CarderPlanet
Professional
- Messages
- 2,549
- Reaction score
- 724
- Points
- 113
Analysts believe that the LostTrust cryptographer is just a renamed MetaEncryptor. This is evidenced by the similarity of cryptographers and onion sites for publishing a list of victims who refused to pay the ransom.
Malware LostTrust appeared on the Internet in March of this year, but gained wide popularity only last month, when it began using its own site of leaks in the Tor network. Windows networks are infected; whether the malware is able to encrypt data on Linux machines is still unclear.
The launch of MetaEncryptor, apparently, took place in August 2022. During the year, it managed to hit 12 organizations; the list of victims on its leak site has not been updated for the past two months.
BleepingComputer's analysis of both malware types showed that the encryptors are almost identical and use SFile2 code (using SHA-512, AES-256, and RSA-2048). The relationship of successors is indicated by the METAENCRYPTING string displayed in the console when LostTrust is executed.
In order to cover as many target files as possible, the rookie forcibly terminates Windows services that interfere with it. After encryption, the extension is added to the file name .losttrustencoded.
In the note created by the malware, it is said that its operators thus draw attention to gaps in the IT infrastructure, which should not be spared funds to protect.
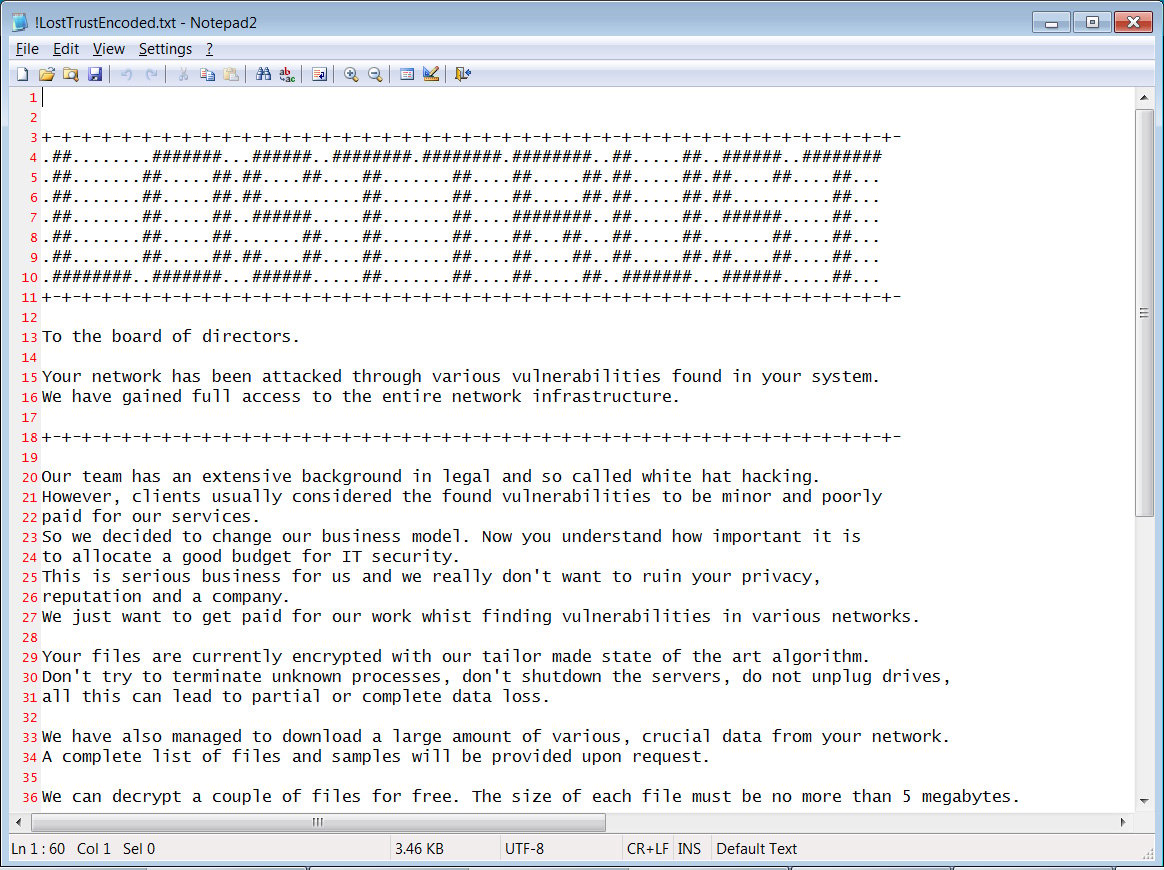
Here you can also find a personal link to onion, a site for negotiating a buyout. This platform, according to experts, is almost empty and provides only chat functions. According to reports, victims are required from $100 thousand to millions for the decryptor.
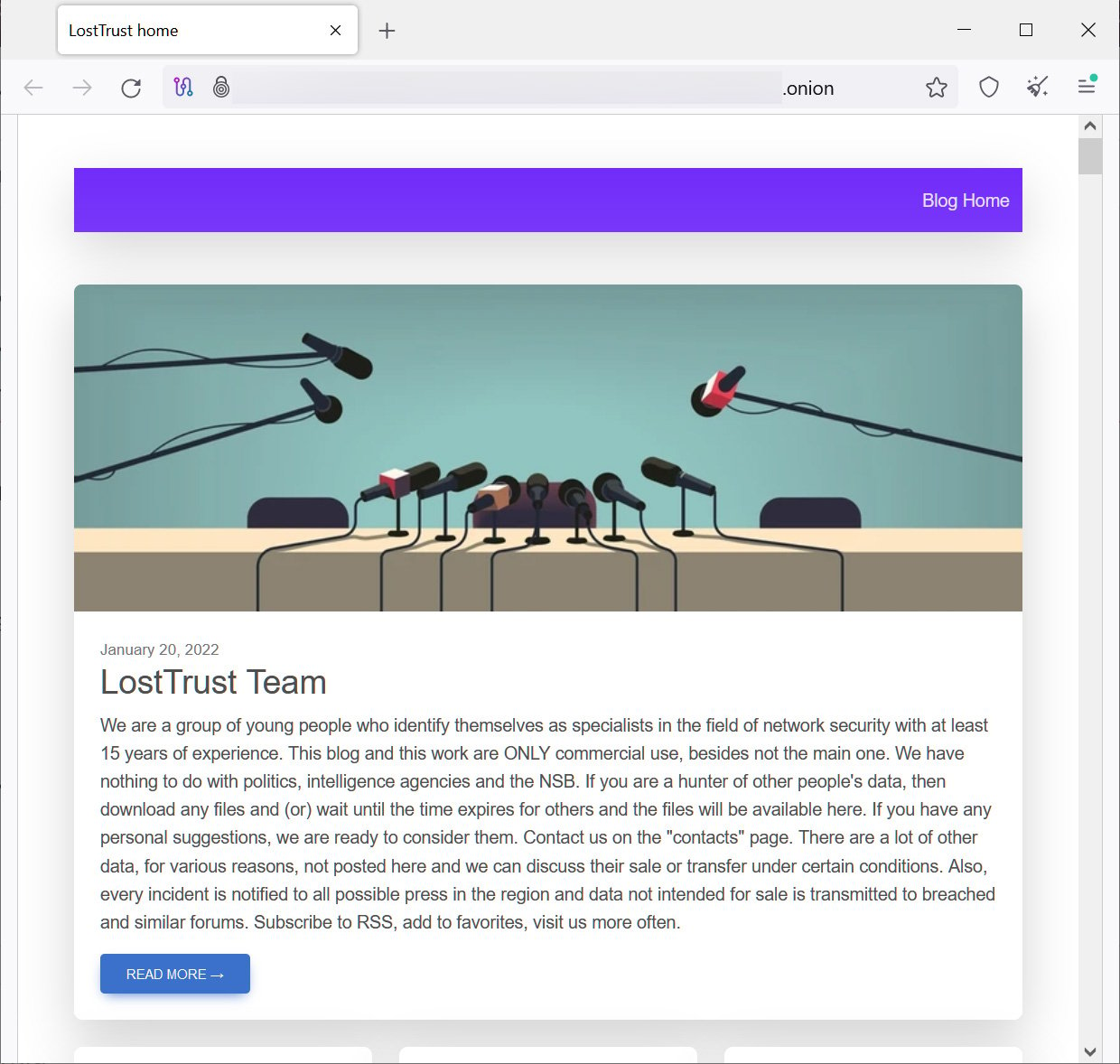
The LostTrust leak site uses the MetaEncryptor template. Currently, it has 53 victims of infection. Information stolen from defaulters ends up in the public; it is not known whether it is deleted after receiving a ransom, and there are no reviews about the paid decryptor either.
Malware LostTrust appeared on the Internet in March of this year, but gained wide popularity only last month, when it began using its own site of leaks in the Tor network. Windows networks are infected; whether the malware is able to encrypt data on Linux machines is still unclear.
The launch of MetaEncryptor, apparently, took place in August 2022. During the year, it managed to hit 12 organizations; the list of victims on its leak site has not been updated for the past two months.
BleepingComputer's analysis of both malware types showed that the encryptors are almost identical and use SFile2 code (using SHA-512, AES-256, and RSA-2048). The relationship of successors is indicated by the METAENCRYPTING string displayed in the console when LostTrust is executed.
In order to cover as many target files as possible, the rookie forcibly terminates Windows services that interfere with it. After encryption, the extension is added to the file name .losttrustencoded.
In the note created by the malware, it is said that its operators thus draw attention to gaps in the IT infrastructure, which should not be spared funds to protect.

Here you can also find a personal link to onion, a site for negotiating a buyout. This platform, according to experts, is almost empty and provides only chat functions. According to reports, victims are required from $100 thousand to millions for the decryptor.
The LostTrust leak site uses the MetaEncryptor template. Currently, it has 53 victims of infection. Information stolen from defaulters ends up in the public; it is not known whether it is deleted after receiving a ransom, and there are no reviews about the paid decryptor either.


