Man
Professional
- Messages
- 3,222
- Reaction score
- 1,215
- Points
- 113

A group of scientists from Ben-Gurion University of the Negev (Israel) is studying ways to transmit information from isolated computers (airgap). They have already developed methods for transmitting data by blinking the HDD LED, router or keyboard, electromagnetic radiation from the USB bus and from the GPU card, sounds from the GPU cooler and HDD magnetic head, through thermal radiation and audio speakers (in the inaudible range), by changing the PC's power consumption and display brightness. It turns out that the list is not limited to this.
On April 13, 2020, scientists published a description of a new AiR-ViBeR attack with data exfiltration through fan vibrations. The transfer rate is lower than other methods: only 0.5 bits per second with the system unit lid closed.
A team of researchers led by Mordechai Guri studied the vibrations created by fans in a system unit.
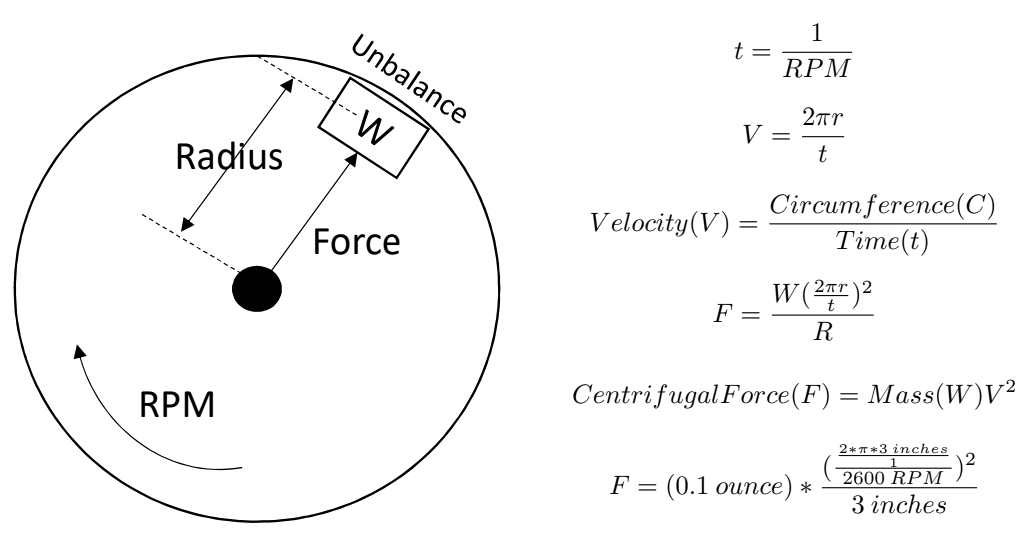
The source of the vibrations is an imbalance, when the center of mass does not coincide with the geometric center of rotation.
The researchers developed a data transfer protocol based on changing the rotation speed of the fan - and, therefore, the vibrations. The method was codenamed AiR-ViBeR.
Isolated systems in local networks without access to the Internet are often used in government or corporate networks to store confidential data. Guri's research does not consider ways to compromise and introduce malware into these highly protected systems, but instead focuses on innovative ways to transmit information in ways that firewalls and security systems are not designed for.
Malicious code injected into the victim's system controls the speed of the fan. In this particular experiment, the FAN CONTROL pin from the motherboard was connected to the GPIO12 pin on the Raspberry Pi 3, and the modulation of the signal by changing the rotation speed of the fan was performed by a Python script.

The signal is received by the accelerometer of the smartphone, which is located at a distance of about a meter from the computer.
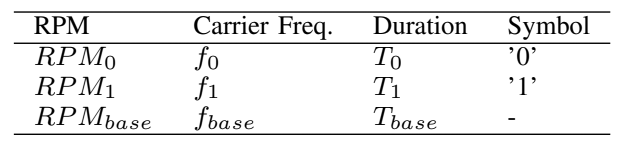
The demodulation algorithm is given below.

Here, a potential attacker has two options: he can either place his smartphone near the infected computer, or infect the smartphones of employees who work with this computer. Accelerometer sensors in modern smartphones are available to any application without requiring user permission, which simplifies the attack, the researchers write.
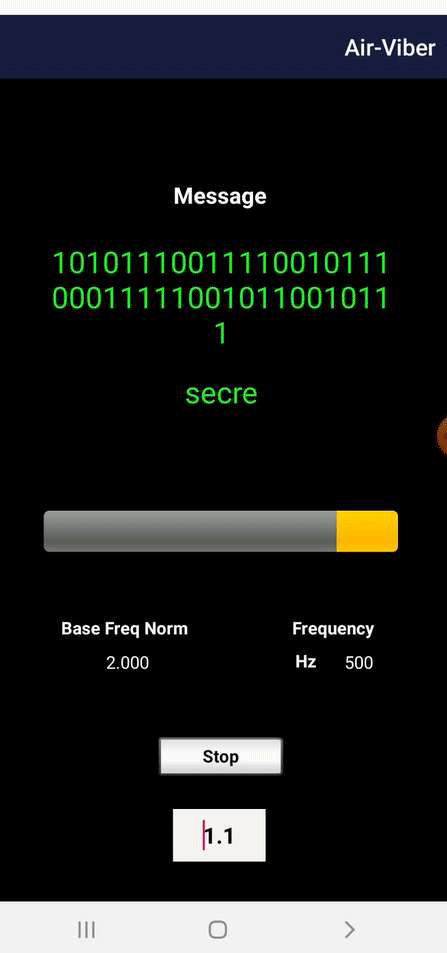
AiR-ViBeR app on smartphone received secret word from computer via table vibrations
Although the AiR-ViBeR attack can be considered theoretically possible, it is extremely unlikely that it will be used in real life. The transmission speed is too low, and attackers would be better off using any other method to retrieve information from an isolated computer.

Signal-to-noise ratio at different positions of the receiving device relative to the signal source (positions are shown in the photo above)
However, administrators of secret systems should keep in mind the theoretical possibility of transmitting data through a computer fan.
Ordinary users should hardly be afraid of this threat. At this rate, a text document will take from several months to a year to be transmitted. Only a password or encryption key can be transmitted in a reasonable amount of time.
Source
