Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,322
- Points
- 113
Experts have revealed a scheme of espionage attacks on domestic businesses.
In July 2024, F. A. C. C. T. Threat Intelligence specialists identified new attacks by the XDSpy cyber espionage group targeting Russian companies.
XDSpy uses phishing emails to send links to download RAR archives containing legitimate executable files (. exe) and malicious libraries (msi.dll). Attackers use the DLL SideLoading technique to activate malware. The main threat comes from a library that downloads and runs additional malware called XDSpy. DSDownloader.
The main target of the attacks was a Russian IT company specializing in the development of software for cash registers. An organization from Tiraspol, Transnistria, could also be a likely victim, since one of the archives was uploaded to VirusTotal from this particular location.
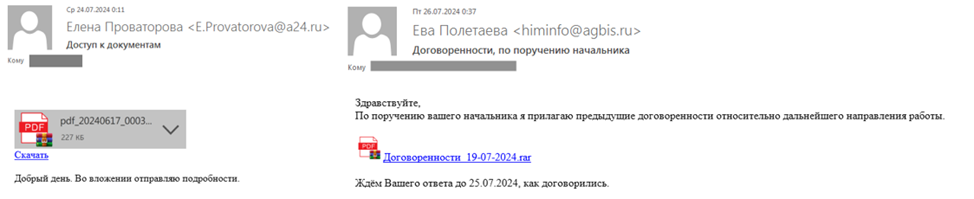
Attackers forged the addresses of the senders of phishing emails. For example, one of the emails with the subject "Access to documents" contained a link to an archive with malware. A second email was soon sent to the same target organization with the subject line "Arrangements made on behalf of the chief".
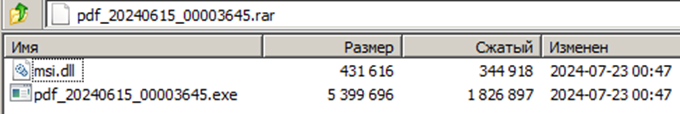
The RAR archive contained two executable files in the PE32+ format: a legitimate executable file pdf_20240615_00003645.exe and a malicious library msi.dll, which was loaded when the legitimate file was launched.
The malicious library XDSpy. DSDownloader is responsible for loading and running the payload file, using various methods to pin it to the system.
Key features of XDSpy. DSDownloader include:
XDSpy targets Russian enterprises in the military, financial, and government sectors, as well as mining, research, and energy organizations. Despite the long-term efforts of specialists from different countries, it is still unclear in whose interests this hacker group operates.
Source
In July 2024, F. A. C. C. T. Threat Intelligence specialists identified new attacks by the XDSpy cyber espionage group targeting Russian companies.
XDSpy uses phishing emails to send links to download RAR archives containing legitimate executable files (. exe) and malicious libraries (msi.dll). Attackers use the DLL SideLoading technique to activate malware. The main threat comes from a library that downloads and runs additional malware called XDSpy. DSDownloader.
The main target of the attacks was a Russian IT company specializing in the development of software for cash registers. An organization from Tiraspol, Transnistria, could also be a likely victim, since one of the archives was uploaded to VirusTotal from this particular location.
Attackers forged the addresses of the senders of phishing emails. For example, one of the emails with the subject "Access to documents" contained a link to an archive with malware. A second email was soon sent to the same target organization with the subject line "Arrangements made on behalf of the chief".

The RAR archive contained two executable files in the PE32+ format: a legitimate executable file pdf_20240615_00003645.exe and a malicious library msi.dll, which was loaded when the legitimate file was launched.

The malicious library XDSpy. DSDownloader is responsible for loading and running the payload file, using various methods to pin it to the system.
Key features of XDSpy. DSDownloader include:
- Extracting a decoy document and saving it in a user directory, then opening it to distract the victim's attention.
- Copying it msi.dll and a legitimate executable file in the directory "C:\Users\Public".
- Creating a registry key for malware startup at system startup.
- Downloading a payload file from the attackers ' server and saving it under a random name in "C:\Users\Public".
- Launching the uploaded payload file.
XDSpy targets Russian enterprises in the military, financial, and government sectors, as well as mining, research, and energy organizations. Despite the long-term efforts of specialists from different countries, it is still unclear in whose interests this hacker group operates.
Source

