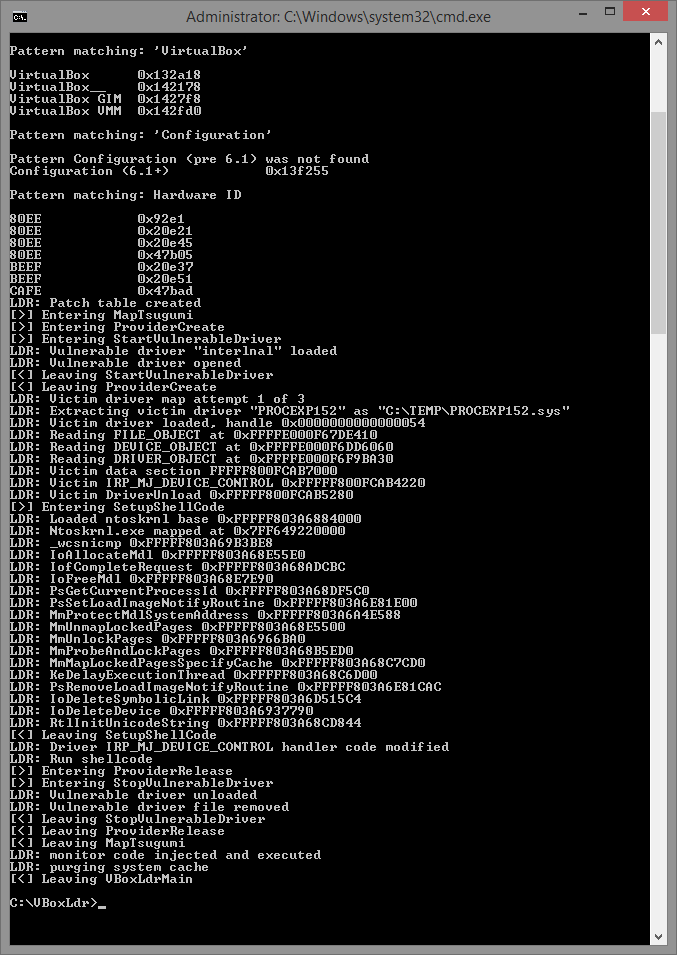
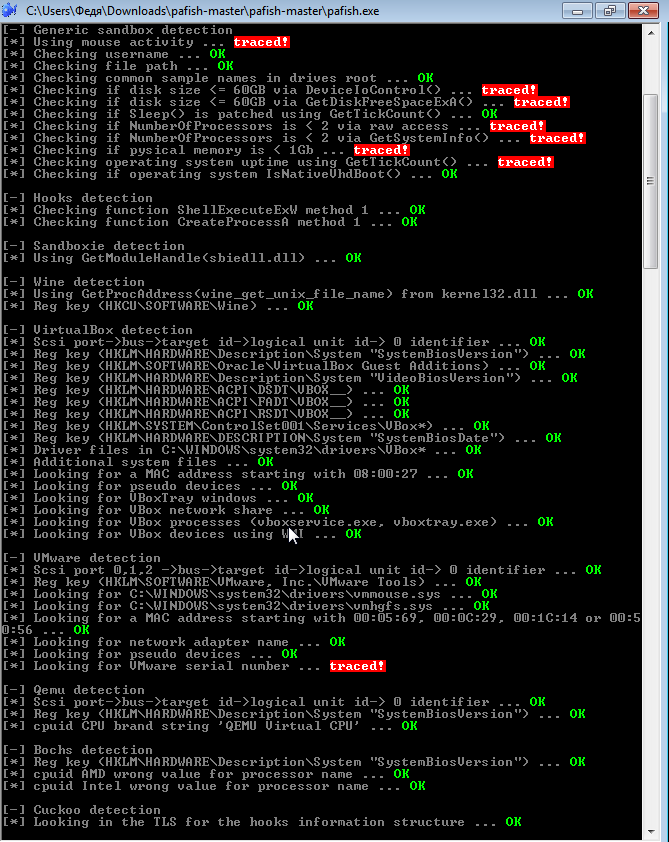
An urgent problem all over the world today is the protection and security of personal data on the network. The ubiquity of technology makes it easy to collect personal information. In addition, users independently share on social networks, instant messengers, e-mail correspondence and other online platforms, often without even suspecting that their data may fall into the wrong hands.
In the modern world, few people are surprised by the fact that everything and everyone is monitored: smartphones, tablets, computers, smart devices, software, etc. On the one hand, companies collecting information do everything to improve a particular service , make this beautiful world even better and improve the quality of user experience. On the other hand, they make money from users, analyze behavioral factors, form characteristic patterns and manipulate for maximum benefit.
In the first part, we will talk about what fingerprints are, setting up your browser and protecting your identity on the web.
Fingerprint or sometimes foorptrint is a complete digital fingerprint of a device, consisting of information about your operating system, settings, active browsers, installed plugins, etc. Such a print is presented in the form of a unique code or picture.
In the field of information technology, a fingerprint is usually called the ability to uniquely identify a person through his device, settings, software and other user characteristics.
What is the difference from cookies? To begin with, cookies are relevant within the same domain, while fingerprint allows you to track the sources of referrals to the target site and the paths of referrals from that site. Cookies, including eternal ones, can be cleared or blocked, which is not a tedious process. In turn, fingerprints can only be replaced.
Fingerprinting technology can be interpreted as a significant vulnerability in information security and, at the same time, as a violation of the privacy and confidentiality of users. We visit certain sites, many of us have personal settings in the browser: fonts, plugins, bookmarks, add-ons and extensions, screen resolutions, window arrangement, navigation buttons placement, etc. The combination of these elements constitutes a unique digital fingerprint of the device and can be conditionally compared with human biometric data, namely, fingerprints.
Where is browser fingerprint used and what is it used for?
Many of us do not see any problem in the fact that every step and every action is under control and settles in "big data". Others, on the contrary, are extremely concerned about their privacy, that they develop special tools and programs that check, impede, distort and block the collection of information.
Digital fingerprints are used to prevent fraud and identity theft. The Internet user, without knowing it, provides data about himself, without any consent. With an increase in the amount of collected data, a person's profile is formed, which is able to contain:
· Gender;
· Age;
· marital status;
· Political Views;
· Financial condition;
· Interests;
· Habits, etc.
It would seem that this information is only superficial, without reference to a specific person, i.e. there is some subject with certain parameters and relationships to certain things, but who exactly is unknown. But this is only for the time being, it is only worth once a person somewhere to indicate real personal data, for example, name, phone number, address, fingerprint will allow companies to fully identify you and thereby supplement the formed profile.
Users are deprived of the ability to prohibit sites from this type of data collection. Subsequently, the collected databases of browser fingerprints can be transferred to other companies for sharing, which inevitably leads to the identification of users.
Now let's discuss how to get around this.
VPN and proxy servers
Here is short. VPN is the easiest method to bypass regional bans. Changes your IP to the one available on the service. Does not protect against multiple trackers and does not affect already picked up cookies.
Proxy is a free spacer that does not encrypt your traffic. Don't skimp on a good multi-channel VPN - and turn it on even when switching to a dedicated server, which we'll talk about further
Browsers and add-ons
Firefox is considered the most reliable. Install plugins on it:
raleyes - will get rid of tracking via CDN.
Privacy Badger - gets rid of trackers, protects privacy.
HTTPS Everywhere - MITM protection on the web.
ScriptSafe - the extension removes everything unnecessary.
Ready config: https://pastebin.com/73QwJFeK
Privacy Settings - simplifies work with configs + there is a privacy mode.
User Agent Swither - plugin replaces browser identification.
Antidetect is a plugin similar to the previous one with more advanced settings. Paid and quite expensive.
Ghoster is a plugin that blocks analytics trackers, ads and other beacons.
Multiloginapp is a platform designed to replace different browser footprints. The program is designed to work with a large number of browser profiles. Each profile is in its own "container" and the option that history will go from one browser, cookies and fingerprints is excluded.
There are also specially assembled browsers for anonymous web surfing:
TOR is the most famous and popular among them.
Pale Moon is an open source browser based on Firefox.
Manually
Manual changes can help make your digital footprint less unique, such as:
· Changing the time zone of the device;
· Installation of another language of the operating system of the device;
· Installing a different browser language;
· Change the screen resolution of the device;
· Changing the scale of the web page;
Disable Flash, Javascript and WebGL execution.
Dedicated servers
The use of Dedicated Servers (from the word dedicated server) is still considered one of the most effective ways to maintain your anonymity. It is a separate physical machine from which no data is transmitted to your main and work.
Pros: Configuring an HTTP / SOCKS proxy or SSH / VPN connection to choose from; Control of the history of requests; Rescues when attacking through Flash, Java, JavaScript, if you use a remote browser;
Cons: Relatively high cost Technical knowledge required to set up correctly.
The main reason for the popularity and effectiveness of this method is that such a virtual computer is completely new and clean for the Internet, works around the clock and does not transmit any information about the end user and the characteristics of his computer (they say Facebook even tracks the MAC address).
Configuring the browser using the about: config page
This page contains links to various browser resources.
I will not delve into each resource, I will just point out a few interesting and useful examples.
about: support
Here you can see detailed information about the browser, user-agent, whether multiple streams are supported, or, for example, a composite manager for rendering the interface.
Here you can also find out the path to your Profile (Profile Directory). Why you will need it, I will describe in more detail below. Unfortunately, the path to the profile folder is not shown on the mobile version, so I will share mine with you (relevant only for android).
/data/data/org.mozilla.firefox/files/mozilla/*.default
The profile folder consists of 2 parts - * - random string (a unique set of letters for each device) + .default - for the default profile
about: memory
Here you can see what the browser memory is spent on, mostly useful for web frontend developers.
about: addons
The page with your extensions is also available from the graphical menu.
about: networking
A page with detailed information about visited sites, dns and websockets. It will also be useful for web developers.
about: config
And finally, the page that contains all the available browser settings in key-value format.
Detailed browser settings
In about: config there is a graphical editor of values, everything should be clear there and so.
But the user.js file, as you can see from its extension, assumes that all settings will be in a format understandable by a javascript parser. For example:
user_pref ("browser.bookmarks.restore_default_bookmarks", false);
user_pref is an object containing all settings.
Anything in the quotes “browser.bookmarks.restore_default_bookmarks” is a key.
The decimal point is followed by the value.
The key is always a string, but the value can be of different types, strings, numbers or boolean false / true (true / false).
The setting shown in the example is responsible for restoring the default bookmarks and is set to false. If you change this value, then all your bookmarks will be deleted and the default set of bookmarks will be restored.
Other settings
user_pref ("browser.bookmarks.showMobileBookmarks", true);
This setting allows you to see your bookmarks from the mobile version on the desktop, if you have synchronization enabled.
user_pref ("browser.ctrlTab.previews", true);
When switching tabs, previews of pages are displayed.
user_pref ("browser.download.autohideButton", false);
user_pref ("browser.download.panel.shown", true);
Settings responsible for displaying browser downloads.
user_pref ("browser.library.activity-stream.enabled", false);
user_pref ("browser.newtabpage.activity-stream.feeds.places", true);
user_pref ("browser.newtabpage.activity-stream.feeds.section.highlights", false);
user_pref ("browser.newtabpage.activity-stream.feeds.telemetry", false);
user_pref ("browser.newtabpage.activity-stream.filterAdult", false);
user_pref ("browser.newtabpage.activity-stream.prerender", false);
user_pref ("browser.newtabpage.activity-stream.showSponsored", false);
user_pref ("browser.newtabpage.activity-stream.telemetry", false);
user_pref ("browser.newtabpage.activity-stream.telemetry.ping.endpoint", "");
user_pref ("browser.newtabpage.activity-stream.tippyTop.service.endpoint", "");
user_pref ("browser.newtabpage.activity-stream.topSitesRows", 3);
user_pref ("browser.newtabpage.enhanced", true);
All activity-stream settings are responsible for your activity. “Newtabpage” - for displaying content in a new tab. I turned off almost everything, except for “feeds.places”, which are responsible for displaying recently visited pages in a new tab. By the way, all settings containing the word “endpoint” are responsible for the address to which the data is sent. If you use an empty string, no data will be transmitted.
user_pref ("browser.ping-center.telemetry", false);
One of the settings for telemetry. I turn it off to speed up surfing, since resources are wasted on any action, even if it works in parallel. Since I know firsthand how to profile programs and how much the performance drops at the same time, it is better to do without it.
user_pref ("browser.safebrowsing.blockedURIs.enabled", false);
user_pref ("browser.safebrowsing.downloads.enabled", false);
user_pref ("browser.safebrowsing.downloads.remote.block_dangerous", false);
user_pref ("browser.safebrowsing.downloads.remote.block_dangerous_host", false);
user_pref ("browser.safebrowsing.downloads.remote.block_potentially_unwanted", false);
user_pref ("browser.safebrowsing.downloads.remote.block_uncommon", false);
user_pref ("browser.safebrowsing.downloads.remote.enabled", false);
user_pref ("browser.safebrowsing.enabled", false);
user_pref ("browser.safebrowsing.malware.enabled", false);
user_pref ("browser.safebrowsing.phishing.enabled", false);
user_pref ("browser.safebrowsing.provider.google.advisoryURL", "");
user_pref ("browser.safebrowsing.provider.google.gethashURL", "");
user_pref ("browser.safebrowsing.provider.google.lists", "");
user_pref ("browser.safebrowsing.provider.google.pver", "");
user_pref ("browser.safebrowsing.provider.google.reportMalwareMistakeURL", "");
user_pref ("browser.safebrowsing.provider.google.reportPhishMistakeURL", "");
user_pref ("browser.safebrowsing.provider.google.reportURL", "");
user_pref ("browser.safebrowsing.provider.google.updateURL", "");
user_pref ("browser.safebrowsing.provider.google4.advisoryName", "");
user_pref ("browser.safebrowsing.provider.google4.advisoryURL", "");
user_pref ("browser.safebrowsing.provider.google4.dataSharingURL", "");
user_pref ("browser.safebrowsing.provider.google4.gethashURL", "");
user_pref ("browser.safebrowsing.provider.google4.lastupdatetime", "");
user_pref ("browser.safebrowsing.provider.google4.lists", "");
user_pref ("browser.safebrowsing.provider.google4.nextupdatetime", "");
user_pref ("browser.safebrowsing.provider.google4.pver", "");
user_pref ("browser.safebrowsing.provider.google4.reportMalwareMistakeURL", "");
user_pref ("browser.safebrowsing.provider.google4.reportPhishMistakeURL", "");
user_pref ("browser.safebrowsing.provider.google4.reportURL", "");
user_pref ("browser.safebrowsing.provider.google4.updateURL", "");
user_pref ("browser.safebrowsing.provider.mozilla.gethashURL", "");
user_pref ("browser.safebrowsing.provider.mozilla.lists", "");
user_pref ("browser.safebrowsing.provider.mozilla.pver", "");
user_pref ("browser.safebrowsing.provider.mozilla.updateURL", "");
“Safebrowsing” - these settings are responsible for checking the visited sites to make sure they are safe. This check involves checking the site host in the local database against a blacklist and checking the uploaded files on Google servers. (Thanks to dartraiden for the hint) If the answer is yes, a service page with a warning is shown instead of the site. I disabled this check to speed up surfing. Perhaps, for those using the Windows operating system, this should not be done.
user_pref ("browser.search.countryCode", "US");
user_pref ("browser.search.geoSpecificDefaults", false);
user_pref ("browser.search.geoSpecificDefaults.url", "");
user_pref ("browser.search.geoip.url", "");
user_pref ("browser.search.hiddenOneOffs", "Bing, Amazon.com, Twitter");
user_pref ("browser.search.region", "US");
user_pref ("geo.wifi.uri", "");
Search settings. I set the region to US, for the anonymity of search queries. Also disabled location for search (“geo”).
user_pref ("browser.tabs.loadInBackground", false);
user_pref ("browser.tabs.tabMinWidth", 30);
user_pref ("browser.tabs.warnOnClose", false);
Tab settings. I would like to mention “tabMinWidth” separately. In chrome, if you open many tabs, the text disappears. And in Firefox, this setting is responsible for the minimum tab length. And if more tabs are open, then they still do not shrink, but simply hide and additional tab control buttons appear. For me, this system is very convenient, since I constantly open many pages from the same site and without text I have to constantly guess which page is where.
user_pref ("browser.urlbar.clickSelectsAll", true);
user_pref ("browser.urlbar.maxRichResults", 15);
user_pref ("browser.urlbar.trimURLs", false);
When you click on the address bar, the entire address is highlighted, not the current word. And also https is not hidden in the address bar.
user_pref ("datareporting.healthreport.uploadEnabled", false);
user_pref ("datareporting.policy.dataSubmissionEnabled", false);
user_pref ("datareporting.policy.firstRunURL", "");
Mozilla Corporation reports
user_pref ("device.sensors.enabled", false);
user_pref ("device.sensors.motion.enabled", false);
user_pref ("device.sensors.orientation.enabled", false);
This is more for the mobile version, but sometimes laptops also have some kind of sensors.
user_pref ("devtools.aboutdebugging.showSystemAddons", true);
user_pref ("devtools.onboarding.telemetry.logged", false);
user_pref ("devtools.theme", "dark");
user_pref ("devtools.toolbox.splitconsoleEnabled", false);
Developer tools settings.
user_pref ("dom.push.enabled", false);
user_pref ("permissions.default.desktop-notification", 2);
user_pref ("permissions.default.geo", 2);
Duplicates disabling notifications from the graphical menu
user_pref ("experiments.activeExperiment", false);
user_pref ("experiments.enabled", false);
user_pref ("experiments.supported", false);
I do not want to experiment. Tuning for an amateur).
user_pref ("extensions.pocket.enabled", false);
user_pref ("extensions.ui.dictionary.hidden", false);
user_pref ("extensions.ui.experiment.hidden", true);
user_pref ("extensions.ui.locale.hidden", true);
user_pref ("extensions.webextensions.remote", true);
Extension settings. Turn off Pocket.
user_pref ("findbar.highlightAll", true);
user_pref ("font.internaluseonly.changed", true);
user_pref ("font.minimum-size.x-western", 10);
user_pref ("font.name.monospace.x-western", "Hack");
user_pref ("font.name.sans-serif.x-western", "Hack");
user_pref ("font.name.serif.x-western", "Hack");
The font settings duplicate the graphical settings of the smooth scrolling, selected experimentally.
user_pref ("general.smoothScroll.durationToIntervalRatio", 1000);
user_pref ("general.smoothScroll.lines.durationMaxMS", 100);
user_pref ("general.smoothScroll.lines.durationMinMS", 100);
user_pref ("general.smoothScroll.mouseWheel.durationMaxMS", 150);
user_pref ("general.smoothScroll.mouseWheel.durationMinMS", 50);
user_pref ("general.smoothScroll.other", false);
user_pref ("general.smoothScroll.pixels", false);
user_pref ("general.smoothScroll.scrollbars.durationMaxMS", 100);
user_pref ("general.smoothScroll.scrollbars.durationMinMS", 100);
user_pref ("general.useragent.override", "Mozilla / 5.0 (X11; Linux x86_64; rv: 60.0) Gecko / 20100101 Firefox / 64.0");
user_pref ("general.useragent.vendor", "");
user_pref ("general.useragent.vendorSub", "");
User agent settings, if there is no special need, it is better not to touch them
user_pref ("general.warnOnAboutConfig", false);
Disable warning window when visiting about: config
user_pref ("gfx.use_text_smoothing_setting", true);
user_pref ("gfx.webrender.enabled", true);
user_pref ("gfx.webrender.highlight-painted-layers", false);
user_pref ("layers.acceleration.force-enabled", true);
Acceleration of rendering.
user_pref ("intl.accept_languages", "en-us, en, uk, ru");
user_pref ("intl.locale.requested", "en-US");
This information is intended to automatically select the language on the site, although the sites themselves very rarely pay attention to this setting. Hopefully the situation will change in the future.
user_pref ("layout.css.devPixelsPerPx", "1.25");
user_pref ("layout.css.osx-font-smoothing.enabled", true);
user_pref ("layout.word_select.stop_at_punctuation", true);
I would like to highlight the “devPixelsPerPx” setting. This setting is responsible for scaling the interface and will be especially useful for people with low vision or on computers with a high screen resolution. The default is “1”.
user_pref ("media.autoplay.enabled", false);
user_pref ("media.av1.enabled", true);
Video related settings. Disables autoplay and enables experimental support for the new AV1 codec.
user_pref ("network.allow-experiments", false);
user_pref ("network.cookie.prefsMigrated", true);
user_pref ("network.dns.disablePrefetch", true);
user_pref ("network.http.speculative-parallel-limit", 0);
user_pref ("network.predictor.enabled", false);
user_pref ("network.prefetch-next", false);
user_pref ("network.security.esni.enabled", true);
user_pref ("network.tcp.tcp_fastopen_enable", true);
user_pref ("network.trr.mode", 2);
user_pref ("network.trr.uri", "https://mozilla.cloudflare-dns.com/dns-query");
user_pref ("network.warnOnAboutNetworking", false);
I want to analyze this group of settings in more detail.
“Dns.disablePrefetch” and “predictor.enabled” are responsible for pre-visiting links on the page to speed up loading if the user wants to click on any of the links. If the Internet is slow, then it only worsens the situation, especially in the mobile version somewhere in the metro.
“Tcp.tcp_fastopen_enable” enables TCP Fast Open
“Trr.mode” is responsible for DNS Over HTTPS. A value of 0 disables DoH completely; 1 - DNS or DoH is used, whichever is faster; 2 - DoH is used by default, and DNS is used as a fallback; 3 - only DoH is used; 4 - mirroring mode in which DoH and DNS are used in parallel.
Well, “trr.uri” is responsible for the server that the browser knocks on to get the IP address of the sites visited.
“Security.esni.enabled” is responsible for the Encrypted SNI
user_pref ("privacy.donottrackheader.enabled", true);
user_pref ("privacy.firstparty.isolate", true);
// Disables memorizing the zoom level for the site
user_pref ("privacy.resistFingerprinting", true);
user_pref ("privacy.resistFingerprinting.autoDeclineNoUserInputCanvasPrompts", false);
Privacy settings.
user_pref ("privacy.userContext.enabled", true);
user_pref ("privacy.userContext.longPressBehavior", 2);
user_pref ("privacy.userContext.ui.enabled", true);
“UserContext” includes Multi-Account Containers.
This add-on isolates cookies and browsing history into separate containers. Unfortunately, only for the desktop. I isolated all the services of Google, Facebook and several other important services separately. Also, if you additionally install the Multi-Account Containers extension, you can use it to bind sites to containers. Even if you open a link linked to another container from one container, it opens in this container, in a new tab. Very comfortably.
user_pref ("reader.color_scheme", "dark");
user_pref ("reader.content_width", 12);
In Firefox there is a very easy read page mode, in which all but the text is deleted. It is still far from ideal, it cuts out some tags with the text, but it is still very convenient to use it. You can activate it here:
user_pref ("security.ssl.errorReporting.automatic", true);
user_pref ("toolkit.identity.enabled", false);
user_pref ("toolkit.telemetry.archive.enabled", false);
user_pref ("toolkit.telemetry.bhrPing.enabled", false);
user_pref ("toolkit.telemetry.coverage.opt-out", false);
user_pref ("toolkit.telemetry.enabled", false);
user_pref ("toolkit.telemetry.firstShutdownPing.enabled", false);
user_pref ("toolkit.telemetry.hybridContent.enabled", false);
user_pref ("toolkit.telemetry.infoURL", "");
user_pref ("toolkit.telemetry.newProfilePing.enabled", false);
user_pref ("toolkit.telemetry.reportingpolicy.firstRun", false);
user_pref ("toolkit.telemetry.server", "");
user_pref ("toolkit.telemetry.shutdownPingSender.enabled", false);
user_pref ("toolkit.telemetry.unified", false);
user_pref ("toolkit.telemetry.updatePing.enabled", false);
Diverse telemetry. Again
user_pref ("widget.chrome.allow-gtk-dark-theme", true);
user_pref ("widget.content.allow-gtk-dark-theme", true);
// user_pref ("widget.content.gtk-theme-override", "Adwaita: light");
How to hide (change) browser fingerprint?
There are protective measures when using browsers, but none of them will work 100%. And a logical question arises: "Does it make sense to use some kind of specialized software or install extensions that block certain processes when visiting sites?" The answer will be ambiguous, since a kind of dissonance arises.
At the time when you are trying to combat tracking and apply special browser settings and special software, you definitely increase the uniqueness of your digital fingerprint of the device, thereby allowing you to be more likely to identify you and form a user profile.
Multiple studies have confirmed that computers and software with “default” settings are more difficult to identify and “associate” with a specific person, while even small changes have the opposite effect.
In practice, the most effective protection is the use of the Tor Browser, which developers put a lot of effort into reducing the uniqueness of fingerprints. For everyday use, an extension like Privacy Badger is a good option. With it, you can reduce the level of tracking and the amount of information transmitted. For even more confidence and privacy protection, all of this must be used in a virtual machine.
All these methods take place, however, for the average user, such actions create certain difficulties and a waste of time.
If the topic for you is very interesting and relevant, watch the video from Ufocoder, where he talks in some detail and shows how the fingerprint technology works and whether it is possible to fight it:
In the next article we will look at ways to spoof fingerprints, as well as other "anonymous" browsers.
You have been fucked, fucked and will be fucked. State, hackers, officials.
It is impossible to stop this swinger party. But I will teach you how to protect yourself. I will show and tell you something that the "Hacker" magazine does not write about and that other channels do not tell or simply do not know. Find here a selection of the best cybersecurity articles and videos. Everything from Wi-Fi audits to auto openings (in case you've lost your keys). And also hot news with author's comments.
In the modern world, few people are surprised by the fact that everything and everyone is monitored: smartphones, tablets, computers, smart devices, software, etc. On the one hand, companies collecting information do everything to improve a particular service , make this beautiful world even better and improve the quality of user experience. On the other hand, they make money from users, analyze behavioral factors, form characteristic patterns and manipulate for maximum benefit.
In the first part, we will talk about what fingerprints are, setting up your browser and protecting your identity on the web.
Fingerprint or sometimes foorptrint is a complete digital fingerprint of a device, consisting of information about your operating system, settings, active browsers, installed plugins, etc. Such a print is presented in the form of a unique code or picture.
In the field of information technology, a fingerprint is usually called the ability to uniquely identify a person through his device, settings, software and other user characteristics.
What is the difference from cookies? To begin with, cookies are relevant within the same domain, while fingerprint allows you to track the sources of referrals to the target site and the paths of referrals from that site. Cookies, including eternal ones, can be cleared or blocked, which is not a tedious process. In turn, fingerprints can only be replaced.
Fingerprinting technology can be interpreted as a significant vulnerability in information security and, at the same time, as a violation of the privacy and confidentiality of users. We visit certain sites, many of us have personal settings in the browser: fonts, plugins, bookmarks, add-ons and extensions, screen resolutions, window arrangement, navigation buttons placement, etc. The combination of these elements constitutes a unique digital fingerprint of the device and can be conditionally compared with human biometric data, namely, fingerprints.
Where is browser fingerprint used and what is it used for?
Many of us do not see any problem in the fact that every step and every action is under control and settles in "big data". Others, on the contrary, are extremely concerned about their privacy, that they develop special tools and programs that check, impede, distort and block the collection of information.
Digital fingerprints are used to prevent fraud and identity theft. The Internet user, without knowing it, provides data about himself, without any consent. With an increase in the amount of collected data, a person's profile is formed, which is able to contain:
· Gender;
· Age;
· marital status;
· Political Views;
· Financial condition;
· Interests;
· Habits, etc.
It would seem that this information is only superficial, without reference to a specific person, i.e. there is some subject with certain parameters and relationships to certain things, but who exactly is unknown. But this is only for the time being, it is only worth once a person somewhere to indicate real personal data, for example, name, phone number, address, fingerprint will allow companies to fully identify you and thereby supplement the formed profile.
Users are deprived of the ability to prohibit sites from this type of data collection. Subsequently, the collected databases of browser fingerprints can be transferred to other companies for sharing, which inevitably leads to the identification of users.
Now let's discuss how to get around this.
VPN and proxy servers
Here is short. VPN is the easiest method to bypass regional bans. Changes your IP to the one available on the service. Does not protect against multiple trackers and does not affect already picked up cookies.
Proxy is a free spacer that does not encrypt your traffic. Don't skimp on a good multi-channel VPN - and turn it on even when switching to a dedicated server, which we'll talk about further
Browsers and add-ons
Firefox is considered the most reliable. Install plugins on it:
raleyes - will get rid of tracking via CDN.
Privacy Badger - gets rid of trackers, protects privacy.
HTTPS Everywhere - MITM protection on the web.
ScriptSafe - the extension removes everything unnecessary.
Ready config: https://pastebin.com/73QwJFeK
Privacy Settings - simplifies work with configs + there is a privacy mode.
User Agent Swither - plugin replaces browser identification.
Antidetect is a plugin similar to the previous one with more advanced settings. Paid and quite expensive.
Ghoster is a plugin that blocks analytics trackers, ads and other beacons.
Multiloginapp is a platform designed to replace different browser footprints. The program is designed to work with a large number of browser profiles. Each profile is in its own "container" and the option that history will go from one browser, cookies and fingerprints is excluded.
There are also specially assembled browsers for anonymous web surfing:
TOR is the most famous and popular among them.
Pale Moon is an open source browser based on Firefox.
Manually
Manual changes can help make your digital footprint less unique, such as:
· Changing the time zone of the device;
· Installation of another language of the operating system of the device;
· Installing a different browser language;
· Change the screen resolution of the device;
· Changing the scale of the web page;
Disable Flash, Javascript and WebGL execution.
Dedicated servers
The use of Dedicated Servers (from the word dedicated server) is still considered one of the most effective ways to maintain your anonymity. It is a separate physical machine from which no data is transmitted to your main and work.
Pros: Configuring an HTTP / SOCKS proxy or SSH / VPN connection to choose from; Control of the history of requests; Rescues when attacking through Flash, Java, JavaScript, if you use a remote browser;
Cons: Relatively high cost Technical knowledge required to set up correctly.
The main reason for the popularity and effectiveness of this method is that such a virtual computer is completely new and clean for the Internet, works around the clock and does not transmit any information about the end user and the characteristics of his computer (they say Facebook even tracks the MAC address).
Configuring the browser using the about: config page
This page contains links to various browser resources.
I will not delve into each resource, I will just point out a few interesting and useful examples.
about: support
Here you can see detailed information about the browser, user-agent, whether multiple streams are supported, or, for example, a composite manager for rendering the interface.
Here you can also find out the path to your Profile (Profile Directory). Why you will need it, I will describe in more detail below. Unfortunately, the path to the profile folder is not shown on the mobile version, so I will share mine with you (relevant only for android).
/data/data/org.mozilla.firefox/files/mozilla/*.default
The profile folder consists of 2 parts - * - random string (a unique set of letters for each device) + .default - for the default profile
about: memory
Here you can see what the browser memory is spent on, mostly useful for web frontend developers.
about: addons
The page with your extensions is also available from the graphical menu.
about: networking
A page with detailed information about visited sites, dns and websockets. It will also be useful for web developers.
about: config
And finally, the page that contains all the available browser settings in key-value format.
Detailed browser settings
In about: config there is a graphical editor of values, everything should be clear there and so.
But the user.js file, as you can see from its extension, assumes that all settings will be in a format understandable by a javascript parser. For example:
user_pref ("browser.bookmarks.restore_default_bookmarks", false);
user_pref is an object containing all settings.
Anything in the quotes “browser.bookmarks.restore_default_bookmarks” is a key.
The decimal point is followed by the value.
The key is always a string, but the value can be of different types, strings, numbers or boolean false / true (true / false).
The setting shown in the example is responsible for restoring the default bookmarks and is set to false. If you change this value, then all your bookmarks will be deleted and the default set of bookmarks will be restored.
Other settings
user_pref ("browser.bookmarks.showMobileBookmarks", true);
This setting allows you to see your bookmarks from the mobile version on the desktop, if you have synchronization enabled.
user_pref ("browser.ctrlTab.previews", true);
When switching tabs, previews of pages are displayed.
user_pref ("browser.download.autohideButton", false);
user_pref ("browser.download.panel.shown", true);
Settings responsible for displaying browser downloads.
user_pref ("browser.library.activity-stream.enabled", false);
user_pref ("browser.newtabpage.activity-stream.feeds.places", true);
user_pref ("browser.newtabpage.activity-stream.feeds.section.highlights", false);
user_pref ("browser.newtabpage.activity-stream.feeds.telemetry", false);
user_pref ("browser.newtabpage.activity-stream.filterAdult", false);
user_pref ("browser.newtabpage.activity-stream.prerender", false);
user_pref ("browser.newtabpage.activity-stream.showSponsored", false);
user_pref ("browser.newtabpage.activity-stream.telemetry", false);
user_pref ("browser.newtabpage.activity-stream.telemetry.ping.endpoint", "");
user_pref ("browser.newtabpage.activity-stream.tippyTop.service.endpoint", "");
user_pref ("browser.newtabpage.activity-stream.topSitesRows", 3);
user_pref ("browser.newtabpage.enhanced", true);
All activity-stream settings are responsible for your activity. “Newtabpage” - for displaying content in a new tab. I turned off almost everything, except for “feeds.places”, which are responsible for displaying recently visited pages in a new tab. By the way, all settings containing the word “endpoint” are responsible for the address to which the data is sent. If you use an empty string, no data will be transmitted.
user_pref ("browser.ping-center.telemetry", false);
One of the settings for telemetry. I turn it off to speed up surfing, since resources are wasted on any action, even if it works in parallel. Since I know firsthand how to profile programs and how much the performance drops at the same time, it is better to do without it.
user_pref ("browser.safebrowsing.blockedURIs.enabled", false);
user_pref ("browser.safebrowsing.downloads.enabled", false);
user_pref ("browser.safebrowsing.downloads.remote.block_dangerous", false);
user_pref ("browser.safebrowsing.downloads.remote.block_dangerous_host", false);
user_pref ("browser.safebrowsing.downloads.remote.block_potentially_unwanted", false);
user_pref ("browser.safebrowsing.downloads.remote.block_uncommon", false);
user_pref ("browser.safebrowsing.downloads.remote.enabled", false);
user_pref ("browser.safebrowsing.enabled", false);
user_pref ("browser.safebrowsing.malware.enabled", false);
user_pref ("browser.safebrowsing.phishing.enabled", false);
user_pref ("browser.safebrowsing.provider.google.advisoryURL", "");
user_pref ("browser.safebrowsing.provider.google.gethashURL", "");
user_pref ("browser.safebrowsing.provider.google.lists", "");
user_pref ("browser.safebrowsing.provider.google.pver", "");
user_pref ("browser.safebrowsing.provider.google.reportMalwareMistakeURL", "");
user_pref ("browser.safebrowsing.provider.google.reportPhishMistakeURL", "");
user_pref ("browser.safebrowsing.provider.google.reportURL", "");
user_pref ("browser.safebrowsing.provider.google.updateURL", "");
user_pref ("browser.safebrowsing.provider.google4.advisoryName", "");
user_pref ("browser.safebrowsing.provider.google4.advisoryURL", "");
user_pref ("browser.safebrowsing.provider.google4.dataSharingURL", "");
user_pref ("browser.safebrowsing.provider.google4.gethashURL", "");
user_pref ("browser.safebrowsing.provider.google4.lastupdatetime", "");
user_pref ("browser.safebrowsing.provider.google4.lists", "");
user_pref ("browser.safebrowsing.provider.google4.nextupdatetime", "");
user_pref ("browser.safebrowsing.provider.google4.pver", "");
user_pref ("browser.safebrowsing.provider.google4.reportMalwareMistakeURL", "");
user_pref ("browser.safebrowsing.provider.google4.reportPhishMistakeURL", "");
user_pref ("browser.safebrowsing.provider.google4.reportURL", "");
user_pref ("browser.safebrowsing.provider.google4.updateURL", "");
user_pref ("browser.safebrowsing.provider.mozilla.gethashURL", "");
user_pref ("browser.safebrowsing.provider.mozilla.lists", "");
user_pref ("browser.safebrowsing.provider.mozilla.pver", "");
user_pref ("browser.safebrowsing.provider.mozilla.updateURL", "");
“Safebrowsing” - these settings are responsible for checking the visited sites to make sure they are safe. This check involves checking the site host in the local database against a blacklist and checking the uploaded files on Google servers. (Thanks to dartraiden for the hint) If the answer is yes, a service page with a warning is shown instead of the site. I disabled this check to speed up surfing. Perhaps, for those using the Windows operating system, this should not be done.
user_pref ("browser.search.countryCode", "US");
user_pref ("browser.search.geoSpecificDefaults", false);
user_pref ("browser.search.geoSpecificDefaults.url", "");
user_pref ("browser.search.geoip.url", "");
user_pref ("browser.search.hiddenOneOffs", "Bing, Amazon.com, Twitter");
user_pref ("browser.search.region", "US");
user_pref ("geo.wifi.uri", "");
Search settings. I set the region to US, for the anonymity of search queries. Also disabled location for search (“geo”).
user_pref ("browser.tabs.loadInBackground", false);
user_pref ("browser.tabs.tabMinWidth", 30);
user_pref ("browser.tabs.warnOnClose", false);
Tab settings. I would like to mention “tabMinWidth” separately. In chrome, if you open many tabs, the text disappears. And in Firefox, this setting is responsible for the minimum tab length. And if more tabs are open, then they still do not shrink, but simply hide and additional tab control buttons appear. For me, this system is very convenient, since I constantly open many pages from the same site and without text I have to constantly guess which page is where.
user_pref ("browser.urlbar.clickSelectsAll", true);
user_pref ("browser.urlbar.maxRichResults", 15);
user_pref ("browser.urlbar.trimURLs", false);
When you click on the address bar, the entire address is highlighted, not the current word. And also https is not hidden in the address bar.
user_pref ("datareporting.healthreport.uploadEnabled", false);
user_pref ("datareporting.policy.dataSubmissionEnabled", false);
user_pref ("datareporting.policy.firstRunURL", "");
Mozilla Corporation reports
user_pref ("device.sensors.enabled", false);
user_pref ("device.sensors.motion.enabled", false);
user_pref ("device.sensors.orientation.enabled", false);
This is more for the mobile version, but sometimes laptops also have some kind of sensors.
user_pref ("devtools.aboutdebugging.showSystemAddons", true);
user_pref ("devtools.onboarding.telemetry.logged", false);
user_pref ("devtools.theme", "dark");
user_pref ("devtools.toolbox.splitconsoleEnabled", false);
Developer tools settings.
user_pref ("dom.push.enabled", false);
user_pref ("permissions.default.desktop-notification", 2);
user_pref ("permissions.default.geo", 2);
Duplicates disabling notifications from the graphical menu
user_pref ("experiments.activeExperiment", false);
user_pref ("experiments.enabled", false);
user_pref ("experiments.supported", false);
I do not want to experiment. Tuning for an amateur).
user_pref ("extensions.pocket.enabled", false);
user_pref ("extensions.ui.dictionary.hidden", false);
user_pref ("extensions.ui.experiment.hidden", true);
user_pref ("extensions.ui.locale.hidden", true);
user_pref ("extensions.webextensions.remote", true);
Extension settings. Turn off Pocket.
user_pref ("findbar.highlightAll", true);
user_pref ("font.internaluseonly.changed", true);
user_pref ("font.minimum-size.x-western", 10);
user_pref ("font.name.monospace.x-western", "Hack");
user_pref ("font.name.sans-serif.x-western", "Hack");
user_pref ("font.name.serif.x-western", "Hack");
The font settings duplicate the graphical settings of the smooth scrolling, selected experimentally.
user_pref ("general.smoothScroll.durationToIntervalRatio", 1000);
user_pref ("general.smoothScroll.lines.durationMaxMS", 100);
user_pref ("general.smoothScroll.lines.durationMinMS", 100);
user_pref ("general.smoothScroll.mouseWheel.durationMaxMS", 150);
user_pref ("general.smoothScroll.mouseWheel.durationMinMS", 50);
user_pref ("general.smoothScroll.other", false);
user_pref ("general.smoothScroll.pixels", false);
user_pref ("general.smoothScroll.scrollbars.durationMaxMS", 100);
user_pref ("general.smoothScroll.scrollbars.durationMinMS", 100);
user_pref ("general.useragent.override", "Mozilla / 5.0 (X11; Linux x86_64; rv: 60.0) Gecko / 20100101 Firefox / 64.0");
user_pref ("general.useragent.vendor", "");
user_pref ("general.useragent.vendorSub", "");
User agent settings, if there is no special need, it is better not to touch them
user_pref ("general.warnOnAboutConfig", false);
Disable warning window when visiting about: config
user_pref ("gfx.use_text_smoothing_setting", true);
user_pref ("gfx.webrender.enabled", true);
user_pref ("gfx.webrender.highlight-painted-layers", false);
user_pref ("layers.acceleration.force-enabled", true);
Acceleration of rendering.
user_pref ("intl.accept_languages", "en-us, en, uk, ru");
user_pref ("intl.locale.requested", "en-US");
This information is intended to automatically select the language on the site, although the sites themselves very rarely pay attention to this setting. Hopefully the situation will change in the future.
user_pref ("layout.css.devPixelsPerPx", "1.25");
user_pref ("layout.css.osx-font-smoothing.enabled", true);
user_pref ("layout.word_select.stop_at_punctuation", true);
I would like to highlight the “devPixelsPerPx” setting. This setting is responsible for scaling the interface and will be especially useful for people with low vision or on computers with a high screen resolution. The default is “1”.
user_pref ("media.autoplay.enabled", false);
user_pref ("media.av1.enabled", true);
Video related settings. Disables autoplay and enables experimental support for the new AV1 codec.
user_pref ("network.allow-experiments", false);
user_pref ("network.cookie.prefsMigrated", true);
user_pref ("network.dns.disablePrefetch", true);
user_pref ("network.http.speculative-parallel-limit", 0);
user_pref ("network.predictor.enabled", false);
user_pref ("network.prefetch-next", false);
user_pref ("network.security.esni.enabled", true);
user_pref ("network.tcp.tcp_fastopen_enable", true);
user_pref ("network.trr.mode", 2);
user_pref ("network.trr.uri", "https://mozilla.cloudflare-dns.com/dns-query");
user_pref ("network.warnOnAboutNetworking", false);
I want to analyze this group of settings in more detail.
“Dns.disablePrefetch” and “predictor.enabled” are responsible for pre-visiting links on the page to speed up loading if the user wants to click on any of the links. If the Internet is slow, then it only worsens the situation, especially in the mobile version somewhere in the metro.
“Tcp.tcp_fastopen_enable” enables TCP Fast Open
“Trr.mode” is responsible for DNS Over HTTPS. A value of 0 disables DoH completely; 1 - DNS or DoH is used, whichever is faster; 2 - DoH is used by default, and DNS is used as a fallback; 3 - only DoH is used; 4 - mirroring mode in which DoH and DNS are used in parallel.
Well, “trr.uri” is responsible for the server that the browser knocks on to get the IP address of the sites visited.
“Security.esni.enabled” is responsible for the Encrypted SNI
user_pref ("privacy.donottrackheader.enabled", true);
user_pref ("privacy.firstparty.isolate", true);
// Disables memorizing the zoom level for the site
user_pref ("privacy.resistFingerprinting", true);
user_pref ("privacy.resistFingerprinting.autoDeclineNoUserInputCanvasPrompts", false);
Privacy settings.
user_pref ("privacy.userContext.enabled", true);
user_pref ("privacy.userContext.longPressBehavior", 2);
user_pref ("privacy.userContext.ui.enabled", true);
“UserContext” includes Multi-Account Containers.
This add-on isolates cookies and browsing history into separate containers. Unfortunately, only for the desktop. I isolated all the services of Google, Facebook and several other important services separately. Also, if you additionally install the Multi-Account Containers extension, you can use it to bind sites to containers. Even if you open a link linked to another container from one container, it opens in this container, in a new tab. Very comfortably.
user_pref ("reader.color_scheme", "dark");
user_pref ("reader.content_width", 12);
In Firefox there is a very easy read page mode, in which all but the text is deleted. It is still far from ideal, it cuts out some tags with the text, but it is still very convenient to use it. You can activate it here:
user_pref ("security.ssl.errorReporting.automatic", true);
user_pref ("toolkit.identity.enabled", false);
user_pref ("toolkit.telemetry.archive.enabled", false);
user_pref ("toolkit.telemetry.bhrPing.enabled", false);
user_pref ("toolkit.telemetry.coverage.opt-out", false);
user_pref ("toolkit.telemetry.enabled", false);
user_pref ("toolkit.telemetry.firstShutdownPing.enabled", false);
user_pref ("toolkit.telemetry.hybridContent.enabled", false);
user_pref ("toolkit.telemetry.infoURL", "");
user_pref ("toolkit.telemetry.newProfilePing.enabled", false);
user_pref ("toolkit.telemetry.reportingpolicy.firstRun", false);
user_pref ("toolkit.telemetry.server", "");
user_pref ("toolkit.telemetry.shutdownPingSender.enabled", false);
user_pref ("toolkit.telemetry.unified", false);
user_pref ("toolkit.telemetry.updatePing.enabled", false);
Diverse telemetry. Again
user_pref ("widget.chrome.allow-gtk-dark-theme", true);
user_pref ("widget.content.allow-gtk-dark-theme", true);
// user_pref ("widget.content.gtk-theme-override", "Adwaita: light");
How to hide (change) browser fingerprint?
There are protective measures when using browsers, but none of them will work 100%. And a logical question arises: "Does it make sense to use some kind of specialized software or install extensions that block certain processes when visiting sites?" The answer will be ambiguous, since a kind of dissonance arises.
At the time when you are trying to combat tracking and apply special browser settings and special software, you definitely increase the uniqueness of your digital fingerprint of the device, thereby allowing you to be more likely to identify you and form a user profile.
Multiple studies have confirmed that computers and software with “default” settings are more difficult to identify and “associate” with a specific person, while even small changes have the opposite effect.
In practice, the most effective protection is the use of the Tor Browser, which developers put a lot of effort into reducing the uniqueness of fingerprints. For everyday use, an extension like Privacy Badger is a good option. With it, you can reduce the level of tracking and the amount of information transmitted. For even more confidence and privacy protection, all of this must be used in a virtual machine.
All these methods take place, however, for the average user, such actions create certain difficulties and a waste of time.
If the topic for you is very interesting and relevant, watch the video from Ufocoder, where he talks in some detail and shows how the fingerprint technology works and whether it is possible to fight it:
In the next article we will look at ways to spoof fingerprints, as well as other "anonymous" browsers.
You have been fucked, fucked and will be fucked. State, hackers, officials.
It is impossible to stop this swinger party. But I will teach you how to protect yourself. I will show and tell you something that the "Hacker" magazine does not write about and that other channels do not tell or simply do not know. Find here a selection of the best cybersecurity articles and videos. Everything from Wi-Fi audits to auto openings (in case you've lost your keys). And also hot news with author's comments.