Father
Professional
- Messages
- 2,601
- Reaction score
- 836
- Points
- 113
Greetings to all!
I think that the vast majority of people sitting here are familiar with such devices for stealing bank card data as skimmers. They were actively fought (sometimes successfully, and sometimes not so much), and they quietly and imperceptibly went down in history to the spread of contactless cards.

Many people have probably heard about special pads of a tricky shape on card readers, designed to protect the device from installing foreign equipment. But it wasn't all about protective plastic parts, there were much more interesting devices, a couple of which fell into my hands.
So, in today's article we will talk about such a little-known type of ATM protection among ordinary people as active anti-skimmers. Along the way, let's try to launch my existing devices and find out how they work. Traditionally, there will be a lot of interesting things.
In the era of magnetic cards, this situation was quite common — you withdraw money from an ATM in the alley, everything goes fine, only then suddenly it turns out that the funds on the card did not happen. In our city, I did not find this method of carding, but in larger and more visited places, such devices were actually installed. Alas, this time the reality was not so different from what was told in thematic publications — a simple pair of overlays on the reader and keyboard made it possible to steal data from everyone who used the ATM. With these things actively fought, putting special plastic devices that do not allow you to install something else. But, as it turned out, everything is not so simple, in fact, there were much more interesting solutions. I don't see any point in talking about the skimmers themselves, almost everything has already been said before me. Today we will talk about how they were protected from them.

The simplest option was the usual plastic pads. Such a thing made it very difficult to install extraneous equipment on the reader. And if it did not make it difficult, then the "mined" ATM was easily visible even to the average person.

But there is a problem — with the help of a flat screwdriver, the plastic thing easily came off (after which you could insert your electronics into it and fasten it to the ATM), the transparency of many of these details did not help much. The solution was simple — to ensure that the integrity of this node is controlled. A loop with a snake track like in a POS terminal, and now when a hole is torn off or poked in this part, the card reader is either turned off or an alarm is triggered.

And finally, the most interesting option is hardware anti-skimmers. These devices can either detect malicious devices or interfere with their operation. We'll talk about them today.
By their principle of operation, they are much more complicated than simple attachments. Such devices were produced by several companies, but the principle of operation is approximately the same.
In general, for some reason, there is little mention of the device and the operation of these pieces, only some unique patented technologies are mentioned without a detailed description of how it works.
Hardware antiskimmers are divided into two categories — those that detect the installation of such devices (after which the ATM is usually blocked) or those that suppress their operation (while the ATM can be safely used). The latter usually have the same functionality as the former, reporting suspicious activity to the bank.
A typical such device consists of an antenna that emits interference that interferes with the operation of the skimmer's magnetic head, volume sensors to monitor the presence of something foreign near the card reader, and limit switches to control card rolling.
It so happened that I got my hands on two such devices, one from the Russian company Answer Pro, the other from the Dutch TMD (not to be confused with the duplicator of intercom keys).

And here is the first device. A small blue box with a screen and two LEDs.

The second part of the TMD is another module that connects to the main unit with a three-wire cable.

The second device is the Russian Cerberus. It looks more modest: there are only connectors on the case and nothing else. However, I managed to find software for the second one, so most of the attention will be paid to it today.
The first in line will be a device from TMD Security.

In the field of ATM protection tools, this is a fairly serious company, which also produces the same legendary coloring cassettes, anti-explosion protection tools and other cool equipment, which also includes the same anti-skimmers.

But let's move on to our device. I don't have any pinout of it, so in order to run it, it had to be disassembled. Inside, everything is expected-a display (8*2, HD44780), a couple of relays, LEDs, a squeaker, a reset button, an RTC battery.

Let's remove the screen. There are three PIC microcontrollers under it at once. Power was found quite quickly — the first and second pins of the rightmost connector.
We apply 24 volts, and the device starts.

But, alas, after initializing the sensors, it gives an error. I don't have the faintest idea how these sensors work (and they are digital here), nor do I have any software to configure them (which is much more serious), so nothing can be done about it.

And here is the filling of a small box. This is the same interference generator. There is another small PIC on the board, as well as the BD6232HFP chip — a powerful H-bridge. In general, it is used as a motor driver, but in this case it controls the coil connected to the second connector on the board. It emits a magnetic field during the operation of the device, which interferes with the operation of the skimmer's magnetic head.
Let's move on to the second device. This time it is a product from a Russian company. Its website still works, so you can immediately download drivers and software.

And here is the inside of the device. The power elements of the power supply circuits of the device, card reader and antenna, the STM32 microcontroller, and the power-off relay are clearly visible. The device connects to the card reader's power cable gap and can disconnect it if necessary. The second power connector is connected to the same antenna that generates interference. There are three more connectors — an end cap, a receiving antenna,and a capacitive sensor. The box is connected to the computer via the CP2102 USB-UART bridge.

This is what the same coil looks like, being installed on an ATM. In appearance, it is very similar to the demagnetization loop that can be found in old televisions and monitors.

Launching it. The relay clicks, and the error LED lights up. A good start.
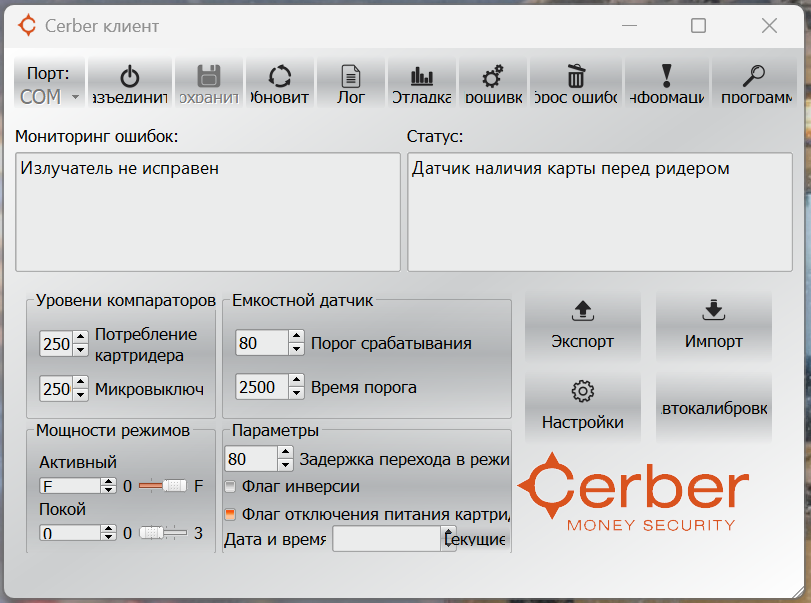
Now it's the software's turn. We start the standard software and see in the list of errors the break of the same induction loop. I don't have a standard coil, so instead I just connected a powerful resistor. The field created by the coil is quite powerful, with its resistance of ten ohms (as stated in the documentation), a current of about four amperes flows in it.

After that, all three LEDs, as expected, turned green.
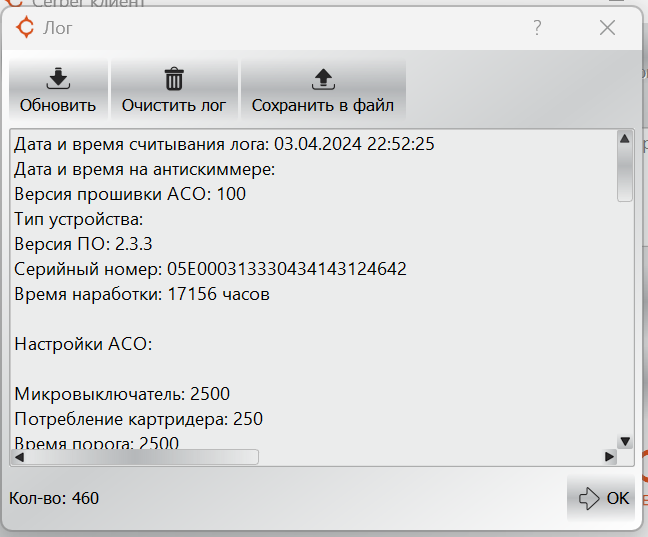
Judging by the log, the last time the device was launched was in 2017.
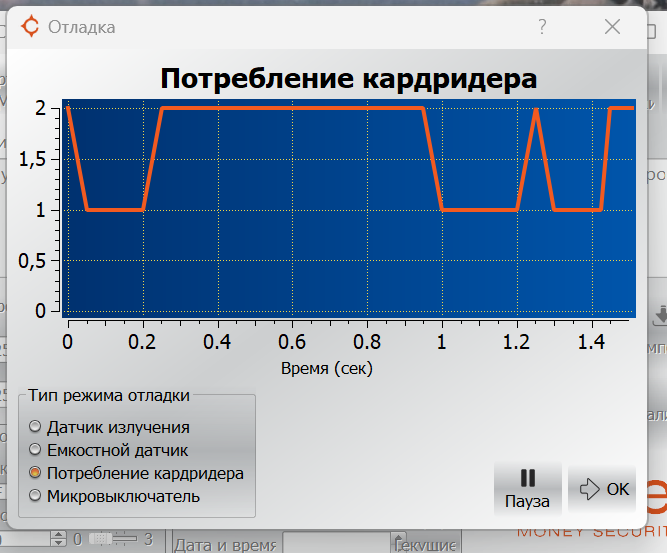
The most interesting point is debugging. Here you can view real-time sensor data. For example, I connected a 36-volt incandescent lamp and a toggle switch to the power connector of the card reader. When it was turned on and off, the values on the chart also changed.
The radiation sensor is just a loop antenna.
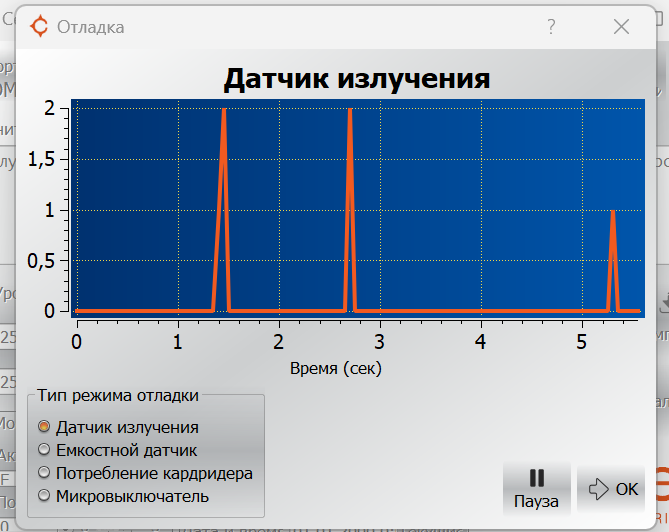
By the way, if you place the emitter next to the control unit, it will begin to respond to its own interference, first peaks will appear, and then the graph will quickly creep up.
With the end cap, obviously, nothing interesting.
The most interesting thing is the capacitive sensor, which is connected to the unit with as many as six wires. The sensor itself, alas, I do not have, and in its absence, the reading does not go…

This is what this part looks like when installed. It allows you to control the presence of something foreign near the slot of the card reader.
Well, let's move on to the most interesting part — an analysis of how it all works.

Here is a typical magnetic card drive from an ATM. Specifically, this one is NCR IMCRW, but in other models (Wincor, Diebold), these pieces are absolutely identical in design.
In fact, I have several such devices, so maybe someday I will tell you more about them.

But now we are only interested in itsmuzzle receiving slot. Here is an example of such a module from the NCR MCRW card reader (not to be confused with the newer IMCRW).

The unit itself came to me burnt out (they tried to start it up and applied 24 V to the 5 V bus), and I disassembled it for the sake of mechanical parts, leaving part of the swallowing mechanism as a memory.

Unlike terminals, where the card slot is not protected by anything, everything is much more interesting here. If you look at this module from below, you can see the so-called pre-reading head. It does not read anything, but only detects that the inserted card contains a magnetic stripe. This is necessary to protect the reader from vandals (stuffing a business card, a simple plastic card, or any other object of a similar size will no longer work) and inattentive users (a card inserted on the wrong side due to the presence of convex letters on it may get stuck or scratch rubber rollers).

And here is the limit switch that works when inserting the card. This is where one of the device's inputs is connected (in parallel with the card reader).

If the limit switch is activated and the head sees the strip, the electromagnet opens the curtain, allowing you to push the card further. It is this moment that is controlled by the antiskimmer. As you know, the most dangerous moment for a map is when it is inserted. This is when you need to turn off the potentially installed skimmer. In normal mode, the coil emits medium-power interference (to potentially eliminate reading before the sensor is triggered, and also to prevent the skimmer from transmitting data over the radio channel, if any). When the card is inserted, the limit switch closes, and the interference turns on at full power, preventing an unauthorized device from reading the card data. Since the head in the skimmer is not shielded in the same way as in an ATM or terminal, the output signal is easily clogged with noise. When the limit switch is released, the interference power drops to a minimum: the card is inside, now the most important thing is not to interfere with its reading. Activity is also monitored by card reader consumption. A drive motor and electromagnets (shutters, swallowing mechanism, smart card reader drive) are installed inside it, which is why the start of its operation leads to a clearly distinguishable current surge.
Also, a relay is installed inside the unit, which allows you to turn off the power to the card reader in an emergency situation. When the capacitive sensor is triggered, the device understands that there is something else next to the reader and can block working with cards, if this is specified in its settings. These trigger thresholds are defined in the same control software.
Despite its effectiveness against very simple skimmers, very often this thing created a lot of problems.
By themselves, skimmers quickly adapted to such devices — their creators learned how to compensate for interference and save dumps on the built-in memory. But those who serve ATMs, these devices drank a lot of blood. The coil caused such powerful interference that the magnetic readout head believed that the card was always there (moreover, the instructions for installing the device on some ATM models explicitly stated to disconnect its connector from the board), which is why the reader was triggered in fact only from the limit switch, which led to its damage from incorrectly or simply crookedly inserted cards. In addition, the installation of sensors on the receiving slot required special care: if the card reader is not aligned with the slot on the door when closing the door (on some models of ATMs with such a design), then the card will no longer be able to leave by itself after insertion. Fortunately, with the spread of contactless and chip cards, the theft of magnetic stripe dumps gradually faded away, which is why the relevance of such devices fell to almost zero.
Such things.
I think that the vast majority of people sitting here are familiar with such devices for stealing bank card data as skimmers. They were actively fought (sometimes successfully, and sometimes not so much), and they quietly and imperceptibly went down in history to the spread of contactless cards.

Many people have probably heard about special pads of a tricky shape on card readers, designed to protect the device from installing foreign equipment. But it wasn't all about protective plastic parts, there were much more interesting devices, a couple of which fell into my hands.
So, in today's article we will talk about such a little-known type of ATM protection among ordinary people as active anti-skimmers. Along the way, let's try to launch my existing devices and find out how they work. Traditionally, there will be a lot of interesting things.
❯ The bottom line is
In the era of magnetic cards, this situation was quite common — you withdraw money from an ATM in the alley, everything goes fine, only then suddenly it turns out that the funds on the card did not happen. In our city, I did not find this method of carding, but in larger and more visited places, such devices were actually installed. Alas, this time the reality was not so different from what was told in thematic publications — a simple pair of overlays on the reader and keyboard made it possible to steal data from everyone who used the ATM. With these things actively fought, putting special plastic devices that do not allow you to install something else. But, as it turned out, everything is not so simple, in fact, there were much more interesting solutions. I don't see any point in talking about the skimmers themselves, almost everything has already been said before me. Today we will talk about how they were protected from them.
❯ What else was installed to protect against such devices?

The simplest option was the usual plastic pads. Such a thing made it very difficult to install extraneous equipment on the reader. And if it did not make it difficult, then the "mined" ATM was easily visible even to the average person.

But there is a problem — with the help of a flat screwdriver, the plastic thing easily came off (after which you could insert your electronics into it and fasten it to the ATM), the transparency of many of these details did not help much. The solution was simple — to ensure that the integrity of this node is controlled. A loop with a snake track like in a POS terminal, and now when a hole is torn off or poked in this part, the card reader is either turned off or an alarm is triggered.

And finally, the most interesting option is hardware anti-skimmers. These devices can either detect malicious devices or interfere with their operation. We'll talk about them today.
❯ What are these devices?
By their principle of operation, they are much more complicated than simple attachments. Such devices were produced by several companies, but the principle of operation is approximately the same.
In general, for some reason, there is little mention of the device and the operation of these pieces, only some unique patented technologies are mentioned without a detailed description of how it works.
Hardware antiskimmers are divided into two categories — those that detect the installation of such devices (after which the ATM is usually blocked) or those that suppress their operation (while the ATM can be safely used). The latter usually have the same functionality as the former, reporting suspicious activity to the bank.
A typical such device consists of an antenna that emits interference that interferes with the operation of the skimmer's magnetic head, volume sensors to monitor the presence of something foreign near the card reader, and limit switches to control card rolling.
❯ Hardware Overview
It so happened that I got my hands on two such devices, one from the Russian company Answer Pro, the other from the Dutch TMD (not to be confused with the duplicator of intercom keys).

And here is the first device. A small blue box with a screen and two LEDs.

The second part of the TMD is another module that connects to the main unit with a three-wire cable.

The second device is the Russian Cerberus. It looks more modest: there are only connectors on the case and nothing else. However, I managed to find software for the second one, so most of the attention will be paid to it today.
❯ TMD
The first in line will be a device from TMD Security.

In the field of ATM protection tools, this is a fairly serious company, which also produces the same legendary coloring cassettes, anti-explosion protection tools and other cool equipment, which also includes the same anti-skimmers.

But let's move on to our device. I don't have any pinout of it, so in order to run it, it had to be disassembled. Inside, everything is expected-a display (8*2, HD44780), a couple of relays, LEDs, a squeaker, a reset button, an RTC battery.

Let's remove the screen. There are three PIC microcontrollers under it at once. Power was found quite quickly — the first and second pins of the rightmost connector.
We apply 24 volts, and the device starts.

But, alas, after initializing the sensors, it gives an error. I don't have the faintest idea how these sensors work (and they are digital here), nor do I have any software to configure them (which is much more serious), so nothing can be done about it.

And here is the filling of a small box. This is the same interference generator. There is another small PIC on the board, as well as the BD6232HFP chip — a powerful H-bridge. In general, it is used as a motor driver, but in this case it controls the coil connected to the second connector on the board. It emits a magnetic field during the operation of the device, which interferes with the operation of the skimmer's magnetic head.
❯ Cerber
Let's move on to the second device. This time it is a product from a Russian company. Its website still works, so you can immediately download drivers and software.

And here is the inside of the device. The power elements of the power supply circuits of the device, card reader and antenna, the STM32 microcontroller, and the power-off relay are clearly visible. The device connects to the card reader's power cable gap and can disconnect it if necessary. The second power connector is connected to the same antenna that generates interference. There are three more connectors — an end cap, a receiving antenna,and a capacitive sensor. The box is connected to the computer via the CP2102 USB-UART bridge.

This is what the same coil looks like, being installed on an ATM. In appearance, it is very similar to the demagnetization loop that can be found in old televisions and monitors.

Launching it. The relay clicks, and the error LED lights up. A good start.

Now it's the software's turn. We start the standard software and see in the list of errors the break of the same induction loop. I don't have a standard coil, so instead I just connected a powerful resistor. The field created by the coil is quite powerful, with its resistance of ten ohms (as stated in the documentation), a current of about four amperes flows in it.

After that, all three LEDs, as expected, turned green.

Judging by the log, the last time the device was launched was in 2017.

The most interesting point is debugging. Here you can view real-time sensor data. For example, I connected a 36-volt incandescent lamp and a toggle switch to the power connector of the card reader. When it was turned on and off, the values on the chart also changed.

The radiation sensor is just a loop antenna.

By the way, if you place the emitter next to the control unit, it will begin to respond to its own interference, first peaks will appear, and then the graph will quickly creep up.

With the end cap, obviously, nothing interesting.

The most interesting thing is the capacitive sensor, which is connected to the unit with as many as six wires. The sensor itself, alas, I do not have, and in its absence, the reading does not go…

This is what this part looks like when installed. It allows you to control the presence of something foreign near the slot of the card reader.
❯ How does it all work?
Well, let's move on to the most interesting part — an analysis of how it all works.

Here is a typical magnetic card drive from an ATM. Specifically, this one is NCR IMCRW, but in other models (Wincor, Diebold), these pieces are absolutely identical in design.
In fact, I have several such devices, so maybe someday I will tell you more about them.

But now we are only interested in its

The unit itself came to me burnt out (they tried to start it up and applied 24 V to the 5 V bus), and I disassembled it for the sake of mechanical parts, leaving part of the swallowing mechanism as a memory.

Unlike terminals, where the card slot is not protected by anything, everything is much more interesting here. If you look at this module from below, you can see the so-called pre-reading head. It does not read anything, but only detects that the inserted card contains a magnetic stripe. This is necessary to protect the reader from vandals (stuffing a business card, a simple plastic card, or any other object of a similar size will no longer work) and inattentive users (a card inserted on the wrong side due to the presence of convex letters on it may get stuck or scratch rubber rollers).

And here is the limit switch that works when inserting the card. This is where one of the device's inputs is connected (in parallel with the card reader).

If the limit switch is activated and the head sees the strip, the electromagnet opens the curtain, allowing you to push the card further. It is this moment that is controlled by the antiskimmer. As you know, the most dangerous moment for a map is when it is inserted. This is when you need to turn off the potentially installed skimmer. In normal mode, the coil emits medium-power interference (to potentially eliminate reading before the sensor is triggered, and also to prevent the skimmer from transmitting data over the radio channel, if any). When the card is inserted, the limit switch closes, and the interference turns on at full power, preventing an unauthorized device from reading the card data. Since the head in the skimmer is not shielded in the same way as in an ATM or terminal, the output signal is easily clogged with noise. When the limit switch is released, the interference power drops to a minimum: the card is inside, now the most important thing is not to interfere with its reading. Activity is also monitored by card reader consumption. A drive motor and electromagnets (shutters, swallowing mechanism, smart card reader drive) are installed inside it, which is why the start of its operation leads to a clearly distinguishable current surge.
Also, a relay is installed inside the unit, which allows you to turn off the power to the card reader in an emergency situation. When the capacitive sensor is triggered, the device understands that there is something else next to the reader and can block working with cards, if this is specified in its settings. These trigger thresholds are defined in the same control software.
❯ That's something like this
Despite its effectiveness against very simple skimmers, very often this thing created a lot of problems.
By themselves, skimmers quickly adapted to such devices — their creators learned how to compensate for interference and save dumps on the built-in memory. But those who serve ATMs, these devices drank a lot of blood. The coil caused such powerful interference that the magnetic readout head believed that the card was always there (moreover, the instructions for installing the device on some ATM models explicitly stated to disconnect its connector from the board), which is why the reader was triggered in fact only from the limit switch, which led to its damage from incorrectly or simply crookedly inserted cards. In addition, the installation of sensors on the receiving slot required special care: if the card reader is not aligned with the slot on the door when closing the door (on some models of ATMs with such a design), then the card will no longer be able to leave by itself after insertion. Fortunately, with the spread of contactless and chip cards, the theft of magnetic stripe dumps gradually faded away, which is why the relevance of such devices fell to almost zero.
Such things.

