Brother
Professional
- Messages
- 2,590
- Reaction score
- 531
- Points
- 113
Android users from Southeast Asia tried out the work of the hidden code.
Promon has discovered a new malware for Android, called FjordPhantom. The virus uses a unique virtualization tactic to hide from detection by running malicious code in a special container.
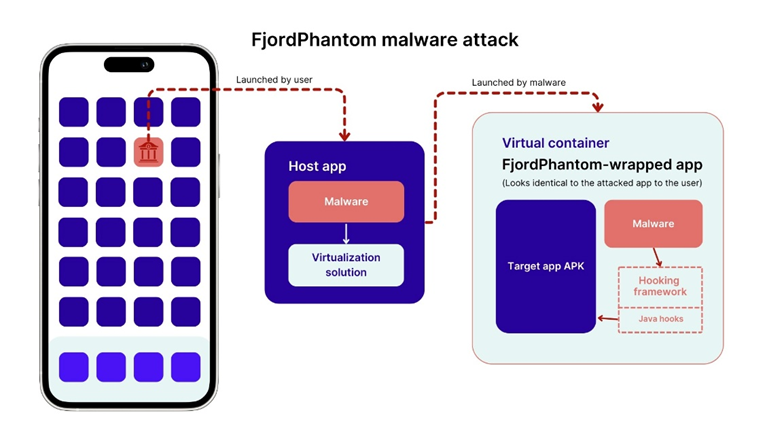
The essence of the FjordPhantom attack is that victims are invited to download fake banking applications that mimic real ones. In fact, the applications contain malicious code that runs in a virtual environment to disrupt the operation of a real banking application. The main purpose of the infection is to steal online banking credentials and manipulate transactions on the account.
FjordPhantom Attack
The malware is distributed via email, SMS, and instant messengers, and attacks have been recorded in Southeast Asian countries, including Indonesia, Thailand, Vietnam, Singapore, and Malaysia. Notably, one of the FjordPhantom use cases resulted in the theft of $280,000 from the victim, which was made possible by combining the evasive nature of the malware with social engineering in the form of calls from "bank customer support staff".
The malware uses virtualization to create a virtual container on the victim's device, without the user suspecting anything. Malicious code runs inside the container along with a real banking application, which allows it to manipulate data and intercept confidential information.
Particularly troubling is the fact that FjordPhantom violates the core security concept, the Android Sandbox, designed to prevent apps from interacting with each other. This makes the attack particularly dangerous, since changes in the banking application code do not occur, and conventional malware detection methods are powerless.
In addition, FjordPhantom is able to block functions associated with GooglePlayServices, which makes it difficult to detect root security checks. Malware is also capable of intercepting logging data, which may indicate that the malware is actively being developed and improved for targeted attacks on other applications. Promon warned that, given the active development of FjordPhantom, in the future the malware can expand its scope to cover new countries and targets.
Promon has discovered a new malware for Android, called FjordPhantom. The virus uses a unique virtualization tactic to hide from detection by running malicious code in a special container.
The essence of the FjordPhantom attack is that victims are invited to download fake banking applications that mimic real ones. In fact, the applications contain malicious code that runs in a virtual environment to disrupt the operation of a real banking application. The main purpose of the infection is to steal online banking credentials and manipulate transactions on the account.

FjordPhantom Attack
The malware is distributed via email, SMS, and instant messengers, and attacks have been recorded in Southeast Asian countries, including Indonesia, Thailand, Vietnam, Singapore, and Malaysia. Notably, one of the FjordPhantom use cases resulted in the theft of $280,000 from the victim, which was made possible by combining the evasive nature of the malware with social engineering in the form of calls from "bank customer support staff".
The malware uses virtualization to create a virtual container on the victim's device, without the user suspecting anything. Malicious code runs inside the container along with a real banking application, which allows it to manipulate data and intercept confidential information.
Particularly troubling is the fact that FjordPhantom violates the core security concept, the Android Sandbox, designed to prevent apps from interacting with each other. This makes the attack particularly dangerous, since changes in the banking application code do not occur, and conventional malware detection methods are powerless.
In addition, FjordPhantom is able to block functions associated with GooglePlayServices, which makes it difficult to detect root security checks. Malware is also capable of intercepting logging data, which may indicate that the malware is actively being developed and improved for targeted attacks on other applications. Promon warned that, given the active development of FjordPhantom, in the future the malware can expand its scope to cover new countries and targets.

