Hacker
Professional
- Messages
- 1,041
- Reaction score
- 852
- Points
- 113
Of course, we are not talking about your conversations, but it is quite possible to find out about your place of residence, work, and travel, since mobile devices are able to report their previous connections. You probably didn't know about this.
How does this happen ? To connect to existing networks that do not notify you of their presence, any mobile device has to send test packets to detect the networks they know. These packets can be intercepted when the gadget is turned on or disconnected from the network. This is done using the usual tools — airodump / tcpdump. For example:
# airodump-ng -w wifi-dump wlan0# tcpdump -n -l -e -r wifi-dump.cap | grep ‘Probe Request ([^)]‘
The output indicates the time, MAC address of the device, and network name. Another example:
16:32:26.628209 BSSID:ff:ff:ff:ff:ff:ff DA:ff:ff:ff:ff:ff:ff SA:50:ea:d6:aa:bb:cc Probe Request (SUBWAY) [1.0 2.0 5.5 11.0 Mbit]
This means that the device is 50: ea:d6:aa:bb: cc needed to check if the SUBWAY network was within reach.
It would seem that what difference does it make whether your gadget emits such packets with network names or not ? There is, however, one caveat, namely, the presence of unique names for most local networks. SUBWAY-type names are widely used, but in a large number of homes, networks receive either automatically created names based on the ProviderNameDEADBEEF principle, or the names are set by users themselves.
Thus, the list of trial packages will usually contain the following network names:
For home users: ProviderNameXXXXX, StreetNameWifi, etc.;
for workers: Company, CompanyCity, etc.;
for cafes, restaurants, bars, etc.: standard;
for hotels: the names will be unique, except for chain hotels.
Thus, if someone intercepts such a trial packet, they will be able to find out what kind of provider you have and where you usually eat, although without any BSSID, coordinates, etc.
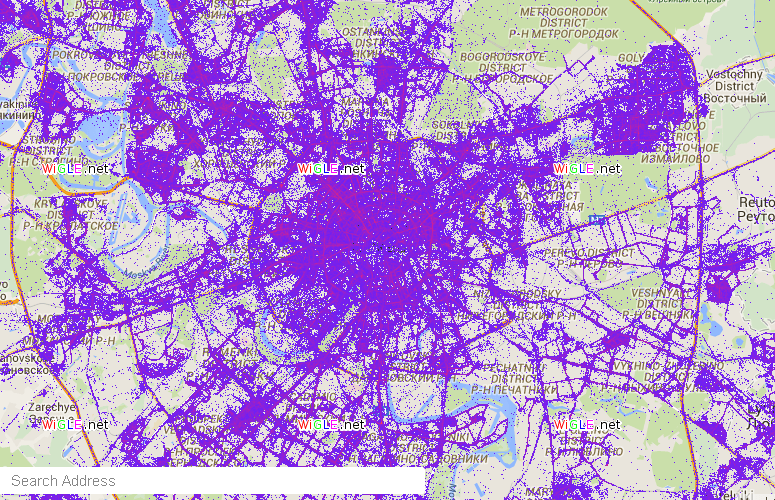
It seems to be nothing terrible, if not for WiGLE, which stands for " engine for recording information about wireless networks." The motto of this service is "All networks that all people find", and with its help you can actually find most of the city's networks by their name.
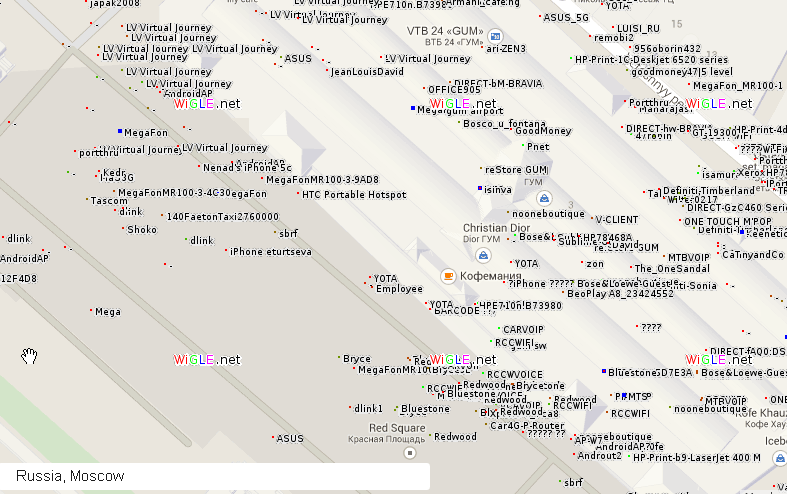
Now let's talk about how you can collect information based on the list of networks. Take a look at the map with its icons – results downloaded from the wiggle library.
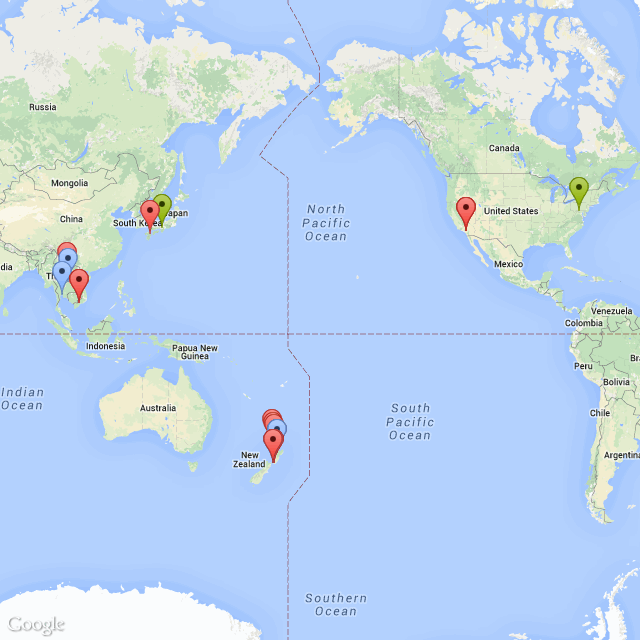
The networks are designated as follows:
red – open;
green – encrypted;
blue – unknown.
Each marker points to a specific building.
What can I find out about the owner of this mobile device ? Most likely, he lives in the eastern United States, often goes to Japan, as evidenced by the token of an encrypted corporate network, and goes on vacation to Thailand (this is indicated by networks with hotel names) or to New Zealand (here networks with the name of campsites). You can use the name of the corporate network to find out what the company is called.
Impressive? But is it possible to find this particular person based on this data alone? You can, because the MAC address contains information about the gadget model.
So are there any ways to hide your data somehow ? Experienced people suggest setting up wpa_supplicant networks on Linux, specifying scan_ssid=0. With this setup, trial packages will not be sent. You can also turn Wi-Fi on and off as needed, or give your home network some common name, but you still won't be able to completely disguise yourself.
How does this happen ? To connect to existing networks that do not notify you of their presence, any mobile device has to send test packets to detect the networks they know. These packets can be intercepted when the gadget is turned on or disconnected from the network. This is done using the usual tools — airodump / tcpdump. For example:
# airodump-ng -w wifi-dump wlan0# tcpdump -n -l -e -r wifi-dump.cap | grep ‘Probe Request ([^)]‘
The output indicates the time, MAC address of the device, and network name. Another example:
16:32:26.628209 BSSID:ff:ff:ff:ff:ff:ff DA:ff:ff:ff:ff:ff:ff SA:50:ea:d6:aa:bb:cc Probe Request (SUBWAY) [1.0 2.0 5.5 11.0 Mbit]
This means that the device is 50: ea:d6:aa:bb: cc needed to check if the SUBWAY network was within reach.

It would seem that what difference does it make whether your gadget emits such packets with network names or not ? There is, however, one caveat, namely, the presence of unique names for most local networks. SUBWAY-type names are widely used, but in a large number of homes, networks receive either automatically created names based on the ProviderNameDEADBEEF principle, or the names are set by users themselves.
Thus, the list of trial packages will usually contain the following network names:
For home users: ProviderNameXXXXX, StreetNameWifi, etc.;
for workers: Company, CompanyCity, etc.;
for cafes, restaurants, bars, etc.: standard;
for hotels: the names will be unique, except for chain hotels.
Thus, if someone intercepts such a trial packet, they will be able to find out what kind of provider you have and where you usually eat, although without any BSSID, coordinates, etc.

It seems to be nothing terrible, if not for WiGLE, which stands for " engine for recording information about wireless networks." The motto of this service is "All networks that all people find", and with its help you can actually find most of the city's networks by their name.
Now let's talk about how you can collect information based on the list of networks. Take a look at the map with its icons – results downloaded from the wiggle library.

The networks are designated as follows:
red – open;
green – encrypted;
blue – unknown.
Each marker points to a specific building.
What can I find out about the owner of this mobile device ? Most likely, he lives in the eastern United States, often goes to Japan, as evidenced by the token of an encrypted corporate network, and goes on vacation to Thailand (this is indicated by networks with hotel names) or to New Zealand (here networks with the name of campsites). You can use the name of the corporate network to find out what the company is called.
Impressive? But is it possible to find this particular person based on this data alone? You can, because the MAC address contains information about the gadget model.
So are there any ways to hide your data somehow ? Experienced people suggest setting up wpa_supplicant networks on Linux, specifying scan_ssid=0. With this setup, trial packages will not be sent. You can also turn Wi-Fi on and off as needed, or give your home network some common name, but you still won't be able to completely disguise yourself.

