Carding
Professional
- Messages
- 2,870
- Reaction score
- 2,494
- Points
- 113
Telekopye is not just a Telegram bot, but a whole criminal hierarchy.
A new financially motivated group of attackers is using a malicious Telegram bot for fraud.
The set of tools, called Telekopye (from Telegram and kopye), functions as an automated tool for creating phishing web pages based on a ready-made template that mimic legitimate sites for entering payment data. The bot automatically generates phishing pages and sends links to potential victims, which criminals call "Mammoths".
According to ESET, the first versions of Telekopye appeared back in 2015, that is, the tool has been actively developed and used for many years. The exact origin of the intruders, called "Neanderthals" (Neanderthals), is unknown. However, hackers use the Russian language in SMS messages sent to victims and target popular Russian marketplaces.
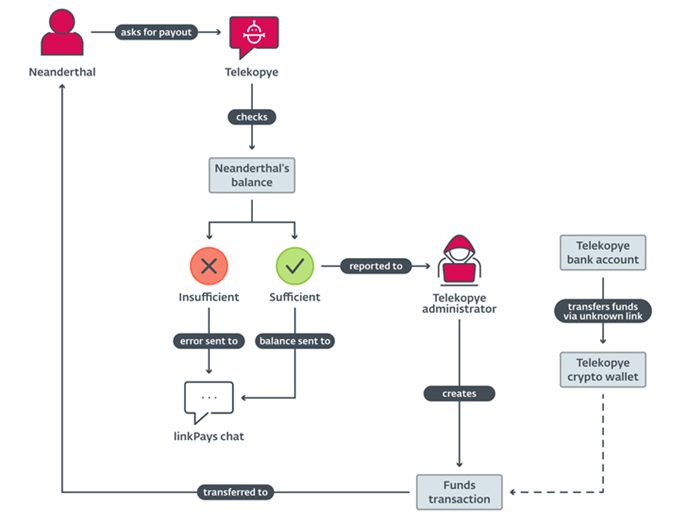
Telekopye operation structure
The Telekopye group has a hierarchy by user level, which shows a high degree of organization of the criminal group:
The attack scheme is as follows: Neanderthals find Mammoths and gain their trust, and then send the victims a fake link generated using Telekopye, by mail, SMS or in private messages in social networks.
As soon as the victim enters payment details on the phishing page, the data is used to steal funds, which are then laundered through cryptocurrency. Telekopye administration receives a percentage of each successful attack.
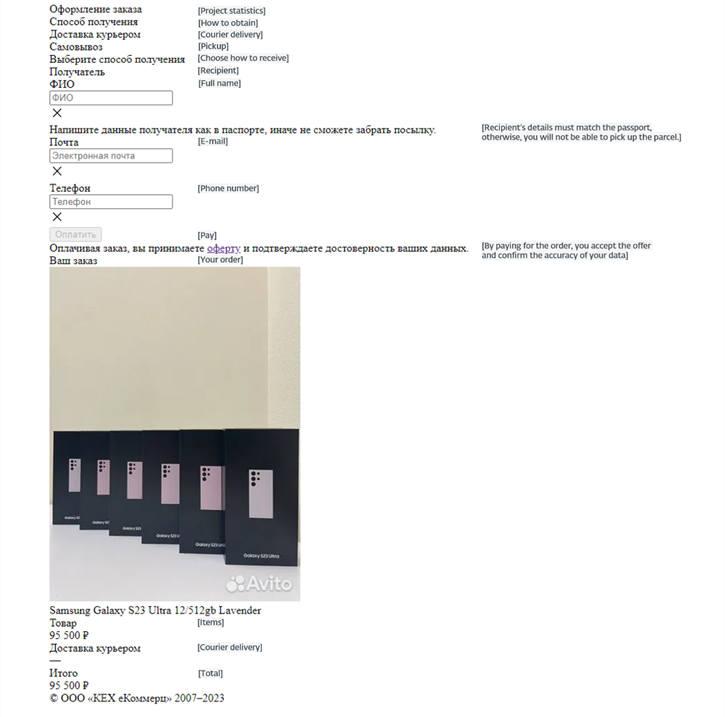
Example of a phishing page template
A distinctive feature of the campaign is a centralized payment system. Instead of transferring the stolen funds to their accounts, Neanderthals send them to a shared account controlled by the Telekopye administrator, which allows you to monitor the actions of each fraudster.
To protect against attacks, we recommend using strong passwords, two-factor authentication (2FA), and antivirus programs. ESET also recommends that you always insist on a face-to-face meeting when buying with your hands and not send money to strangers.
Earlier, ESET specialists discovered a malicious tool kit called Spacecolon, which is used to distribute variants of the Scarab ransomware around the world. According to the study, Spacecolon penetrates organizations ' systems by exploiting web server vulnerabilities (such as Zerologon) or using brute-force methods to attack RDP (Remote Desktop Protocol) credentials.
In addition, the ESET team in August revealed a large-scale phishing campaign aimed at customers of the popular Zimbra email service, which spread to hundreds of organizations in more than 10 countries around the world. Despite the primitiveness of the scheme used, the attackers managed to send targeted emails under the guise of notifications from Zimbra to hundreds of users of the collaboration software. The emails contained malicious attachments that were directed to the victim's phishing login page.
A new financially motivated group of attackers is using a malicious Telegram bot for fraud.
The set of tools, called Telekopye (from Telegram and kopye), functions as an automated tool for creating phishing web pages based on a ready-made template that mimic legitimate sites for entering payment data. The bot automatically generates phishing pages and sends links to potential victims, which criminals call "Mammoths".
According to ESET, the first versions of Telekopye appeared back in 2015, that is, the tool has been actively developed and used for many years. The exact origin of the intruders, called "Neanderthals" (Neanderthals), is unknown. However, hackers use the Russian language in SMS messages sent to victims and target popular Russian marketplaces.

Telekopye operation structure
The Telekopye group has a hierarchy by user level, which shows a high degree of organization of the criminal group:
- administrators – users with the highest privileges who can add phishing web page templates and change payout rates;
- moderators – users who can raise or lower the level of other participants, as well as approve new participants, but cannot change the settings of the toolkit;
- rank-and-file workers – a common role assigned to all new Neanderthals;
- good employees – increased employee role with higher pay and lower commission;
- blocked users – users who are prohibited from using Telekopye for possible violation of the project's rules;
The attack scheme is as follows: Neanderthals find Mammoths and gain their trust, and then send the victims a fake link generated using Telekopye, by mail, SMS or in private messages in social networks.
As soon as the victim enters payment details on the phishing page, the data is used to steal funds, which are then laundered through cryptocurrency. Telekopye administration receives a percentage of each successful attack.

Example of a phishing page template
A distinctive feature of the campaign is a centralized payment system. Instead of transferring the stolen funds to their accounts, Neanderthals send them to a shared account controlled by the Telekopye administrator, which allows you to monitor the actions of each fraudster.
To protect against attacks, we recommend using strong passwords, two-factor authentication (2FA), and antivirus programs. ESET also recommends that you always insist on a face-to-face meeting when buying with your hands and not send money to strangers.
Earlier, ESET specialists discovered a malicious tool kit called Spacecolon, which is used to distribute variants of the Scarab ransomware around the world. According to the study, Spacecolon penetrates organizations ' systems by exploiting web server vulnerabilities (such as Zerologon) or using brute-force methods to attack RDP (Remote Desktop Protocol) credentials.
In addition, the ESET team in August revealed a large-scale phishing campaign aimed at customers of the popular Zimbra email service, which spread to hundreds of organizations in more than 10 countries around the world. Despite the primitiveness of the scheme used, the attackers managed to send targeted emails under the guise of notifications from Zimbra to hundreds of users of the collaboration software. The emails contained malicious attachments that were directed to the victim's phishing login page.

