Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,046
- Points
- 113
Experts from Israel's Ben-Gurion University presented a new method for extracting data from machines physically isolated from any networks and potentially dangerous periphery. Such computers are often found in government systems and corporate networks, they store secret documents, as well as classified and confidential information.
The experts' attack was named BRIGHTNESS. It should be noted that the researchers' method, as usual, only solves the issue of data theft, but you need to understand that before that the attacker will need to infect an isolated machine with malware.
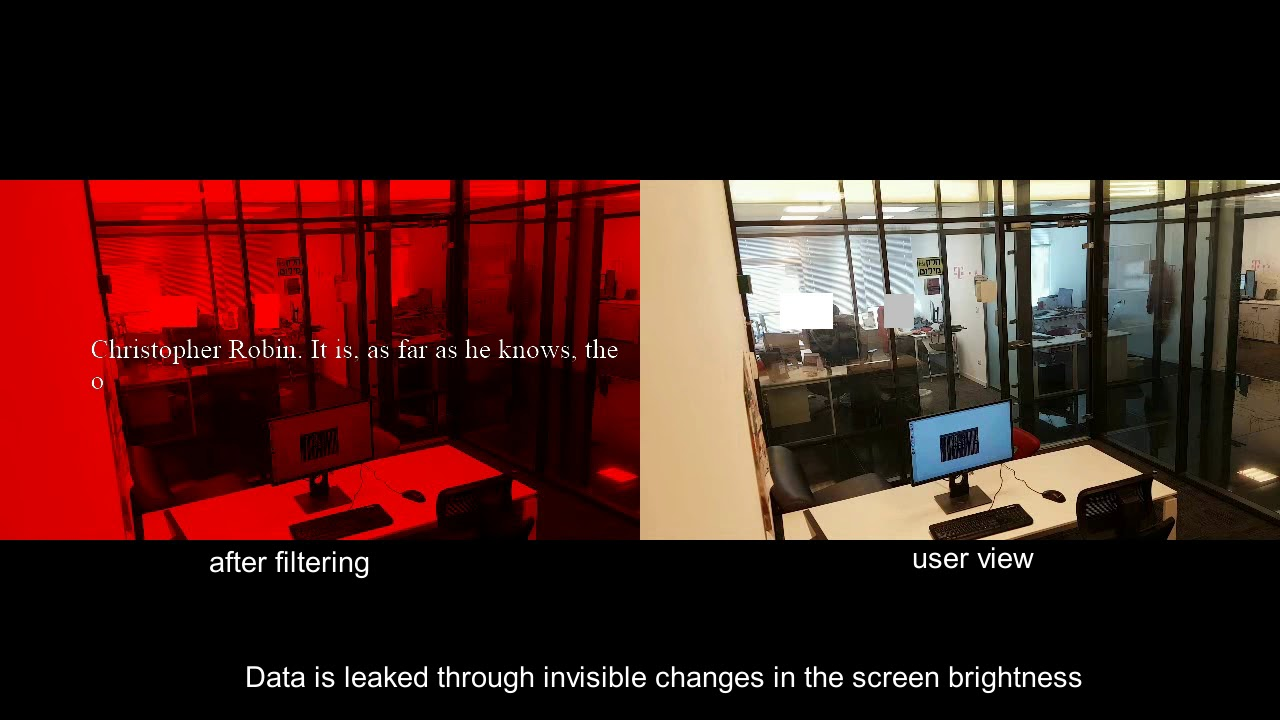
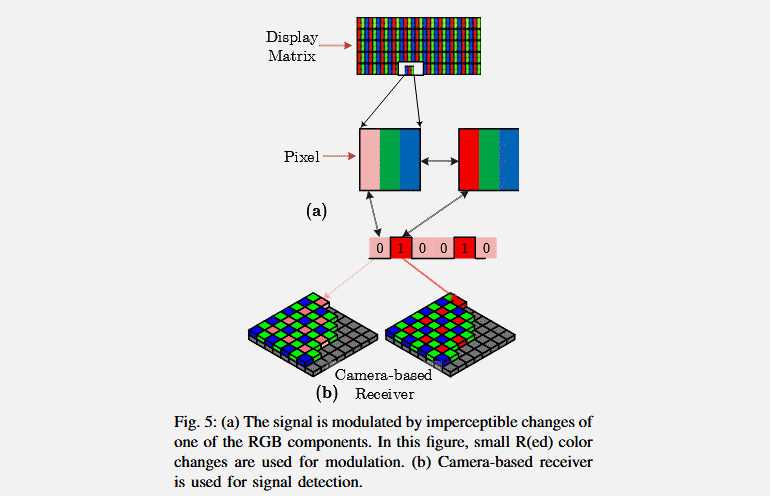
The attack works as follows. Malware infiltrating the machine collects data that needs to be stolen, and when it comes time to "merge" it, it changes the monitor settings to change the screen brightness level. These differences in brightness are a sequence of zeros and ones, that is, a binary code, and allow you to gradually transfer the desired data, one bit at a time. An attacker only needs to record the flickering of the screen, and later analyze the video and restore the transferred file.
After testing BRIGHTNESS on several configurations, the researchers achieved the best results, varying the brightness of the red pixels by about 3%. Such minor changes are almost impossible to notice with the naked eye, but modern cameras (including webcams, surveillance cameras, as well as cameras in smartphones and laptops) can record them without problems.

Of course, the main disadvantage of this attack is the data transfer rate. So, according to the test results, the maximum data transfer rate was only 5-10 bit / s, and this is the worst result among all exotic methods of extracting information from isolated machines that researchers have invented (see the list at the end). In fact, the BRIGHTNESS attack can be useful only for stealing a small encryption key, but it is definitely impossible to transfer a 1 GB archive in this way.

The research notes that the easiest way to protect against such attacks is to apply polarizing film to monitor screens.
It is worth mentioning other developments of specialists from Ben-Gurion University. Here are just a few of them:
- USBee : turns almost any USB device into an RF transmitter for transferring data from a secure PC;
- DiskFiltration : intercepts information by recording the sounds that the hard disk of the computer emits while the computer is running;
- AirHopper : Uses the FM receiver in your mobile phone to analyze the electromagnetic radiation emanating from your computer's graphics card and turns it into data;
- Fansmitter : regulates the speed of the cooler on the infected machine, as a result of which the tone of the cooler's operation changes, it can be listened to and recorded by extracting data;
- GSMem : will transmit data from an infected PC to any, even the oldest push-button telephone, using GSM frequencies;
- BitWhisper : uses thermal sensors and thermal energy fluctuations;
- An unnamed attack that uses flatbed scanners and smart bulbs to transmit information;
- HVACKer and aIR-Jumper : stealing data using CCTV cameras that are equipped with IR LED (infrared light-emitting diodes), as well as use as a "bridge" to isolated networks of heating, ventilation and air conditioning systems;
- MOSQUITO : data extraction is suggested to be carried out using ordinary headphones or speakers;
- PowerHammer : It is suggested to use regular power cables for data extraction.
- CTRL-ALT-LED : Caps Lock, Num Lock and Scroll Lock diodes are used to retrieve information.

