Man
Professional
- Messages
- 3,051
- Reaction score
- 577
- Points
- 113
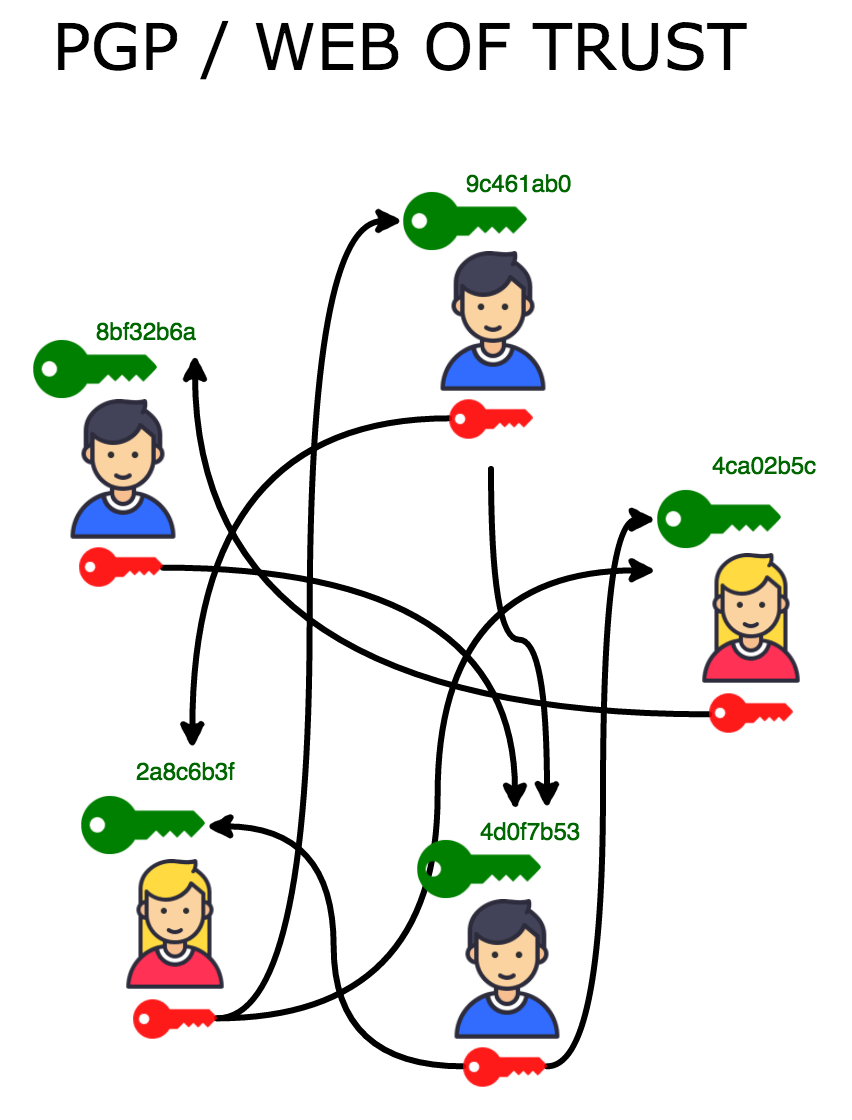
Nowadays, encryption is as relevant as ever. Communication is moving to instant messengers, people continue to encrypt electronic messages with digital certificates, but sometimes this may require additional efforts, including exchanging keys through a web of trust. In such circumstances, even some long-time cryptography enthusiasts are forced to abandon PGP. For secure messaging, open-source instant messengers with reliable end-to-end encryption, such as Signal, are much more convenient (see the guide from the Electronic Frontier Foundation).
At the same time, PGP is still used in “machine” operations: for signing packages, encrypting files on disk, etc. But here, too, PGP is gradually falling out of use. For example, the Go community suggests stopping support for the OpenPGP package, due to the “ancient protocol that still causes serious vulnerabilities,” as well as the unsolved problem of key exchange and, most importantly, the outdated implementation of the protocol itself.
Why even old users are abandoning PGP, writes the famous information security specialist Filippo Valsorda, who is part of the crypto group of the company Cloudflare and is known as the author of the Heartbleed vulnerability testing service:
First, the lack of adoption of encryption that others have talked about hasn’t gone away. I received maybe two encrypted emails a year, at most.
Then there’s the inconvenience. Critical bugs that are easy to make. Confusing server listings with keys that are years old. “I can’t read this email on my phone.” “Or on my laptop, I left keys I never use on another machine.”
But the real problems I’ve seen are much more subtle. I’ve never felt like my long-term keys are safe. The more time has passed, the less confident I’ve become in any given one. YubiKeys can get intercepted in a hotel room. Offline keys can get left in a drawer or safe far away. New vulnerabilities can be announced. USB devices can get hooked.
The security of long-term keys is the least common divisor of your lifetime security actions. That’s the weak link.
To make matters worse, existing long-term key management practices, such as collecting key signatures and printing public key fingerprints on business cards, conflict with other behaviors that would otherwise be considered obvious good hygiene: changing keys frequently, having different keys on different devices, and compartmentalization. Existing long-term key management practices actually widen the attack vector by encouraging key backups.
This is a pretty comprehensive explanation. But the question arises: if not PGP, then what to use? With email, it is clear, it can be replaced with instant messengers with reliable end-to-end encryption. But what to use for signing packages and software updates and encrypting files? Fortunately, there are modern alternatives here too .
Package Signatures
Linux distributions and many software update systems use PGP signatures to ensure the authenticity of files.
For signing packages, there are simple alternatives, such as signify (sign and verify) from OpenBSD and minisign. These are extremely simple utilities, but thanks to this, they are extremely reliable. Both work with a single algorithm, Ed25519 (ErDSA): a digital signature scheme using a variant of the Schnorr scheme on the Edwards elliptic curve. It is designed for maximum speed and is much faster than RSA. Since both utilities are based on the same algorithm, their digital signatures are compatible with each other, i.e. signify can verify signatures generated by minisign, and vice versa.
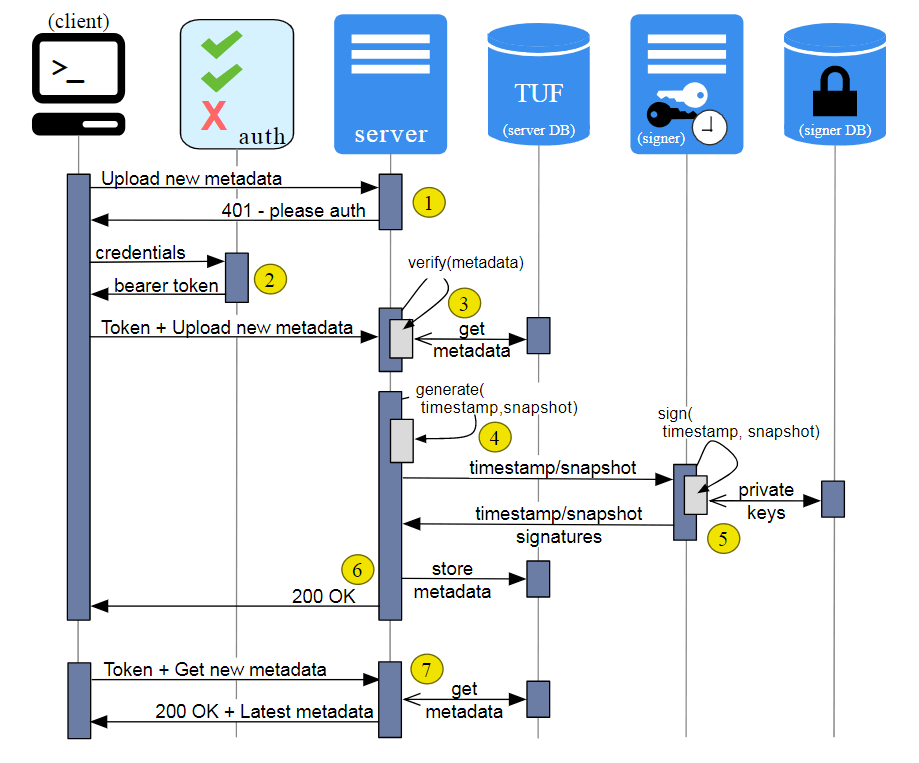
These are the most minimalistic alternatives, without the slightest additional functionality. If you manage a serious infrastructure with package distribution and need a more functional option, you can take a look at The Update Framework (TUF): a flexible framework that can be adapted to any software update mechanism.
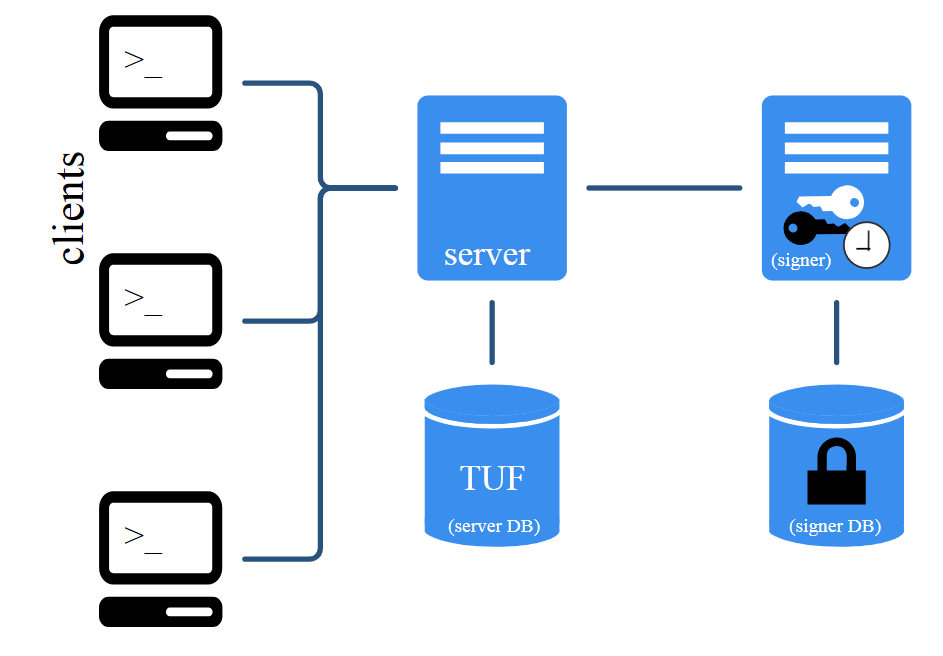
The developers write that TUF is used in production by companies such as Cloudflare, Docker, DigitalOcean, Flynn, IBM, Microsoft, LEAP, Kolide, and Vmware, and a TUF variant called Uptane is widely used for over-the-air updates of automotive software.
TUF implementation for Python package infrastructure: PEP 458, PEP 480. The Notary project is based on TUF, with a ready-to-use and tested client-server implementation.
File encryption
Modern alternatives to nacl/box and nacl/secretbox are universal programs for encrypting any data. They support symmetric and asymmetric encryption, modern ciphers and protocols.
The Keybase service is suitable for encrypting chat messages, emails, files or any other data. The main Keybase website is a public key directory that matches social network profiles with encryption keys. Keybase also offers encrypted chat (Keybase Chat), cloud file storage (Keybase file system or KBFS) and Git repositories.
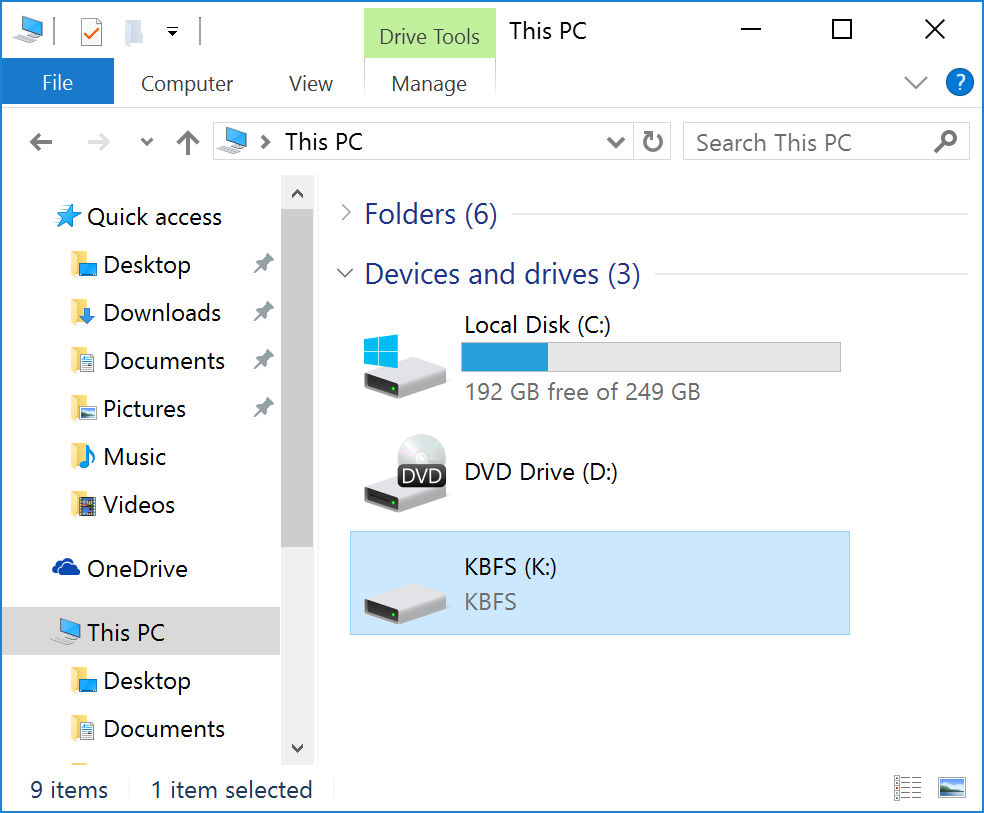
KBFS file system mounted by Keybase
Overall, this is a fully functional alternative to PGP for data encryption.
Transferring encrypted files
In the last century, it was common to encrypt a file, protect it with a password and send it as an attachment by e-mail. This option is still possible today, but there are more modern alternatives. For example, the Firefox Send service for exchanging encrypted files has recently left beta. Files are encrypted on the sender's computer and decrypted on the recipient's computer (JS in the browser). The service generates a link to the file with a limit on its lifetime or number of downloads.
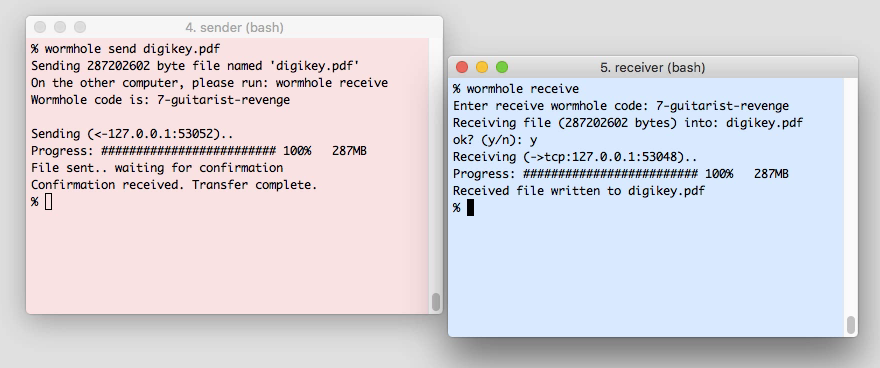
If you do not trust JS, then you can encrypt files, for example, using the magic-wormhole program. The program is installed on the sender's and recipient's computers, uses modern PAKE (password-authenticated key agreement) cryptographic technology and generates passwords from several words, breaks through firewalls and supports Tor. We live in the 21st century. There are much better options than sending encrypted files by e-mail.
Certificates for signing documents of Microsoft Office, Adobe PDF, LibreOffice, etc.
Source
