Man
Professional
- Messages
- 3,222
- Reaction score
- 1,215
- Points
- 113
In the previous article, it was mentioned that modern IoT device manufacturers implement the PKI system directly at the factory. That is, right on the conveyor. Each device receives a unique ID and certificate, which is used to identify and authenticate this specific device throughout its entire life cycle.
How does this happen, in short?
Let's look at the situation using Carnegie Technologies as an example. This system integrator is implementing the Longview platform to manage LoRaWAN devices for customers from various industries: construction, oil and gas, real estate developers, smart cities, etc. Carnegie places orders for production with EMS, a company that specializes in the manufacture of sensors and gateways.
The Longview security system includes three levels:
Certificates are needed to protect devices throughout their entire lifecycle, from manufacturing and deployment to long-term use and proper replacement at the end of their life.
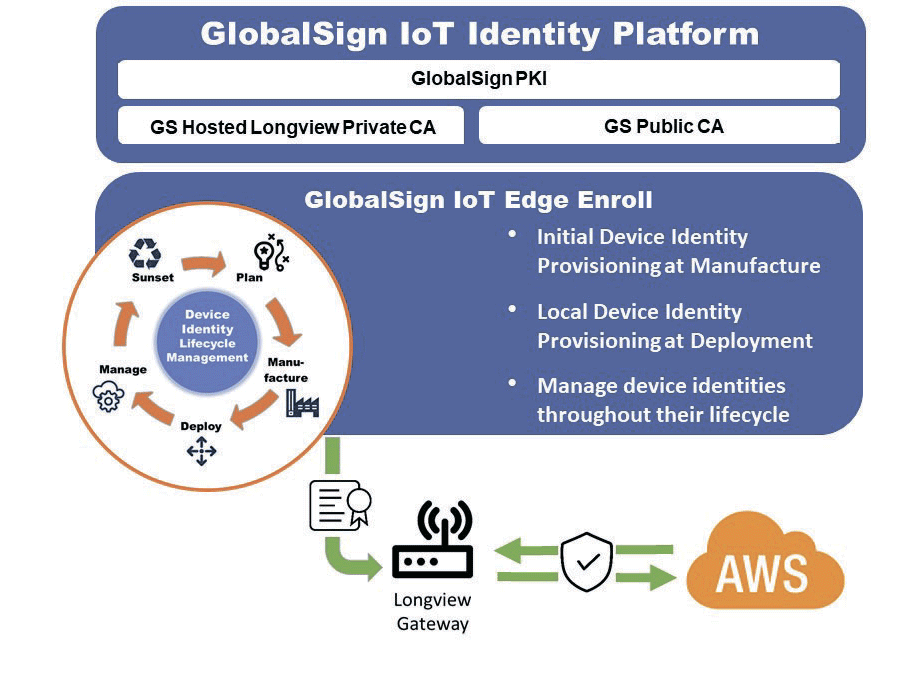
For this particular customer, GlobalSign installed a private CA, Longview Private CA, which issues IDevID certificates (also known as “birth certificates”) for each gateway manufactured by EMS.
Local Device Identity (LDevID) certificates are also issued during the deployment phase of the gateways and are subsequently renewed as needed.
Longview and IoT Identity Platform
Integration As shown in the diagram, the private CA is integrated into the IoT Edge Enroll platform, while also leveraging AWS resources.
As we discussed in the previous article, IoT Identity supports a number of operations throughout the lifecycle of devices, including certificate and key management, token issuance, and secure code signing.
If the platform is installed directly by the device manufacturer, then the IoT Identity system is also implemented straight from the assembly line.
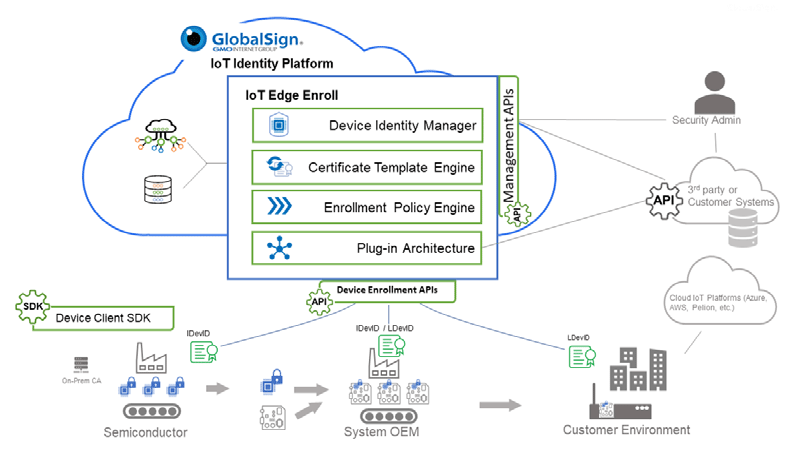
The scheme may look like this:

IoT Edge Enroll is a first-of-its-kind Registration Authority as a Service (RaaS) for identifying and authenticating certificate applicants.
Edge Enroll speeds up RA setup and operation using a set of pre-built workflows. These are policy templates, certificate profiles, and standard enrollment methods that fit typical IoT use cases while still leaving room for additional customization. For unique use cases, PKI experts offer professional RA configuration services using modular plugins.
Connecting enrollment servers via the EST API speeds up integration.
Who uses Edge Enroll:
Recently, the analytical company ABI Research published an independent analysis of IoT Identity platforms .
The rating is based on the most relevant aspects of IoT implementation, including security, identity management, network deployment, partner ecosystem size and intelligent automated services. The
report included eight certification authorities (CA). The companies were divided into three groups:
The authors of the report note that market leaders offer not only a standard ecosystem, but also specific services focused on specific IoT applications. Here are additional options for digital certificates (except X.509), non-standard management methods taking into account bandwidth restrictions and specific connection requirements. As a result, users get the opportunity to configure their IoT Identity system themselves.
As we can see, IoT Identity systems are in demand by chip manufacturers, device vendors, and system integrators. The device registration center as a service (RaaS) is quite accessible and easy to manage.
How does this happen, in short?
Let's look at the situation using Carnegie Technologies as an example. This system integrator is implementing the Longview platform to manage LoRaWAN devices for customers from various industries: construction, oil and gas, real estate developers, smart cities, etc. Carnegie places orders for production with EMS, a company that specializes in the manufacture of sensors and gateways.
The Longview security system includes three levels:
- Native 128-bit LoRaWAN encryption
- SRAM PUF (Physical Unclonable Function) — generation of a key and unique identifiers of devices. The Intrinsic ID system is used. Due to the smallest anomalies in the production of microcircuits, each chip is physically slightly different from the others. This allows the PUF system to use a “physical RNG” and some analogue of a digital fingerprint to uniquely identify each sensor.
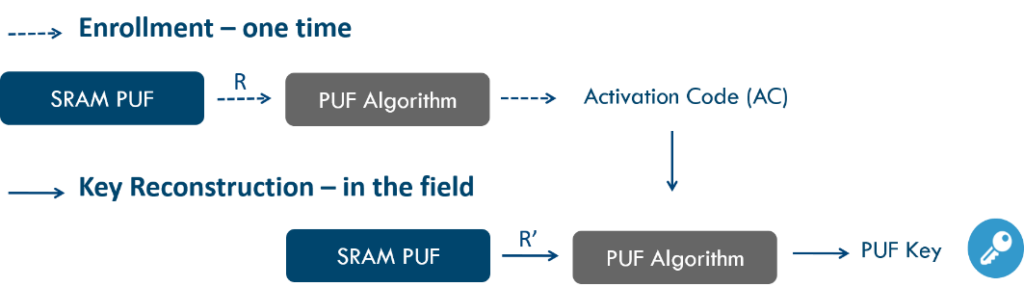
No special hardware devices are required for PUF operation. All functions for creating a key storage or obtaining several keys can be implemented as hardware integrated circuits or in software. The only necessary “hardware” is the unique physical structure of the PUF itself. Thus, on any device where PUF algorithms have access to (uninitialized) SRAM memory, the SRAM PUF system can be implemented. This distinguishes SRAM PUF from other methods of generating unique hardware IDs.

According to some embedded systems experts, this is the only type of PUF currently in existence that can be implemented in hardware by simply loading software onto the device.
- CA for signing certificates
Certificates are needed to protect devices throughout their entire lifecycle, from manufacturing and deployment to long-term use and proper replacement at the end of their life.
For this particular customer, GlobalSign installed a private CA, Longview Private CA, which issues IDevID certificates (also known as “birth certificates”) for each gateway manufactured by EMS.
Local Device Identity (LDevID) certificates are also issued during the deployment phase of the gateways and are subsequently renewed as needed.

Longview and IoT Identity Platform
Integration As shown in the diagram, the private CA is integrated into the IoT Edge Enroll platform, while also leveraging AWS resources.
Implementation on the conveyor belt
As we discussed in the previous article, IoT Identity supports a number of operations throughout the lifecycle of devices, including certificate and key management, token issuance, and secure code signing.
If the platform is installed directly by the device manufacturer, then the IoT Identity system is also implemented straight from the assembly line.

The scheme may look like this:
- Production CA
This certification authority (CA, as in the diagram) signs keys on endpoints. The server generates unique public/private key pairs for endpoints and sends batches of CSR signing requests. The CA returns signed endpoint certificates, which are distributed to all production locations.
- Firmware signing CA
This CA creates a firmware signing certificate. This is another element in the trust hierarchy, but it is located in a secure cloud and is accessed very rarely and only by authorized persons.
- Code Verification CA
This CA issues certificates for individual devices that potentially interact with millions of endpoints. A unique key pair is generated for each device, the public key is sent to the CA for signing, and certificates are dynamically distributed to endpoints to verify signed critical commands (for example, proprietary vendor network interfaces may be used).
Registration Center as a Cloud Service

IoT Edge Enroll is a first-of-its-kind Registration Authority as a Service (RaaS) for identifying and authenticating certificate applicants.
Edge Enroll speeds up RA setup and operation using a set of pre-built workflows. These are policy templates, certificate profiles, and standard enrollment methods that fit typical IoT use cases while still leaving room for additional customization. For unique use cases, PKI experts offer professional RA configuration services using modular plugins.
Connecting enrollment servers via the EST API speeds up integration.
Functions
- Device Lifecycle Manager: Policy Manager, User Manager, CA Account Manager, Identifier Registry, Audit. Device Lifecycle Manager allows authorized administrators to view registered or whitelisted devices and their statuses via the device store. It provides access to the certificate store to manage certificate expirations, renewals, whitelists, and re-registrations. Administrators can even view the history of when and how a device was registered and managed.
- Direct integration with GlobalSign CA for production certificates: key generation, policy enforcement, enrollment servers, CSR generation, certificate templates, pre-configured workflows
Who uses Edge Enroll:
- Device manufacturers and operators: to generate device IDs and digital certificates, to reduce operating costs for device registration, and to simplify the entire system for registering and managing devices
- Chip makers: For them, smart chips with embedded ID create a competitive advantage to ensure supply chain security from top to bottom
- IoT system developers and organizations wishing to manage unique device IDs throughout their lifecycle
Platform Rating
Recently, the analytical company ABI Research published an independent analysis of IoT Identity platforms .
The rating is based on the most relevant aspects of IoT implementation, including security, identity management, network deployment, partner ecosystem size and intelligent automated services. The
report included eight certification authorities (CA). The companies were divided into three groups:
- Market leaders: Device Authority, Entrust, Digicert, GlobalSign
- Mainstream: HID Global, Sectigo
- Followers: WISeKey, Nexus
The authors of the report note that market leaders offer not only a standard ecosystem, but also specific services focused on specific IoT applications. Here are additional options for digital certificates (except X.509), non-standard management methods taking into account bandwidth restrictions and specific connection requirements. As a result, users get the opportunity to configure their IoT Identity system themselves.
As we can see, IoT Identity systems are in demand by chip manufacturers, device vendors, and system integrators. The device registration center as a service (RaaS) is quite accessible and easy to manage.
