Man
Professional
- Messages
- 3,221
- Reaction score
- 1,185
- Points
- 113
Guide to Analyzing Network Traffic with Wireshark
1. What is Wireshark?

Program logo
Wireshark is a widely used tool for capturing and analyzing network traffic, which is actively used both for educational purposes and for troubleshooting a computer or network. Wireshark works with almost all OSI model protocols, has an interface that is understandable for the average user and a convenient data filtering system. In addition to all this, the program is cross-platform and supports the following operating systems: Windows, Linux, Mac OS X, Solaris, FreeBSD, NetBSD, OpenBSD.
In this guide, we will look at the basic functionality of the Wireshark program, relate it to the OSI model, learn how to analyze network traffic and secure your presence on the global Internet.
2. How to install Wireshark?
First, we need to download and install the Wireshark program. Since the program is distributed under the GNU GPL v2 license (i.e. it can be freely distributed), it is easy to find any version of the program in the public domain. In this guide, we will use the functionality of an earlier version of the program (1.12.3). This is due to the fact that this version has the SSL protocol built in, which is used in Chapter 6. Installing an earlier version makes it easier to get started with the program, so we chose it. You can find the installer on the official website.Further installation of the program is simple – click “Next” - “Next” - “Next”.
Installing the program
After successful installation, a Wireshark shortcut will appear on your desktop. We can begin to examine the functionality!

Program shortcut on the desktop
3. How to use Wireshark?
One of the main features of the program is to capture network traffic. Therefore, first you need to learn how to capture your network traffic.Let's launch the program! We are immediately greeted by the start menu, where you can see the computer interfaces available for capture, instructions from the program developers and many other interesting things.
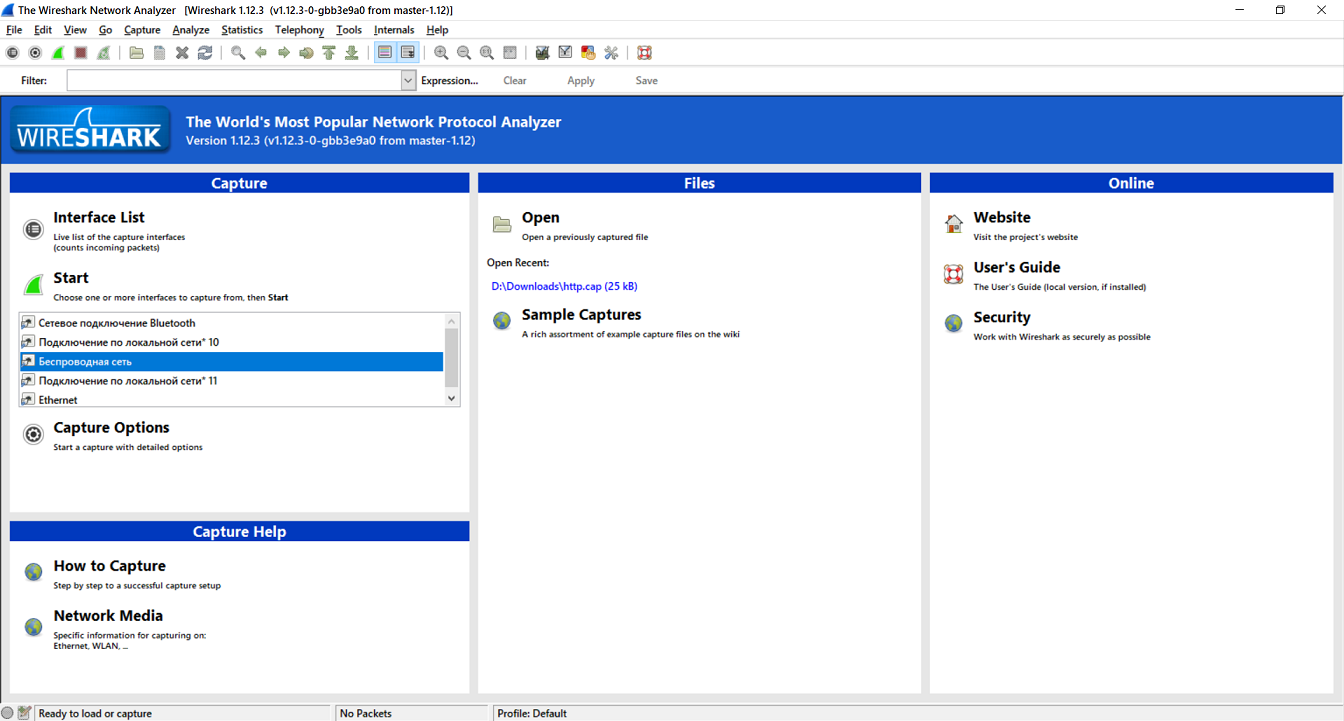
Start menu
From all of this, we need to pay attention to this area of the program.
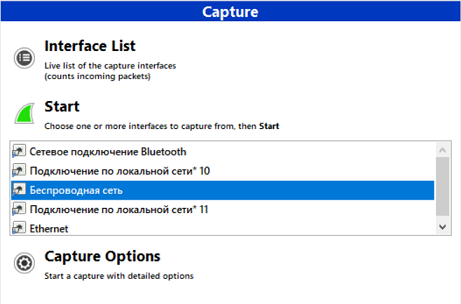
Network Interface Traffic Capture Scope
Here you need to select the network interface through which you are connected to the Internet.
The network interface is software that interacts with the network driver and the IP layer. It provides the IP layer with access to all available network adapters whose traffic we will intercept. The most common network interfaces in the Wireshark program are wireless (Wi-Fi) and cable (Ethernet).
The tutorial uses Wi-Fi, so we will perform a capture of "Wireless Network" and then click "Start".
If you have selected the correct interface, you will be able to see the following.
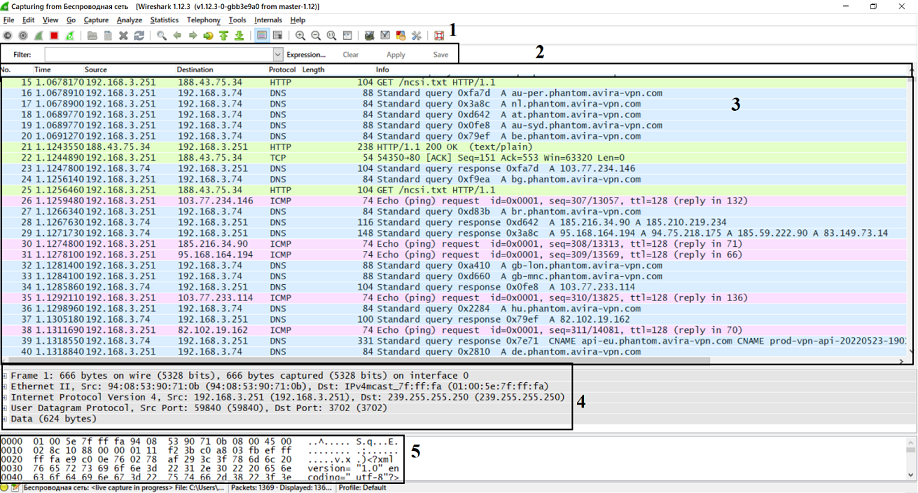
Overview of the beginning of traffic capture
Let's take a closer look at this window, based on the items listed on it:
- The filter panel, which allows you to find the information you need. More information about it is provided in Chapter 5 of the guide.
- The name panel, which separates the information from point 3 into the number, time since the start of the traffic capture, source and destination, as well as the protocol used, the packet size and a little information about the network packet.
- A real-time package panel where package information is divided into columns defined in the name panel.
- The Layers panel describes the OSI model layers of the selected network packet.
- Metadata panel presenting data in hexadecimal code and symbols.
Congratulations! You have successfully captured your network traffic. You can now see the data packets passing through the network, as well as some information about them: the sender and recipient addresses, the protocols used, and the packet contents.
Now you can start analyzing network traffic.
4. How to find hidden information?
Before you start analyzing traffic, you need to have basic knowledge of the OSI network model protocols. It is enough to read the Wikipedia article.Many programs use the HTTP protocol to transfer information, which allows you to receive various resources from the Internet and back. Let's consider one of the packets transferred via the HTTP protocol.
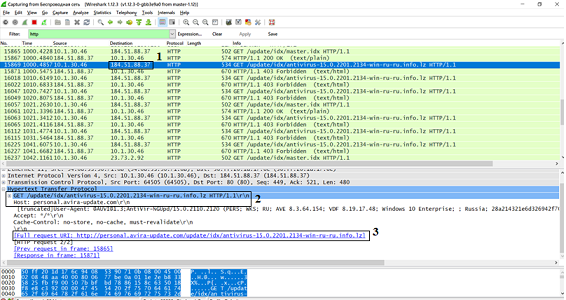
HTTP Package Overview
The HTTP protocol uses GET (intended for receiving data) and POST (intended for sending data) requests to transfer data.
In the picture in field 1 we see the IP address of the recipient (in this case, it is the address of my computer). In field 2 we learn that the antivirus server sent a GET request in order to request some data about my computer. This is necessary for the correct update of the program. And in field 3 we see what this request looks like in the form of a URL (Internet link).
A little homework!
To consolidate the material, try to analyze any HTTP protocol packet on your computer and try to explain why it was sent.5. How to find the necessary packages among all the packages?
When doing your homework, you may have had a problem finding the necessary package. To solve it, the Wireshark program has a solution - filtering! In the special "Filter" field, you can enter the necessary commands or use the prompts.
Overview of the "Filter" field
The most commonly used filtering is by IP address, by port number and by protocol. Let's see how it works.
Filtering by IP address allows us to view all packets coming from or going to someone. For example, let's select all packets coming from IP address 10.1.30.46 by entering "ip.src == xxxx" in the filter.

Overview of the "ip.src" command
You can also filter network traffic by the IP address of the packet recipient using the command "ip.dst == xxxx".
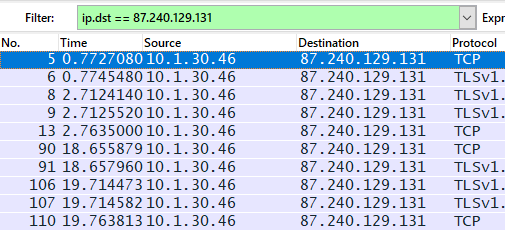
Overview of the "ip.dst" command
Additionally, you can see packets regardless of traffic direction using "ip.addr == xxxx".
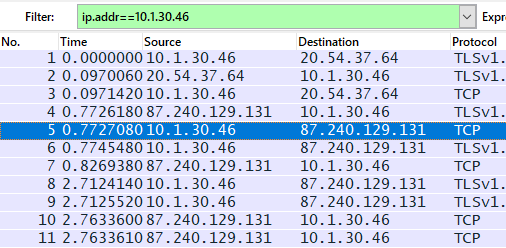
Overview of the "ip.addr" command
To filter by port number, use ".port=x" after the protocol name. For example, to view TCP port 80, which is used for unencrypted HTTP traffic, use the command "tpc.port==80".
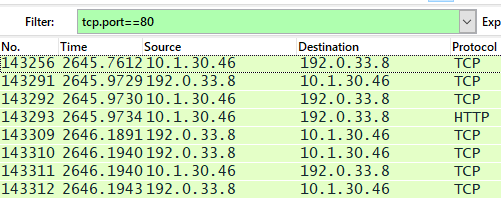
Overview of the "tcp.port" command
And finally, to filter traffic by the protocols used by the packets, you just need to enter the protocol name.
Please note that filters can be combined using the logical operators AND "and/&&", OR "or/||" and NOT "not/!"
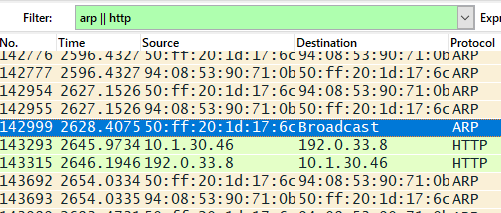
Overview of Logical Operators
Homework again!
To practice finding the information you need, try looking at the number of packets for a particular protocol and think about why there are so many of them.6. How to intercept data transmitted over secure communication channels?
Having dealt with the basic functionality of Wireshark, we can move on to more complex and useful ones.Data transfer on the global Internet is unsafe, especially if it is not protected in any way. Modern browsers use the SSL/TLS protocol, which encrypts information and allows it to be transferred securely.
Sometimes a user or system administrator needs to check traffic for suspicious activity or for correct operation of a program. Because of this, it becomes necessary to decrypt intercepted secure traffic.
First, let's understand how the SSL/TLS protocol works. Before encrypted data is exchanged, a connection establishment process, also called a handshake, is used.
During the handshake stage, the client and server undergo authentication, exchange information about their capabilities, and only then begin to negotiate a common session key.
There are many algorithms for negotiating over an unprotected communication channel. The choice is made from a list of algorithms supported by the client at the initial stage of the handshake.
The most common session key exchange algorithm is RSA. Let's look at the infographic describing the algorithm's mechanism.

RSA Session Key Exchange Algorithm
During the handshake, the client creates a random number called a pre-secret and sends it encrypted with the server's public key. Both parties then convert the pre-secret into a master secret and create a session key, which is used for further information exchange.
Now let's try to intercept protected information in the Wireshark program. Let's perform preparatory actions, namely, check the algorithm used to negotiate session keys and configure the browser. First, find the handshake using the filter by entering "ssl.handshake" and check the server message.
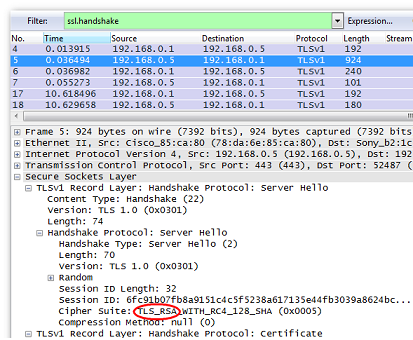
Overview of the "ssl.handshake" command
In the "Cipher Suite" field we can increase "TLS_RSA". This means that we can proceed to further actions.
Setting up a browser in the Windows operating system is quite simple. Open the computer properties, then "Advanced system settings" and select "Environment variables...".
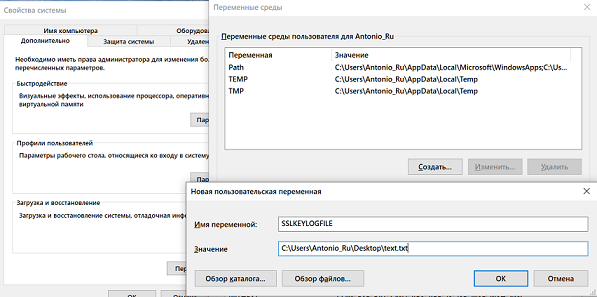
Setting up a browser in Windows 10
We add a new user variable “SSKEYLOGFILE” and specify the path to the file where we want to save it.
Consider the client's response message: it contains the encrypted value of the current session's pre-secret.
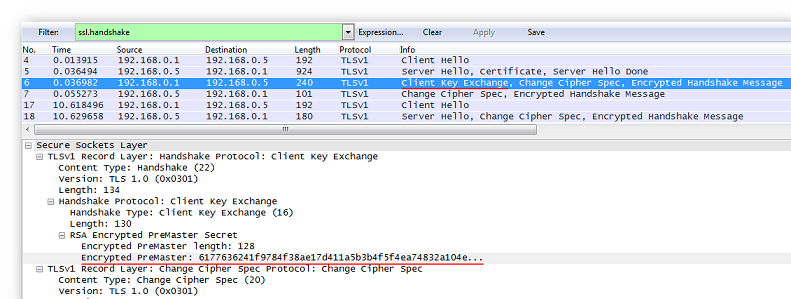
Client response message
Next, we proceed to configuring the Wireshark program. Using the key combination "Ctrl+Shift+P", open the "Preferences" menu, then expand the "Protocols" branch and select "SSL".
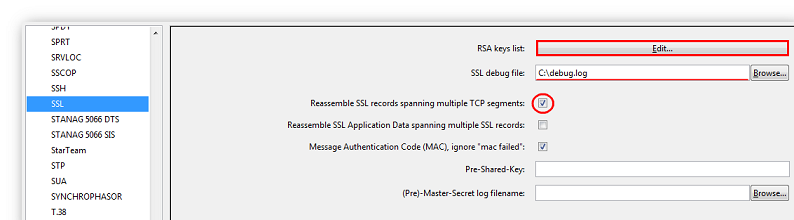
Setting up Wireshark
We check the installation of the required fields shown in the picture and click the "Edit" button. In the window that appears, click the "New" button and fill in the following fields: IP Address (IP address of the SSL server), Port (port of the SSL server), Protocol (protocol using SSL encryption. If unknown, specify data), Key File (path to the file with the secret key of the server, which we specified in the Environment Variables) and Password (if the secret key is password protected).
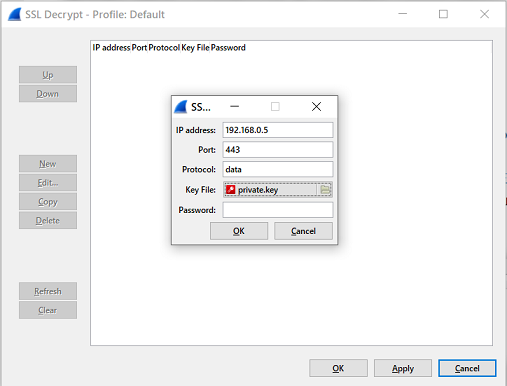
Setting up SSL in Wireshark
Now you can confirm the settings and start viewing the decrypted traffic. Don't forget to use the filter!
Consolidation of the material covered!
Try to connect to the server of any site yourself and see what packets your computer exchanges with it.7. What opportunities does capturing protected traffic provide?
Capturing secure traffic offers many possibilities. One of them is intercepting HTTPS requests from users connected to the network. Let's look at how to do this and what results we get.First, repeat the steps from the previous point, but specify the address of the required site as the IP address of the SSL server. The HTTP data transfer protocol is often used to transfer passwords. We already talked about the methods used in it in Chapter 4. To use HTTP traffic filtering by methods, you can use the command "http.request.method == "method name"". Since we want to intercept data sent by the client to the server, we will consider POST requests. To do this, we will use the filter "http.request.method == "POST"".

Capturing secure traffic
By doing these simple steps, we have obtained important data of another user. Therefore, it is important to remember that public networks are unsafe and pose a threat even to protected traffic.
A little practice!
Try capturing secure email server traffic and log in using your login and password. Find the POST request and see what's in there.Most likely, important data will be encrypted. In this way, the mail service protects your data, but the risk of hacking still remains.
8. How can the OSI model be related to the Wireshark program?
Having reviewed all the functionality of the Wireshark program, we can relate it to the OSI network model. But first, we should remember what this model is.OSI is a set of network protocols by which various network devices interact with each other. The model defines seven levels of system interaction. Let's look at the OSI model levels table.
| Level | Data type | Functions | Examples |
| 7. Applied | Data | Access to network services | HTTP, FTP |
| 6. Representations | Data | Data presentation and encryption | ASCII, JPEG |
| 5. Session | Data | Session Management | RPC, PAP |
| 4. Transport | Segments | Direct connection between end points and reliability | TCP, UDP |
| 3. Network | Packages | Route Determination and Logical Addressing | IPv4, IPv6, ICMP |
| 2. Channel | Footage | Physical addressing | Ethernet, ARP |
| 1. Physical | Bits | Working with transmission media, signals and binary data | USB, RJ |
Now let's correlate these levels with Wireshark. Let's look at the most common protocols when analyzing traffic, namely HTTP, TCP and ICMP.
The HTTP protocol in Wireshark has 4 layers according to the OSI model, namely application (Hypertext Transfer Protocol), transport (TCP), network (IPv4) and data link (Ethernet II).
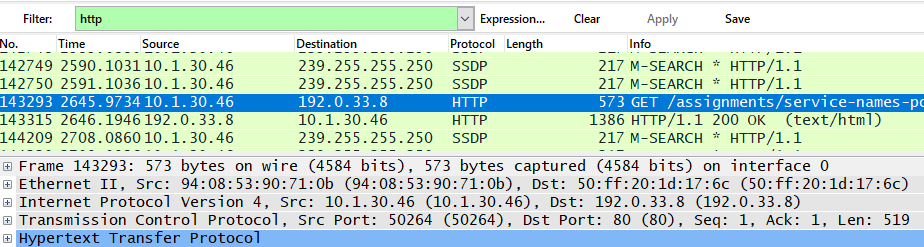
HTTP Protocol Overview
The TCP protocol has 3 layers according to the OSI model, which include transport (TCP), network (IPv4) and data link (Ethernet II).
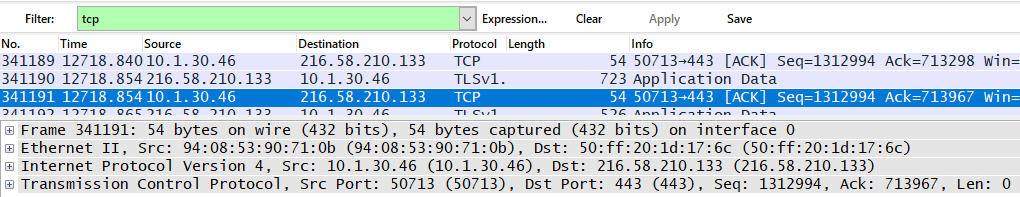
TCP Protocol Overview
The ICMP protocol generally has only 2 levels according to the OSI model: network (IPv4) and data link (Ethernet II).
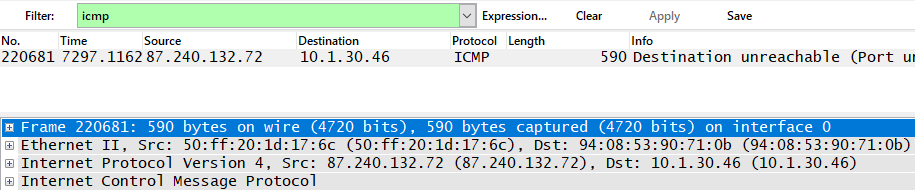
ICMP Protocol Overview
In total, Wireshark defines only 5 layers of the OSI model: application, transport, network, channel and physical. Depending on the protocol, you can see different levels.
Summing up
After reading this guide, we learned how to analyze traffic and search for hidden information, as well as intercept protected information. For future information security specialists, these are very important skills that will definitely come in handy in the future and will serve as a foundation for future professional development.Source

