Man
Professional
- Messages
- 3,222
- Reaction score
- 1,212
- Points
- 113
According to the independent research and consulting company Frost & Sullivan, TLS certificates from GlobalSign provide the most reliable encryption. In particular, for this, GlobalSign received the 2022 Global Competitive Strategy Leadership Award in September 2022.
But the question arises: how does encryption differ in different certificates? In particular, what algorithms are used for cryptographic signature?
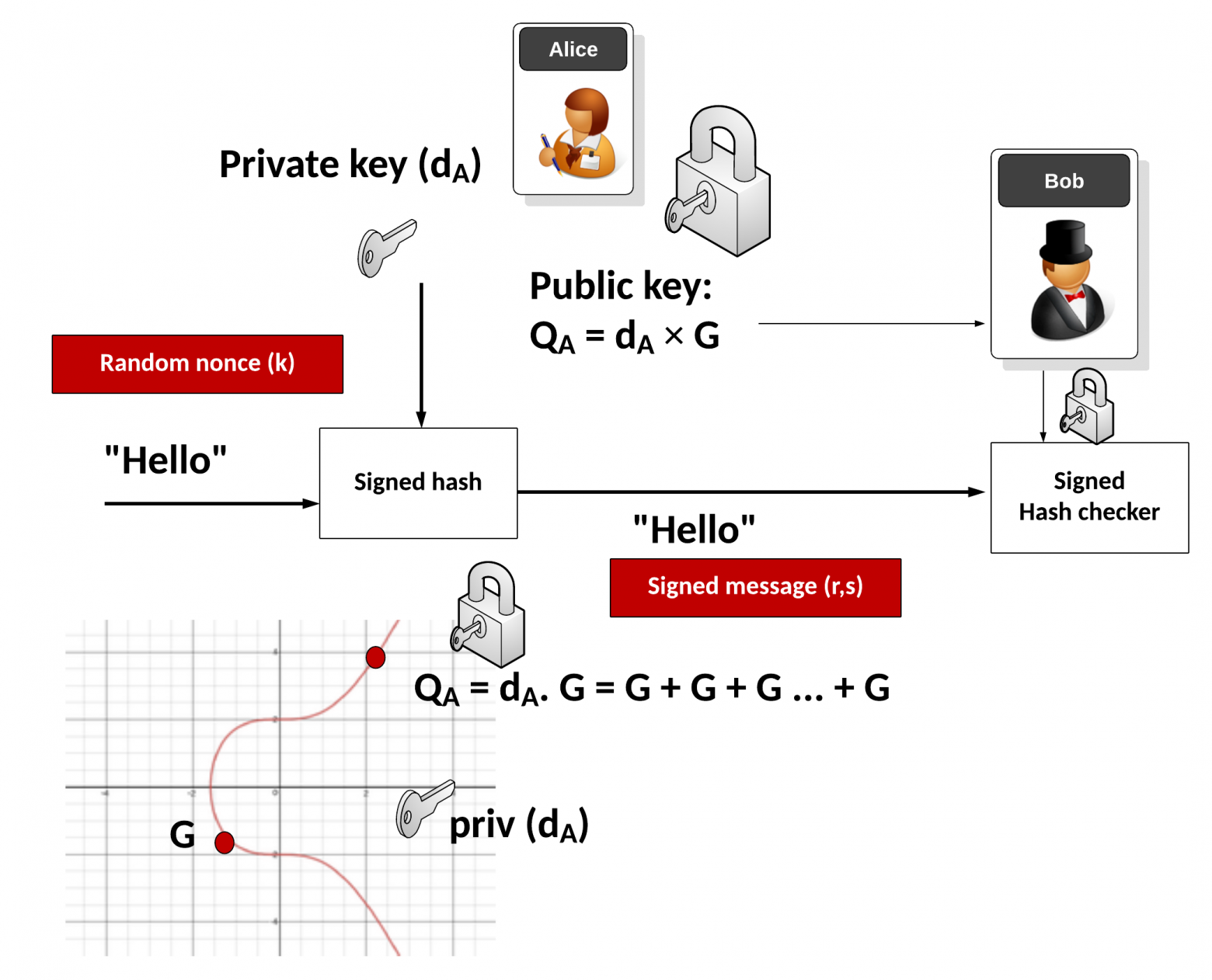
As you know, a digital certificate verifies that a public key belongs to a named entity and specifies the expected ways of using this key. This allows others to rely on signatures made using the private key that corresponds to the certified public key.
A TLS certificate is a digital certificate that complies with the X.509 standard and is presented when using the TLS cryptographic protocol. In turn, X.509 is a general standard that describes the structure of a certificate.
The structure of a certificate does not specify a specific encryption algorithm for signing a certificate, nor does it specify a public key algorithm. That is, these algorithms can be different.
Differences in TLS 1.3
The latest version of the TLS 1.3 protocol is described in RFC 8446 specifications, adopted in August 2018. They are based on the old TLS 1.2 standard, but with a number of important improvements that provide stronger encryption.
The main innovations of TLS 1.3 in terms of cryptography are:
- Separating key agreement and authentication algorithms from cipher suites
- Abandoning weak elliptic curves
- Deprecation of MD5 and SHA-224 hash functions
- Mandatory requirement for digital signatures even when using the previous configuration
- Integration of HKDF Key Derivation Function into Diffie-Hellman Key Exchange Proposal Stage
- Support for single-packet handshakes, i.e. one round-trip (1-RTT) and initial support for 0-RTT
- Perfect Forward Secrecy (PFS) is enforced by using ephemeral keys during (EC)DH key agreement. Perfect Forward Secrecy ensures that session keys derived from a set of long-term keys are not compromised if one of the long-term keys is compromised. That is, an attacker could extract a key from a server, but still not be able to decrypt user sessions.
- Removed many insecure or deprecated features, including unnecessary compression, renegotiation, non- AEAD ciphers , non-PFS key exchange (including static RSA and DH key exchanges), custom DHE groups, elliptic curve point format negotiation, cipher suite change protocol, UNIX time for the Hello message.
- Avoid SSL or RC4 negotiation for backward compatibility
- Session Hash Integration
- Adding ChaCha20 stream cipher with Poly1305 message authentication code
- Adding digital signature algorithms Ed25519 and Ed448
- Adding x25519 and x448 key exchange protocols
- Support for sending multiple OCSP responses. This is a protocol for obtaining the revocation status of an X.509 digital certificate.
- Encrypt all handshake messages after ServerHello
As we can see, the changes in the TLS 1.3 standard strengthen cryptographic protection at all stages, including digital signatures. In particular, two new digital signature schemes, Ed25519 and Ed448, are introduced, both based on the ErDSA standard. The first uses the SHA-512 (SHA-2) and Curve25519 ciphers, and the second uses the SHAKE256 and Curve448 ciphers, according to the new RFC 8032 standard.
It is characteristic that most new standards of modern cryptography are built on Edwards elliptic curves. For example, according to the EdDSA digital signature standard, a public key is essentially a point on a curve, and a signature is a point + an integer. Generating a private key involves choosing a unique elliptic curve and a number of mathematical operations on it.
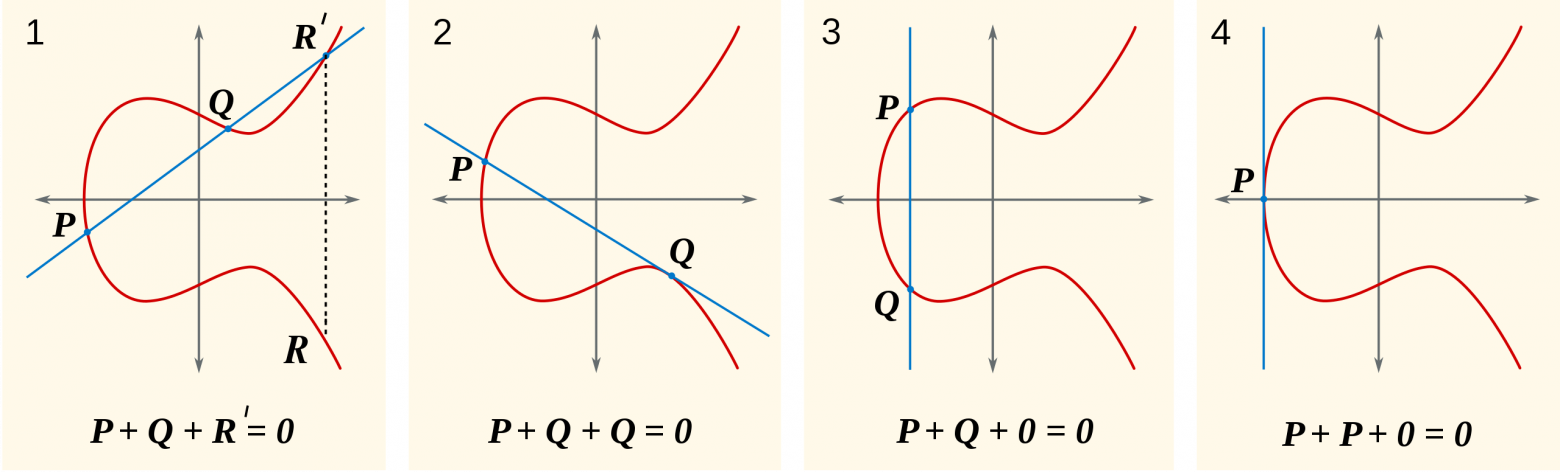
The ErDSA scheme was first published in 2011, but has since been recognized as the most secure elliptic curve algorithm for generating private keys and digital signatures.
Overall, the adoption of the TLS 1.3 standard was a major step toward strengthening all cryptographic primitives used in Internet traffic encryption, including generating digital signatures (certificates).
Thus, TLS certificates can indeed vary in cryptographic strength, depending on which cryptographic algorithms are used to generate the public and private keys and the digital signature, i.e. the certificate itself.
In September 2022, GlobalSign was awarded the 2022 Global Competitive Strategy Leadership Award by Frost & Sullivan for “implementing a broad range of public key infrastructure (PKI) security and digital identity management technologies”.
GlobalSign is the oldest CA in operation, with 25 years in business. According to Frost & Sullivan, it ranks fourth in terms of the number of TLS certificates issued (8.9% share in 2021). On average, the company issued two million certificates per month last year.
GlobalSign provides a variety of PKI products and services, such as PKI management platform, cloud-based Digital Signing Service, Auto Enrollment Gateway, which automates the issuance and maintenance of certificates of all types, including smart card login, digital signatures in Microsoft Office documents, code signing, SSL /TLS, user authentication, device authentication, mobile authentication, etc.
Source
