Man
Professional
- Messages
- 3,223
- Reaction score
- 1,148
- Points
- 113

As you know, a password is only the first stage of authentication, and the least reliable one. A password can be intercepted while being entered (from a keyboard or screen), during transmission to a server, brute-forced, copied from a storage location (including from a company server whose security is not under our control), or learned from a person. Even having a password manager does not improve the situation much.
Two-factor authentication (2FA) is mandatory today, because the second factor significantly increases the effort required to hack. The standard second factor is a phone, where an additional code is sent. Another additional factor is a hardware security key that cannot be copied. Such a key can protect access to your password manager.
Let's see how such keys are made, who issues them. And most importantly, how to make them even better.
U2F standard
The current open authentication standard is U2F (Universal 2nd Factor), promoted by the FIDO alliance.
U2F is an open, driverless 2FA protocol that allows Internet users to use a U2F device as a second factor for authentication on a large number of online services.
A challenge-response authentication scheme is used:
- The relying party sends some data (i.e. generates a challenge) and a handle to the signing key to the browser.
- The browser adds to this the URI from which the signature request was made and the TLS channel ID and sends it to the U2F device.
- Using the key descriptor, the device selects the corresponding private key for signing.
- To prevent cloning of the device, there is a counter inside it that increases its value with each authentication. Its value is also signed and sent to the verifying party.
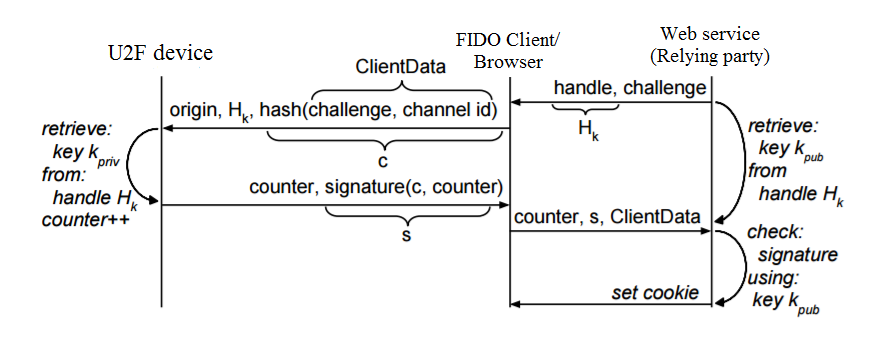
The ECDSA algorithm over the P-256 curve is used for signing, and SHA-256 is used for hashing.
Manufacturers
U2F keys are issued by several companies, including:
- Yubico: Security Key, Security Key NFC, Security Key C NFC, YubiKey 5C, 5C NFC, 5Ci, 5 NFC)
- Google: Titan dongle line (USB-A/NFC, USB-C/NFC);
- Thetis (FIDO U2F and BLE U2F)
- SoloKeys (Solo USB-C, Solo USB-A, Solo Tap USB-C, Solo Tap USB-A)

In practice, using such a key is intuitive and simple:

Own security keys
But nothing stops engineers from looking for better solutions instead of existing ones.
For example, the Swedish company Multivad, which deals with software solutions in the field of information security, recently decided to design and manufacture its own security key on the RISC-V platform with 128 KB of RAM. For this purpose, a separate subsidiary Tillitis AB was registered. Its first product will be Tillitis Key - a new type of security key created using DICE and Measured Boot technologies.
For reference, Measured Boot is a function of checking the hardware firmware during each boot, with saving information in the Trusted Platform Module (TPM), first introduced in Windows 8.
DICE (Device Identifier Composition Engine) aka RIoT (Robust | Resilient | Recoverable - IoT) is an industry standard of the Trusted Computing Group for TPM-based microcontrollers.

The Tillitis
Tillitis Key assumes the function of user programming and the use of arbitrary user applications (on 128 KB of RAM). As the description says, during use, the firmware on the Tillitis Key extracts a unique key for each application launched, checking it before execution:
This is done by combining the application hash with a unique secret for each device. Applications are downloaded to the device from the host computer during use and are not stored permanently on the device.
A user- or host-provided secret can also be mixed into the key derivation function, providing additional security. It is assumed that an advanced hardware attacker knows the hash of the target application and is likely to eventually extract the UDS from the hardware. With the addition of a host-provided secret, knowledge of the application in use and the UDS security key is not enough to obtain the application secret. Thus, the security impact of losing or stealing the Tillitis Key is less than with regular security keys.
Device applications can be chain-loaded, with the first stage of the application passing its secret to the second stage. This improves the user experience by keeping the application secret (and its public key) unchanged even when the application is updated on the device. It also allows developers to define their own software update trust policies. A simple stage one application might perform code signature verification in the second stage, while a more advanced application would require m-of-n code signatures or Sigsum inclusion proof given built-in use cases.
In general, taking into account such scenarios, the programmable security key can be used in more advanced security policies than modern U2F keys.
Most importantly, Tillitis Key is developed on an open design, that is, the circuits and materials/components for the manufacture of the hardware key are published in the public domain. On the one hand, this guarantees the absence of hardware bugs in it and increases trust in the product. On the other hand, anyone can theoretically order the production of exactly the same products or even assemble something similar in a single copy specifically for themselves.
We can recall another attempt to design a security key with an open design and the use of reliable cryptography - Solo V2 keys from SoloKeys, which successfully raised funding on Kickstarter in 2021 and are now in production.


Solo V2 keys are made on the open source Trussed framework for modern cryptographic applications. The idea is that all cryptographic primitives are collected in the firmware. The source code is published on GitHub.
Anyone can use these cryptographic primitives, as well as firmware from SoloKeys, in developing their own cryptographic products, both hardware and software. For example, the German company Nitrokey copied this entire stack and released its own keys. Any startup can set up such production. Everything is completely legal, and proven cryptography is used.
Open ecosystem
Overall, the Trussed developers would like to form a large open ecosystem of “trusted security applications” that would include WireGuard, password managers, GPG, pocket HSMs, and other hardware and software on the open stack. “All of this will eventually replace JavaCard and bring embedded cryptographic firmware into the modern era”, they hope.
Source
