Kickass Torrents was once one of the most popular torrent indexing platforms in the world. Even years after its shutdown, users still search for Kickass Torrents alternatives, proxy sites, and ways to access torrent content safely.
In 2026, many torrent websites are blocked, unstable, or unsafe due to
copyright enforcement,
ISP restrictions, and
malicious mirror sites. This article lists the
10 best Kickass Torrents alternatives in 2026, focusing on sites that are still accessible, relatively safe, and widely trusted by the torrent community.
We’ll also explain why Kickass Torrents is blocked, what risks users should be aware of, and how to access torrent sites more securely.
What Is Kickass Torrents and Why Is It Blocked?
Kickass Torrents (KAT) used to be one of the biggest torrent sites around, with everything from movies and TV shows to software and games. Because so much copyrighted content was shared there, it quickly became a major target for copyright enforcement.
Eventually, the original Kickass Torrents domain was taken down, and many ISPs started blocking access to it. Since then, a lot of fake KAT mirror and proxy sites have popped up. Some of these look convincing but are packed with malware, phishing attempts, or aggressive ads.
If you’re still trying to figure out how to access Kickass Torrents safely, you can also check out this guide:
How to Safely Access Kickass Torrents in 2026 (Unblocked & Secure Guide)
That said, because of the risks involved, most users today prefer using stable and safer Kickass Torrents alternatives rather than relying on unofficial mirrors or proxies.
Best 10 Kickass Torrents Alternatives in 2026
Over the past few weeks, I tested dozens of torrent sites to find the most reliable Kickass Torrents alternatives in 2026.
Below are the Kickass Torrents alternative sites that actually work, load properly in most regions, and have active seeders, even when Kickass Torrents is blocked or restricted by ISPs.
1. The Pirate Bay — Best Overall Kickass Torrents Alternative
Website:
The Pirate Bay is still the closest thing to the original Kickass Torrents experience. It has one of the largest torrent libraries on the internet and works as a go-to Kickass Torrents alternative in most countries.
What I personally like most is the
trusted uploader system. Uploaders with a skull icon are usually reliable, and during my tests I consistently found torrents with thousands of seeders, resulting in very fast downloads.
Pros:
· Massive library across all categories
· Trusted uploader system (skull icon)
· Fewer pop-up ads than most competitors
· Very fast downloads for popular torrents
Cons:
· Blocked in many regions, may require a VPN or proxy
2. 1337x — Great for Movies and TV
Website:
1337x has become one of the most popular Kickass Torrents alternatives 2026, especially for movies and TV shows. I like how clean and organized the site feels compared to older trackers.
The trending section is genuinely useful, and
the category filters make it easy to browse Oscar winners, documentaries, anime, or TV series.
Pros:
· Clean interface with minimal ads
· Well-organized categories
· Trending and Top 100 sections
· Reliable for mainstream content
Cons:
· Smaller library than The Pirate Bay
3. YTS — Best for HD Movies
Website:
YTS is hands-down the best Kickass Torrents alternative site for movie lovers. It specializes in
high-quality movie torrents with
much smaller file sizes than other sites.
I tested several 1080p and 4K downloads, and the quality-to-size ratio is excellent, perfect if you have
limited storage or
slower internet.
Pros:
· Movie-only focus (no clutter)
· 720p, 1080p, and 4K options
· Very small file sizes
· Beautiful, easy-to-use interface
Cons:
· Movies only, no TV or software
4. EZTV — Best for TV Shows
Website:
EZTV is ideal if you mainly download TV series. New episodes usually appear within hours of airing.
The interface looks outdated, but it loads fast and has fewer annoying ads than many other Kickass Torrents alternative sites.
Pros:
· TV-focused library
· Fast episode uploads
· Simple layout with few pop-ups
Cons:
· Outdated UI
· Not great for discovering new content
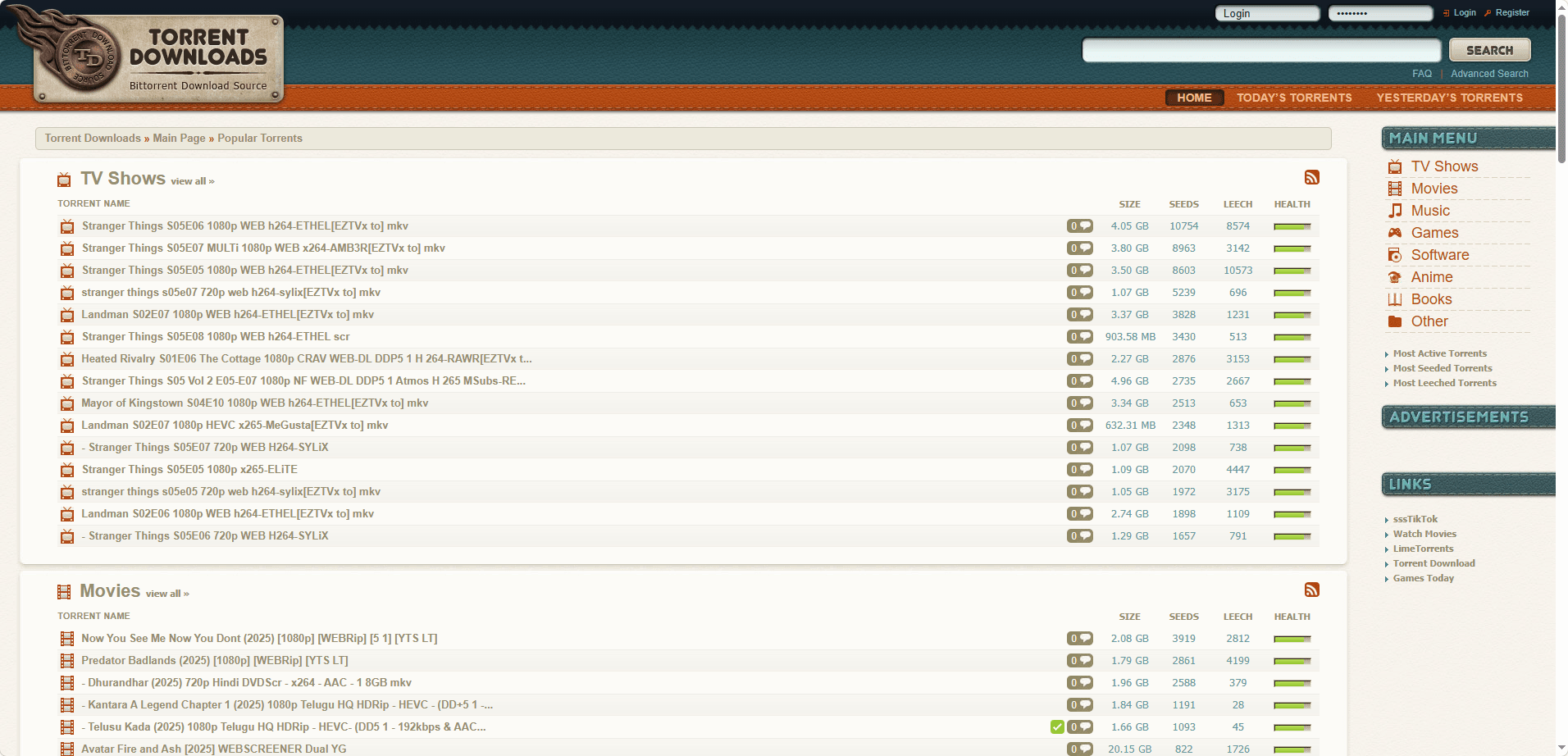
5. TorrentDownloads — Good for Rare Content
Website:
TorrentDownloads is surprisingly useful for finding
obscure or older files: rare books, niche software, or less popular games.
It does show more ads than others, but most are limited to sidebars and don’t interrupt browsing.
Pros:
· Large archive of rare content
· Good search and category system
· Trending section on homepage
Cons:
· More ads than top competitors
· Some torrents have low seed counts
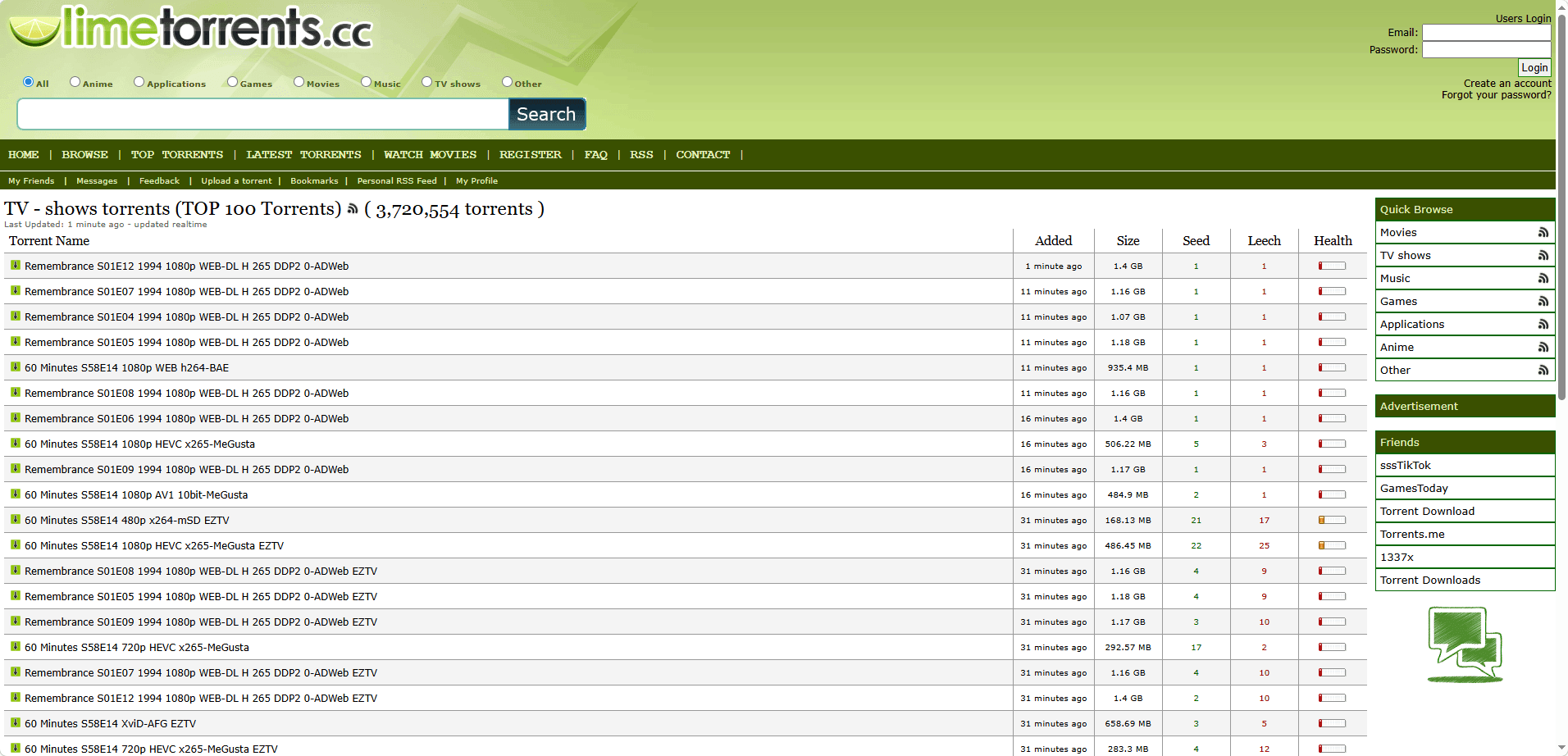
6. LimeTorrents — Good for New Releases
Website:
LimeTorrents is one of the most
beginner-friendly Kickass Torrents alternatives. I particularly like the
health bar next to each torrent, which gives a quick visual indicator of speed and reliability.
Pros:
· Health bar for each torrent
· Clean and simple layout
· Good for new movie and game releases
Cons:
· Occasional fake or dead torrents
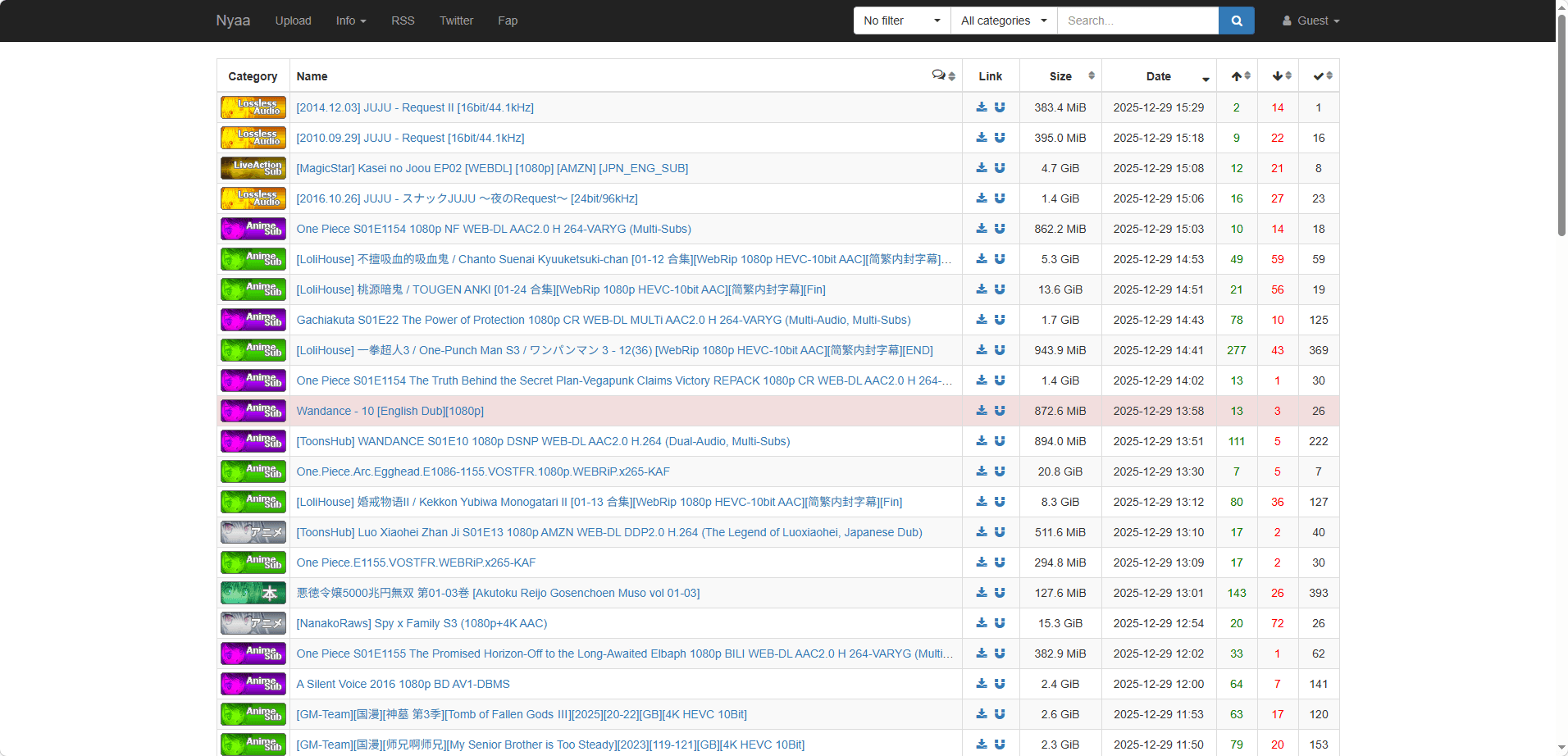
7. Nyaa — Best for Anime
Website:
Nyaa is unbeatable for
anime. It has a massive library of anime series, movies, and manga with strong community support.
Pros:
· Anime-focused content
· Language and subtitle filters
· Active seeders even for old releases
Cons:
· Limited outside
anime niche
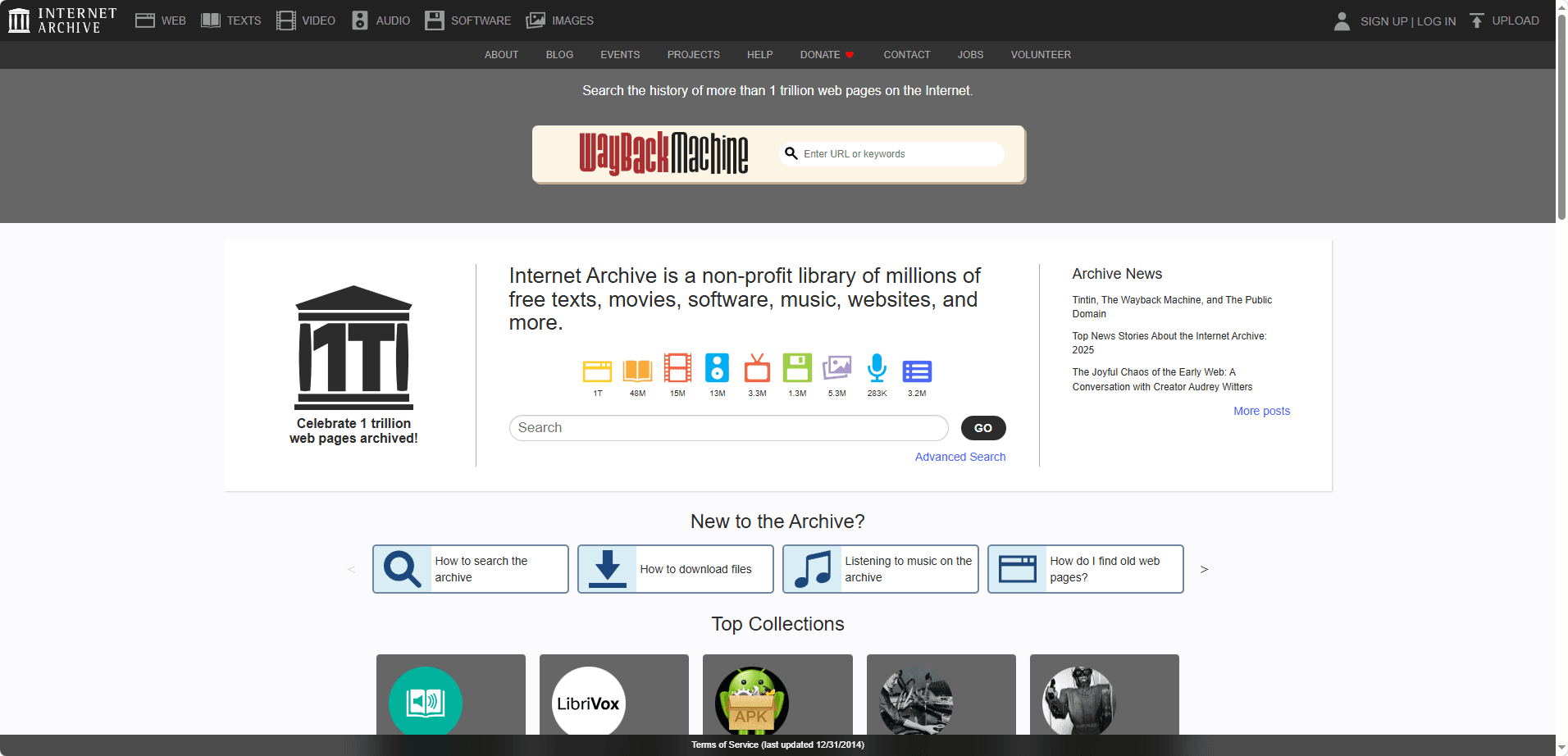
8. Internet Archive — Best Legal Option
Website:
If you want a
completely legal torrenting experience, Internet Archive is the best option. It offers public-domain movies, books, music, and software.
Pros:
· 100% legal torrents
· Massive library
· Well-organized categories
· No malware risk
Cons:
· No copyrighted modern content
9. FitGirl Repacks — Best for Gamers
Website:
FitGirl Repacks is my top Kickass Torrents alternative site for
PC games. The compression is incredible:
large games download much faster,
saving bandwidth and storage.
Pros:
· Highly compressed game repacks
· Detailed installation guides
· Active gaming community
Cons:
· Installation takes longer due to decompression
10. TorrentGalaxy — Visual & Curated Kickass Torrents Alternative
Website:
TorrentGalaxy has become one of my favorite Kickass Torrents alternatives in 2026, especially when I’m looking for movies and visually browsing new releases. Unlike older torrent sites that only show text links,
TorrentGalaxy uses posters and preview images, which makes discovering new content much easier.
Pros:
· Visual, modern interface with posters and previews
· Good curation of movies, TV, and popular releases
· Active and trusted uploader community
· One of the more user-friendly Kickass Torrents alternative sites
Cons:
· Smaller library than The Pirate Bay or 1337x
· Some mirror sites can be unstable or slow depending on region
How to Access Torrent Sites More Securely
Even when using well-known Kickass Torrents alternative sites, there are still basic risks, especially in regions where torrent platforms are blocked or monitored.
Most security issues come from
fake mirror sites,
aggressive ads, and
tracking scripts rather than from the torrent files themselves. To reduce these risks, a few simple habits are usually enough:
Stick to trusted Kickass Torrents alternatives, check seed counts and user comments before downloading, and
avoid clicking on misleading “download” buttons outside the main torrent or magnet links.
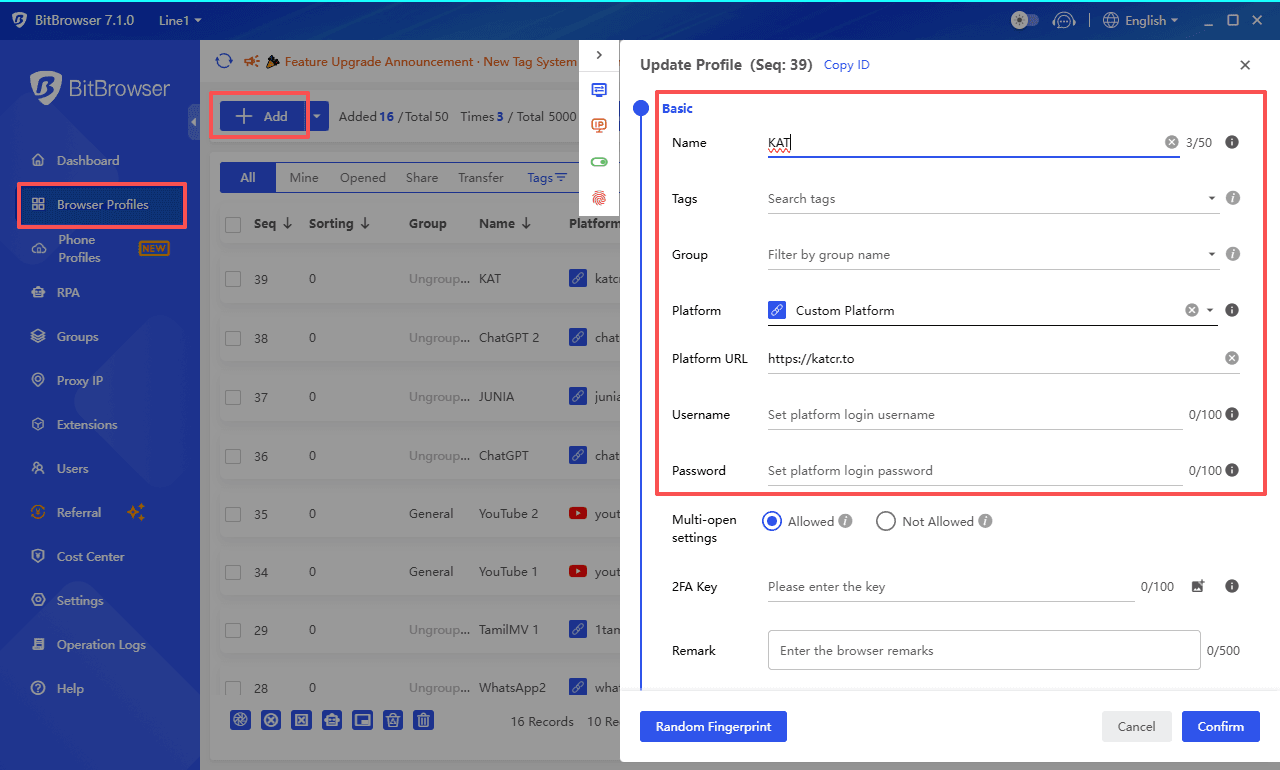
For privacy and isolation, separating torrent browsing from everyday online activity is highly recommended. While VPNs help encrypt traffic, an
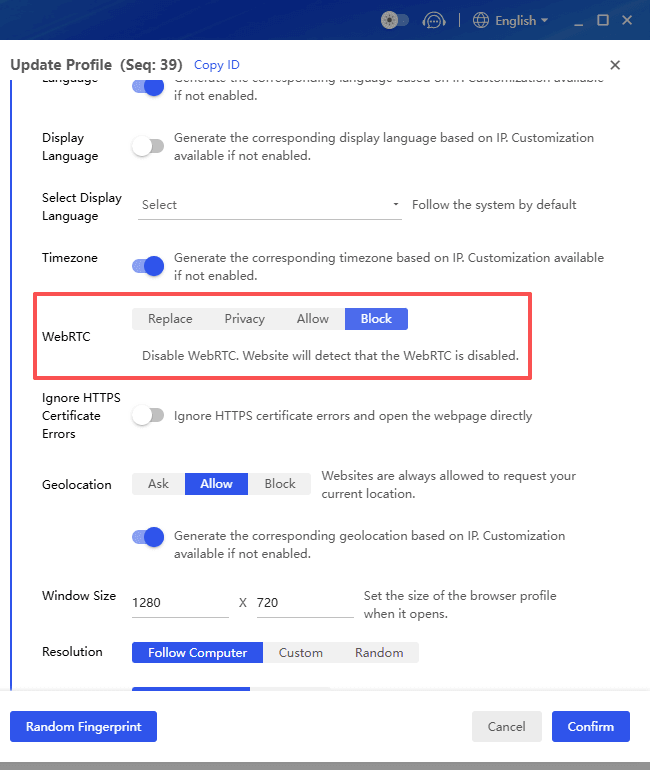
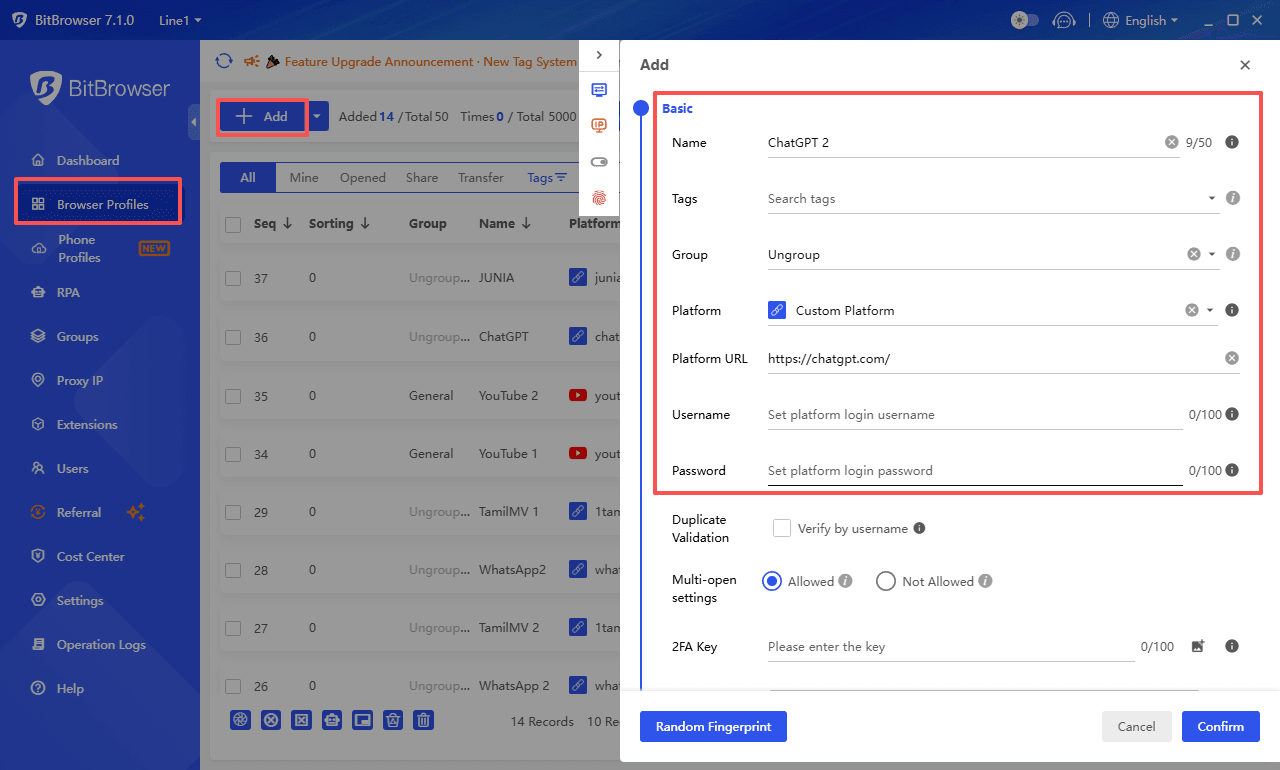
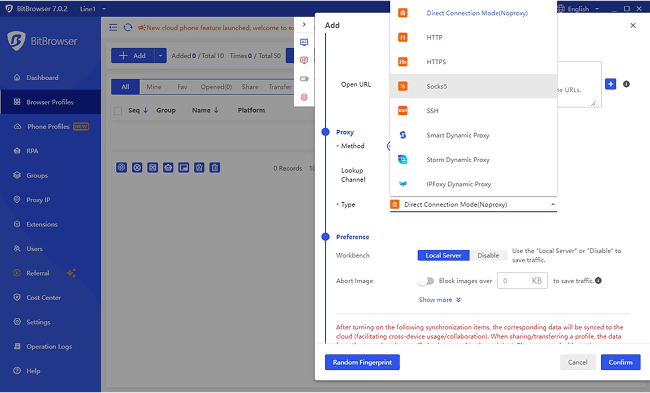
anti-detect browser like
BitBrowser adds another layer by isolating browser fingerprints, cookies, and local storage across sessions. This makes it harder for trackers, ad networks, and blocked platforms to link torrent activity to personal or work accounts.
Try BitBrowser's 10 permanent free personal profiles and enjoy nearly all core features.
Finally, keeping antivirus protection and an ad-blocker enabled helps prevent malicious redirects and unwanted software.
These simple steps are usually sufficient to browse and download torrents more safely and responsibly in 2026.
Legal Disclaimer
Torrenting laws vary by country and region. Some content available on torrent platforms may be protected by copyright, and downloading or sharing such material may be illegal in certain jurisdictions.
This article is for informational purposes only and does not encourage or promote copyright infringement. Users are responsible for ensuring that their activities comply with local laws and regulations and should only download or share content they have the legal right to access.
Always check your local regulations before using torrent sites or downloading any files.
Conclusion
Kickass Torrents may no longer be available in its original form, but there are still many stable, active, and trusted Kickass Torrents alternatives in 2026.
From large general-purpose torrent indexes like
The Pirate Bay and 1337x, to
niche-focused platforms such as YTS for movies, EZTV for TV shows, Nyaa for anime, and
FitGirl Repacks for games, users can still find reliable options depending on their needs.
The key is
choosing well-known alternative sites,
avoiding suspicious mirrors, and
using basic security and privacy tools when accessing torrent platforms, especially in regions where torrent sites are restricted or closely monitored.
With the right habits and tools, it is still possible to access torrent content safely, responsibly, and efficiently in 2026.
You might need:
A Step-by-Step Guide to Safely Accessing Kickass Torrents in 2026.
Frequently Asked Questions (FAQ)
1. Are Kickass Torrents alternatives legal to use?
Torrent sites themselves are not illegal in most countries, but the legality depends on the content being downloaded or shared.
Some torrents contain copyrighted material, and downloading or distributing such content may violate local laws. Users should only download content they have the legal right to access and should always check local regulations before using torrent platforms.
2. Why is Kickass Torrents blocked in so many countries?
Kickass Torrents was blocked primarily due to large-scale copyright enforcement actions and legal pressure from content owners.
As a result, many internet service providers now block access to torrent domains, including Kickass Torrents and its mirrors, which is why users often turn to Kickass Torrents alternative sites or proxy domains.
3. What is the safest way to use Kickass Torrents alternative sites in 2026?
The safest approach is to use well-known, trusted torrent sites, avoid unofficial or suspicious mirrors, and pay attention to seed counts, user comments, and uploader reputations.
Using a VPN for traffic encryption and a privacy-focused browser setup, such as isolating torrent sessions with
an anti-detect browser like BitBrowser, can further reduce tracking, fingerprinting, and exposure to malicious ads or fake sites.