CarderPlanet
Professional
- Messages
- 2,549
- Reaction score
- 724
- Points
- 113
Is it the evolution of a threat or a cry of despair?
In recent months, cyberspace has faced a new threat in the form of the LostTrust cryptographer, which is believed to be a rebranding of the previously known MetaEncryptor. This conclusion was made based on the similarity of data leak sites and cryptographers used by both groups.
The main activity of LostTrust was attacks on organizations that began in March 2023. However, it wasn't until September, when the gang began using the data leak site to publicly blackmail its victims, that the cryptographer gained widespread recognition. At the moment, the data leak site LostTrust lists 53 victims worldwide, some of whom have already experienced a data leak due to refusing to pay a ransom.
MetaEncryptor was launched in August 2022 and collected 12 victims on its data leak site until July 2023, after which new victims stopped being added to the site. In September, a new data leak site for the LostTrust group was launched.
Cybersecurity researcher Stefano Favarato noticed that the new site uses exactly the same template and bio as the data leak site MetaEncryptor. Both sites contain a description stating that the authors are a group of young network security professionals with at least 15 years of experience.
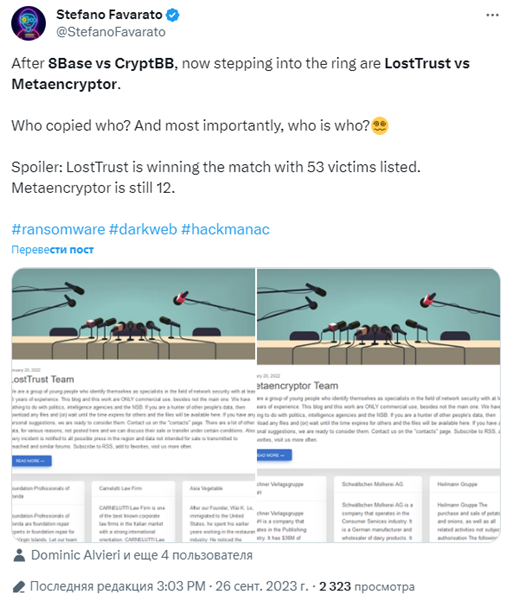
Favarato's tweet about the similarity between LostTrust and MetaEncryptor sites
Analysts at BleepingComputer found that the LostTrust and MetaEncryptor cryptographers are almost identical, with minor changes to ransom notes, embedded public keys, ransom note names, and encrypted file extensions. In addition, a cybersecurity researcher from MalwareHunterTeam reported that LostTrust and MetaEncryptor are based on the SFile2 cryptographer – many matches were found in the code of the LostTrust and sFile cryptographers.
In addition, a sample analysis of the LostTrust cryptographer showed that it can be run with two additional command-line arguments to encrypt a specific path or network resources. During execution, LostTrust disables and stops many Windows services to ensure that all files can be encrypted, including services related to Firebird, MSSQL, SQL, Exchange, and others.
Unlike other groups, the LostTrust hackers present themselves in their ransom note as former white hackers who decided to engage in cybercrime because of poor payment for their services. The buyout message contains information about what happened to the company's files and a unique link to the site of negotiations with the group via the Tor network. The amounts of ransoms required range from $100,000 to millions of dollars.
The data leak site is used to blackmail victims by threatening to divulge stolen data if the ransom is not paid. At the moment, it is not known whether paying the ransom will lead to the deletion of data and the provision of a working decryptor.
In recent months, cyberspace has faced a new threat in the form of the LostTrust cryptographer, which is believed to be a rebranding of the previously known MetaEncryptor. This conclusion was made based on the similarity of data leak sites and cryptographers used by both groups.
The main activity of LostTrust was attacks on organizations that began in March 2023. However, it wasn't until September, when the gang began using the data leak site to publicly blackmail its victims, that the cryptographer gained widespread recognition. At the moment, the data leak site LostTrust lists 53 victims worldwide, some of whom have already experienced a data leak due to refusing to pay a ransom.
MetaEncryptor was launched in August 2022 and collected 12 victims on its data leak site until July 2023, after which new victims stopped being added to the site. In September, a new data leak site for the LostTrust group was launched.
Cybersecurity researcher Stefano Favarato noticed that the new site uses exactly the same template and bio as the data leak site MetaEncryptor. Both sites contain a description stating that the authors are a group of young network security professionals with at least 15 years of experience.

Favarato's tweet about the similarity between LostTrust and MetaEncryptor sites
Analysts at BleepingComputer found that the LostTrust and MetaEncryptor cryptographers are almost identical, with minor changes to ransom notes, embedded public keys, ransom note names, and encrypted file extensions. In addition, a cybersecurity researcher from MalwareHunterTeam reported that LostTrust and MetaEncryptor are based on the SFile2 cryptographer – many matches were found in the code of the LostTrust and sFile cryptographers.
In addition, a sample analysis of the LostTrust cryptographer showed that it can be run with two additional command-line arguments to encrypt a specific path or network resources. During execution, LostTrust disables and stops many Windows services to ensure that all files can be encrypted, including services related to Firebird, MSSQL, SQL, Exchange, and others.
Unlike other groups, the LostTrust hackers present themselves in their ransom note as former white hackers who decided to engage in cybercrime because of poor payment for their services. The buyout message contains information about what happened to the company's files and a unique link to the site of negotiations with the group via the Tor network. The amounts of ransoms required range from $100,000 to millions of dollars.
The data leak site is used to blackmail victims by threatening to divulge stolen data if the ransom is not paid. At the moment, it is not known whether paying the ransom will lead to the deletion of data and the provision of a working decryptor.

