File sharing sites are becoming a new attack vector on Israeli companies.
The information security company Proofpoint has discovered a new phishing campaign of the Iranian group MuddyWater, during which legitimate software for remote monitoring and management of Atera is distributed among Israeli organizations in the fields of global manufacturing, technology and information security.
A distinctive feature of the attack, which took place from March 7 to 11, is the placement of files on file sharing sites (Egnyte, Onehub, Sync and TeraBox) and the use of phishing messages on the topic of bill payment or salary information sent from a hacked account associated with an Israeli domain "co.il".
Clicking on the link in the attached PDF document downloads a ZIP archive containing the MSI installer, which ultimately installs Atera Agent on the compromised system. The MuddyWater Group started using Atera Agent in July 2022.
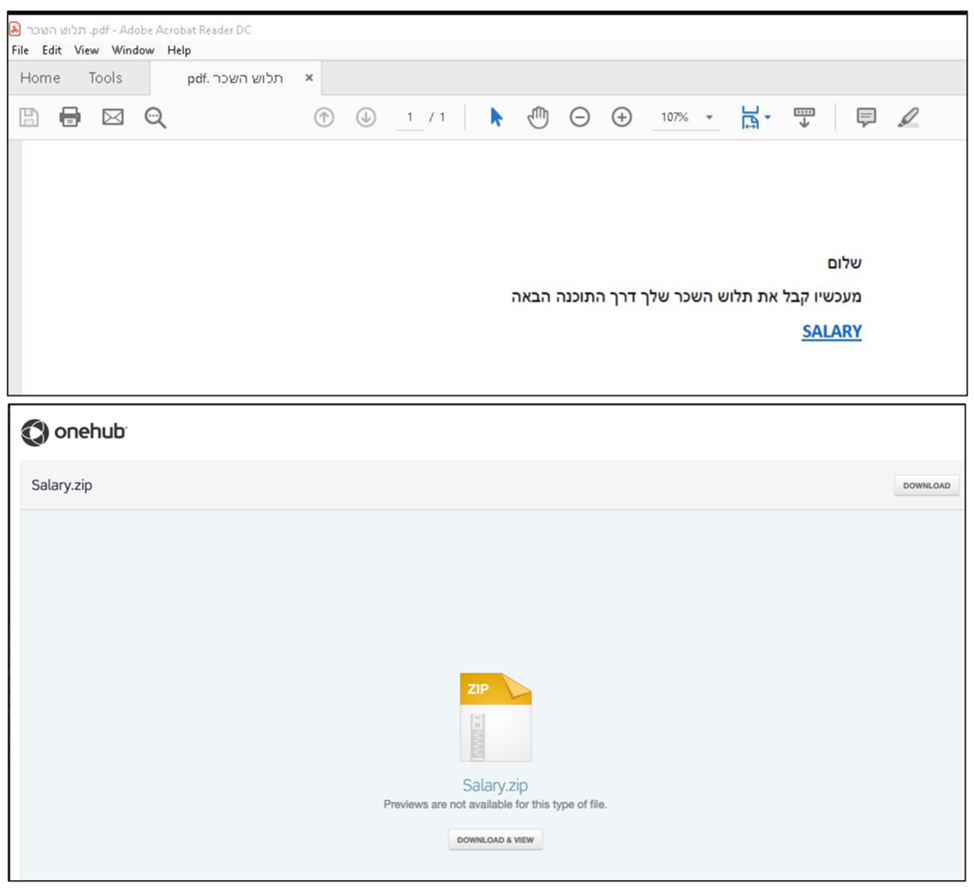
A PDF document with a malicious link will lead to downloading the archive
The detected activity is notable in that it marks a turn in MuddyWater tactics. While the campaign is not the first observed instance of a group using attachments with malicious links, Proofpoint researchers first observed MuddyWater's attempt to deliver a malicious link in an attached PDF file instead of a direct link to the file in an email.
Proofpoint researchers credit the MuddyWater campaign with building on the group's well-known techniques, tactics, and procedures (TTPs), campaign targeting, and malware analysis. In 2022, the US Cyber Command linked the group to the Iranian Ministry of Intelligence and Security.
The information security company Proofpoint has discovered a new phishing campaign of the Iranian group MuddyWater, during which legitimate software for remote monitoring and management of Atera is distributed among Israeli organizations in the fields of global manufacturing, technology and information security.
A distinctive feature of the attack, which took place from March 7 to 11, is the placement of files on file sharing sites (Egnyte, Onehub, Sync and TeraBox) and the use of phishing messages on the topic of bill payment or salary information sent from a hacked account associated with an Israeli domain "co.il".
Clicking on the link in the attached PDF document downloads a ZIP archive containing the MSI installer, which ultimately installs Atera Agent on the compromised system. The MuddyWater Group started using Atera Agent in July 2022.

A PDF document with a malicious link will lead to downloading the archive
The detected activity is notable in that it marks a turn in MuddyWater tactics. While the campaign is not the first observed instance of a group using attachments with malicious links, Proofpoint researchers first observed MuddyWater's attempt to deliver a malicious link in an attached PDF file instead of a direct link to the file in an email.
Proofpoint researchers credit the MuddyWater campaign with building on the group's well-known techniques, tactics, and procedures (TTPs), campaign targeting, and malware analysis. In 2022, the US Cyber Command linked the group to the Iranian Ministry of Intelligence and Security.
