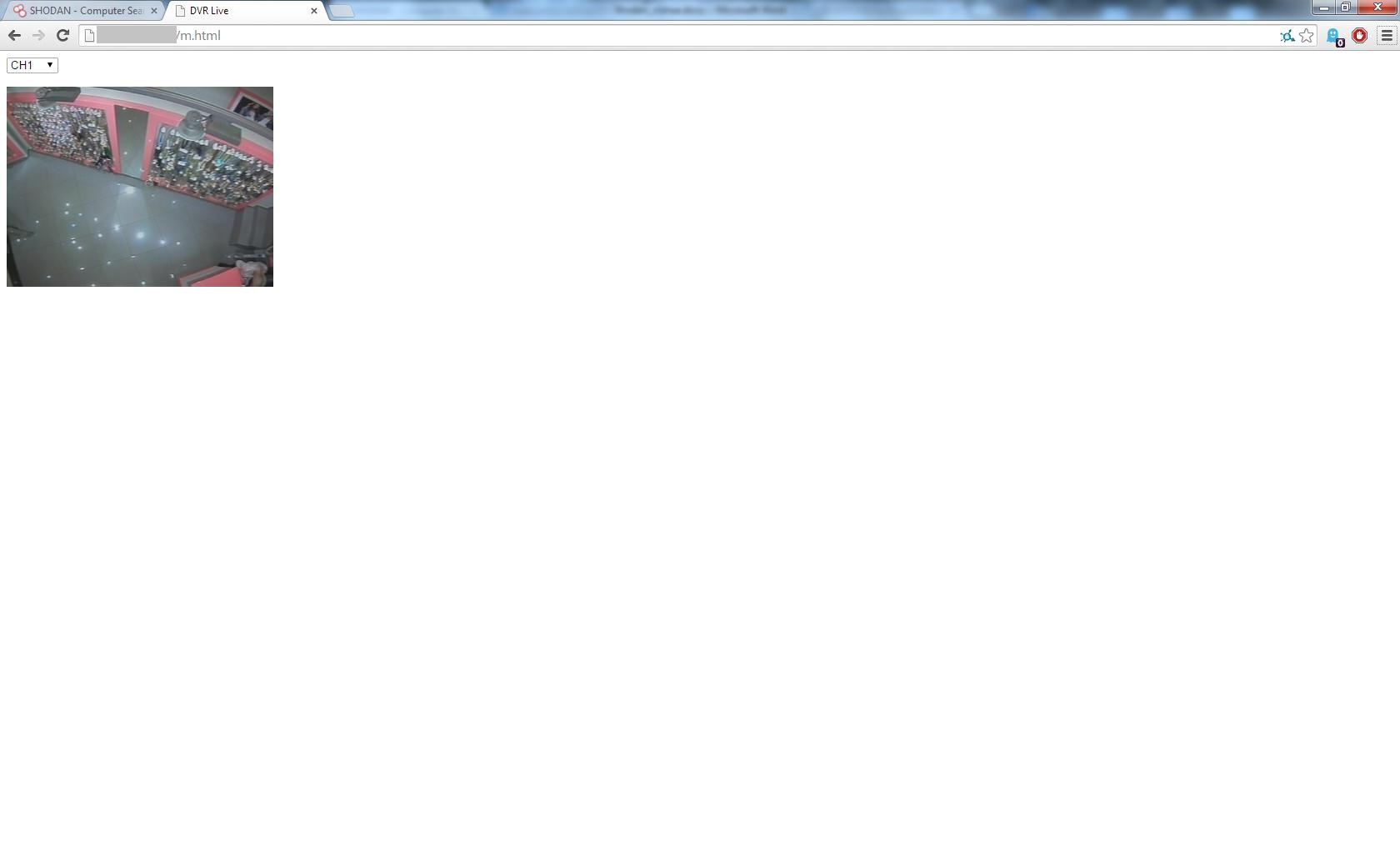
Example 4: Popular Sea
In the Popular Searches section, you can spy on query options, for example, search for ip-cameras from avtech in the United States: linux upnp avtech country: US, add the usual filter port: 80 to it:
And again, on the first page of the search, a device comes across, in which it turned out to be logged in with the help of admin / admin:
Outcomes
Summing up, I want to remind all users once again: please, set strong passwords on ALL devices connected to the network, if you do not have "secret" data in your DVR or smart-TV, this does not mean that these devices cannot become targets of intruders, even if just for fun.
Links
http://www.scribd.com/doc/34507835/SHODAN-for-Penetration-Testers-The-Next-HOPE - Presentation with examples (English).
- Usage video (English).
- John Matherly's Twitter
- official user guide (eng.)
habrastorage.org
Shodan interrogates device ports and, based on the received response banners, draws conclusions about devices and services. The search engine is paid, an annual subscription will cost $ 20, however, you can try it in action for this: after a free registration, 50 search results are available. You will find the history of creation and biography of the author yourself, if it is interesting, but for now let's get down to business:
Filters
Search results can be filtered using the following constructs:
- country: country, in the format RU, UK, US, etc., for example: nginx country: RU
- city: city, for example: nginx city: "Moscow" country: RU
- os: operating system, for example: microsoft-iis os: "windows 2003"
- port: port in the format 21, 80, 443, etc., for example: proftpd port: 21
- hostname: allows you to search based on domain, for example: nginx hostname: .de
Example 1: Cisco Devices
In order to understand the first example, you need to remember how the main HTTP response codes are:
HTTP status codes:
- 200 OK Request succeeded;
- 301 MovedPermanently Assigned a new permanentURI;
- 302 FoundResides under a different URI;
- 401 Unauthorized Request requires authentication;
- 403 ForbiddenRequest is denied regardlessof authentication.
In this example, we will try to find cisco devices with a web interface to access which does not require authorization.
First, let's see what a typical "401 Unauthorized" banner for a cisco device looks like if we just enter "cisco" in the search bar:
HTTP/1.0 401 Unauthorized
Date: Thu, 20 Oct 1994 05:18:36 GMT
Server: cisco-IOS
Connection: close
Accept-Ranges: none
WWW-Authenticate: Basic realm=«level_15_access»
Please note that the line "WWW-Authenticate: Basic realm ="level_15_access" indicates the need to enter a username and password.
In turn, the device in which authorization is not required will return us a banner with a status of 200 (for this we drive in “200 cisco” in the search bar, and the Last-Modified line is a sure sign that this is “our client”:
HTTP/1.0 200 OK
Date: Mon, 08 Sep 2014 22:28:16 GMT
Server: cisco-IOS
Connection: close
Transfer-Encoding: chunked
Content-Type: text/html
Expires: Mon, 08 Sep 2014 22:28:16 GMT
Last-Modified: Mon, 08 Sep 2014 22:28:16 GMT
Cache-Control: no-store, no-cache, must-revalidate
Accept-Ranges: none
It is enough to follow the link ip-address: 80 and we get to the web-console for device management. I downloaded Cisco SDM for convenience.

Example 2: Default Passwords
Many devices with default logins and passwords are connected to the Internet, let's try to find something. To do this, write "default + password" in the search bar. Let's also add port: 80 to select www-authenticated devices.

As a result, we will see a lot of banners containing the desired phrase, and, as practice shows, a large percentage of devices will have a login / password of the form admin / password, admin / pass, etc.,

Example 3: CCTV Cameras
If in the case of network devices, users in most cases set more or less strong passwords, then with the rest of the equipment the situation is much worse. In this example, we will look at CCTV cameras. At work, I often have to deal with DVRs from DVR, some of them have a network connection. We write in the search bar: DVR port: 80 country: RU city: "Saint Petersburg" And we get a list of DVRs in St. Petersburg, about 200 devices were found.

Standard accounts on such devices are admin and user, passwords: admin, user, 1111, 1234, 123456, 8888 (can be found in the instructions). Already on the first page a device with a standard account:

Example 4: Popular Sea
In the Popular Searches section, you can spy on query options, for example, search for ip-cameras from avtech in the United States: linux upnp avtech country: US, add the usual filter port: 80 to it:
And again, on the first page of the search, a device comes across, in which it turned out to be logged in with the help of admin / admin:
Outcomes
Summing up, I want to remind all users once again: please, set strong passwords on ALL devices connected to the network, if you do not have "secret" data in your DVR or smart-TV, this does not mean that these devices cannot become targets of intruders, even if just for fun.
Links
http://www.scribd.com/doc/34507835/SHODAN-for-Penetration-Testers-The-Next-HOPE - Presentation with examples (English).
- John Matherly's Twitter
- official user guide (eng.)
habrastorage.org

