Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,322
- Points
- 113
ESET reveals details of a new wave of cyber attacks on 3 countries at once.
In May, ESET recorded large-scale phishing campaigns targeting small and medium-sized businesses in Poland, Italy and Romania. As a result of the attacks, several malicious programs were installed on the victims ' devices-Agent Tesla, Formbook, and Remcos RAT.
Attackers used already compromised email accounts and company servers to distribute malicious emails, as well as to host and collect stolen data. The campaign included 9 waves of attacks that used the DBatLoader malware loader (ModiLoader and NatsoLoader) to deliver malware.
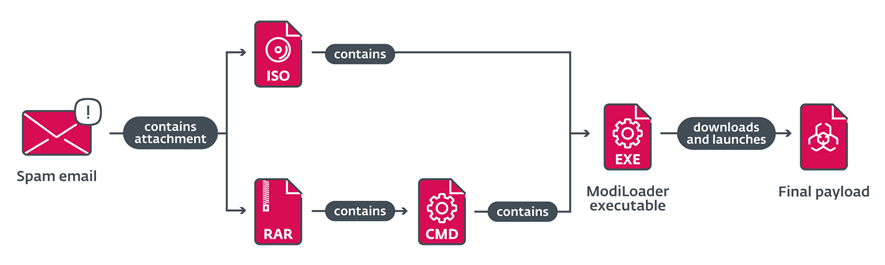
Infection chain
The initial point of the attacks was phishing emails with attachments in RAR or ISO format containing malicious files. When opening attachments, a multi-step process of downloading and activating Trojans was started.
In cases where ISO files were attached, the content was the ModiLoader executable file (named the same or the same as the name of the ISO file itself), which was launched when the executable file was opened.
In cases where RAR files were attached, the contents of the archives were a highly convoluted batch script (with the same name as the archive) with the extension ". cmd". The file also contained a Base64-encoded ModiLoader executable file disguised as a PEM certificate revocation list. The batch script is responsible for decoding and running the built-in ModiLoader.
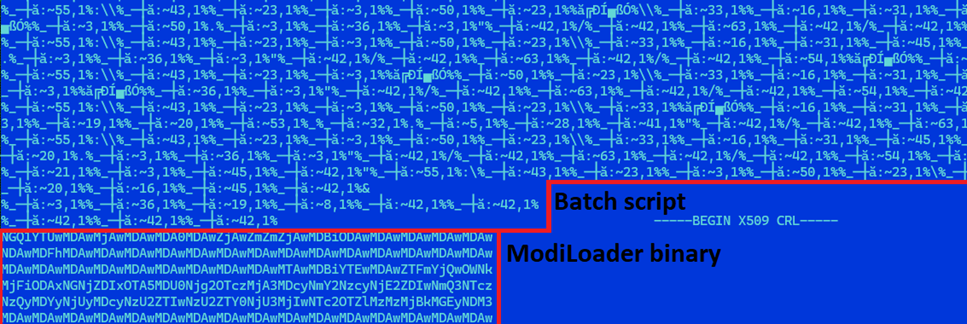
The CMD file contains an obfuscated batch script that decodes the ModiLoader binary file in Base64 encoding
DBatLoader, developed on the basis of Delphi, is designed to download and run next-stage malware from Microsoft OneDrive or from compromised company servers. Regardless of the type of malware installed, Agent Tesla, Formbook and Remcos RAT have the ability to steal confidential information, including from browsers and email clients, which allows attackers to prepare the ground for subsequent attacks.
Source
In May, ESET recorded large-scale phishing campaigns targeting small and medium-sized businesses in Poland, Italy and Romania. As a result of the attacks, several malicious programs were installed on the victims ' devices-Agent Tesla, Formbook, and Remcos RAT.
Attackers used already compromised email accounts and company servers to distribute malicious emails, as well as to host and collect stolen data. The campaign included 9 waves of attacks that used the DBatLoader malware loader (ModiLoader and NatsoLoader) to deliver malware.

Infection chain
The initial point of the attacks was phishing emails with attachments in RAR or ISO format containing malicious files. When opening attachments, a multi-step process of downloading and activating Trojans was started.
In cases where ISO files were attached, the content was the ModiLoader executable file (named the same or the same as the name of the ISO file itself), which was launched when the executable file was opened.
In cases where RAR files were attached, the contents of the archives were a highly convoluted batch script (with the same name as the archive) with the extension ". cmd". The file also contained a Base64-encoded ModiLoader executable file disguised as a PEM certificate revocation list. The batch script is responsible for decoding and running the built-in ModiLoader.

The CMD file contains an obfuscated batch script that decodes the ModiLoader binary file in Base64 encoding
DBatLoader, developed on the basis of Delphi, is designed to download and run next-stage malware from Microsoft OneDrive or from compromised company servers. Regardless of the type of malware installed, Agent Tesla, Formbook and Remcos RAT have the ability to steal confidential information, including from browsers and email clients, which allows attackers to prepare the ground for subsequent attacks.
Source

