Tomcat
Professional
- Messages
- 2,689
- Reaction score
- 963
- Points
- 113
Although the most popular malware tends to bypass MacOS, there are many Trojans for this operating system. To protect your computer from the most common types of malware, we will look at two free utilities that can automatically detect ransomware that encrypt your files and track unauthorized access to the microphone and camera.
These utilities, capable of detecting even previously unknown malware, were developed by Patrick Wardle, a former NSA hacker. We'll look at the OverSight and RansomWhere applications, which, instead of scanning code for known signatures, analyze behavioral characteristics. An alert occurs at the moment when a suspicious program tries to access the camera / microphone or encrypt files.
Another type of malware allows you to gain access to the victim's camera and microphone for remote wiretapping and tracking. When the camera is working, the corresponding indicator is turned on by default on computers with MacOS, but in the case of a microphone, this indicator is not. Accordingly, in order to avoid detection, malware is mainly sharpened by wiretapping through a microphone.
Since some legitimate application updates (for example, from Adobe) can also initiate such activity, intelligent algorithms running in the background reduce the percentage of negative positives to a minimum, trying to distinguish between encryption and compression. Once RansomWhere detects fast encryption of more than three files, you decide whether to continue or not. If you decide to continue the process, the whitelist is replenished, and in the future the percentage of false positives will decrease.
In addition to real-time monitoring, OverSight also logs which programs and when accessed these devices, and whether permission was granted from you. Logs allow you to track down suspicious activity in the past if you are concerned that someone with physical access to your computer could hypothetically install applications to access your microphone.
Let's move on to installing and configuring these utilities.
Figure 1: Section for downloading RansomWhere and OverSight
Step 1. Download RansomWhere
First, go to the section with RansomWhere, where there is a lot of additional useful information. If you would like to learn more about development and other aspects of RansomWhere, you can read Patrick's article on creating this application.
Click on the "Download" link under the logo in the form of a key, and after downloading, unpack and run the installer.
Step 2. Installing and configuring RansomWhere
It is not difficult to install RansomWhere. After starting the installer, enter the password for granting rights to install the application. Then click on the "Install" button to start the installation.
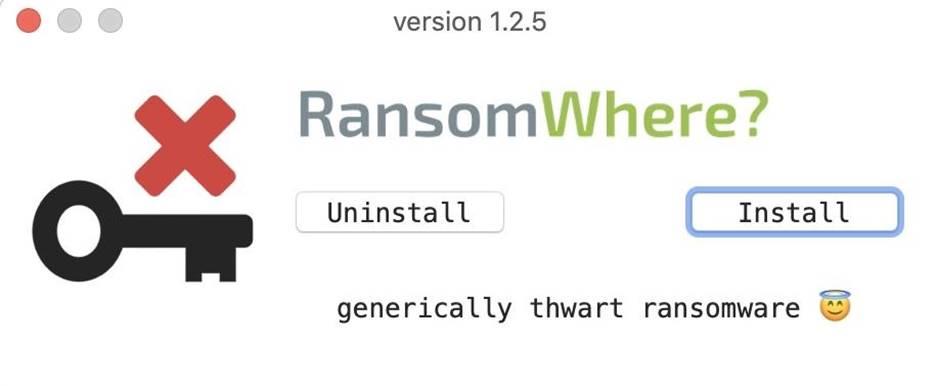
Figure 2: Installing RansomWhere
The installation ends when a message appears stating that the process has completed successfully. Now you can test the RansomWhere application or move on to installing OverSight.
Step 3 (optional). Testing Ransomware with Python
If you want to test RansomWhere, you can run an application that functions as a ransomware. I wrote a Python program to encrypt any PNG file in the same directory.
Open the terminal and enter the commands to create in the home directory "GenEncrypt".
Then copy the code below into the window and after completion of creation press ctrl + x and then enter "Y" after finishing writing to the file.
If you enter the ls command, the file "RealBadFile.py" should appear in the list.
This code will encrypt all PNG files in the same directory using the AES algorithm! We put at least three files in the folder (for example, you can take screenshots), and then enter the command below in the terminal:
Considering that the script encrypted 3 files, a warning should appear, as shown in the figure below. On macOS Catalina, you probably need to enable alerts so that RansomWhere can display popup messages.
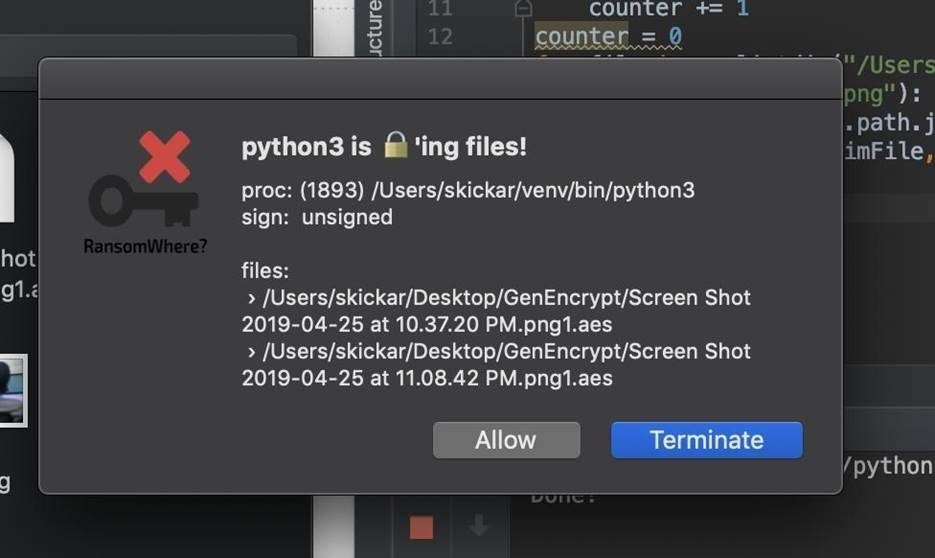
Figure 3: Warning about a suspicious program that encrypts files
To suspend encryption, you need to click on the "Terminate" button.
Step 4. Downloading OverSight
Go to the section on Oversight, where there is a lot of useful information, and a link to download.
To download the installer, click on "Download" under the icon in the upper left corner, then double-click on the file to unpack and then double-click on the executable file again to start the installation. Enter the password for granting installation rights and click on the "Install" button.

Figure 4: Installing OverSight
After the installation is complete, launch the program that needs access to the camera, such as Photo Booth. A warning should appear allowing you to decide whether to allow access to the device or not. On macOS Catalina, you must enable alerts for the OverSightHelper for alerts to appear.
Step 5. Configuring and blocking unwanted requests
To configure OverSight, click on the umbrella-shaped icon located on the taskbar, and then go to settings. The current status of the microphone and camera is also displayed here.
In the settings, you can specify whether OverSight should be launched immediately after logging into the system, whether it is necessary to record activity in the log, or activate some other functions.
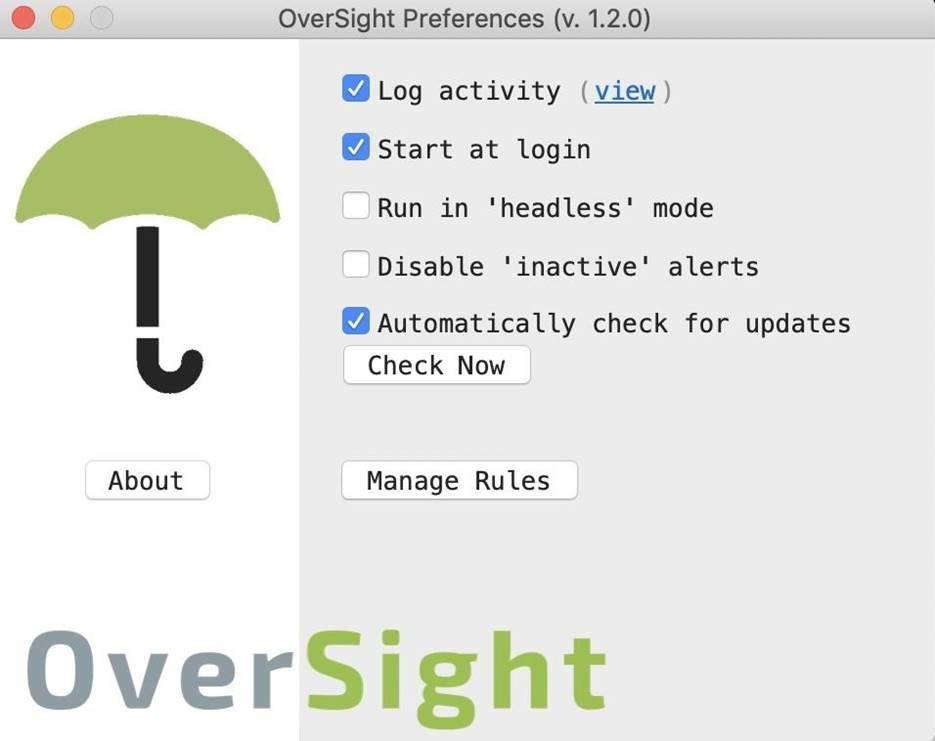
Figure 5: Section with OverSight settings
If you click on the "Manage Rules" button, a whitelist of applications will appear. This list contains programs that are allowed access to the microphone and camera. At any time, you can reconsider your decision by clicking on the cross to the right of the corresponding application.
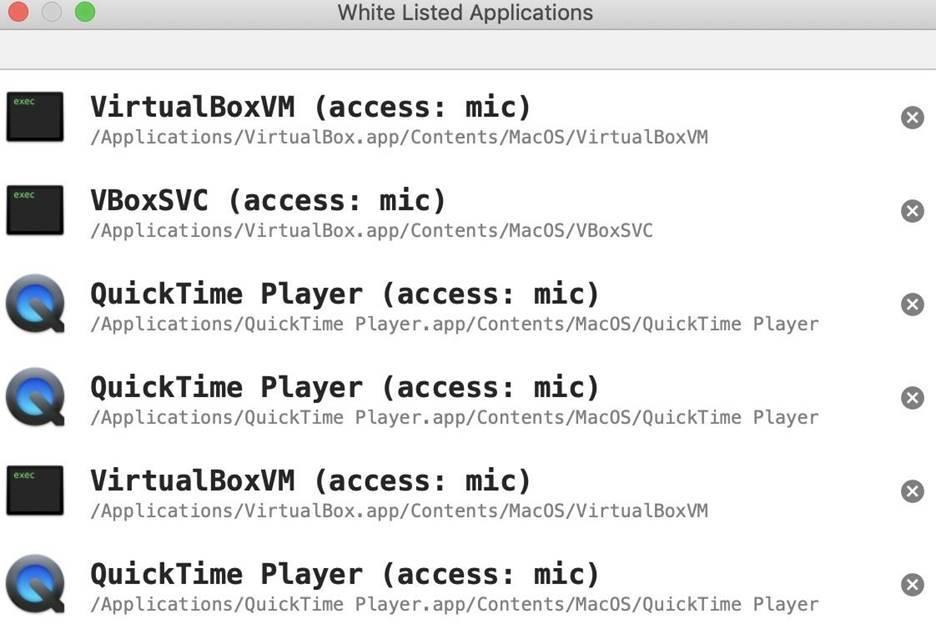
Figure 6: Whitelist of Applications Allowed to Access Devices
Now all the settings needed to track access to devices in real time by any program should be done.
Step 6. Viewing the logs for events related to device activation
In addition to real-time tracking, you can see which programs had access to the microphone or camera. By clicking on the link (view) located after "Log Activity" in the settings section, you will see a complete history of access to both devices.
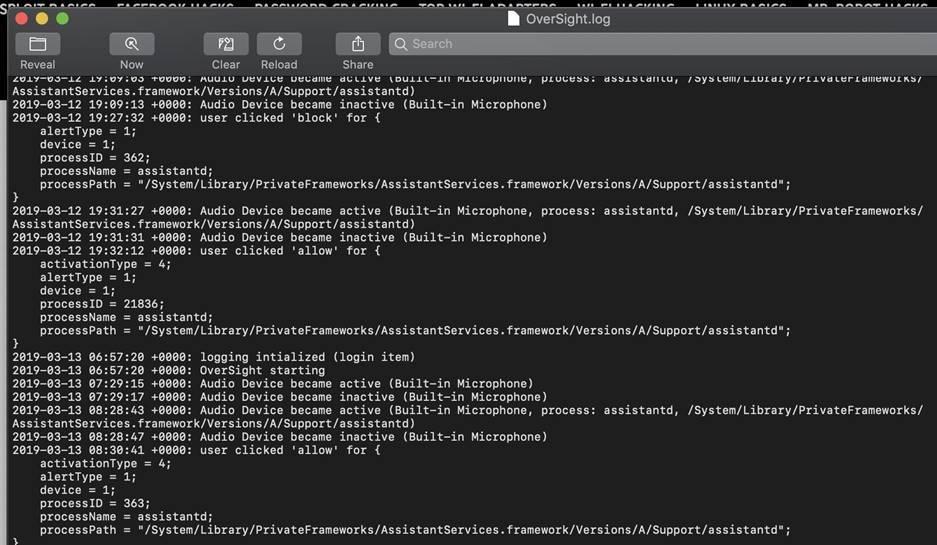
Figure 7: Application access log to devices
With the help of this information, we can figure out in detail which programs and when were connected to the camera and microphone.
I hope you enjoyed this guide and now you can improve security on your macOS system.
(c) securitylab.ru
These utilities, capable of detecting even previously unknown malware, were developed by Patrick Wardle, a former NSA hacker. We'll look at the OverSight and RansomWhere applications, which, instead of scanning code for known signatures, analyze behavioral characteristics. An alert occurs at the moment when a suspicious program tries to access the camera / microphone or encrypt files.
Threats for MacOS
For the typical macOS user, some security threats are more serious than others. Ransomware is a special type of malware designed to make the victim pay to decrypt files previously encrypted on a compromised system. To recover data, the user must pay the attacker for the key. However, even if you pay, there is no guarantee that you will receive the key.Another type of malware allows you to gain access to the victim's camera and microphone for remote wiretapping and tracking. When the camera is working, the corresponding indicator is turned on by default on computers with MacOS, but in the case of a microphone, this indicator is not. Accordingly, in order to avoid detection, malware is mainly sharpened by wiretapping through a microphone.
RansomWhere utility
RansomWhere is a free application that analyzes destructive behavior of processes on your computer, such as fast encryption of many files. When a process of this kind is detected, RansomWhere stops encryption and issues a warning, allowing you to decide whether to continue or not. In the event that malware tries to encrypt the hard drive, you will be warned at the earliest possible stage and you can complete the process.Since some legitimate application updates (for example, from Adobe) can also initiate such activity, intelligent algorithms running in the background reduce the percentage of negative positives to a minimum, trying to distinguish between encryption and compression. Once RansomWhere detects fast encryption of more than three files, you decide whether to continue or not. If you decide to continue the process, the whitelist is replenished, and in the future the percentage of false positives will decrease.
Wiretapping tracking with OverSight
The OverSight utility is for those who want to keep track of which apps are trying to access their webcam or microphone. OverSight allows you to monitor these devices and alert you to any breaches of your privacy. Microphone access becomes more transparent, just like with the camera, and it becomes easy to notice and disable programs trying to access the device. As a general rule of thumb, if you find that random applications are requesting access to your microphone and camera, you probably have a security problem with your computer and need to do a more thorough scrutiny.In addition to real-time monitoring, OverSight also logs which programs and when accessed these devices, and whether permission was granted from you. Logs allow you to track down suspicious activity in the past if you are concerned that someone with physical access to your computer could hypothetically install applications to access your microphone.
Let's move on to installing and configuring these utilities.
What is needed
To install the aforementioned utilities, which can be found in the corresponding section of the objective-see.com website, you will need a MacOS computer, a browser and an internet connection.
Figure 1: Section for downloading RansomWhere and OverSight
Step 1. Download RansomWhere
First, go to the section with RansomWhere, where there is a lot of additional useful information. If you would like to learn more about development and other aspects of RansomWhere, you can read Patrick's article on creating this application.
Click on the "Download" link under the logo in the form of a key, and after downloading, unpack and run the installer.
Step 2. Installing and configuring RansomWhere
It is not difficult to install RansomWhere. After starting the installer, enter the password for granting rights to install the application. Then click on the "Install" button to start the installation.

Figure 2: Installing RansomWhere
The installation ends when a message appears stating that the process has completed successfully. Now you can test the RansomWhere application or move on to installing OverSight.
Step 3 (optional). Testing Ransomware with Python
If you want to test RansomWhere, you can run an application that functions as a ransomware. I wrote a Python program to encrypt any PNG file in the same directory.
Open the terminal and enter the commands to create in the home directory "GenEncrypt".
Code:
cdThen copy the code below into the window and after completion of creation press ctrl + x and then enter "Y" after finishing writing to the file.
Code:
import pyAesCryptIf you enter the ls command, the file "RealBadFile.py" should appear in the list.
This code will encrypt all PNG files in the same directory using the AES algorithm! We put at least three files in the folder (for example, you can take screenshots), and then enter the command below in the terminal:
Code:
pip install pyAesCryptConsidering that the script encrypted 3 files, a warning should appear, as shown in the figure below. On macOS Catalina, you probably need to enable alerts so that RansomWhere can display popup messages.

Figure 3: Warning about a suspicious program that encrypts files
To suspend encryption, you need to click on the "Terminate" button.
Step 4. Downloading OverSight
Go to the section on Oversight, where there is a lot of useful information, and a link to download.
To download the installer, click on "Download" under the icon in the upper left corner, then double-click on the file to unpack and then double-click on the executable file again to start the installation. Enter the password for granting installation rights and click on the "Install" button.

Figure 4: Installing OverSight
After the installation is complete, launch the program that needs access to the camera, such as Photo Booth. A warning should appear allowing you to decide whether to allow access to the device or not. On macOS Catalina, you must enable alerts for the OverSightHelper for alerts to appear.
Step 5. Configuring and blocking unwanted requests
To configure OverSight, click on the umbrella-shaped icon located on the taskbar, and then go to settings. The current status of the microphone and camera is also displayed here.
In the settings, you can specify whether OverSight should be launched immediately after logging into the system, whether it is necessary to record activity in the log, or activate some other functions.

Figure 5: Section with OverSight settings
If you click on the "Manage Rules" button, a whitelist of applications will appear. This list contains programs that are allowed access to the microphone and camera. At any time, you can reconsider your decision by clicking on the cross to the right of the corresponding application.

Figure 6: Whitelist of Applications Allowed to Access Devices
Now all the settings needed to track access to devices in real time by any program should be done.
Step 6. Viewing the logs for events related to device activation
In addition to real-time tracking, you can see which programs had access to the microphone or camera. By clicking on the link (view) located after "Log Activity" in the settings section, you will see a complete history of access to both devices.

Figure 7: Application access log to devices
With the help of this information, we can figure out in detail which programs and when were connected to the camera and microphone.
Conclusion
While it can be difficult for the average user to deal with malware on MacOS, using the applications discussed above will make it easy to track down and stop malicious activity on the system. Thanks to OverSight and RansomWhere, we can detect and prevent suspicious behavior before more serious consequences ensue. We are even talking about previously unknown malware.I hope you enjoyed this guide and now you can improve security on your macOS system.
(c) securitylab.ru
