Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,046
- Points
- 113
Content:
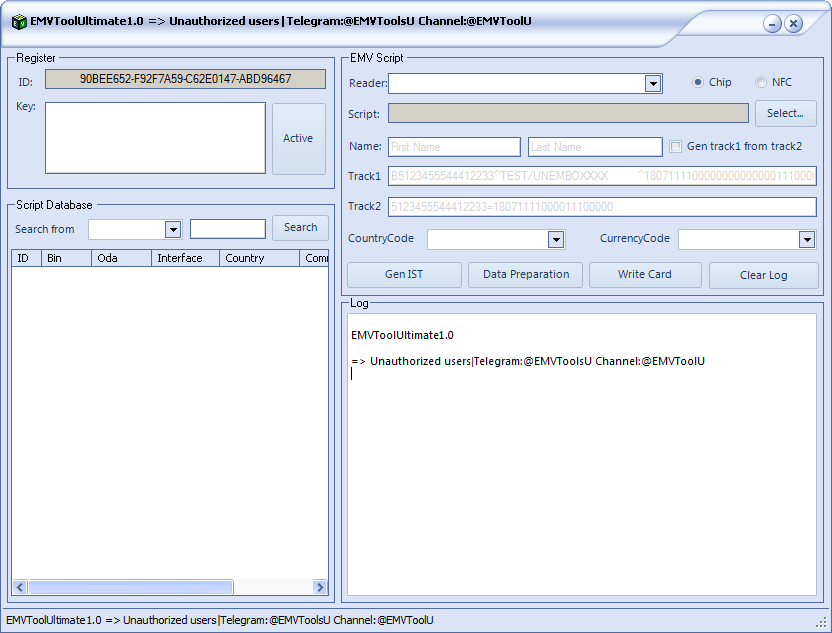
EMVToolUltimate v1.0
SHA-256: 06f40072750772663041e71e3c22b14471894a8433441f41d901095b0393ebfd - VT
SHA-1: ab3e81336b929a0d4f7afbb516580a9dafe523cb
File type: EXE/Windows
File size: 4.70 MB
File name: EMVToolUltimate1.0.exe
ProtectionID:[!] [.net scan core] dotNetReactor detected!
[!] [.net scan core] Confuser detected!
PDB/VBP pathway: c:\MyProjects\gitlab\ILProtector\ILProtector\Output2010\Win32\Release\Protect32.pdb
Compilation date: 2021-06-06 13:07:12
First seen: 2021-06-12 03:26:56
Name: EMVToolUltimate v1.0
Actor: EMVToolsU
Additional note: Seem similar to b3b6085b6706ef90eadba2e48877677d06fa3a6df7c2df5c94773aa7e8b8c1df (ATRToolUltimate 1.0)
Screenshot:
CATR 3.8.7
SHA-256: 81f547c84f90c7a1f9bbba4118e08c41899b40264347d52df73b378f83fab200 - VT (FIRST RACE!)
SHA-1: 9f786b71ca8395c60ad6bb3aa5608c670c01229a
File type: EXE/Windows
File size: 3.50 MB
File name: CATR 2021.exe
ProtectionID:[!] [.net scan core] (smartassembly) DotNet Obfuscator detected!
Compilation date: 2021-08-07 19:35:41
First seen: 2021-10-24 12:05:35
Name: CATR 3.8.7
Screenshot:

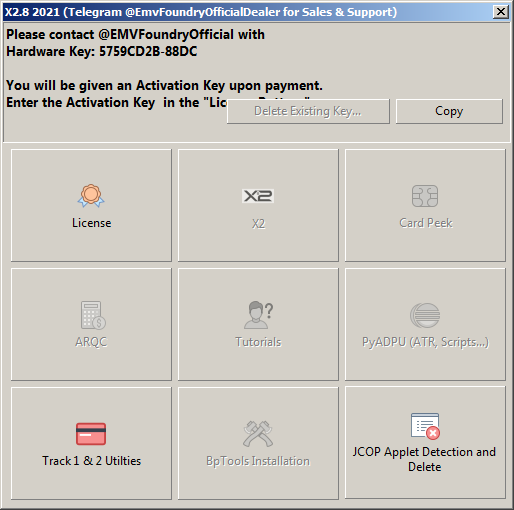
X2 v2.8
SHA-256: 63008b67c5cd4e2985c615402b527c48815ec5cb3d5a771c7651f44bb58f906f - VT
SHA-1: 9cdcdd3a3214881c256c3a4c018593dc6ce54340
File type: EXE/Windows
File size: 24.73 MB
File name: x2classics.exe
ProtectionID:[!] ASProtect SKE v2.72 or higher detected !
[CompilerDetect] -> Borland Delphi (unknown version) - 80% probability
Compilation date: 2021-05-03 19:52:06
First seen: 2021-05-22 22:16:40
Name: X2 v2.8
Actor: EmvFoundryOfficialDealer
Screenshot:
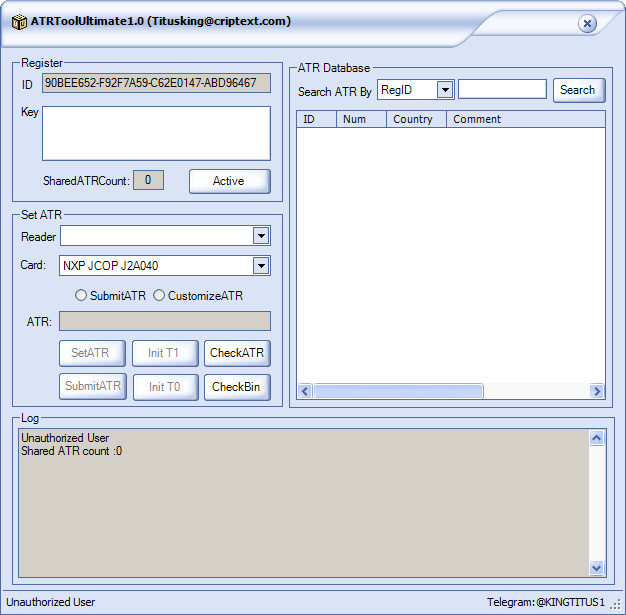
ATRToolUltimate 1.0
SHA-256: b3b6085b6706ef90eadba2e48877677d06fa3a6df7c2df5c94773aa7e8b8c1df - VT
SHA-1: 0666fc1169b5a707f0b063cb416995631e64f44a
File type: EXE/Windows
File size: 2.35 MB
File name: ATRToolUltimate1.0.exe
ProtectionID:[!] [.net scan core] dotNetReactor detected!
[!] [.net scan core] Confuser detected!
PDB/VBP pathway: c:\MyProjects\gitlab\ILProtector\ILProtector\Output2010\Win32\Release\Protect32.pdb
Compilation date: 2021-03-17 01:41:00
First seen: 2021-03-17 02:11:08
Name: ATRToolUltimate 1.0
Actor: titusking@criptext.com
Additional note: Seem similar to 06f40072750772663041e71e3c22b14471894a8433441f41d901095b0393ebfd (EMVToolUltimate 1.0)
Screenshot:
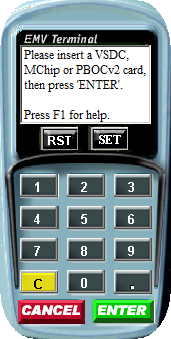
POS Simulator 2.0
SHA-256: 0b014dfd75149161109f5aca027e972100104603fca68b4245780ff9b928e1f7 - VT
SHA-1: 1be4659b6c427292912668527bc19729d8c6958e
File type: EXE/Windows
File size: 1.09 MB
File name: EMVTran.EXE
ProtectionID:[!] File appears to have no protection or is using an unknown protection
Compilation date: 2010-05-23 09:30:46
First seen: 2021-08-07 16:26:52
Name: POS Simulator 2.0
Additional note: "EMV Transaction Tool V1.34 Copyright(C) 2005-2009 Raul Xu"
Screenshot:
ATRtool v2.0
SHA-256: 8a3a3358eb344235a7948179bdea5e1f5df26a8dd15762e691cc8b0d3f0a39d8 - VT
SHA-1: 95f31bf0e402d18813abcd29127c22771061de2d
File type: EXE/Windows
File size: 3.11 MB
File name: ATRTool_2.0.exe
ProtectionID:[!] Enigma Protector V 6.80 Build 0 (reserved 0) detected !
[!] Themida/Winlicense detected !
Compilation date: 1992-05-22 21:12:13
First seen: 2021-01-16 23:09:58
Name: ATRtool v2.0
Actor: TitusKing
Screenshot:
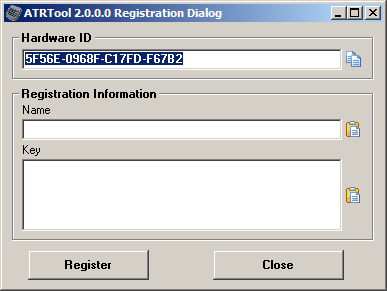
EMVToolUltimate v1.2R
SHA-256: 4ac6b9aa216c21322c5fca1da6395da40962d287fc2fc662a0ac5c05be8a79c9 - VT
SHA-1: 311dcf0134acbabed91d289ad01eb0a5e3822a9d
File type: EXE/Windows
File size: 4.70 MB
File name: EMVToolUltimate1.2.exe
ProtectionID:[!] [.net scan core] dotNetReactor detected!
[!] [.net scan core] Confuser detected!
PDB/VBP pathway: c:\MyProjects\gitlab\ILProtector\ILProtector\Output2010\Win32\Release\Protect32.pdb
Compilation date: 2021-07-08 03:46:30
First seen: 2021-07-17 02:36:48
Name: EMVToolUltimate v1.2R
Actor: TitusKing, EMVToolsU
Screenshot:
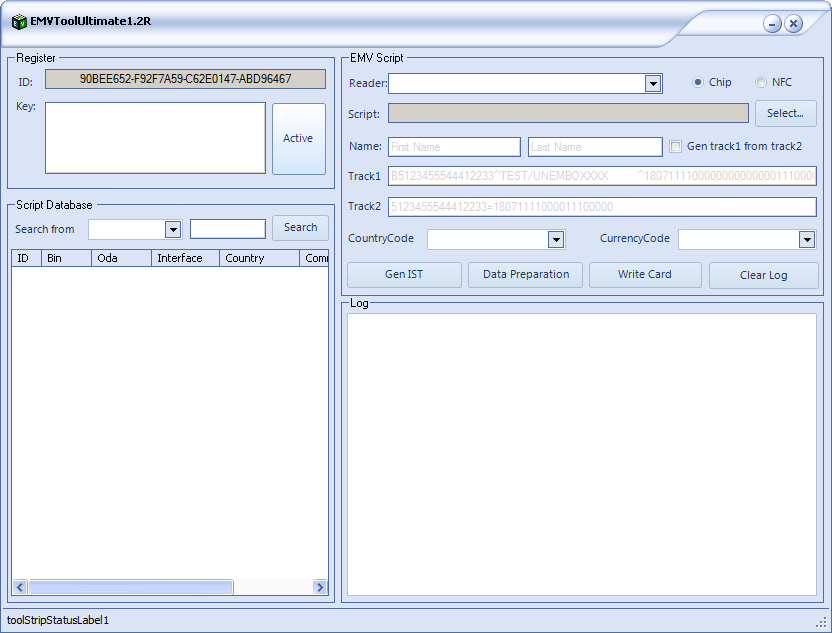
Emvfoundry v1.0.0.63
SHA-256: 5ccaeb149d0311f9820d40956d36959b8d223ebbda6b3394c683c9a6c6a1ec78 - VT (FIRST RACE!)
SHA-1: edff931d6152c37ade8f1e9165ad8beddf7b8170
File type: EXE/Windows
File size: 43.24 MB
File name: emvsetupfull_1063.exe
ProtectionID:[VersionInfo] Version Comments : This installation was built with Inno Setup.
Compilation date: 2020-11-15 09:48:30
First seen: 2021-06-05 07:34:25
Name: Emvfoundry v1.0.0.63
Actor: EmvFoundryOfficialDealer, BC1887, MaggotM
Screenshot:
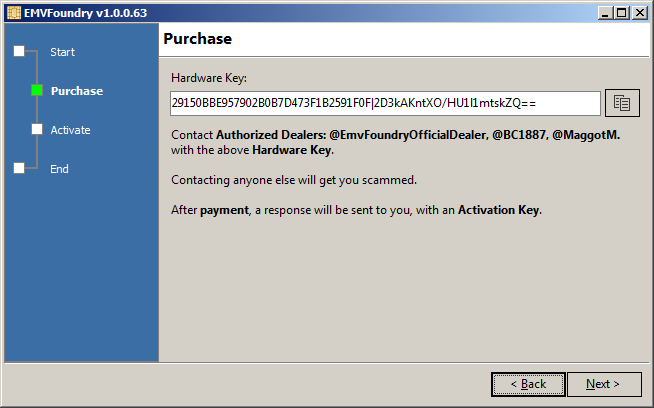
POS Simulator 2.0
SHA-256: 8f278185707c7c359dd66569a0b28361131f25aa59f2f7fcd194b6bd8c55884d - VT (FIRST RACE!)
SHA-1: 8c05a70c73eb0da63d511e925d88219f9ae40809
File type: EXE/Windows
File size: 1.59 MB
File name: emvfoundrypos2.exe
ProtectionID:[!] ASProtect SKE v2.72 or higher detected !
[CompilerDetect] -> Borland Delphi (unknown version) - 20% probability
Compilation date: 2010-05-23 09:30:46
First seen: 2021-05-22 21:54:15
Name: POS Simulator 2.0
Screenshot:
Mirror provided by vx-underground.org, thx!
X2.EMV
SHA-256: e420fd7404e6e256f21e1520ba5859c8e0028bf80fe9e85f68e8b3802d012b50 - VT
SHA-1: dda2f30270476fa60a2e646e295ba54e77298aaa
File type: EXE/Windows
File size: 5.94 MB
File name: x2.exe
ProtectionID:[VersionInfo] Version Comments : Modified by an unpaid evaluation copy of Resource Tuner 2
PDB/VBP pathway: g:\dev\_current\smart card reader\NoProtect_bk\Src\X1\Release\X1.pdb
Compilation date: 2015-08-07 18:04:19
First seen: 2021-03-03 11:09:53
Name: X2.EMV
Actor: 717115364
Additional note: From the same family: X1 v1.1, X1 v1.1, X1 Toronto.
Cosmetic reshacks from the 'x2 cartel':
X1 v4.1, X1 v5.0, X2G, X2A, X2A (nfc design), X2A (mr_emv trial), X2A Cracked, X2.
Screenshot:
emvfoundry v1.0.0.54
SHA-256: 9ca464e277596f3bfb99a32cd6db4a3f8e751c0b2805ff05390ee4ecb2fefd36 - VT (FIRST RACE!)
SHA-1: 383474556c4d92d187bcb7b17274ef4f296dc392
File type: EXE/Windows
File size: 42.24 MB
File name: emvsetupfull_1054.exe
ProtectionID:[-= Installer =-] Inno Setup v6.1.0 Module
Compilation date: 2020-11-15 09:48:30
First seen: 2021-05-23 01:14:34
Name: emvfoundry v1.0.0.54
Actor: EmvFoundryOfficialDealer, BC1887, MaggotM
Screenshot:
EMVStudio v1.1.3 cracked
SHA-256: 050847f886f9df20c5d99a1cd2edffa478fedacaa433f7b17139fe66ab7b810a - VT
SHA-1: 8068873fb68b5492c054e9070e4b3fc37e163469
File type: EXE/Windows
File size: 1.43 MB
File name: emvstudio.exe
ProtectionID:[!] [.net scan core] dotNetReactor detected!
[!] [.net scan core] Confuser detected!
Compilation date: 2021-01-12 19:39:42
First seen: 2021-01-13 04:39:43
Name: EMVStudio v1.1.3 cracked ver
Additional note: Same family as: EMVCardIssueSystem, EMVStudio v1.1.1, EMVStudio Trial v1.0, EMVStudio v1.1.3, ARQC TOOL PLUS v1.0, ShadeStudio v1.0, EMVStudio v1.1.2, EMVStudio v1.1.3, EMVStudio v1.1.3
Screenshot:
Daphne
SHA-256: 05dfe50496f27c4bac5fa3676ae4dd679aede5f46fa2475f543c7fbcf2874124 - VT
SHA-1: a92e821b15870cf0bbab459a374e246e5e3e2c19
File type: EXE/Windows
File size: 828.00 KB
File name: daphne.exe
ProtectionID:[CompilerDetect] -> Visual Basic 6 (native)
PDB/VBP pathway: C:\prj\atual\client\prjclient.vbp
Compilation date: 2014-07-02 12:46:03
First seen: 2014-09-04 05:13:08
Name: Daphne
Actor: Prilex
Documentation: https://securelist.com/goodfellas-the-brazilian-carding-scene-is-after-you/84263/
Screenshot:
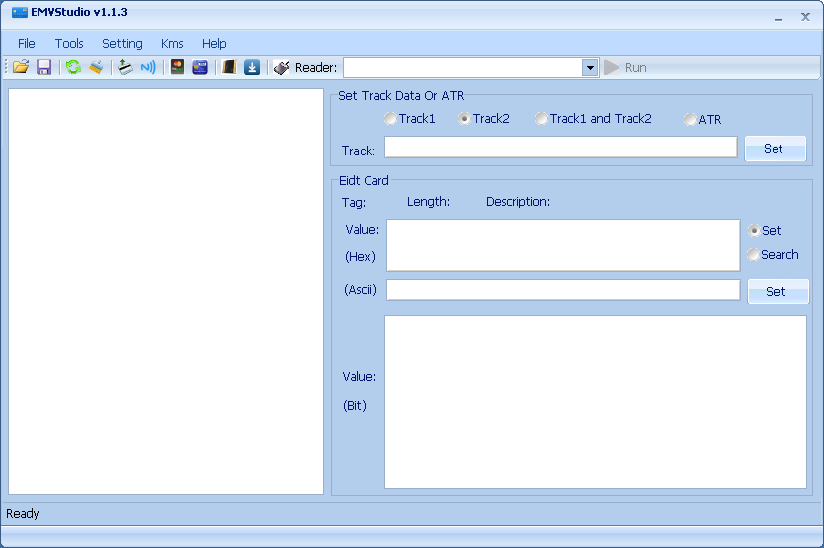
EMVStudio v1.1.3 cracked
SHA-256: 52c89dbef55bd526def42ab9dbb04a2a02dac17cd4b4c0af7177ac61dd8f4297 - VT
SHA-1: 2529e62e314f691b5bed179759b89443a9cd6122
File type: EXE/Windows
File size: 1.83 MB
File name: emvstudio.exe
ProtectionID:[!] [.net scan core] dotNetReactor detected!
[!] [.net scan core] Confuser detected!
Compilation date: 2021-01-06 19:05:29
First seen: 2021-01-13 04:41:10
Name: EMVStudio v1.1.3 cracked ver
Additional note: Same family as: EMVCardIssueSystem, EMVStudio v1.1.1, EMVStudio Trial v1.0, EMVStudio v1.1.3, ARQC TOOL PLUS v1.0, ShadeStudio v1.0, EMVStudio v1.1.2, EMVStudio v1.1.3, EMVStudio v1.1.3
Screenshot:
Emvfoundry v1.0.0.19
SHA-256: 93214d9c664ca7b445a2a841b6112eb853d25109e76a81793f583209e08da03c - VT
SHA-1: 705f5618ffd14c181ddcc0ad8f8f719e0d7810c3
File type: EXE/Windows
File size: 62.58 MB
File name: emvfoundry.exe
ProtectionID:[CompilerDetect] -> Borland Delphi (unknown version) - 60% probability
Compilation date: 2021-03-04 14:40:47
First seen: 2021-03-16 14:19:04
Name: Emvfoundry v1.0.0.19
Actor: mr_emv
Screenshot:

This site is addressed at Malware Analysts/RE/Security people, not to lamers.
If you are curious about how that kind of things work (how they handle smart cards, code similarities, etc..), you have here a list of +100 hashes to beggin your investigations.
There is before each hash a quick link access to their virustotal scan report, and also a hybrid-analysis and any.run link. (HA and AR may return 404 error if they haven't already stumbled across the sample of interest.)
May hopefully someone find one or two useful gems, but i doubt (just my two cents, i already analyzed them and most of theses 'softs' are mostly copycat if not 'ressource hacked' of each others relying on GPShield and a 'macgyver.cap'.
You may want to have a look also on @fboldewin presentation: MacGyver's return - An EMV Chip cloning case.
How can I use the datas ?
As usual our policy is to CC0. the whole content of this website is released under Creative
Common's CC0 1.0. We Believe in OSINT and thinks we can achieve great things by sharing datas.
Feel free to do what you want with the datas and files hosted here.
Can I contribute to eMVTRACKER?
Yes, we are always looking for people who want to share valuable informations
ie: yaras, samples, unpacks, paracetamol, swag, wine and cakes.
If you found a mistake somewhere on eMVTRACKER, or if something need a fix, if you have inquiries or whatever.
Contact: coSnPtaActM@atm.cybercrime-tracker.net (remove all capital letters)
Can I batch download the files?
Yes you can, we have a page here who list all the files.
Hashs, with signature and date can be found here.
Are the dates reliable?
Dates are based on first apparition on a public scanner service: Virus Total (for most.)
We cannot guarantee correctness of the datas being presented and sometime when we thinks the date
presented isn't good, we adjust it manually. Date aren't reliable but at least we try to get them
as accurate as possible.
What is 'FIRST RACE!'?
Some notice may be mentionned with 'FIRST RACE!' on Virscan line, it just indicate that we're
the first to submit the file on VirusTotal, It does not necessarily mean it's something new used
in the wild, but at least it mean this file definitely picked our attention, since somehow it
passed out gate and we're the first to release it.
Now the FAQ for lamers..
Can a EMV Software be used to clone or duplicate cards?
The EMV standard regarding Signed-SDA, DDA and CDA have never been broken.
There are few reasons:
- EMV softwares cannot write accurately card data that varies on every transaction or upon "read".
Such data include ARQC, DDOL, CDA data and other dynamic EMV data.
- EMV softwares cannot write accurately card data for data, that varies upon every transaction.
Good example, is DDA data, which changes or varies, and cannot be static.
Thus, a "cloned" card will never be accepted as anti-fraud systems will detect the DDA, CDA data is static, and marked as invalid.
How are all these videos using blank cards, and withdrawing from ATMs and places ?
The people doing this, are:
1) remove the chip of an actual working EMV card (most of time visa prepaid cards) and put the chip on a white plastic card.
2) remove the paint lamination on a working card, and then use that card on an ATM.
They can be spotted easilly in their 'cashout' videos, contact plate of the emv chip ain't their J2A040.
In reality they are withdrawing from their own prepaid cards that they buy with the cash of their victims.
We are aware of such videos, and when we are bored, we report them.
Suppose example, EMV Software 'X' saves data from one credit card, to another live credit card, is that possible?
No. That is not possible.
All live credit-card systems have anti-tamper systems built into the card.
A request to write data will be, ACCESS_DENIED and result in CARD_LOCKED.
Can EMV Software 'X' be used to code data from "dumps"?
That is not possible.
First, the EMV Standard encodes more data required, such as ICC (a 1400+ bit RSA key) and IPK (another 1400+ bit RSA Key) which cannot be easily duplicated.
Second, as above. The EMV standard DDA and CDA has never been broken.
If someone clones a card, and brings it to a store, would it work?
No, it would not work.
The person would be stopped as the card does not work.
As explained earlier the main feature that prevents fraudulent attacks is the use of dynamic data for each transaction,
so that even if the card data is stolen or intercepted during a transaction, nothing can be done with it.
All dynamic card data can only be used for one individual transaction, and after that, it's useless.
Is there a version of (Software) that works to modify dynamic data in-chip?
No. No such version of software exists at all.
You can't predict the dynamic data: EMV Algorithms have never been hacked nor broken.
Someone told me i need to buy 'X2 2028', it work!
No. no it will not work.
Basically x1 is dead in late 2015, and all the newest versions "x2" are just reshacked versions where scammers
just change pictures and placement of controls (buttons, texts, etc..).
Their mistakes are obvious as the pdb pathway and compilation timestamp are always the same.
It mean they don't even recompile from source, just same old 'X1' file in a new outfit.
Sometime they even do more mistakes like leaving: "Modified by an unpaid evaluation copy of Resource Tuner 2" in file informations.
Hey bro let's make some bread, what's your jabber?
Lmao.
(c) https://emv.cybercrime-tracker.net/
- EMVToolUltimate v1.0
- CATR 3.8.7
- X2 v2.8
- ATRToolUltimate 1.0
- POS Simulator 2.0
- ATRtool v2.0
- EMVToolUltimate v1.2R
- Emvfoundry v1.0.0.63
- POS Simulator 2.0
- X2.EMV
- emvfoundry v1.0.0.54
- EMVStudio v1.1.3 cracked
- Daphne
- EMVStudio v1.1.3 cracked
- Emvfoundry v1.0.0.19
EMV MALWARE NOTiCE
EMVToolUltimate v1.0
SHA-256: 06f40072750772663041e71e3c22b14471894a8433441f41d901095b0393ebfd - VT
SHA-1: ab3e81336b929a0d4f7afbb516580a9dafe523cb
File type: EXE/Windows
File size: 4.70 MB
File name: EMVToolUltimate1.0.exe
ProtectionID:[!] [.net scan core] dotNetReactor detected!
[!] [.net scan core] Confuser detected!
PDB/VBP pathway: c:\MyProjects\gitlab\ILProtector\ILProtector\Output2010\Win32\Release\Protect32.pdb
Compilation date: 2021-06-06 13:07:12
First seen: 2021-06-12 03:26:56
Name: EMVToolUltimate v1.0
Actor: EMVToolsU
Additional note: Seem similar to b3b6085b6706ef90eadba2e48877677d06fa3a6df7c2df5c94773aa7e8b8c1df (ATRToolUltimate 1.0)
Screenshot:
CATR 3.8.7
SHA-256: 81f547c84f90c7a1f9bbba4118e08c41899b40264347d52df73b378f83fab200 - VT (FIRST RACE!)
SHA-1: 9f786b71ca8395c60ad6bb3aa5608c670c01229a
File type: EXE/Windows
File size: 3.50 MB
File name: CATR 2021.exe
ProtectionID:[!] [.net scan core] (smartassembly) DotNet Obfuscator detected!
Compilation date: 2021-08-07 19:35:41
First seen: 2021-10-24 12:05:35
Name: CATR 3.8.7
Screenshot:
X2 v2.8
SHA-256: 63008b67c5cd4e2985c615402b527c48815ec5cb3d5a771c7651f44bb58f906f - VT
SHA-1: 9cdcdd3a3214881c256c3a4c018593dc6ce54340
File type: EXE/Windows
File size: 24.73 MB
File name: x2classics.exe
ProtectionID:[!] ASProtect SKE v2.72 or higher detected !
[CompilerDetect] -> Borland Delphi (unknown version) - 80% probability
Compilation date: 2021-05-03 19:52:06
First seen: 2021-05-22 22:16:40
Name: X2 v2.8
Actor: EmvFoundryOfficialDealer
Screenshot:
ATRToolUltimate 1.0
SHA-256: b3b6085b6706ef90eadba2e48877677d06fa3a6df7c2df5c94773aa7e8b8c1df - VT
SHA-1: 0666fc1169b5a707f0b063cb416995631e64f44a
File type: EXE/Windows
File size: 2.35 MB
File name: ATRToolUltimate1.0.exe
ProtectionID:[!] [.net scan core] dotNetReactor detected!
[!] [.net scan core] Confuser detected!
PDB/VBP pathway: c:\MyProjects\gitlab\ILProtector\ILProtector\Output2010\Win32\Release\Protect32.pdb
Compilation date: 2021-03-17 01:41:00
First seen: 2021-03-17 02:11:08
Name: ATRToolUltimate 1.0
Actor: titusking@criptext.com
Additional note: Seem similar to 06f40072750772663041e71e3c22b14471894a8433441f41d901095b0393ebfd (EMVToolUltimate 1.0)
Screenshot:
POS Simulator 2.0
SHA-256: 0b014dfd75149161109f5aca027e972100104603fca68b4245780ff9b928e1f7 - VT
SHA-1: 1be4659b6c427292912668527bc19729d8c6958e
File type: EXE/Windows
File size: 1.09 MB
File name: EMVTran.EXE
ProtectionID:[!] File appears to have no protection or is using an unknown protection
Compilation date: 2010-05-23 09:30:46
First seen: 2021-08-07 16:26:52
Name: POS Simulator 2.0
Additional note: "EMV Transaction Tool V1.34 Copyright(C) 2005-2009 Raul Xu"
Screenshot:
ATRtool v2.0
SHA-256: 8a3a3358eb344235a7948179bdea5e1f5df26a8dd15762e691cc8b0d3f0a39d8 - VT
SHA-1: 95f31bf0e402d18813abcd29127c22771061de2d
File type: EXE/Windows
File size: 3.11 MB
File name: ATRTool_2.0.exe
ProtectionID:[!] Enigma Protector V 6.80 Build 0 (reserved 0) detected !
[!] Themida/Winlicense detected !
Compilation date: 1992-05-22 21:12:13
First seen: 2021-01-16 23:09:58
Name: ATRtool v2.0
Actor: TitusKing
Screenshot:
EMVToolUltimate v1.2R
SHA-256: 4ac6b9aa216c21322c5fca1da6395da40962d287fc2fc662a0ac5c05be8a79c9 - VT
SHA-1: 311dcf0134acbabed91d289ad01eb0a5e3822a9d
File type: EXE/Windows
File size: 4.70 MB
File name: EMVToolUltimate1.2.exe
ProtectionID:[!] [.net scan core] dotNetReactor detected!
[!] [.net scan core] Confuser detected!
PDB/VBP pathway: c:\MyProjects\gitlab\ILProtector\ILProtector\Output2010\Win32\Release\Protect32.pdb
Compilation date: 2021-07-08 03:46:30
First seen: 2021-07-17 02:36:48
Name: EMVToolUltimate v1.2R
Actor: TitusKing, EMVToolsU
Screenshot:
Emvfoundry v1.0.0.63
SHA-256: 5ccaeb149d0311f9820d40956d36959b8d223ebbda6b3394c683c9a6c6a1ec78 - VT (FIRST RACE!)
SHA-1: edff931d6152c37ade8f1e9165ad8beddf7b8170
File type: EXE/Windows
File size: 43.24 MB
File name: emvsetupfull_1063.exe
ProtectionID:[VersionInfo] Version Comments : This installation was built with Inno Setup.
Compilation date: 2020-11-15 09:48:30
First seen: 2021-06-05 07:34:25
Name: Emvfoundry v1.0.0.63
Actor: EmvFoundryOfficialDealer, BC1887, MaggotM
Screenshot:
POS Simulator 2.0
SHA-256: 8f278185707c7c359dd66569a0b28361131f25aa59f2f7fcd194b6bd8c55884d - VT (FIRST RACE!)
SHA-1: 8c05a70c73eb0da63d511e925d88219f9ae40809
File type: EXE/Windows
File size: 1.59 MB
File name: emvfoundrypos2.exe
ProtectionID:[!] ASProtect SKE v2.72 or higher detected !
[CompilerDetect] -> Borland Delphi (unknown version) - 20% probability
Compilation date: 2010-05-23 09:30:46
First seen: 2021-05-22 21:54:15
Name: POS Simulator 2.0
Screenshot:
Mirror provided by vx-underground.org, thx!
X2.EMV
SHA-256: e420fd7404e6e256f21e1520ba5859c8e0028bf80fe9e85f68e8b3802d012b50 - VT
SHA-1: dda2f30270476fa60a2e646e295ba54e77298aaa
File type: EXE/Windows
File size: 5.94 MB
File name: x2.exe
ProtectionID:[VersionInfo] Version Comments : Modified by an unpaid evaluation copy of Resource Tuner 2
PDB/VBP pathway: g:\dev\_current\smart card reader\NoProtect_bk\Src\X1\Release\X1.pdb
Compilation date: 2015-08-07 18:04:19
First seen: 2021-03-03 11:09:53
Name: X2.EMV
Actor: 717115364
Additional note: From the same family: X1 v1.1, X1 v1.1, X1 Toronto.
Cosmetic reshacks from the 'x2 cartel':
X1 v4.1, X1 v5.0, X2G, X2A, X2A (nfc design), X2A (mr_emv trial), X2A Cracked, X2.
Screenshot:
emvfoundry v1.0.0.54
SHA-256: 9ca464e277596f3bfb99a32cd6db4a3f8e751c0b2805ff05390ee4ecb2fefd36 - VT (FIRST RACE!)
SHA-1: 383474556c4d92d187bcb7b17274ef4f296dc392
File type: EXE/Windows
File size: 42.24 MB
File name: emvsetupfull_1054.exe
ProtectionID:[-= Installer =-] Inno Setup v6.1.0 Module
Compilation date: 2020-11-15 09:48:30
First seen: 2021-05-23 01:14:34
Name: emvfoundry v1.0.0.54
Actor: EmvFoundryOfficialDealer, BC1887, MaggotM
Screenshot:
EMVStudio v1.1.3 cracked
SHA-256: 050847f886f9df20c5d99a1cd2edffa478fedacaa433f7b17139fe66ab7b810a - VT
SHA-1: 8068873fb68b5492c054e9070e4b3fc37e163469
File type: EXE/Windows
File size: 1.43 MB
File name: emvstudio.exe
ProtectionID:[!] [.net scan core] dotNetReactor detected!
[!] [.net scan core] Confuser detected!
Compilation date: 2021-01-12 19:39:42
First seen: 2021-01-13 04:39:43
Name: EMVStudio v1.1.3 cracked ver
Additional note: Same family as: EMVCardIssueSystem, EMVStudio v1.1.1, EMVStudio Trial v1.0, EMVStudio v1.1.3, ARQC TOOL PLUS v1.0, ShadeStudio v1.0, EMVStudio v1.1.2, EMVStudio v1.1.3, EMVStudio v1.1.3
Screenshot:
Daphne
SHA-256: 05dfe50496f27c4bac5fa3676ae4dd679aede5f46fa2475f543c7fbcf2874124 - VT
SHA-1: a92e821b15870cf0bbab459a374e246e5e3e2c19
File type: EXE/Windows
File size: 828.00 KB
File name: daphne.exe
ProtectionID:[CompilerDetect] -> Visual Basic 6 (native)
PDB/VBP pathway: C:\prj\atual\client\prjclient.vbp
Compilation date: 2014-07-02 12:46:03
First seen: 2014-09-04 05:13:08
Name: Daphne
Actor: Prilex
Documentation: https://securelist.com/goodfellas-the-brazilian-carding-scene-is-after-you/84263/
Screenshot:
EMVStudio v1.1.3 cracked
SHA-256: 52c89dbef55bd526def42ab9dbb04a2a02dac17cd4b4c0af7177ac61dd8f4297 - VT
SHA-1: 2529e62e314f691b5bed179759b89443a9cd6122
File type: EXE/Windows
File size: 1.83 MB
File name: emvstudio.exe
ProtectionID:[!] [.net scan core] dotNetReactor detected!
[!] [.net scan core] Confuser detected!
Compilation date: 2021-01-06 19:05:29
First seen: 2021-01-13 04:41:10
Name: EMVStudio v1.1.3 cracked ver
Additional note: Same family as: EMVCardIssueSystem, EMVStudio v1.1.1, EMVStudio Trial v1.0, EMVStudio v1.1.3, ARQC TOOL PLUS v1.0, ShadeStudio v1.0, EMVStudio v1.1.2, EMVStudio v1.1.3, EMVStudio v1.1.3
Screenshot:
Emvfoundry v1.0.0.19
SHA-256: 93214d9c664ca7b445a2a841b6112eb853d25109e76a81793f583209e08da03c - VT
SHA-1: 705f5618ffd14c181ddcc0ad8f8f719e0d7810c3
File type: EXE/Windows
File size: 62.58 MB
File name: emvfoundry.exe
ProtectionID:[CompilerDetect] -> Borland Delphi (unknown version) - 60% probability
Compilation date: 2021-03-04 14:40:47
First seen: 2021-03-16 14:19:04
Name: Emvfoundry v1.0.0.19
Actor: mr_emv
Screenshot:
USAGE / FAQ
Why?This site is addressed at Malware Analysts/RE/Security people, not to lamers.
If you are curious about how that kind of things work (how they handle smart cards, code similarities, etc..), you have here a list of +100 hashes to beggin your investigations.
There is before each hash a quick link access to their virustotal scan report, and also a hybrid-analysis and any.run link. (HA and AR may return 404 error if they haven't already stumbled across the sample of interest.)
May hopefully someone find one or two useful gems, but i doubt (just my two cents, i already analyzed them and most of theses 'softs' are mostly copycat if not 'ressource hacked' of each others relying on GPShield and a 'macgyver.cap'.
You may want to have a look also on @fboldewin presentation: MacGyver's return - An EMV Chip cloning case.
How can I use the datas ?
As usual our policy is to CC0. the whole content of this website is released under Creative
Common's CC0 1.0. We Believe in OSINT and thinks we can achieve great things by sharing datas.
Feel free to do what you want with the datas and files hosted here.
Can I contribute to eMVTRACKER?
Yes, we are always looking for people who want to share valuable informations
ie: yaras, samples, unpacks, paracetamol, swag, wine and cakes.
If you found a mistake somewhere on eMVTRACKER, or if something need a fix, if you have inquiries or whatever.
Contact: coSnPtaActM@atm.cybercrime-tracker.net (remove all capital letters)
Can I batch download the files?
Yes you can, we have a page here who list all the files.
Hashs, with signature and date can be found here.
Are the dates reliable?
Dates are based on first apparition on a public scanner service: Virus Total (for most.)
We cannot guarantee correctness of the datas being presented and sometime when we thinks the date
presented isn't good, we adjust it manually. Date aren't reliable but at least we try to get them
as accurate as possible.
What is 'FIRST RACE!'?
Some notice may be mentionned with 'FIRST RACE!' on Virscan line, it just indicate that we're
the first to submit the file on VirusTotal, It does not necessarily mean it's something new used
in the wild, but at least it mean this file definitely picked our attention, since somehow it
passed out gate and we're the first to release it.
Now the FAQ for lamers..
Can a EMV Software be used to clone or duplicate cards?
The EMV standard regarding Signed-SDA, DDA and CDA have never been broken.
There are few reasons:
- EMV softwares cannot write accurately card data that varies on every transaction or upon "read".
Such data include ARQC, DDOL, CDA data and other dynamic EMV data.
- EMV softwares cannot write accurately card data for data, that varies upon every transaction.
Good example, is DDA data, which changes or varies, and cannot be static.
Thus, a "cloned" card will never be accepted as anti-fraud systems will detect the DDA, CDA data is static, and marked as invalid.
How are all these videos using blank cards, and withdrawing from ATMs and places ?
The people doing this, are:
1) remove the chip of an actual working EMV card (most of time visa prepaid cards) and put the chip on a white plastic card.
2) remove the paint lamination on a working card, and then use that card on an ATM.
They can be spotted easilly in their 'cashout' videos, contact plate of the emv chip ain't their J2A040.
In reality they are withdrawing from their own prepaid cards that they buy with the cash of their victims.
We are aware of such videos, and when we are bored, we report them.
Suppose example, EMV Software 'X' saves data from one credit card, to another live credit card, is that possible?
No. That is not possible.
All live credit-card systems have anti-tamper systems built into the card.
A request to write data will be, ACCESS_DENIED and result in CARD_LOCKED.
Can EMV Software 'X' be used to code data from "dumps"?
That is not possible.
First, the EMV Standard encodes more data required, such as ICC (a 1400+ bit RSA key) and IPK (another 1400+ bit RSA Key) which cannot be easily duplicated.
Second, as above. The EMV standard DDA and CDA has never been broken.
If someone clones a card, and brings it to a store, would it work?
No, it would not work.
The person would be stopped as the card does not work.
As explained earlier the main feature that prevents fraudulent attacks is the use of dynamic data for each transaction,
so that even if the card data is stolen or intercepted during a transaction, nothing can be done with it.
All dynamic card data can only be used for one individual transaction, and after that, it's useless.
Is there a version of (Software) that works to modify dynamic data in-chip?
No. No such version of software exists at all.
You can't predict the dynamic data: EMV Algorithms have never been hacked nor broken.
Someone told me i need to buy 'X2 2028', it work!
No. no it will not work.
Basically x1 is dead in late 2015, and all the newest versions "x2" are just reshacked versions where scammers
just change pictures and placement of controls (buttons, texts, etc..).
Their mistakes are obvious as the pdb pathway and compilation timestamp are always the same.
It mean they don't even recompile from source, just same old 'X1' file in a new outfit.
Sometime they even do more mistakes like leaving: "Modified by an unpaid evaluation copy of Resource Tuner 2" in file informations.
Hey bro let's make some bread, what's your jabber?
Lmao.
(c) https://emv.cybercrime-tracker.net/
Last edited by a moderator:

