Father
Professional
- Messages
- 2,602
- Reaction score
- 786
- Points
- 113
Who were the mysterious "Gods" and "Bignosa", and how did the researchers manage to calculate them?
A recent comprehensive study conducted by Check Point sheds light on the dark side of cyberspace, revealing the activities and identities of attackers using the Agent Tesla malware.
Agent Tesla is an advanced remote access Trojan (RAT) that specializes in stealing and infiltrating confidential information from infected machines. Recently, a campaign of this malware targeting organizations in the US and Australia was discovered, starting on November 7, 2023. Behind the campaign are two cybercriminals, known under the pseudonyms " Bignosa "and" Gods", who use phishing campaigns to spread malware.
With the help of spam mailings with decoys in the form of business offers, attackers distributed Agent Tesla disguised as innocent attachments. During the investigation, Check Point experts were able to track the activity of these attackers and determine that the main one, "Bignosa", is part of a group engaged in malicious campaigns and phishing, and the majority of servers used to distribute Agent Tesla are under the control of this particular group.
Special attention in the Check Point report was paid to the Cassandra Protector tool, which was used to mask malicious code and convert it to ISO images, thus increasing the chances of successful infection of target machines. This tool has anti-virus bypass, emulation functions, and can also register itself in the Windows Task Scheduler to ensure persistence.
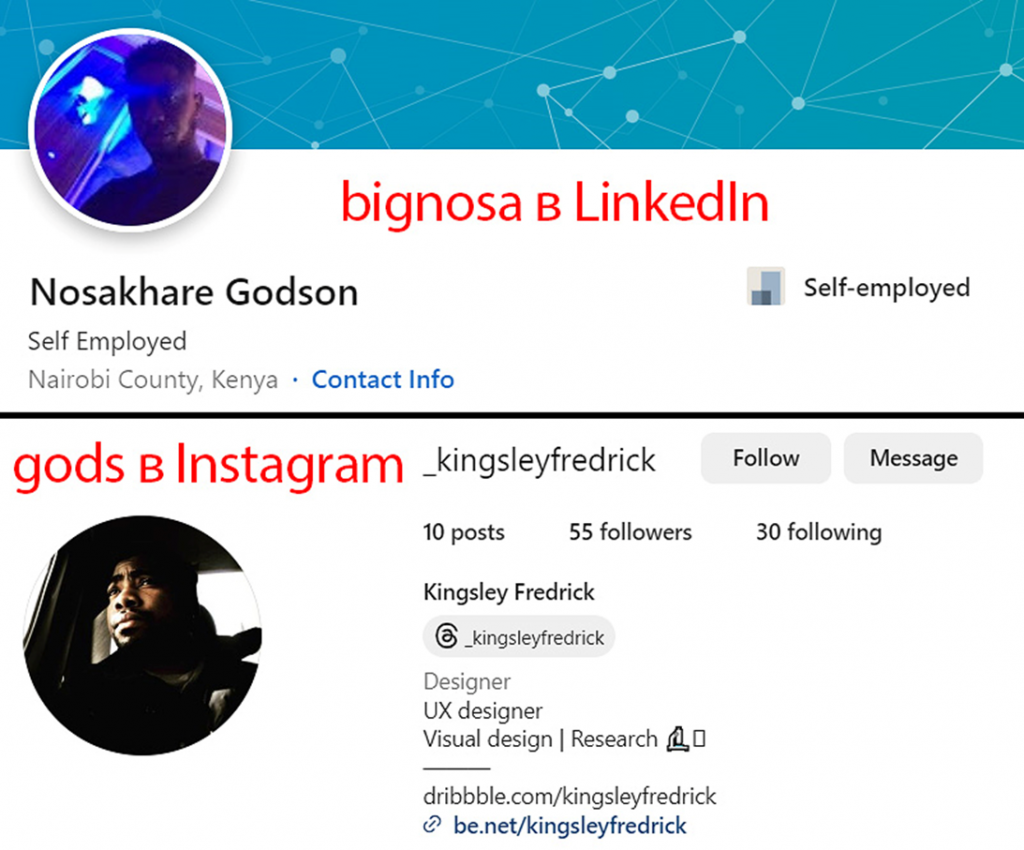
A thorough analysis of information related to Bignosa and Gods, including IP addresses, email addresses, phone numbers, cryptotransactions, and profiles in Jabber, Skype, LinkedIn, and Instagram* that somehow flashed across the Web, helped researchers uncover the real identities of the attackers.
The first, "Bignosa", turned out to be a Kenyan named Nosahare Godson, who has an extensive history of using Agent Tesla and conducting phishing attacks. The second, Kingsley Fredrik, known under the pseudonyms "Gods" and "Kmarshal", is of Nigerian origin, but studied at a Turkish university. The hacker has been linked to phishing and malware campaigns since March 2023. The country of its current location is not known for certain.
Initially, experts considered cooperation between hackers exclusively in the form of a "student-mentor" role model, since "Gods" quite often helped "Bignosa" in setting up Agent Tesla instances, as well as in removing the remnants of infection from the computer after an unintentional launch. However, the more recent results of the study indicate a closer collaboration between the hackers-they acted as a single group.
Thus, the numerous traces left by cybercriminals on the network allowed researchers to reveal their identities, recreate their actions, and also look into their daily activities. As it turns out, even tiny and unimportant pieces of data can sum up the big picture and reveal the truth that attackers would prefer to hide.
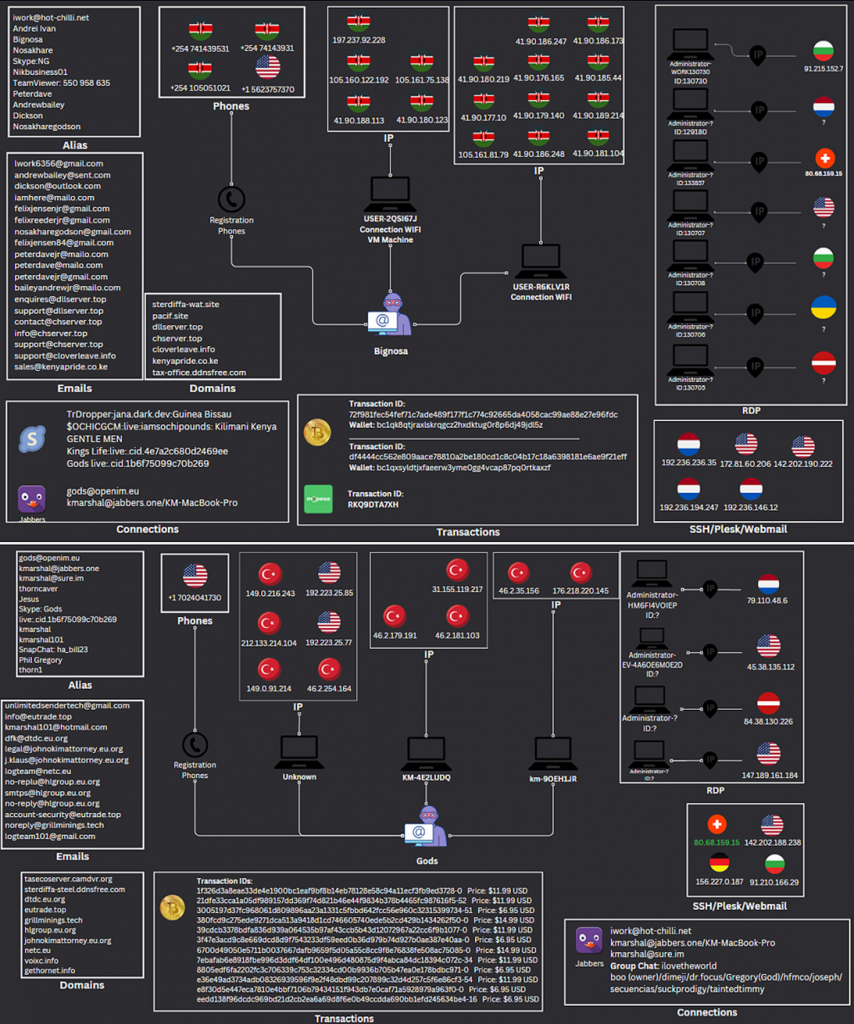
Detailed digital footprint maps for both hackers
Check Point specialists say that they worked closely with law enforcement agencies during their investigation, so it's safe to say that it's only a matter of time before cybercriminals are formally charged, found and arrested.
This study highlights the importance of cybersecurity vigilance and demonstrates how careful analysis of digital footprints can help identify threats.
As for Agent Tesla, in order to minimize the risks of infection with this and similar malware, it is recommended to update your operating systems and applications in a timely manner, be careful with unexpected emails, and increase your awareness of cyber threats.
Check Point will continue to actively monitor the activities of cybercriminals and cooperate with law enforcement agencies to prevent future attacks.
A recent comprehensive study conducted by Check Point sheds light on the dark side of cyberspace, revealing the activities and identities of attackers using the Agent Tesla malware.
Agent Tesla is an advanced remote access Trojan (RAT) that specializes in stealing and infiltrating confidential information from infected machines. Recently, a campaign of this malware targeting organizations in the US and Australia was discovered, starting on November 7, 2023. Behind the campaign are two cybercriminals, known under the pseudonyms " Bignosa "and" Gods", who use phishing campaigns to spread malware.
With the help of spam mailings with decoys in the form of business offers, attackers distributed Agent Tesla disguised as innocent attachments. During the investigation, Check Point experts were able to track the activity of these attackers and determine that the main one, "Bignosa", is part of a group engaged in malicious campaigns and phishing, and the majority of servers used to distribute Agent Tesla are under the control of this particular group.
Special attention in the Check Point report was paid to the Cassandra Protector tool, which was used to mask malicious code and convert it to ISO images, thus increasing the chances of successful infection of target machines. This tool has anti-virus bypass, emulation functions, and can also register itself in the Windows Task Scheduler to ensure persistence.
A thorough analysis of information related to Bignosa and Gods, including IP addresses, email addresses, phone numbers, cryptotransactions, and profiles in Jabber, Skype, LinkedIn, and Instagram* that somehow flashed across the Web, helped researchers uncover the real identities of the attackers.
The first, "Bignosa", turned out to be a Kenyan named Nosahare Godson, who has an extensive history of using Agent Tesla and conducting phishing attacks. The second, Kingsley Fredrik, known under the pseudonyms "Gods" and "Kmarshal", is of Nigerian origin, but studied at a Turkish university. The hacker has been linked to phishing and malware campaigns since March 2023. The country of its current location is not known for certain.

Initially, experts considered cooperation between hackers exclusively in the form of a "student-mentor" role model, since "Gods" quite often helped "Bignosa" in setting up Agent Tesla instances, as well as in removing the remnants of infection from the computer after an unintentional launch. However, the more recent results of the study indicate a closer collaboration between the hackers-they acted as a single group.
Thus, the numerous traces left by cybercriminals on the network allowed researchers to reveal their identities, recreate their actions, and also look into their daily activities. As it turns out, even tiny and unimportant pieces of data can sum up the big picture and reveal the truth that attackers would prefer to hide.

Detailed digital footprint maps for both hackers
Check Point specialists say that they worked closely with law enforcement agencies during their investigation, so it's safe to say that it's only a matter of time before cybercriminals are formally charged, found and arrested.
This study highlights the importance of cybersecurity vigilance and demonstrates how careful analysis of digital footprints can help identify threats.
As for Agent Tesla, in order to minimize the risks of infection with this and similar malware, it is recommended to update your operating systems and applications in a timely manner, be careful with unexpected emails, and increase your awareness of cyber threats.
Check Point will continue to actively monitor the activities of cybercriminals and cooperate with law enforcement agencies to prevent future attacks.
