Lord777
Professional
- Messages
- 2,577
- Reaction score
- 1,556
- Points
- 113
Over the past few decades, mobile networks have undergone significant changes, with each new generation inheriting the infrastructural solutions of its predecessors. For the period of 2022, in conjunction with big data analysis and the development of artificial intelligence (all of which are at the core of Industry 4.0), we are talking about a "fifth generation" communications network, which also has a dependence on 4G/LTE components. It is worth noting that although the new 4G networks use a different signaling system, called Diameter, SS7 security issues are still acute, as mobile operators must ensure support for 2G and 3G networks, as well as the interaction between networks of different generations.

One of the biggest problems of 2G/3G systems is the use of the SS7 signaling protocol, which dates back to the 1970s and is very vulnerable to hackers because of outdated security principles. SS7 is a set of telephony signaling protocols used for most of the world's public telephone networks. SS7 is mainly used for basic installation, call control and termination of subscribers, organization of wireless roaming and authentication of mobile subscribers, call forwarding, caller name/number mapping, SMS (short message service) provisioning. Today the signaling network is not isolated, and this allows an attacker to exploit its weaknesses and intercept calls and SMS, bypass billing, steal money from the mobile account or affect the performance of the mobile network.
There are many SS7 vulnerabilities relevant today that you should be aware of.

Before we look at major attacks on 2nd and 3rd generation networks, we need to refresh our minds on basic definitions of cellular networks. For those who want to build a more detailed picture of how mobile systems work, which describes the basic elements of 2G(GSM-network) and 3G(UMTS) systems. Below, for the convenience of reading this article, the key of them in the consideration of the problem:
HLR (Home Location Register) - A database that stores all subscriber information in a home network.
MSC (Mobile Switching Center) - Switching node in GSM network
STP (Signaling Transfer Point) - is a node that routes signaling messages.
VLR (Visitor Location Register) - a guest location register of 2G and 3G networks. Usually one VLR corresponds to one MSC. It serves to store the data of all active MSC subscribers and is a shortened information from HLR.
I am attaching for you a link to the basic terms of telephone networks http://1234g.ru/book/terminy-i-opredeleniya-mobilnoj-svyazi
The picture below shows a variant of the attack, this example will help us to consolidate the concepts presented above.
Let's say we have two subscribers exchanging information using a cellular carrier. The MSC is essentially a switch which determines, depending on the subscriber's number, which MSC to send a particular message to (in this picture a text message interception was carried out). In order to determine the location of the subscriber in the entire cellular network, HLR, a huge database of subscribers of the cellular network, determines in which MSC, or, simply put, in the zone of which switch is the called subscriber. As part of this attack, hackers likely tampered with the Message Service Center (SMSC) by sending a request to update information to the HLR. The network now sent all the numbers of the attacked subscribers to the attackers' MSC rather than to their actual switch. As a result of the attack, all voice calls and SMS messages destined for victims went to the attacker.
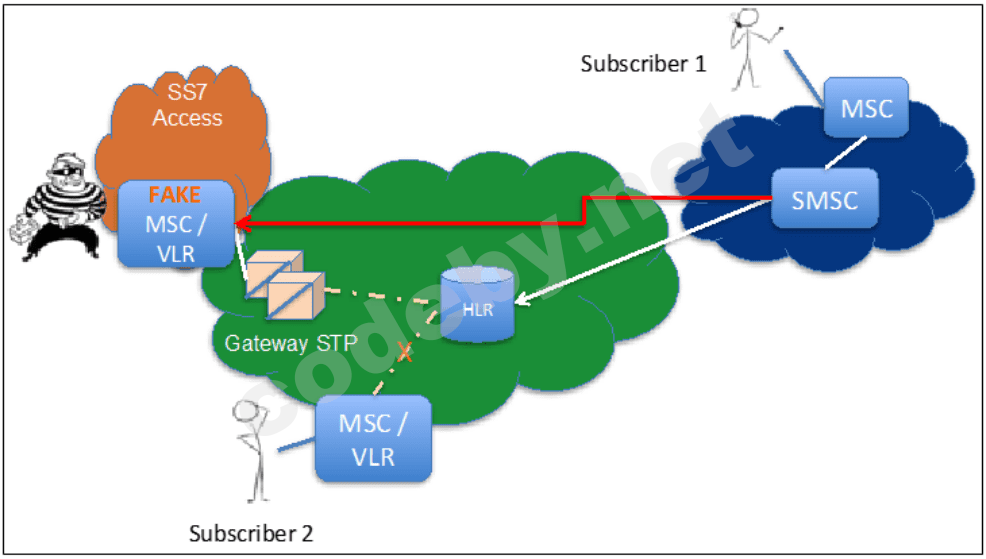
Today, there are real threats of disclosure of information about subscribers, network structure, interception of SMS-messages, fraud, denial of service, which causes losses to both the subscriber and the operator. In this regard, recently much attention has been paid to the specifics of this vulnerability. Developers of domestic information security products have a difficult task to create a quality product, capable of solving complex tasks of verification of the actual location of the subscriber, filtering messages, and more. SS7 protocol is one of the most popular methods of connecting global networks, it is widely used both by mobile network providers and intelligence organizations, as this protocol is quite effective for monitoring purposes.
SS7 attacks are mobile cyberattacks that aim to intercept SMS and voice messages on cellular networks by exploiting imperfections in the SS7 protocol. The attacks target telephone communications rather than wireless networks, which is sort of like a man-in-the-middle attack.
How does an SS7 attack work?
The hacker's kit for these attacks usually includes a Linux-based system and the SS7 SDK, freely available on the Internet, is the kit needed to launch an attack. However, you should be careful when trying to purchase any software implementing this type of attack, as there are a large number of scams in this area. The attack itself requires serious preparation, knowledge of the structure of the attacked network (IMSI users and things like that), so its implementation is a complex labor-intensive process.
Once the hacker is connected to the SS7 system, the attack begins on the customers by spoofing data in the network, namely the attacker is trying to pass himself off as a node of the MSC/VLR.
I provide a link where you can learn how to create your own lightweight SS7 network analogues SS7 TOOL: FULL GUIDE FOR LINUX USERS - Hacking By Kali Linux
Using the SS7 toolkit
Once connected to the SS7 system, the hacker must have his own software to attack SS7 or acquire existing software (the risks of this activity were discussed above). In order to create software, which implements an SS7 attack, it is necessary to have an SDK, which has the necessary libraries and stacks.
Registering SS7 software as a real device
When the phone connects to the roaming network, you need to register the same software. To do this you need the IMSI from the sim card associated with the number of cell phone.International Mobile Subscriber Identity - International Mobile Subscriber Identity, associated with each user of mobile communications standard GSM, UMTS or CDMA. When a subscriber registers on the network, the device transmits IMSI, which is used to identify him or her. Hence, based on the definition of this identifier and the logic of the attack, it becomes clear why the hacker needs it. There is absolutely no problem with obtaining a cell phone number, but it may be difficult to obtain the IMSI information. The data set mobile device + SIM card is the ID in HLR and is referred to as IMSI.
You must use the IMSI catcher tool to get the IMSI information.For more details on these devices I leave the link DC7495
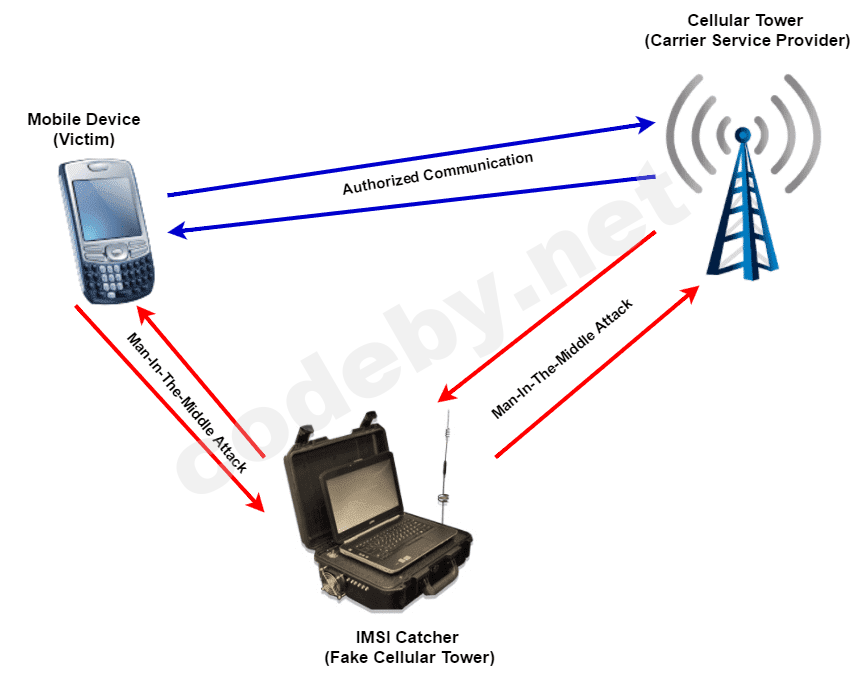
You must also fill in the addresses of the calling and called party SCCP. The address of the called party is generated from the IMSI, and the address of the calling party is the GT of the program. The HLR will respond with an Insert Subscriber Data message during Update Location. For the Update Location method to be successful and for the application to attach as a smartphone, the application program must recognize the ISD in the HLR. However, the attachment will be completed after the HLR transmits the ACK of the updated location.
After these steps, it is quite possible to perform an SS7 attack on subscribers' calls, messages, WhatsApp,other social networks and other applications.
How to prevent SS7 attack?
2FA based on SMS cannot be a secure way to authenticate users if there is a threat of SMS interception, but this method is still widely used. Companies that care about the security of their services are abandoning SMS authentication and offering consumers new methods to bypass outdated phone standards, such as SS7. The combination of several different authentication methods reduces the probability of an SS7 network attack by more than 90%.
Be aware!!!
Knowing your attacker's techniques and methods is the first step to neutralizing them. You need to know how often these types of attacks occur nowadays and take the necessary steps to prevent them.
Yes, given the sheer number of people with cell phones, one would assume that hackers are unlikely to target you for monitoring purposes However, the risk grows if you are an executive of a large company, a government employee, a lawyer, or someone who has important protected data on their mobile device. You can be hacked if you still use SMS-based 2FA for financial services.
One can only hope that in today's cyber warfare environment, domestic advances in telecommunications will ensure end users and phone companies from major leaks and losses, as worthwhile information security threats become the most pressing issues for the very long term. Be attentive, watch out for domestic solutions and be reverent about your protected information!!!

One of the biggest problems of 2G/3G systems is the use of the SS7 signaling protocol, which dates back to the 1970s and is very vulnerable to hackers because of outdated security principles. SS7 is a set of telephony signaling protocols used for most of the world's public telephone networks. SS7 is mainly used for basic installation, call control and termination of subscribers, organization of wireless roaming and authentication of mobile subscribers, call forwarding, caller name/number mapping, SMS (short message service) provisioning. Today the signaling network is not isolated, and this allows an attacker to exploit its weaknesses and intercept calls and SMS, bypass billing, steal money from the mobile account or affect the performance of the mobile network.
There are many SS7 vulnerabilities relevant today that you should be aware of.

Before we look at major attacks on 2nd and 3rd generation networks, we need to refresh our minds on basic definitions of cellular networks. For those who want to build a more detailed picture of how mobile systems work, which describes the basic elements of 2G(GSM-network) and 3G(UMTS) systems. Below, for the convenience of reading this article, the key of them in the consideration of the problem:
HLR (Home Location Register) - A database that stores all subscriber information in a home network.
MSC (Mobile Switching Center) - Switching node in GSM network
STP (Signaling Transfer Point) - is a node that routes signaling messages.
VLR (Visitor Location Register) - a guest location register of 2G and 3G networks. Usually one VLR corresponds to one MSC. It serves to store the data of all active MSC subscribers and is a shortened information from HLR.
I am attaching for you a link to the basic terms of telephone networks http://1234g.ru/book/terminy-i-opredeleniya-mobilnoj-svyazi
The picture below shows a variant of the attack, this example will help us to consolidate the concepts presented above.
Let's say we have two subscribers exchanging information using a cellular carrier. The MSC is essentially a switch which determines, depending on the subscriber's number, which MSC to send a particular message to (in this picture a text message interception was carried out). In order to determine the location of the subscriber in the entire cellular network, HLR, a huge database of subscribers of the cellular network, determines in which MSC, or, simply put, in the zone of which switch is the called subscriber. As part of this attack, hackers likely tampered with the Message Service Center (SMSC) by sending a request to update information to the HLR. The network now sent all the numbers of the attacked subscribers to the attackers' MSC rather than to their actual switch. As a result of the attack, all voice calls and SMS messages destined for victims went to the attacker.

Today, there are real threats of disclosure of information about subscribers, network structure, interception of SMS-messages, fraud, denial of service, which causes losses to both the subscriber and the operator. In this regard, recently much attention has been paid to the specifics of this vulnerability. Developers of domestic information security products have a difficult task to create a quality product, capable of solving complex tasks of verification of the actual location of the subscriber, filtering messages, and more. SS7 protocol is one of the most popular methods of connecting global networks, it is widely used both by mobile network providers and intelligence organizations, as this protocol is quite effective for monitoring purposes.
SS7 attacks are mobile cyberattacks that aim to intercept SMS and voice messages on cellular networks by exploiting imperfections in the SS7 protocol. The attacks target telephone communications rather than wireless networks, which is sort of like a man-in-the-middle attack.
How does an SS7 attack work?
The hacker's kit for these attacks usually includes a Linux-based system and the SS7 SDK, freely available on the Internet, is the kit needed to launch an attack. However, you should be careful when trying to purchase any software implementing this type of attack, as there are a large number of scams in this area. The attack itself requires serious preparation, knowledge of the structure of the attacked network (IMSI users and things like that), so its implementation is a complex labor-intensive process.
Once the hacker is connected to the SS7 system, the attack begins on the customers by spoofing data in the network, namely the attacker is trying to pass himself off as a node of the MSC/VLR.
I provide a link where you can learn how to create your own lightweight SS7 network analogues SS7 TOOL: FULL GUIDE FOR LINUX USERS - Hacking By Kali Linux
Using the SS7 toolkit
Once connected to the SS7 system, the hacker must have his own software to attack SS7 or acquire existing software (the risks of this activity were discussed above). In order to create software, which implements an SS7 attack, it is necessary to have an SDK, which has the necessary libraries and stacks.
Registering SS7 software as a real device
When the phone connects to the roaming network, you need to register the same software. To do this you need the IMSI from the sim card associated with the number of cell phone.International Mobile Subscriber Identity - International Mobile Subscriber Identity, associated with each user of mobile communications standard GSM, UMTS or CDMA. When a subscriber registers on the network, the device transmits IMSI, which is used to identify him or her. Hence, based on the definition of this identifier and the logic of the attack, it becomes clear why the hacker needs it. There is absolutely no problem with obtaining a cell phone number, but it may be difficult to obtain the IMSI information. The data set mobile device + SIM card is the ID in HLR and is referred to as IMSI.
You must use the IMSI catcher tool to get the IMSI information.For more details on these devices I leave the link DC7495

You must also fill in the addresses of the calling and called party SCCP. The address of the called party is generated from the IMSI, and the address of the calling party is the GT of the program. The HLR will respond with an Insert Subscriber Data message during Update Location. For the Update Location method to be successful and for the application to attach as a smartphone, the application program must recognize the ISD in the HLR. However, the attachment will be completed after the HLR transmits the ACK of the updated location.
After these steps, it is quite possible to perform an SS7 attack on subscribers' calls, messages, WhatsApp,other social networks and other applications.
How to prevent SS7 attack?
2FA based on SMS cannot be a secure way to authenticate users if there is a threat of SMS interception, but this method is still widely used. Companies that care about the security of their services are abandoning SMS authentication and offering consumers new methods to bypass outdated phone standards, such as SS7. The combination of several different authentication methods reduces the probability of an SS7 network attack by more than 90%.
Be aware!!!
Knowing your attacker's techniques and methods is the first step to neutralizing them. You need to know how often these types of attacks occur nowadays and take the necessary steps to prevent them.
Yes, given the sheer number of people with cell phones, one would assume that hackers are unlikely to target you for monitoring purposes However, the risk grows if you are an executive of a large company, a government employee, a lawyer, or someone who has important protected data on their mobile device. You can be hacked if you still use SMS-based 2FA for financial services.
One can only hope that in today's cyber warfare environment, domestic advances in telecommunications will ensure end users and phone companies from major leaks and losses, as worthwhile information security threats become the most pressing issues for the very long term. Be attentive, watch out for domestic solutions and be reverent about your protected information!!!

