CarderPlanet
Professional
Let's talk about what logs are. We will show how to extract the necessary information from the log for setting up configurations from scratch.
Let's start very briefly for beginners about what logs are. Logs are a set of files that contain various information from the user's PC. Logs include: browser data (Cookie, History of visits, Auto fill, List of downloads, Logins / Passwords from various sites), Information about the user's system, Screenshot of the user's screen. May also contain: files from cryptocurrency wallets, files from Steam, saved by CC, etc.
Logs are used in different areas of work: from gray to black, but more often, as a rule, the latter option. Logs can be bought or obtained by yourself. The most common options for selling logs are:
The second option is much less common, costs more, but gives even more confidence from shops, Antifraud systems, since you use the IP address of the PC owner.
Let's move on to the main part. We got it, we bought a log from any stealer. Popular stealers, from which logs are received now: AZORul, Arkei Stealer and Vidar. AZORult is the most popular stealer, but recently the author has closed official sales and topics on forums. The last stealer, Vidar, appeared not so long ago, but a lot of logs from this stealer are already being sold, and according to reviews for those who want to receive logs themselves, this is a great option.
Although there are different stealers, the basic information and its structure are very similar, so the log from which stealer does not play a big role.
Now let's move on to working with logs.
By all parameters, all logs can be divided according to the degree of importance (in descending order of importance):
For beginners, first of all, there will be advice not to disdain category 2 and 3 logs, treat them with the same seriousness as logs in the first category in order to gain experience, get their hands on, technically learn how to use the log and the selected tool for processing it correctly ...
On the forums, spent logs of different categories are often distributed; this option is also a good option for starting work with logs.
You can determine the degree of importance by the Logins / Passwords of the log, auto-fill, and sometimes even by the splash screen on the desktop, you can distinguish the log of a nerd student from a good log.
With experience, depending on your skills, financial situation, you yourself will determine once or twice with which log to work painstakingly, with which not very much, and which one should be thrown out and not wasted your time.
It often happens that newbies work out logs for only 1 request, for example, on Paypal, and if they can't work out, they get upset and throw out the log. This is a bad approach to work, because with it you will not get a normal profit and knowledge; if you have a lot of time and little experience, work out the log to the fullest, fill your hand.
Tips and tricks for working with logs
For example, you can urgently call the holder to work, send a wreath with threats (Having said that this is from the mafia, the insurance company will return everything, do not rock the boat until we rob you). It is important to understand the essence of these thoughts, and the imagination in the options for using useful information can be limitless.
Getting basic information from the system log

In the screenshot, I have highlighted the parameters that we need to configure the system.
Screenshot:
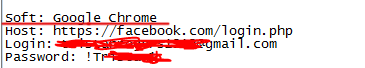
As well as files in the "Cookies" folder for the presence of the necessary sites (files in this folder are divided into browsers; it is possible that the Cookies files can be stored in a shared folder. It all depends on which stealer the log is from).
Example:
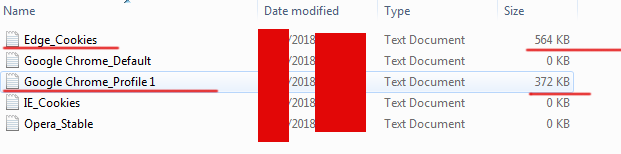
In my case, there is only one Google Chrome browser in the log, so I mark myself only 1 browser. Moving on to more interesting information that does not lie on the surface.
Determine if there is FLASH in the system and its version, determine the browser version (if possible)
To do this, go to the System.txt or Information.log file and look for "Adobe Flash Player" in the [Software] section of the installed programs. If found, then we mark that Flash is, write down its version. There are two types of Adobe Flash Player: Adobe Flash Player ** NPAPI - for Firefox browser. Adobe Flash Player ** PPAPI - for Opera / Chrome browser.
Screenshot:
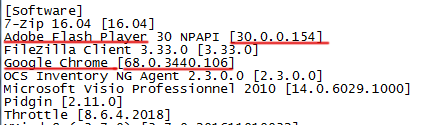
Next, on the same screenshot, we see the version of Google Chrome, if not, then we try to find it in the file at the request “Google Chrome”. We also mark the version for ourselves. We will need the type of browser and its version to configure the "navigator.UserAgent" parameter, and, in exceptional cases, to disable canvas substitution. We are looking for the Mozilla Firefox browser by the request "Firefox", we should find something like this "Mozilla Firefox 64.0 (x64 en-US) [64.0]". The name of the Firefox browser contains the bitness of the program (32 or 64 bit), which is also useful in setting "navigator.UserAgent". We are looking for the Opera browser for the query "Opera", we should find something like this "Opera Stable 57.0.3098.106 [57.0.3098.106]".
For various reasons, it is not always possible to determine the version of the browser, one of which is that the browser can be Portable, ie not installed on the system. IE browser will not be visible, because it's already natively in Windows, with Edge in Win 10 the same hat.
We need Flash and its version in order to add it to plugins and, if necessary, enable its physical version in the antidetect.
Determine the user's desktop computer (Desktop) or Laptop (Laptop)
This can be determined using various options.
User's network: we define an approximate router and its model (if possible)
Sometimes the log can be used to determine the brand of the user's router or its approximate model. This may be necessary for more precise configuration of WebRTC, or rather, Local IP Address.
To do this, you need to look in the log in the file with logins / passwords or in the file where the browser history is stored, the popular masks of the IP addresses of routers.
If the username and password are still indicated there, you can try to look by brands here:
Browser plugins: identify popular plugins that are installed in the browser.
Plugins in any program are add-ons that allow you to expand its capabilities. Most of the popular browsers have the ability to install plugins that extend its capabilities. For example, it can be a Flash plugin from Adobe, the ability to read PDF pages in a browser; in Chrome, this plugin is already included by default; the ability to run any Audio / Video codecs.
With each new release of updates, the number of new features and variations of the supported content increases, so plugins are gradually losing their relevance. As a result, in the browsers Chrome, Firefox, Opera, Edge, there are only built-in plugins and one added: Adobe Flash Player. Therefore, the search for plugins is more relevant for the Internet Explorer browser, or for older versions of Firefox (up to version 52), Chrome, Opera.
Most popular plugins: Flash, Java, Microsoft Office, Adobe PDF Reader, Windows Media Player, Real Video / Audio.
At the beginning of the article, we already determined whether Flash is on the system. So Flash Player is also a plugin in the browser. Therefore, if there is Flash, then in some types of browser it will be in plugins. We mark ourselves, if available.
We will also search for other plugins in the System.txt file, or Information.log in the [Software] section of the installed programs.
Plugins:
[*] The QuickTime plug-in is found by request "QuickTime", the approximate name of the plug-in: "QuickTime 7 [7.79.80.95]"
[*] The Silverlight plugin is found by the query "Microsoft Silverlight", the approximate name of the plugin: "Microsoft Silverlight [5.1.50907.0]"
[*] The Java plug-in is found by the query "Java", the approximate name of the plug-in: "Java 8 Update 191 [8.0.1910.12]"
[*] The RealPlayer plugin is found by request "RealPlayer", the approximate name of the plugin: "RealPlayer [18.1.15.]"
[*] Plugin Adobe Acrobat (for reading PDF files) is found by request "Adobe Acrobat Reader DC", in the end it will be something like "Adobe Acrobat Reader DC [19.010.20064.]"
There are many other different plugins, this was just an example of popular plugins. The list can be continued for a very long time.
This completes the collection of information from the log.
Display Resolution: 1920x1080
Display Language: en-US
Keyboard Languages: English (United States)
CPU Count: 4
RAM: 8139 MB
VideoCard: NVIDIA GeForce GTX 970
[Network]
IP: 38.104.174.234
Country: United States (US)
City: Pleasant View (California)
ZIP: 93260
ISP: Cogent Communications (Txox Communications)
-
Browser: Google Chrome ver. 68.0.3440.106
Flash: available, ver. 30.0.0.154
-
PC: Laptop
-
[Task bar]
Position: Horizontal
Icon Size: Large
Hidden Taskbar: No
Is there a browser in the screenshot: YES
-
Router: ~ TP-Link TL-WR741N or TL-WR841N
-
[Browser Plugins]
Adobe flash player
RealPlayer
Adobe acrobat
Of course, this example has too much information. In practice, it may be less.
Let's start very briefly for beginners about what logs are. Logs are a set of files that contain various information from the user's PC. Logs include: browser data (Cookie, History of visits, Auto fill, List of downloads, Logins / Passwords from various sites), Information about the user's system, Screenshot of the user's screen. May also contain: files from cryptocurrency wallets, files from Steam, saved by CC, etc.
Logs are used in different areas of work: from gray to black, but more often, as a rule, the latter option. Logs can be bought or obtained by yourself. The most common options for selling logs are:
- Sell only log
- Sell the holder's log + Socks
The second option is much less common, costs more, but gives even more confidence from shops, Antifraud systems, since you use the IP address of the PC owner.
- Sell log + VNC / HVNC access
Let's move on to the main part. We got it, we bought a log from any stealer. Popular stealers, from which logs are received now: AZORul, Arkei Stealer and Vidar. AZORult is the most popular stealer, but recently the author has closed official sales and topics on forums. The last stealer, Vidar, appeared not so long ago, but a lot of logs from this stealer are already being sold, and according to reviews for those who want to receive logs themselves, this is a great option.
Although there are different stealers, the basic information and its structure are very similar, so the log from which stealer does not play a big role.
Now let's move on to working with logs.
By all parameters, all logs can be divided according to the degree of importance (in descending order of importance):
- A log that has a set of standard services complete with BA and cryptocurrency exchanges.
- Log, which has a set of standard services such as Paypal, Amazon, various shops
- A log that has a couple of services / not interesting small shops; We do not particularly admire the cookies of this log.
- Useless log
For beginners, first of all, there will be advice not to disdain category 2 and 3 logs, treat them with the same seriousness as logs in the first category in order to gain experience, get their hands on, technically learn how to use the log and the selected tool for processing it correctly ...
On the forums, spent logs of different categories are often distributed; this option is also a good option for starting work with logs.
You can determine the degree of importance by the Logins / Passwords of the log, auto-fill, and sometimes even by the splash screen on the desktop, you can distinguish the log of a nerd student from a good log.
With experience, depending on your skills, financial situation, you yourself will determine once or twice with which log to work painstakingly, with which not very much, and which one should be thrown out and not wasted your time.
Log processing can be complex, or processing for one specific request.Working out logs in Linken Sphere is very convenient because, using different tabs, you can process several logs at the same time, which also saves time.
It often happens that newbies work out logs for only 1 request, for example, on Paypal, and if they can't work out, they get upset and throw out the log. This is a bad approach to work, because with it you will not get a normal profit and knowledge; if you have a lot of time and little experience, work out the log to the fullest, fill your hand.
Tips and tricks for working with logs
- Determine your "attack vector". Simply put, you need to understand where the holder has money, what means of payment he uses most often. You can view the popular payment methods of the holder in Amazon, Paypal, Ebay, etc.). After you have determined where the money is, you need to try to find out how much money is kept by the holder, if possible. To do this, you need to get into online banking, look statemans, etc.
- Operator services such as AT&T, Verizon and others may have the function of blocking a SIM card, losing a phone and other useful things that can complicate the restoration of the holder's access, or even complete loss.
- Always put messages from unwanted services and shops from which messages may come from in the mail of the holder in the spam filters. Redirect the necessary messages through filters to your mail.
- Check all cloud storages (Google drive, icloud, onedrive, dropbox, etc.) There is a good chance that you will find Photo ID, Drive License, Credit Cards, Wallet Seed, 2FA and other useful information there.
- Live the life of a holder. After collecting all the information on the holder, read it on Facebook and other social media. networks, look where he is going tomorrow, when he is not at home, when he is in the gym, when he eats, with whom he fucks, this will help to compose a psychological portrait for psychological impact, as well as give the opportunity to choose the best attack time
For example, you can urgently call the holder to work, send a wreath with threats (Having said that this is from the mafia, the insurance company will return everything, do not rock the boat until we rob you). It is important to understand the essence of these thoughts, and the imagination in the options for using useful information can be limitless.
- Leave backdoors behind. Put your secret questions on mails, link up your 2FA, phones, backup mails. Then, with a high probability, the holder will not be able to quickly and painlessly return his account, and even if he does, he may not notice your backdoor, which you can use again.
- Passwords. Many holders use the same passwords, therefore, even if the required service is not in the log, you can choose it yourself by brute force
- Activity. By letters in the mail, you can determine the most popular and freshest by date services that the holder uses. From them, choose the ones you need, which you know how to work out. These services will be more fraud-loyal, since the holder often uses them, and, therefore, they have more recent cookies compared to other services.
Getting basic information from the system log
In the log, the most basic information about the system is contained in the System.txt file, or Information.log.

In the screenshot, I have highlighted the parameters that we need to configure the system.
- Windows - This parameter contains information about the Windows version and the bitness of the system (32-bit or 64-bit, 64-bit is much more common). Most often you will come across logs of Windows 7, Windows 10, less often - Windows 8, 8.1, XP. We will need this parameter to configure "navigator.UserAgent" and some derivatives.
- Display Resolution - This parameter contains information about the user's screen resolution. Required to configure all settings related to screen resolution and browser window size and derived settings.
- Display Language, Keyboard Languages - These parameters contain information about the system language / languages. Needed to configure the parameters “navigator. Language "," navigator. Languages ”and HTTP_ACCEPT_LANGUAGE.
- CPU Count - This parameter contains information about the number of processor threads. Needed to configure the parameter "navigator.hardwareConcurrency"
- RAM - This parameter contains information about the amount of RAM. Required for setting "navigator.deviceMemory"
- Videocard - This parameter contains information about the video card of the system. Required for configuring WebGL. Please note that the system can contain two video cards: one discrete and the other integrated. This is usually used on laptops. And which of them runs for the browser is 100% unknown. Firstly, the user can manually set which video card will be used, and secondly, for example, it can be like this: if the laptop is on charge, a discrete video card is used, if from a battery, then an integrated one. Therefore, in laptops, you should not rely on this parameter 100%.
- [Network] We take almost all parameters, except Geo (Latitude and Longitude); This information will be useful to you for a more competent selection of Socks / SSH tunnel. There is no ZIP in my log, but it is not difficult to break through it. To do this, you just need to punch the IP address through the MaxMind database, or find the user's home address in the browser autocomplete, or by mail or in a shop. It is advisable to select the IP not only as close as possible to the ZIP address, but also, if possible, with the same IP mask and the same Internet provider.
Screenshot:

As well as files in the "Cookies" folder for the presence of the necessary sites (files in this folder are divided into browsers; it is possible that the Cookies files can be stored in a shared folder. It all depends on which stealer the log is from).
Example:

In my case, there is only one Google Chrome browser in the log, so I mark myself only 1 browser. Moving on to more interesting information that does not lie on the surface.
Determine if there is FLASH in the system and its version, determine the browser version (if possible)
To do this, go to the System.txt or Information.log file and look for "Adobe Flash Player" in the [Software] section of the installed programs. If found, then we mark that Flash is, write down its version. There are two types of Adobe Flash Player: Adobe Flash Player ** NPAPI - for Firefox browser. Adobe Flash Player ** PPAPI - for Opera / Chrome browser.
Screenshot:

Next, on the same screenshot, we see the version of Google Chrome, if not, then we try to find it in the file at the request “Google Chrome”. We also mark the version for ourselves. We will need the type of browser and its version to configure the "navigator.UserAgent" parameter, and, in exceptional cases, to disable canvas substitution. We are looking for the Mozilla Firefox browser by the request "Firefox", we should find something like this "Mozilla Firefox 64.0 (x64 en-US) [64.0]". The name of the Firefox browser contains the bitness of the program (32 or 64 bit), which is also useful in setting "navigator.UserAgent". We are looking for the Opera browser for the query "Opera", we should find something like this "Opera Stable 57.0.3098.106 [57.0.3098.106]".
For various reasons, it is not always possible to determine the version of the browser, one of which is that the browser can be Portable, ie not installed on the system. IE browser will not be visible, because it's already natively in Windows, with Edge in Win 10 the same hat.
We need Flash and its version in order to add it to plugins and, if necessary, enable its physical version in the antidetect.
Determine the user's desktop computer (Desktop) or Laptop (Laptop)
This can be determined using various options.
- According to the screenshot of the screen in the log . On the screenshot of the screen, we are looking for something that is characteristic of a laptop on the taskbar in the lower right corner, or on the desktop that is characteristic of a laptop (icons for programs for a laptop, etc.).
- According to information about the processor in the system . To do this, go to the System.txt file, or Information.log and look at the "Processors" parameter
Examples of processes: Intel (R) Wireless Bluetooth (R), Dell Touchpad.Well, another option is to look in the processes or installed programs in the System.txt file, or Information.log for processes / programs that belong to the laptop. For example, these are processes in which the keyword "Bluetooth" appears, programs specific to a particular laptop manufacturer (ASUS, DELL, MSI, ACER, etc.)
User's network: we define an approximate router and its model (if possible)
Sometimes the log can be used to determine the brand of the user's router or its approximate model. This may be necessary for more precise configuration of WebRTC, or rather, Local IP Address.
To do this, you need to look in the log in the file with logins / passwords or in the file where the browser history is stored, the popular masks of the IP addresses of routers.
The most popular masks for searching in the log are: "192.168.", "10.0.", "10.1.", "10.90.". I highlighted the most popular brands in light blue in the table.
If the username and password are still indicated there, you can try to look by brands here:
Browser plugins: identify popular plugins that are installed in the browser.
Plugins in any program are add-ons that allow you to expand its capabilities. Most of the popular browsers have the ability to install plugins that extend its capabilities. For example, it can be a Flash plugin from Adobe, the ability to read PDF pages in a browser; in Chrome, this plugin is already included by default; the ability to run any Audio / Video codecs.
With each new release of updates, the number of new features and variations of the supported content increases, so plugins are gradually losing their relevance. As a result, in the browsers Chrome, Firefox, Opera, Edge, there are only built-in plugins and one added: Adobe Flash Player. Therefore, the search for plugins is more relevant for the Internet Explorer browser, or for older versions of Firefox (up to version 52), Chrome, Opera.
Most popular plugins: Flash, Java, Microsoft Office, Adobe PDF Reader, Windows Media Player, Real Video / Audio.
At the beginning of the article, we already determined whether Flash is on the system. So Flash Player is also a plugin in the browser. Therefore, if there is Flash, then in some types of browser it will be in plugins. We mark ourselves, if available.
We will also search for other plugins in the System.txt file, or Information.log in the [Software] section of the installed programs.
Plugins:
[*] The QuickTime plug-in is found by request "QuickTime", the approximate name of the plug-in: "QuickTime 7 [7.79.80.95]"
[*] The Silverlight plugin is found by the query "Microsoft Silverlight", the approximate name of the plugin: "Microsoft Silverlight [5.1.50907.0]"
[*] The Java plug-in is found by the query "Java", the approximate name of the plug-in: "Java 8 Update 191 [8.0.1910.12]"
[*] The RealPlayer plugin is found by request "RealPlayer", the approximate name of the plugin: "RealPlayer [18.1.15.]"
[*] Plugin Adobe Acrobat (for reading PDF files) is found by request "Adobe Acrobat Reader DC", in the end it will be something like "Adobe Acrobat Reader DC [19.010.20064.]"
There are many other different plugins, this was just an example of popular plugins. The list can be continued for a very long time.
This completes the collection of information from the log.
Windows: Windows 10 Home [x64]As a result, we have collected the following information:
Display Resolution: 1920x1080
Display Language: en-US
Keyboard Languages: English (United States)
CPU Count: 4
RAM: 8139 MB
VideoCard: NVIDIA GeForce GTX 970
[Network]
IP: 38.104.174.234
Country: United States (US)
City: Pleasant View (California)
ZIP: 93260
ISP: Cogent Communications (Txox Communications)
-
Browser: Google Chrome ver. 68.0.3440.106
Flash: available, ver. 30.0.0.154
-
PC: Laptop
-
[Task bar]
Position: Horizontal
Icon Size: Large
Hidden Taskbar: No
Is there a browser in the screenshot: YES
-
Router: ~ TP-Link TL-WR741N or TL-WR841N
-
[Browser Plugins]
Adobe flash player
RealPlayer
Adobe acrobat
Of course, this example has too much information. In practice, it may be less.
