Carding 4 Carders
Professional
- Messages
- 2,724
- Reaction score
- 1,579
- Points
- 113
Spy in your pocket
Your devices-computers, mobile phones, tablets-are constantly sharing information about your location. A mobile phone is very convenient for this task. Wherever you go, your phone is always with you. It captures where you are, even without an Internet connection.
Your life according to geolocation data
The data has been collected for some time, and now we have a surprisingly detailed picture of who you are and how you live. Add public addresses, tweets, photos, and phone details, and it will be hard to imagine a more complete picture of you.
Geolocation data reveals not only where you live and work, but also your visits to churches, clinics, bars, and friends and relatives. The data will tell you which protest actions you participated in, and which political or social groups you belong to.
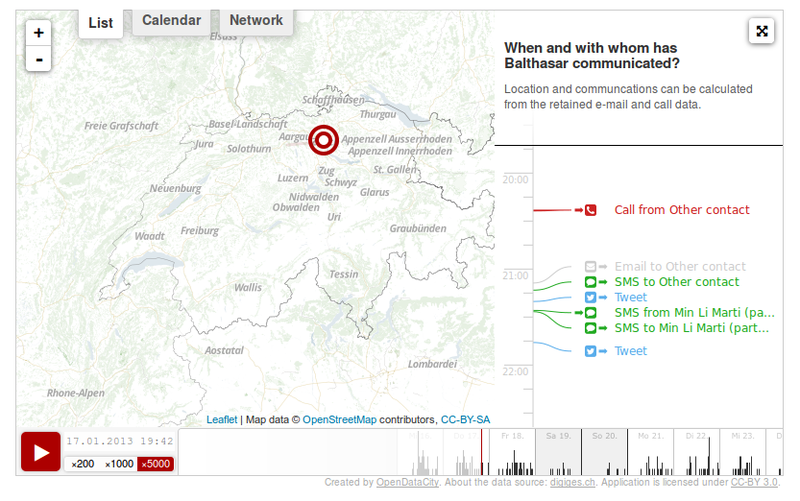
Image for post.
How this works can be seen in a special map (en)recently prepared by Open Data City. The map is based on communication data from Balthasar Glättli, a member of the Green party of Switzerland, collected over six months. It's amazing how deep into a person's life you can get thanks to location data.
In Germany, a member of the Green party, Malte Spitz, was subjected to a similar experiment. Mr. Spitz requested the data from his mobile operator. The results were published in the newspaper Die Zeit. The recordings included information about calls, text messages, and location. The newspaper processed the data and provided a detailed picture of the life of the politician (de). His daily movements and unusual deviations from routine tasks were clearly visible. Read more here.
And here you can see how Google tracks your movements around the city. (You need a Google account).
Social connection schemes
Geolocation data can be used to evaluate your relationships with other people. For example, you and someone else (one or more people) spend a certain amount of time in the same place every day. You probably have something in common, such as a common job, love or family relationship. Another example: you are a civil servant, and your location (lunch break, cafe) coincided with the coordinates of one journalist. Maybe you "leak" information to this journalist?
Who needs this data and why
The most detailed picture can fall into the hands of any people and organizations. Data can be sold for profit. You can make predictions about where a person will end up in the future. Finally, information can be used by the government.
Cell towers and your phone number
Mobile phone towers
To send and receive calls and messages, your phone must be in contact with cell towers. This activity is monitored and recorded by the operator. In fact, the mobile operator knows where you are and where you were before.
GPS tracking
Your smartphone is actually a GPS device. Most smartphones have a built-in GPS receiver. If the corresponding function is enabled, the receiver receives signals from GPS satellites, and the accuracy of coordinates increases.
Location records
Geolocation data can be used by your phone and various applications. Most smartphones have a mapping program installed. When you move, your current coordinates and where you were in the past are recorded.
Who has access
Your location data is available to anyone who has (or can access) your phone. Google and Apple presumably also have access to geolocation data, since they control both coordinate tracking apps and operating systems for most smartphones.
View geolocation data
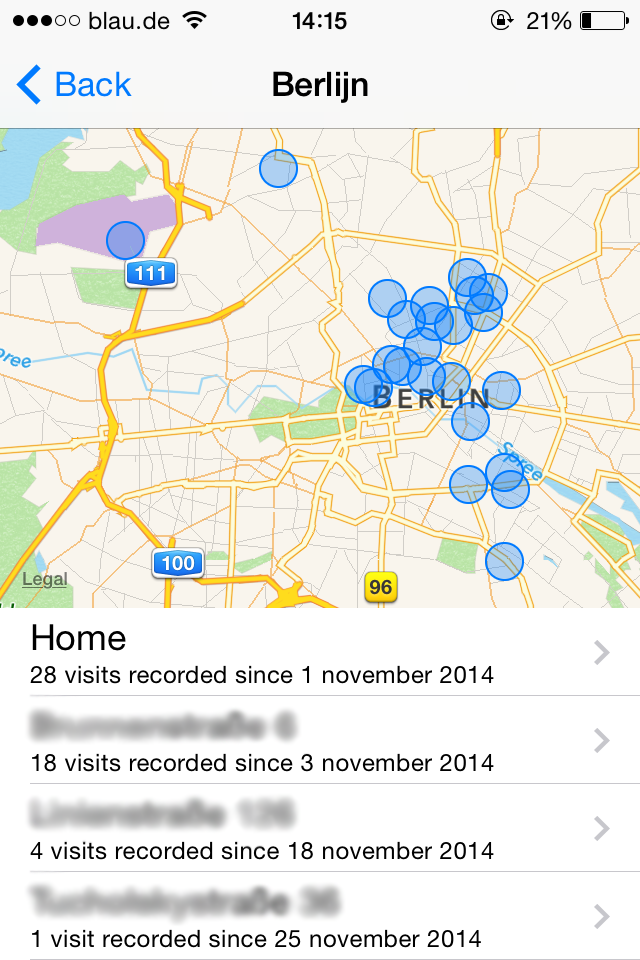
Image for post.
Some people disable location detection on their phone. If you didn't do this, your device may be recording the coordinates. The iPhone owner can see this information on the map.
If your iPhone is running on iOS7 or a more recent operating system, select Settings - > Privacy → geolocation Services → System services → Frequently visited places → select a city → > see the map.
How can they find out where I live?
On the iPhone, the app detects the "home" and "work" points. Apple's logic: if you regularly spend the night in the same place, it's probably home. And if you regularly spend daytime hours elsewhere, that's probably your job.
Are there any other ways to display my movements on your phone?
Yes. You can install the recommended Open Paths app (iPhone or Android).
Note: if you install Open Paths, the New York Times, the developer of this app, will have de facto access to your personal data.
Wi-fi history
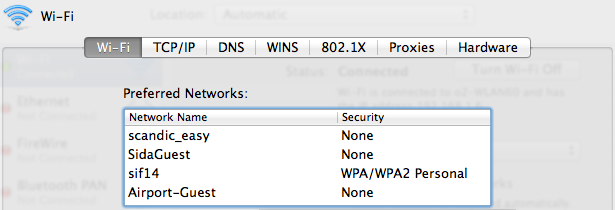
Image for post.
There are two main ways that your phone can share location data when wi-fi is enabled.
Before connecting to the network
Let's say you go to a coffee shop you've never been to before and turn on your computer. Wi-fi is enabled by default. The computer is looking for a network, but not any random network. It's easier if they already know this network and have previously connected to it.
To find out if there are any familiar networks nearby, the computer will start transmitting their names. This list may include cafes, offices, airports, apartments and homes of your friends, and various public places.
Who has access
The owner of the network and anyone who is able to intercept traffic, for example, by creating a fake network. An attacker can get a detailed picture of where you've been before.
Inside the network
There may be several access points in the network, for example, if the network belongs to a large company or conference hall (as an option-with support for Wireless Distribution System technology). When you connect to such a wi-fi network and move within it from one access point to another, your movements can also be tracked.
What it looks like
A similar observation was established for the participants of the Re ublica conference in Berlin (2013) as part of the Open Data City project. You can view the conference guests ' movements on the interactive map here.
ublica conference in Berlin (2013) as part of the Open Data City project. You can view the conference guests ' movements on the interactive map here.
View your wi-fi history
You can't view the history of wi-fi connections on iPhone or iPad devices, although you can get rid of all connection records by clicking on the links Settings → General → Reset → Reset network settings.
On Android phones and computers (including Macs), you can see a list of wi-fi connections and delete these entries one by one.
Your devices-computers, mobile phones, tablets-are constantly sharing information about your location. A mobile phone is very convenient for this task. Wherever you go, your phone is always with you. It captures where you are, even without an Internet connection.
Your life according to geolocation data
The data has been collected for some time, and now we have a surprisingly detailed picture of who you are and how you live. Add public addresses, tweets, photos, and phone details, and it will be hard to imagine a more complete picture of you.
Geolocation data reveals not only where you live and work, but also your visits to churches, clinics, bars, and friends and relatives. The data will tell you which protest actions you participated in, and which political or social groups you belong to.

Image for post.
How this works can be seen in a special map (en)recently prepared by Open Data City. The map is based on communication data from Balthasar Glättli, a member of the Green party of Switzerland, collected over six months. It's amazing how deep into a person's life you can get thanks to location data.
In Germany, a member of the Green party, Malte Spitz, was subjected to a similar experiment. Mr. Spitz requested the data from his mobile operator. The results were published in the newspaper Die Zeit. The recordings included information about calls, text messages, and location. The newspaper processed the data and provided a detailed picture of the life of the politician (de). His daily movements and unusual deviations from routine tasks were clearly visible. Read more here.
And here you can see how Google tracks your movements around the city. (You need a Google account).
Social connection schemes
Geolocation data can be used to evaluate your relationships with other people. For example, you and someone else (one or more people) spend a certain amount of time in the same place every day. You probably have something in common, such as a common job, love or family relationship. Another example: you are a civil servant, and your location (lunch break, cafe) coincided with the coordinates of one journalist. Maybe you "leak" information to this journalist?
Who needs this data and why
The most detailed picture can fall into the hands of any people and organizations. Data can be sold for profit. You can make predictions about where a person will end up in the future. Finally, information can be used by the government.
Cell towers and your phone number
Mobile phone towers
To send and receive calls and messages, your phone must be in contact with cell towers. This activity is monitored and recorded by the operator. In fact, the mobile operator knows where you are and where you were before.
GPS tracking
Your smartphone is actually a GPS device. Most smartphones have a built-in GPS receiver. If the corresponding function is enabled, the receiver receives signals from GPS satellites, and the accuracy of coordinates increases.
Location records
Geolocation data can be used by your phone and various applications. Most smartphones have a mapping program installed. When you move, your current coordinates and where you were in the past are recorded.
Who has access
Your location data is available to anyone who has (or can access) your phone. Google and Apple presumably also have access to geolocation data, since they control both coordinate tracking apps and operating systems for most smartphones.
View geolocation data

Image for post.
Some people disable location detection on their phone. If you didn't do this, your device may be recording the coordinates. The iPhone owner can see this information on the map.
If your iPhone is running on iOS7 or a more recent operating system, select Settings - > Privacy → geolocation Services → System services → Frequently visited places → select a city → > see the map.
How can they find out where I live?
On the iPhone, the app detects the "home" and "work" points. Apple's logic: if you regularly spend the night in the same place, it's probably home. And if you regularly spend daytime hours elsewhere, that's probably your job.
Are there any other ways to display my movements on your phone?
Yes. You can install the recommended Open Paths app (iPhone or Android).
Note: if you install Open Paths, the New York Times, the developer of this app, will have de facto access to your personal data.
Wi-fi history

Image for post.
There are two main ways that your phone can share location data when wi-fi is enabled.
Before connecting to the network
Let's say you go to a coffee shop you've never been to before and turn on your computer. Wi-fi is enabled by default. The computer is looking for a network, but not any random network. It's easier if they already know this network and have previously connected to it.
To find out if there are any familiar networks nearby, the computer will start transmitting their names. This list may include cafes, offices, airports, apartments and homes of your friends, and various public places.
Who has access
The owner of the network and anyone who is able to intercept traffic, for example, by creating a fake network. An attacker can get a detailed picture of where you've been before.
Inside the network
There may be several access points in the network, for example, if the network belongs to a large company or conference hall (as an option-with support for Wireless Distribution System technology). When you connect to such a wi-fi network and move within it from one access point to another, your movements can also be tracked.
What it looks like
A similar observation was established for the participants of the Re
View your wi-fi history
You can't view the history of wi-fi connections on iPhone or iPad devices, although you can get rid of all connection records by clicking on the links Settings → General → Reset → Reset network settings.
On Android phones and computers (including Macs), you can see a list of wi-fi connections and delete these entries one by one.


