Man
Professional
- Messages
- 3,222
- Reaction score
- 909
- Points
- 113
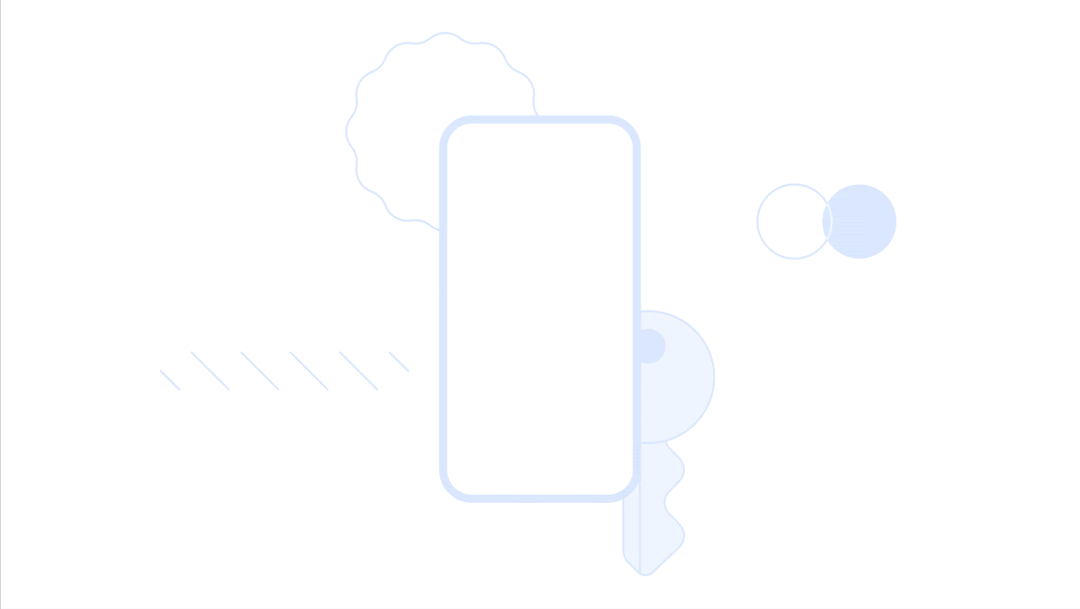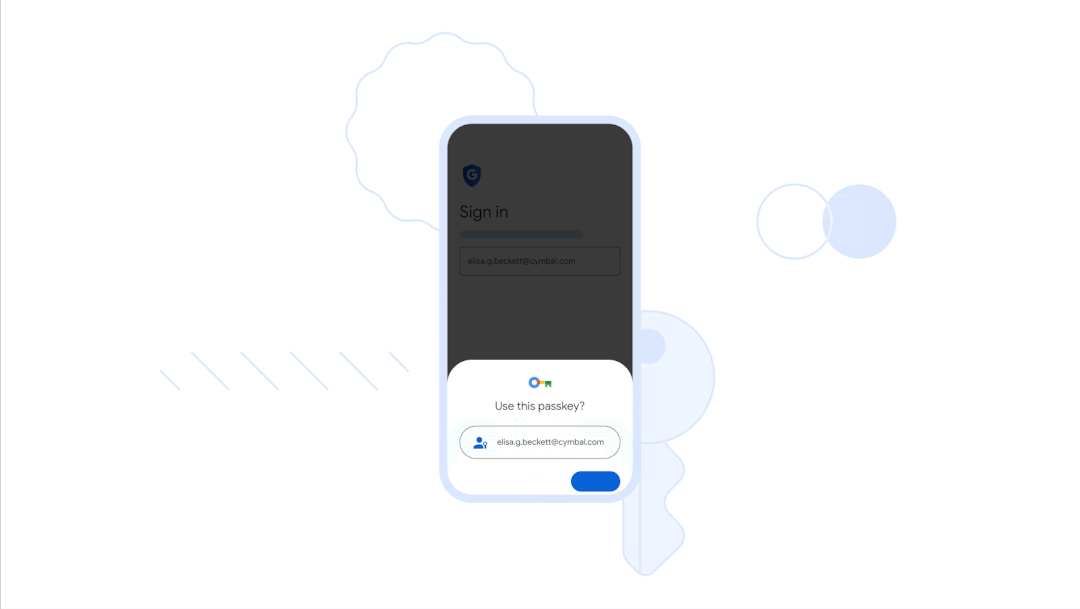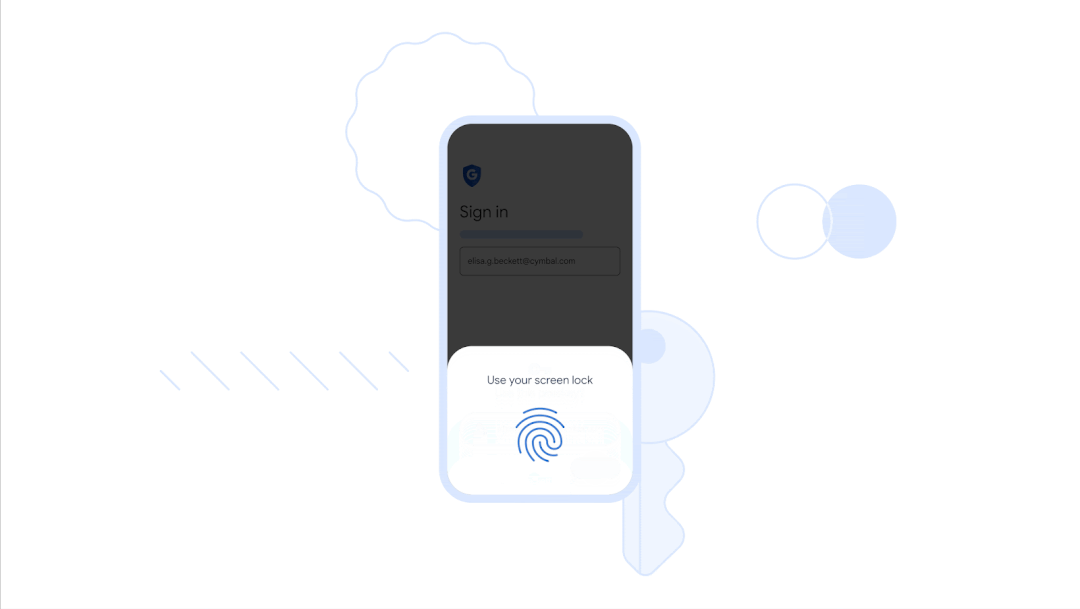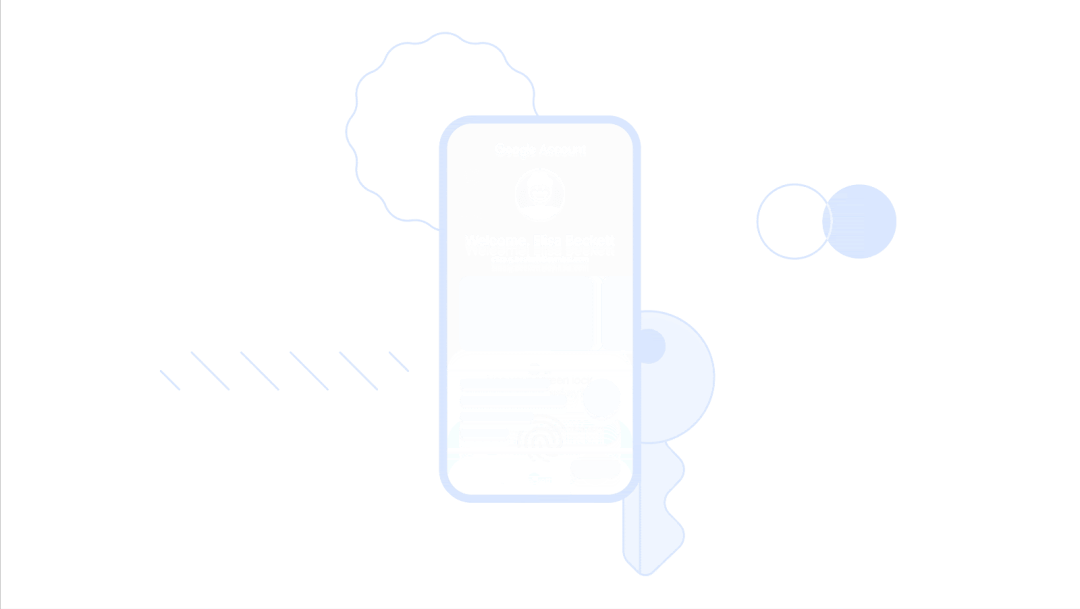
In May 2023, Google joined the general trend of abandoning passwords — and rolled out passkeys (access keys), which allow you to log into your account without a password, but with a finger, face, local PIN code or hardware key. That is, log in to Google using the same method you use to log in to the operating system (on a smartphone or PC). Microsoft had previously announced its abandonment of passwords.
By their nature, passkeys cannot be “lost”. They cannot be used by an intruder. Developers say that such keys are more secure than regular passwords and even more secure than 2FA via SMS, since SMS is easy to intercept.
Although some are talking about the beginning of a post-password era, such optimism still seems a little excessive.
Access keys have been supported on all Google accounts since May, and on some Workspace and Cloud accounts (testing) since June. The Chrome browser has supported passkeys since December.
What is this?
Access keys as a two-step verification method (2-Step Verification, 2SV) are a more convenient and secure alternative to passwords. They work on all major platforms and browsers, allowing you to sign in by unlocking your computer or mobile device using your fingerprint, face recognition, or local PIN.
To create an access key, you need to follow a special link and log in to your account.
After that, Google will start asking for the key when you sign in or perform important actions in your account.
The key itself is stored on the user's local computer or mobile device. To access it, the device checks the fingerprint, face, or PIN to confirm the owner's identity.
Unlike passwords, access keys exist only locally. They cannot be written down or accidentally transmitted to an intruder. When you use a login key, it proves that you have access to your device and can unlock it. Together, this means that keys also protect against phishing, password reuse, or data leaks. According to the developers, this is more reliable protection than most modern 2SV methods (2FA/MFA).
Creating an access key makes it an option to sign in to a Google account. Other methods, including a password, still work when using devices that do not yet support keys.
Access keys are still a novelty and will take some time before they work everywhere. However, creating a key already provides security benefits, Google believes, because it allows you to more carefully consider other cases of sign-in, without using keys, as potential signs of an attacker.
How does this work?
The keys work according to a standard asymmetric cryptography scheme. The main component is a private key, which is stored on the device. When it is created, the corresponding public key is uploaded to Google. When you log in, it asks the device to sign a unique challenge using the private key. The device does this only with the user's approval, which requires unlocking the device. The system then verifies the signature using the public key. That's it.
This scheme ensures that the signature can only be shared with a specific party (Google), and not with phishing intermediaries. So there is no risk of leakage and no phishing site can harm the user. The only data that is transmitted to the server in this scheme is the public key and the signature. Neither of these contains biometric data.
Since each key can only be used for one account, there is no risk of reuse across different services.
The access keys are built on the protocols and standards of the FIDO Alliance and the WebAuthn working group. That is, they are open standards. Any web developer can implement such a scheme to authenticate users on their servers.
For more information on key support on the Chrome and Android platforms, see the developer documentation.
Multimodal authentication
In fact, passwords have become very familiar to the average user over the years.
Among the most common authentication methods, fingerprint scanning is considered the simplest and most secure (see table below). At the same time, entering a password is slightly more comfortable and natural (second line in the table), although the difference between them is not too great.

Source: "Multimodal User Authentication in Smart Environments: A Study of User Attitudes" (arXiv:2305.03699v2, second version of the preprint published May 23, 2023)
Interestingly, people's willingness to use increasingly complex authentication methods increases when they are alone (or at least in the company of a spouse). In public, the desire to use strong authentication decreases:

Source same
A future without passwords?
Overall, humanity still has a lot to improve on the path to better authentication, namely, to achieve a balance between convenience, reliability, privacy, ease of use, and security. This pentabasis is depicted in the following illustration:
Let's hope that Passkeys is a step in the right direction. But we should not forget that among all authentication methods, entering a password is still the most comfortable and natural for users (see the research results above).
And in the case of access keys, we must remember that in this case, losing control over the device (smartphone) automatically means compromising the Google account, because there is no password protection. Google itself acknowledges the problem and writes: "Anyone with access to the device and the ability to unlock it will be able to sign in to your Google Account. While this may seem a little alarming, most people find it easier to control access to their devices than to maintain a high level of security with passwords and constantly monitor phishing attempts."
Perhaps we are really witnessing the beginning of a passwordless future, but it is not yet clear. Some experts consider WebAuthn a dubious standard: "It removes almost all risk from the service provider and places all responsibility on the user. Since the keys are just strings, nothing prevents us from storing them anywhere. We already do this – storing SSH or GPG keys is something we do every day. However, this does not apply to the general public. I can’t imagine a grandmother who has to make sure she never loses this file, writes Michal Sapka, a Polish developer. – As mentioned above, Apple and Google are trying to become the guardians of private keys. At first, this sounds great: the key will be stored and synchronized automatically in a Google or Apple iCloud account. But after some thought, it turns out that this is not the best idea for most people.
Firstly, it is unsafe. It is known that corporations can block user accounts without reason. Secondly, it makes it difficult to use different ecosystems at the same time, and even more so – alternative OS and browsers. That is, handing over your keys to an external party for storage is not always a good idea, according to some experts.
In any case, it is too early to give up passwords in the most secure systems.
Source
