BitBrowser Anti - Detect
Professional
- Messages
- 374
- Reaction score
- 4
- Points
- 18
As a popular short video platform in the world, TikTok users often encounter the problem of "Hot videos list is empty", which not only affects the content browsing experience, but also may hinder the account traffic of cross-border operations. This article will analyze the common causes of this problem and provide efficient solutions. At the same time, combined with the functions of Bit Cloud Phone, it will explore how it can become the preferred tool for cross-border practitioners.
Ⅰ. Common reasons for TikTok's "Hot List is Empty"
Network environment restrictions: TikTok has strict restrictions on regional access. If the device IP is identified as an uncommon area, it may trigger platform risk control, resulting in content failure to load.
Account abnormality or association risk: The same device frequently switches accounts or logs in to multiple accounts, which is easy to be judged as "non-real users", thereby limiting functions.
Application cache or version problems: Local cache accumulation or failure to update the application version in time may cause page loading abnormalities.
Device fingerprint is marked: Virtualized environments (such as traditional cloud phones) are easily detected as "non-real devices" by TikTok, resulting in traffic reduction or even account closure.
Ⅱ. Targeted solutions of Bit Cloud Phone
To address the above problems, Bit Cloud Phone, with its core technology advantages, provides a complete set of response strategies:
1. Simulate the real device environment to bypass geographical restrictions
Bit Cloud Phone automatically matches the language, time zone, operator and other parameters corresponding to the IP through real mobile phone chip simulation. For example, when using a US IP, the system will simultaneously generate an English interface, Los Angeles time zone and AT&T operator information to avoid being intercepted by the platform due to "virtualization characteristics". Users only need to configure the Socks5 proxy IP with one click to stably access TikTok's global content and solve the blank list caused by IP problems.2. Independent management of multiple accounts to avoid associated risks
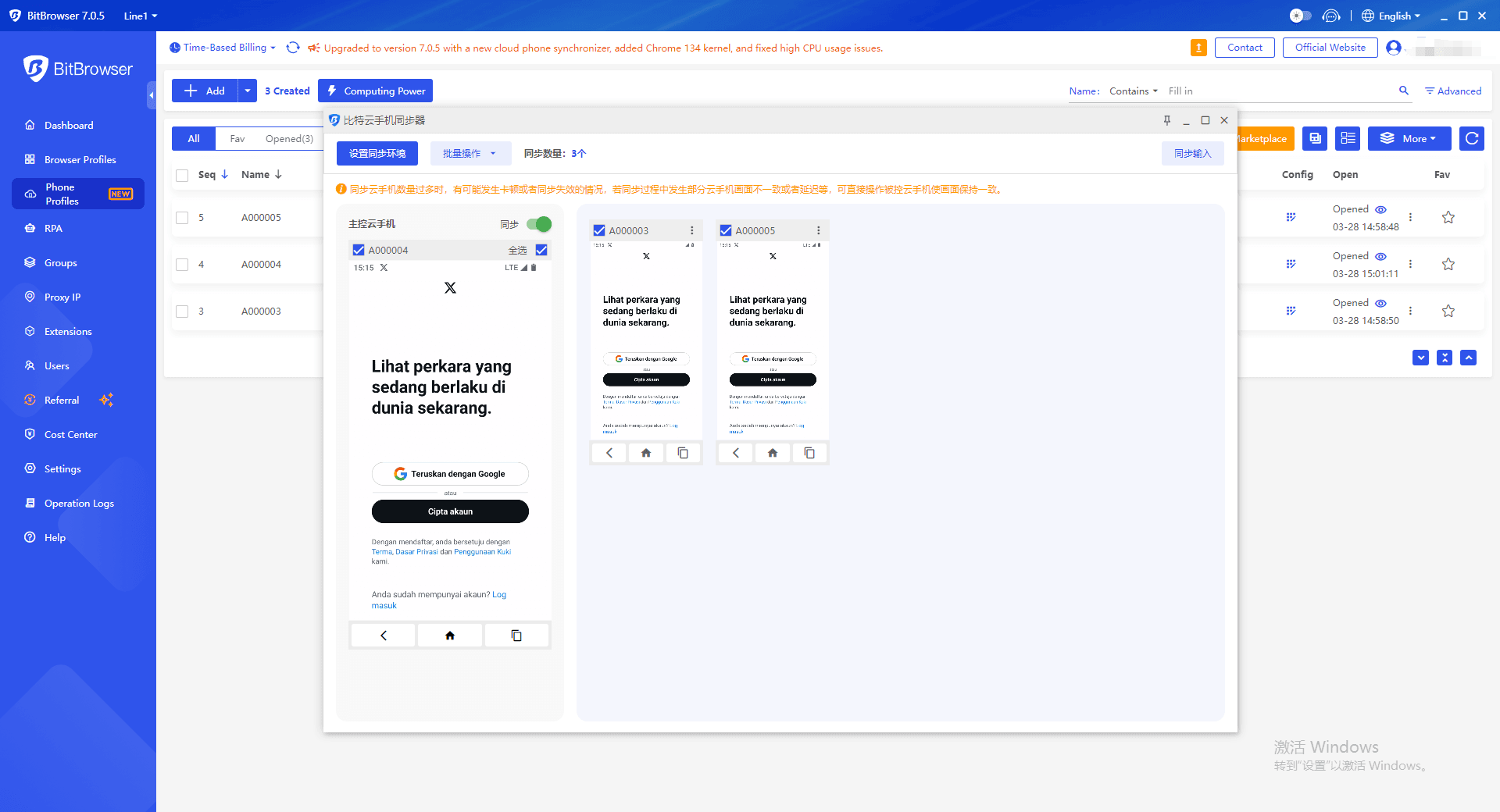
Traditional mobile phones are prone to triggering risk control when logging in to multiple accounts on the same device, while Bit Cloud Phone supports independent operation of multiple environments. Each environment has independent device fingerprints, IP and storage space, which is equivalent to "one real machine with ten devices". For example, users can operate TikTok accounts in the United States and Southeast Asia at the same time without frequently switching VPNs to avoid account abnormalities due to IP jumping.3. One-click cache cleanup and quick application update
Bit Cloud Phone provides cloud storage management function. Users can directly clean TikTok cache or uninstall old versions of apps in the cloud, and download the latest version of TikTok through the built-in Google Play Store to ensure application compatibility. In addition, all operations do not occupy local mobile phone memory to avoid loading failures due to insufficient storage.4. Real device parameters + dynamic risk control confrontation
Unlike ordinary virtual machines, Bit Cloud Phone ensures the authenticity of device fingerprints by simulating 600+ operator information and sensor data (such as gyroscopes and GPS tracks). For example, the system automatically generates corresponding SIM card information based on the proxy IP, and simulates real-person operation intervals (such as sliding speed ±300ms) through the AI behavior engine, effectively avoiding TikTok's "quantum matrix detection" algorithm.Ⅲ. Why recommend Bit Cloud Phone?
Cost-effective: The hourly billing mode (0.16 yuan/24 hours) supports unlimited creation of environments, saving 90% of hardware costs compared to purchasing multiple real machines.
Easy to operate: supports batch import of environments, synchronizer group control and ADB script customization, such as automatically refreshing TikTok hot pages through scripts to improve operation and maintenance efficiency.
Safety and compliance: provides sub-account permission management function, enterprises can dynamically allocate employee operation permissions to avoid account resource abuse.
Create an overseas environment: select "Computing Power B (Overseas Network)" in Bit Cloud Phone, configure Socks5 proxy and detect IP availability.
Install TikTok: Download the latest version through the built-in application market to avoid compatibility issues.
Optimize account behavior: enable the "AI behavior simulation" function, set a random sliding interval, and simulate real user activity.
Regularly change the environment: use the "one-click new machine" function to reset device parameters and keep the account safe.
Behind the "blank hot list" problem of TikTok, there is often a game between the device environment and the platform's risk control. Bit Cloud Phone has become a "breakthrough weapon" for cross-border operators with its real device simulation, multi-account isolation and dynamic risk control confrontation capabilities. Whether you are an individual creator or a corporate team, you can achieve efficient and secure global content operations through its flexible function configuration.
Experience Bit Cloud Phone now, click [Official Website Link] to download, new users can also receive 5 yuan experience money, start your TikTok global traffic journey!