Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,095
- Points
- 113
How the good old GTA IV served as bait to disguise a new virus.
Researchers from Cado Security have discovered a new piece of malware targeting users of the macOS operating system. Dubbed the 'Cthulhu Stealer', this malware is designed to collect a wide range of data from Apple devices, highlighting the growing activity of cybercriminals targeting this platform.
The Cthulhu Stealer has been distributed since late 2023 in a malware-as-a-service (MaaS) model with a price tag of $500 per month. It is capable of running on both x86_64 and Arm architectures. The malware is disguised as legitimate software, including popular applications such as CleanMyMac and even the video game Grand Theft Auto IV.
The main danger is that users who decide to run an unsigned file are forced to bypass Gatekeeper's protection and enter the system password.
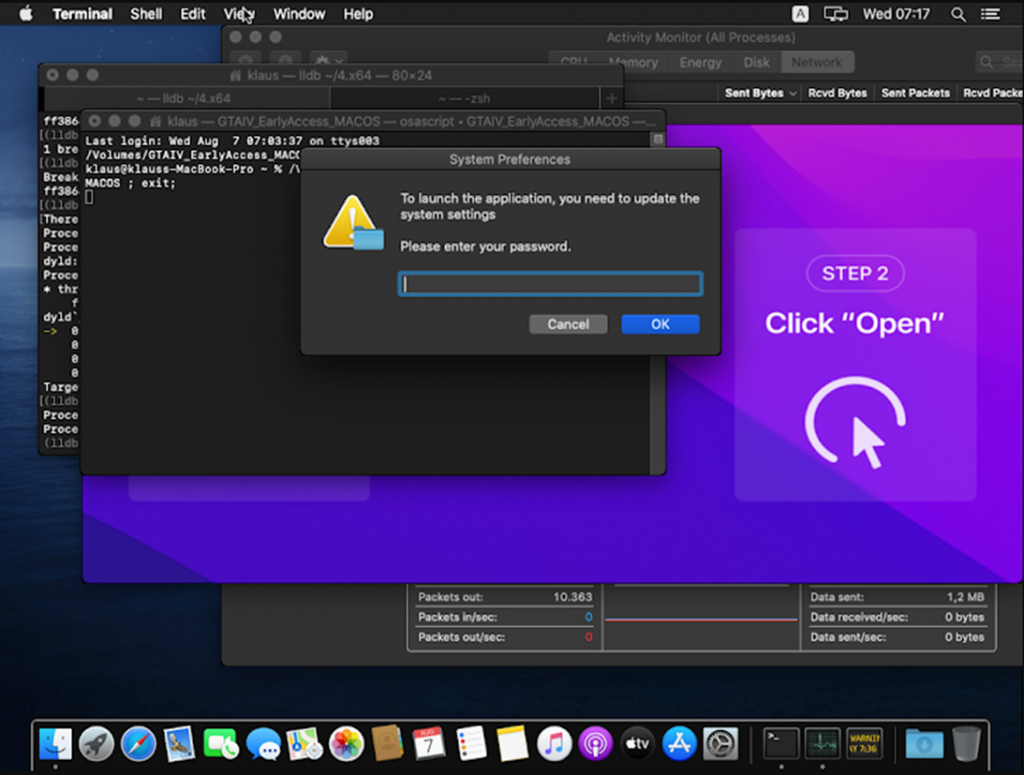
The malware can also ask for the password from MetaMask, making it particularly dangerous for cryptocurrency wallet owners. The Cthulhu Stealer collects system information and extracts passwords from iCloud Keychain using the Chainbreaker open source tool.
The collected data, including web browser cookies and Telegram account information, is compressed into an archive and sent to the attackers' server. The main goal of this malware is to steal credentials and cryptocurrency wallets, as well as game accounts.
According to Cado Security, the functions of the Cthulhu Stealer are similar in many ways to another well-known malware, the Atomic Stealer. It is likely that the developer of the Cthulhu Stealer took the code of the Atomic Stealer as a basis and made changes to it.
At the moment, the threat actors behind the development of the Cthulhu Stealer have ceased their activities. Internal conflicts and disputes over payments led to accusations of fraud and the fact that the main developer was permanently banned from the cybercriminal market, where this software was promoted.
Although the Cthulhu Stealer is not very complex or has unique features, its existence underscores the increased interest in the macOS platform among cybercriminals. Users are advised to download programs only from trusted sources, avoid installing unverified applications, and update systems regularly.
Apple has also paid attention to the growth of threats to macOS and recently announced security improvements in the next version of the operating system. For example, in macOS Sequoia, users will no longer be able to bypass Gatekeeper protection through Control-click to run unsigned software.
Instead, you will need to go to "System Settings" and manually allow suspicious programs to run, which can prevent inexperienced users from accidentally infecting their macOS device.
Source
Researchers from Cado Security have discovered a new piece of malware targeting users of the macOS operating system. Dubbed the 'Cthulhu Stealer', this malware is designed to collect a wide range of data from Apple devices, highlighting the growing activity of cybercriminals targeting this platform.
The Cthulhu Stealer has been distributed since late 2023 in a malware-as-a-service (MaaS) model with a price tag of $500 per month. It is capable of running on both x86_64 and Arm architectures. The malware is disguised as legitimate software, including popular applications such as CleanMyMac and even the video game Grand Theft Auto IV.
The main danger is that users who decide to run an unsigned file are forced to bypass Gatekeeper's protection and enter the system password.

The malware can also ask for the password from MetaMask, making it particularly dangerous for cryptocurrency wallet owners. The Cthulhu Stealer collects system information and extracts passwords from iCloud Keychain using the Chainbreaker open source tool.
The collected data, including web browser cookies and Telegram account information, is compressed into an archive and sent to the attackers' server. The main goal of this malware is to steal credentials and cryptocurrency wallets, as well as game accounts.
According to Cado Security, the functions of the Cthulhu Stealer are similar in many ways to another well-known malware, the Atomic Stealer. It is likely that the developer of the Cthulhu Stealer took the code of the Atomic Stealer as a basis and made changes to it.
At the moment, the threat actors behind the development of the Cthulhu Stealer have ceased their activities. Internal conflicts and disputes over payments led to accusations of fraud and the fact that the main developer was permanently banned from the cybercriminal market, where this software was promoted.
Although the Cthulhu Stealer is not very complex or has unique features, its existence underscores the increased interest in the macOS platform among cybercriminals. Users are advised to download programs only from trusted sources, avoid installing unverified applications, and update systems regularly.
Apple has also paid attention to the growth of threats to macOS and recently announced security improvements in the next version of the operating system. For example, in macOS Sequoia, users will no longer be able to bypass Gatekeeper protection through Control-click to run unsigned software.
Instead, you will need to go to "System Settings" and manually allow suspicious programs to run, which can prevent inexperienced users from accidentally infecting their macOS device.
Source

