Hacker
Professional
- Messages
- 1,044
- Reaction score
- 828
- Points
- 113

How do I find out if the VPN service keeps logs?
Nowadays, when computers and phones can monitor the user, security and anonymity on the Internet is important for all people.
Using a VPN service without logs allows you to completely solve the problem of anonymity.
First, let's find out – what are the logs of a VPN service?
What are VPN server logs?
Logs are any records that can help identify each client individually.
For example, a PPTP VPN doesn't have a built-in logout feature. And the log is written to the standard log file of the operating system. The PPTP VPN server log is shown in the image below, taken from the Internet.
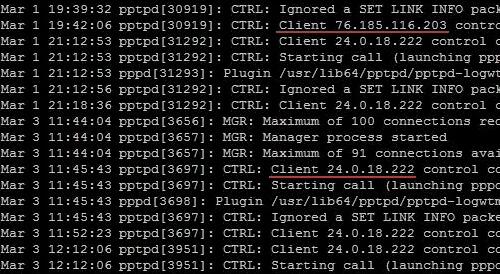
What does the PPTP VPN server log look like?
The standard PPTP and OpenVPN server log contains the connection time, the client's real IP address, and a set of commands that show the connection status.
The presence of real IP addresses of clients and the connection time makes it possible to accurately identify each client.
The following parameters can be used as client identification on the server:
- real IP address of the client issued by the Internet Service Provider
- internal client number in the system – a unique client ID in the system
- browser, OS, and connection time parameters – these data can be taken from the user's browser, traffic analyzer, and so on.
- internal IP address of the client when connecting to the VPN – this IP address can be of the form 10.0... or 192.168... and is used for forwarding traffic inside the VPN network
- external IP address of the client – this IP address will be displayed on sites on the Internet
Which is better – a shared IP address or a dedicated one?
We are often asked which IP address is best to use: shared IP for all users or dedicated IP for each client?
Since a unique dedicated IP address for each client can be a user identifier in the system, it is safer to use the shared IP address of the VPN server.
The abuse is sent to the server owner with the IP address and time of the attack.
If the service keeps logs, then these 2 parameters can be used to accurately calculate the client when using a dedicated IP address for each client.
We recommend using a static (permanent) shared IP address.
Now we know what server logs are and which IP address is best to use. Let's move on to the list of questions, having received answers to which, you will know for sure whether the VPN service keeps logs and whether it provides anonymous services.
List of questions for determining the anonymity of a VPN service
The most frequent question from customers who come to our technical support is whether your VPN service keeps logs?
And this is not surprising. Now many services write on the main page of the site that they provide an anonymous VPN. But in the small print in the “Terms of Use” they say that they reserve the right to record user data for their own security purposes.
In such cases, the question arises: can such a service be considered anonymous?
We have compiled a list of questions that can help you understand exactly whether the VPN service keeps logs and whether the services can be considered anonymous.
Ask these questions to technical support (or sales) and analyze the answers. You can just copy these questions from here.
We recommend using a trusted anonymous data transfer channel (anonymous VPN + TOR + proxy), as some services may cooperate with the police. The questions are related to information security, so they may start following you, thinking that you are a hacker.
How should I ask questions?
You need to ask 1 question in each email and wait for a response. Then send the second question and so on. If you write all the questions at once, you won't get honest answers.
Question 1. Where is your company's office located?
This question is more necessary in order to understand whether the company is officially registered and whether it has an office. Or it's a ghost company that only has a website.
POSSIBLE ANSWER 1: our office is located in a certain country and has a state registration.
This is bad, because the police can send a legal request to the company's office and the company will be required to respond to the police by law. By law, all companies are required to keep logs and monitor the activities of their customers. If they do not do this, then all legal responsibility for the activities of their clients falls on them.
All companies that are officially registered and have an office are required to keep logs and cannot provide anonymous services.
Usually, office addresses and company registration number are posted on the website.
POSSIBLE ANSWER 2: We only have a website. This option is better, since sending an email to technical support does not entail legal consequences.
POSSIBLE ANSWER 3: our company is registered offshore, in the Cayman Islands, or on an island where only palm trees and coconuts grow
Most often, they respond in this way to give their company status and credibility. But in fact, this is the answer 2. However, there are cases when the company is really registered in offshore countries. This is bad, as you can send an official legal request to this country, and the company will be required to give an official response in accordance with the law of this country.
Question 2. Does your service keep logs?
POSSIBLE ANSWER 1: yes, logs are kept.
You don't have to ask any more questions. Everything became clear. You can write to them, thank you for your honesty
POSSIBLE ANSWER 2: We collect some statistics on the use of our services. Go to question 3.
POSSIBLE ANSWER 3: no, not maintained. Go to question 4.
Question 3. What kind of statistics do you collect (what data)?
POSSIBLE ANSWER 1: personal data (for example: Email, connection time, browser version, OS, etc.)
In this case, it is only possible to identify the user. Most likely, the service keeps logs and is not anonymous. Go to question 4 to check it out.
POSSIBLE ANSWER 2: We use Google Analytics for statistics of visits to our site. There is nothing wrong with this, since Google Analytics only collects statistics on site visits. Go to question 4.
Question 4. You said that no logs are being kept. If I spam or attack websites through your VPN, will you block my account?
POSSIBLE ANSWER 1: no, we will not block your account, but if there are a lot of abuse, we will block access to the site through the VPN from which the abuse come. This way, your account will work, but you will not be able to access this site through our VPN. This means that this is an anonymous VPN service and does not keep logs.
POSSIBLE ANSWER 2: yes, we will block it. After all, we have a certain system that allows us to disable logs on the server, but at the same time identify prohibited client activity. Accordingly, your account will be blocked by this system. Go to question 5.
Question 5. Tell us more about how your security system works?
POSSIBLE ANSWER 1: We can't tell you because it's our secret.
This answer says only one thing – this service keeps logs and is not anonymous. Because if there was such a magical system, you could tell everyone about it and be proud of it. Unfortunately, such miracles do not happen.
POSSIBLE ANSWER 2: but most often after such questions, technical support (sales department) stops answering your questions at all. This also means that the service keeps logs and is not anonymous.
LAST QUESTION: Are you ready to test it for yourself?
If after answering all your questions, the service seems anonymous to you and does not keep logs, then you can make checks on yourself.
Further actions are performed at your own risk, as you will be responsible for your actions. We don't recommend that you do this. But these actions will directly answer your question whether the VPN service keeps logs.
Use the maximum number of protection methods (anonymous VPN + TOR + proxy). We will talk about perfect protection in the following articles.
The main point is to connect to the VPN server of this service and try to perform prohibited actions. If your account is blocked, then the logs are still kept and the service is not anonymous.
Once again, we don't recommend that you do this, but how else can you find out the truth?
Phenome - VPN service for $5
What does a customer who uses a low-cost service get? Many people think of low-cost security. There is no cheap security.
Winston Churchill said, ”You have to pay for security, but you have to pay for the lack of it."
Cons of a cheap VPN:
- A cheap or free VPN can be a decoy for the police. Such a VPN cannot provide anonymous services, but on the contrary can collect data about you companies specifically use a dynamic IP address so that each client can be identified by time and IP address. Each client receives a unique dedicated IP address when connecting
- cheapness is achieved by purchasing several servers and linking IP address packets from different countries to it. As a consequence, the use of Google DNS on all servers. Accordingly, your DNS will always be displayed as the United States, and you will change the exit points, for example, to Germany, Malaysia
- connection speed drops because more clients are on 1 server
- We recommend using an unreliable PPTP connection, as it is the easiest to configure. It is supported by all operating systems by default there are no OpenVPN configs for manually configuring the connection via the official open source OpenVPN app
Why are there so few anonymous VPN services without logs?
An anonymous VPN service that doesn't keep logs can't find out which clients are violating the rules. This is the main problem, as one unscrupulous client can interfere with the entire service.
Only the development of an anti-malware protection system can prevent VPN server clients from violating the rules (for example, sending spam, performing attacks, scanning server ports, etc.)
Usually, services are afraid of abuzz and it is easier to refuse a client than to respond to abuse.
We often say the word abuse. Let's take a closer look at what it is.
What is an abuse?
Abuse - from the English word abuse, which means complaint. If a site is attacked, you can write a complaint to the owner of this IP address. The abuse usually comes in the form of an email message.
A site that has been attacked via a VPN server sends a complaint to the owner of the IP address from which the attack was made.
Most often, the owner of an IP address is an organization, and it sends this abuse to the server owner. And already the server owner must take action to stop the attack.
Currently, there are already automatic systems for monitoring copyright compliance on the Internet.
For example, a user uploaded a torrent file with a famous Paramount Pictures movie to a torrent tracker. The system automatically finds the IP address of the client who did this and also automatically sends an abuse to the owner of the IP address from which the illegal download of the movie version was made.
The situation is similar with copies of e-books.
Example of an abuse when attacking a third-party server (image taken from the Internet). The abuse contains the external IP address of the attacker, the time of the attack, and the website that was attacked.
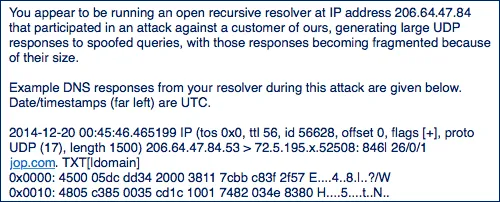
What does abuse look like when attacking a server?
On the Internet, users often ask whether it is possible to disable logs completely.
There are operating systems that allow you to do this. These operating systems include Linux (and all its variants).
For example, the "log /dev/null" command on Linux completely removes the OpenVPN service's log entry. Thanks to the settings, you can completely disable logging of connections to the OpenVPN server.
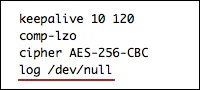
Disabling logs on the OpenVPN server
User tracking systems
There are systems for intercepting traffic and tracking user actions on the Internet, through telephone, fax, wireless and radio connections.
Such systems are installed in all data centers in the world and are located in front of the data center equipment or an Internet service provider. Access to all data is always available and you don't even need to write official letters to Internet service providers. The country's Security Service can view the necessary data itself without any permission from the Internet Service provider or users. Even the Internet service provider now doesn't know which user is being followed.
For example, the Solera system is installed in most CIS countries, Europe, and the United States.
The SORM system is being installed in Russia.
SORM-1 was introduced back in 1996 for listening to telephone conversations.
The SORM-2 system was introduced in 2000, and its functionality was expanded to track users on the Internet.
SORM-3 has already been implemented and here is a list of what it can do:
- binding network packets to user ids
- organize sorting and selection of data by IP address, email logins, social networks, instant messaging services, phone number, subscriber location
The user tracking system is implemented on all telecom operators in the world.
Thus, the system is already able to track users by IP addresses, social networks, unique browser identifiers, and phone number.
This raises an important question: is it worth using VPNs and other methods of protection if we are constantly being monitored?
Why use a VPN if SORM is monitoring us?
At the moment, the system is not able to decrypt traffic. And the only recommendation of the system manufacturer how to circumvent this is the suggestion to upload a virus to the client who would steal data from his computer, or by physical means to find out the encryption key from the user
Thus, using a VPN helps to solve the problem of surveillance.
The second important factor is that you need to use a VPN in conjunction with other security methods to make your stay on the Internet safe and anonymous.
Be an expert in Internet security. We will help you with this.
